2D Tiling: Domino, Tetromino and Percolation
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Matchgates Revisited
THEORY OF COMPUTING, Volume 10 (7), 2014, pp. 167–197 www.theoryofcomputing.org RESEARCH SURVEY Matchgates Revisited Jin-Yi Cai∗ Aaron Gorenstein Received May 17, 2013; Revised December 17, 2013; Published August 12, 2014 Abstract: We study a collection of concepts and theorems that laid the foundation of matchgate computation. This includes the signature theory of planar matchgates, and the parallel theory of characters of not necessarily planar matchgates. Our aim is to present a unified and, whenever possible, simplified account of this challenging theory. Our results include: (1) A direct proof that the Matchgate Identities (MGI) are necessary and sufficient conditions for matchgate signatures. This proof is self-contained and does not go through the character theory. (2) A proof that the MGI already imply the Parity Condition. (3) A simplified construction of a crossover gadget. This is used in the proof of sufficiency of the MGI for matchgate signatures. This is also used to give a proof of equivalence between the signature theory and the character theory which permits omittable nodes. (4) A direct construction of matchgates realizing all matchgate-realizable symmetric signatures. ACM Classification: F.1.3, F.2.2, G.2.1, G.2.2 AMS Classification: 03D15, 05C70, 68R10 Key words and phrases: complexity theory, matchgates, Pfaffian orientation 1 Introduction Leslie Valiant introduced matchgates in a seminal paper [24]. In that paper he presented a way to encode computation via the Pfaffian and Pfaffian Sum, and showed that a non-trivial, though restricted, fragment of quantum computation can be simulated in classical polynomial time. Underlying this magic is a way to encode certain quantum states by a classical computation of perfect matchings, and to simulate certain ∗Supported by NSF CCF-0914969 and NSF CCF-1217549. -

Computations in Algebraic Geometry with Macaulay 2
Computations in algebraic geometry with Macaulay 2 Editors: D. Eisenbud, D. Grayson, M. Stillman, and B. Sturmfels Preface Systems of polynomial equations arise throughout mathematics, science, and engineering. Algebraic geometry provides powerful theoretical techniques for studying the qualitative and quantitative features of their solution sets. Re- cently developed algorithms have made theoretical aspects of the subject accessible to a broad range of mathematicians and scientists. The algorith- mic approach to the subject has two principal aims: developing new tools for research within mathematics, and providing new tools for modeling and solv- ing problems that arise in the sciences and engineering. A healthy synergy emerges, as new theorems yield new algorithms and emerging applications lead to new theoretical questions. This book presents algorithmic tools for algebraic geometry and experi- mental applications of them. It also introduces a software system in which the tools have been implemented and with which the experiments can be carried out. Macaulay 2 is a computer algebra system devoted to supporting research in algebraic geometry, commutative algebra, and their applications. The reader of this book will encounter Macaulay 2 in the context of concrete applications and practical computations in algebraic geometry. The expositions of the algorithmic tools presented here are designed to serve as a useful guide for those wishing to bring such tools to bear on their own problems. A wide range of mathematical scientists should find these expositions valuable. This includes both the users of other programs similar to Macaulay 2 (for example, Singular and CoCoA) and those who are not interested in explicit machine computations at all. -

Project Design: Tetris
Project Design: Tetris Prof. Stephen Edwards Spring 2020 Arsalaan Ansari (aaa2325) Kevin Rayfeng Li (krl2134) Sooyeon Jo (sj2801) Josh Learn (jrl2196) Introduction The purpose of this project is to build a Tetris video game system using System Verilog and C language on a FPGA board. Our Tetris game will be a single player game where the computer randomly generates tetromino blocks (in the shapes of O, J, L, Z, S, I) that the user can rotate using their keyboard. Tetrominoes can be stacked to create lines that will be cleared by the computer and be counted as points that will be tracked. Once a tetromino passes the boundary of the screen the user will lose. Fig 1: Screenshot from an online implementation of Tetris User input will come through key inputs from a keyboard, and the Tetris sprite based output will be displayed using a VGA display. The System Verilog code will create the sprite based imagery for the VGA display and will communicate with the C language game logic to change what is displayed. Additionally, the System Verilog code will generate accompanying audio that will supplement the game in the form of sound effects. The C game logic will generate random tetromino blocks to drop, translate key inputs to rotation of blocks, detect and clear lines, determine what sound effects to be played, keep track of the score, and determine when the game has ended. Architecture The figure below is the architecture for our project Fig 2: Proposed architecture Hardware Implementation VGA Block The Tetris game will have 3 layers of graphics. -

Treb All De Fide Gra U
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by UPCommons. Portal del coneixement obert de la UPC Grau en Matematiques` T´ıtol:Tilings and the Aztec Diamond Theorem Autor: David Pardo Simon´ Director: Anna de Mier Departament: Mathematics Any academic:` 2015-2016 TREBALL DE FI DE GRAU Facultat de Matemàtiques i Estadística David Pardo 2 Tilings and the Aztec Diamond Theorem A dissertation submitted to the Polytechnic University of Catalonia in accordance with the requirements of the Bachelor's degree in Mathematics in the School of Mathematics and Statistics. David Pardo Sim´on Supervised by Dr. Anna de Mier School of Mathematics and Statistics June 28, 2016 Abstract Tilings over the plane R2 are analysed in this work, making a special focus on the Aztec Diamond Theorem. A review of the most relevant results about monohedral tilings is made to continue later by introducing domino tilings over subsets of R2. Based on previous work made by other mathematicians, a proof of the Aztec Dia- mond Theorem is presented in full detail by completing the description of a bijection that was not made explicit in the original work. MSC2010: 05B45, 52C20, 05A19. iii Contents 1 Tilings and basic notions1 1.1 Monohedral tilings............................3 1.2 The case of the heptiamonds.......................8 1.2.1 Domino Tilings.......................... 13 2 The Aztec Diamond Theorem 15 2.1 Schr¨odernumbers and Hankel matrices................. 16 2.2 Bijection between tilings and paths................... 19 2.3 Hankel matrices and n-tuples of Schr¨oderpaths............ 27 v Chapter 1 Tilings and basic notions The history of tilings and patterns goes back thousands of years in time. -

Human-Computer Interaction in 3D Object Manipulation in Virtual Environments: a Cognitive Ergonomics Contribution Sarwan Abbasi
Human-computer interaction in 3D object manipulation in virtual environments: A cognitive ergonomics contribution Sarwan Abbasi To cite this version: Sarwan Abbasi. Human-computer interaction in 3D object manipulation in virtual environments: A cognitive ergonomics contribution. Computer Science [cs]. Université Paris Sud - Paris XI, 2010. English. tel-00603331 HAL Id: tel-00603331 https://tel.archives-ouvertes.fr/tel-00603331 Submitted on 24 Jun 2011 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Human‐computer interaction in 3D object manipulation in virtual environments: A cognitive ergonomics contribution Doctoral Thesis submitted to the Université de Paris‐Sud 11, Orsay Ecole Doctorale d'Informatique Laboratoire d'Informatique pour la Mécanique et les Sciences de l'Ingénieur (LIMSI‐CNRS) 26 November 2010 By Sarwan Abbasi Jury Michel Denis (Directeur de thèse) Jean‐Marie Burkhardt (Co‐directeur) Françoise Détienne (Rapporteur) Stéphane Donikian (Rapporteur) Philippe Tarroux (Examinateur) Indira Thouvenin (Examinatrice) Object Manipulation in Virtual Environments Thesis Report by Sarwan ABBASI Acknowledgements One of my former professors, M. Ali YUSUF had once told me that if I learnt a new language in a culture different than mine, it would enable me to look at the world in an entirely new way and in fact would open up for me a whole new world for me. -

Homework 4: Tetronimoes
CS 371M Homework 4: Tetronimoes Submission: All submissions should be done via git. Refer to the git setup, and submission documents for the correct procedure. The root directory of your repository should contain your README file, and your Android Studio project directory. Overview: “If Tetris has taught me anything, it’s that errors pile up and accomplishments disappear.” – Some guy on Reddit In this and the next homework, you will be implementing a simple game of Tetris. For those who have never played Tetris, definitely try it out. Below is a link to a free online tetris game. Use the “up” arrow key to rotate the blocks. https://www.freetetris.org/game.php On the following page is a screenshot of the game as it should look for this class. For previous assignments, layout and quality of appearance have not been major factors in grading. However, appearance will be considered for this assignment. Your app should look at least as polished as the example app. API: We have defined several framework classes for your use. TCell: A class that represents a singe square. Each TCell has a color and (x,y) coordinates. TGrid: A class that creates a grid of cells. Use this to represent the main grid of cells in your game. This class also provides several utility functions that help you to detect and delete full rows of cells. Tetromino: A class that represents a Tetris Tetromino. This class can be inserted into a TGrid, moved, and rotated. All Tetromino movement functions return a Boolean value depending on whether the movement succeeded or not. -

On the Computation of Pfaffians?
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Elsevier - Publisher Connector DISCRETE APPLIED MATHEMATICS ELSEVIER Discrete Applied Mathematics 51 (1994) 269-275 On the computation of pfaffians? G. Galbiati” and F. Maffiolibs* “Universitir di Pavia, Italy bPolitecnico di Milano, Milano, Italy (Received 21 October 1991) Abstract We present an efficient algorithm for computing the pfaffian of a matrix whose elements belong to an integral domain. Relevant applications are exact value problems in matching and matroid theory. 1. Introduction This work deals with efficient ways of computing the pfaffian of a skew-symmetric matrix whose elements belong to an integral domain. Pfaffians play an important role in matching problems [9], and in their natural generalization into matroid parity problems [3,8]. Since for every skew-symmetric matrix of even order it is well known [7] that its determinant is equal to the square of the pfaffian of the matrix, in the solution of existence versions of the above mentioned matching and matroid parity problems, the computation of the pfaffian can be substituted by the computation of the determinant. However, in the solution of the corresponding exact value problems, computing pfaffians becomes essential [2,3]. The possibility of directly computing pfaffians was already pointed out in [l]. This paper presents an efficient algorithm for computing the pfaffian of a matrix whose elements belong to an integral domain. When applied to an integral matrix, similarly to Edmonds’ algorithm for computing the determinant [4], this algorithm works with elements of bounded magnitude, namely bounded above by the magni- tude of any minor of the given matrix. -

An Exploration of the Permanent-Determinant Method
An exploration of the permanent-determinant method Greg Kuperberg UC Davis [email protected] Abstract The permanent-determinant method and its generalization, the Hafnian- Pfaffian method, are methods to enumerate perfect matchings of plane graphs that were discovered by P. W. Kasteleyn. We present several new techniques and arguments related to the permanent-determinant with consequences in enu- merative combinatorics. Here are some of the results that follow from these techniques: 1. If a bipartite graph on the sphere with 4n vertices is invariant under the antipodal map, the number of matchings is the square of the number of matchings of the quotient graph. 2. The number of matchings of the edge graph of a graph with vertices of degree at most 3 is a power of 2. 3. The three Carlitz matrices whose determinants count a × b × c plane partitions all have the same cokernel. 4. Two symmetry classes of plane partitions can be enumerated with almost no calculation. Submitted: October 16, 1998; Accepted: November 9, 1998 [Also available as math.CO/9810091] The permanent-determinant method and its generalization, the Hafnian-Pfaffian method, is a method to enumerate perfect matchings of plane graphs that was dis- covered by P. W. Kasteleyn [18]. Given a bipartite plane graph Z, the method pro- duces a matrix whose determinant is the number of perfect matchings of Z.Given a non-bipartite plane graph Z, it produces a Pfaffian with the same property. The method can be used to enumerate symmetry classes of plane partitions [21, 22] and domino tilings of an Aztec diamond [45] and is related to some recent factorizations of the number of matchings of plane graphs with symmetry [5, 15]. -

Tetromino Reptiles
Mathigon – Lesson Plan Tetromino Reptiles Standards Prior knowledge NC Key Stage 3: Use scale factors, scale diagrams and maps It will help if students have some familiarity with expressing relationships CCSS 7.G.A.1: Solve problems involving scale drawings of using ratio, and with square numbers. geometric figures Lesson outline This task uses Polypad’s tetrominoes as a context for exploring enlargements (dilations) and scale factors. Tetrominoes are shapes which can be made from 4 individual squares, and will be instantly recognisable to any student who has played the classic game Tetris. Lesson objective: Understand how the area of a shape changes when it is enlarged. Lesson activity Warm-up Show students this Polypad canvas. Explain that two of the tetrominoes have been enlarged (dilated) correctly, but two of them have mistakes. Invite students to work out the scale factor by which the two correct enlargements have been drawn, and to use the pen tool (or copy the diagrams onto squared paper) to correct the mistakes in the Canvas Link incorrect enlargements. Solution: The square has been correctly enlarged by a scale factor of 3, and the L tetromino has been correctly enlarged by a scale factor of 5. The T tetromino and the Z tetromino have not been enlarged correctly. If students haven’t seen tetrominoes before, and you think they could benefit from additional scaffolding before the warm up above, you could challenge them to find all the different arrangements of four 1-square tiles. They can use this canvas as a starting point. Main Activity Some shapes can be used to tile an enlargement of themselves – this is sometimes called a rep-tile. -

A Speech Therapy Game for Children with Speech Sound Disorders
Apraxia World: A Speech Therapy Game for Children with Speech Sound Disorders Adam Hair* Penelope Monroe* Beena Ahmed Texas A&M University University of Sydney University of New South Wales College Station, TX, USA Sydney, NSW, Australia Sydney, NSW, Australia [email protected] [email protected] Texas A&M University at Qatar Doha, Qatar [email protected] Kirrie J. Ballard Ricardo Gutierrez-Osuna University of Sydney Texas A&M University Sydney, NSW, Australia College Station, TX, USA [email protected] [email protected] ABSTRACT INTRODUCTION This paper presents Apraxia World, a remote therapy tool Speech sound disorders (SSDs) can affect language for speech sound disorders that integrates speech exercises production and speech articulation in children, leading to into an engaging platformer-style game. In Apraxia World, serious communicative disabilities [4]. Estimates for the the player controls the avatar with virtual buttons/joystick, prevalence of SSDs in children vary; some suggest between whereas speech input is associated with assets needed to 2% and 25% of children aged 5-7 years may be affected advance from one level to the next. We tested performance [21], while others estimate values closer to 1% of the and child preference of two strategies for delivering speech primary-school-aged population [26]. Regardless of their exercises: during each level, and after it. Most children exact prevalence, SSDs can have potentially devastating indicated that doing exercises after completing each level effects on a child’s communication development [10]. was less disruptive and preferable to doing exercises Fortunately, children can reduce symptoms and improve scattered through the level. -
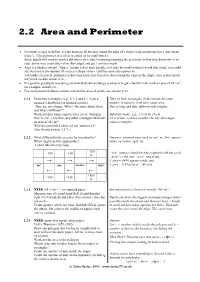
Area and Perimeter
2.2 Area and Perimeter Perimeter is easy to define: it’s the distance all the way round the edge of a shape (land sometimes has a “perimeter fence”). (The perimeter of a circle is called its circumference.) Some pupils will want to mark a dot where they start measuring/counting the perimeter so that they know where to stop. Some may count dots rather than edges and get 1 unit too much. Area is a harder concept. “Space” means 3-d to most people, so it may be worth trying to avoid that word: you could say that area is the amount of surface a shape covers. (Surface area also applies to 3-d solids.) (Loosely, perimeter is how much ink you’d need to draw round the edge of the shape; area is how much ink you’d need to colour it in.) It’s good to get pupils measuring accurately-drawn drawings or objects to get a feel for how small an area of 20 cm2, for example, actually is. For comparisons between volume and surface area of solids, see section 2:10. 2.2.1 Draw two rectangles (e.g., 6 × 4 and 8 × 3) on a They’re both rectangles, both contain the same squared whiteboard (or squared acetate). number of squares, both have same area. “Here are two shapes. What’s the same about them One is long and thin, different side lengths. and what’s different?” Work out how many squares they cover. (Imagine Infinitely many; e.g., 2.4 cm by 10 cm. -

Holographic Algorithms
Holographic Algorithms Jin-Yi Cai ∗ Computer Sciences Department University of Wisconsin Madison, WI 53706. USA. Email: [email protected] Abstract Leslie Valiant recently proposed a theory of holographic algorithms. These novel algorithms achieve exponential speed-ups for certain computational problems compared to naive algorithms for the same problems. The methodology uses Pfaffians and (planar) perfect matchings as basic computational primitives, and attempts to create exponential cancellations in computation. In this article we survey this new theory of matchgate computations and holographic algorithms. Key words: Theoretical Computer Science, Computational Complexity Theory, Perfect Match- ings, Pfaffians, Matchgates, Matchcircuits, Matchgrids, Signatures, Holographic Algorithms. 1 Some Historical Background There have always been two major strands of mathematical thought since antiquity and across civilizations: Structural Theory and Computation, as exemplified by Euclid’s Elements and Dio- phantus’ Arithmetica. Structural Theory prizes the formulation and proof of structural theorems, while Computation seeks efficient algorithmic methods to solve problems. Of course, these strands of mathematical thought are not in opposition to each other, but rather they are highly intertwined and mutually complementary. For example, from Euclid’s Elements we learn the Euclidean algo- rithm to find the greatest common divisor of two positive integers. This algorithm can serve as the first logical step in the structural derivation of elementary number theory. At the same time, the correctness and efficiency of this and similar algorithms demand proofs in a purely structural sense, and use quite a bit more structural results from number theory [4]. As another example, the computational difficulty of recognizing primes and the related (but separate) problem of in- teger factorization already fascinated Gauss, and are closely tied to the structural theory of the distribution of primes [21, 1, 2].