Unicode + PHP Ayesh Karunaratne Unicode + PHP Ayesh Karunaratne Security Researcher, Freelance Software Developer
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Alpha • Bravo • Charlie
ALPHA • BRAVO • CHARLIE Inspired by Alpha, Bravo, Charlie (published by Phaidon) these Perfect activity sheets introduce young people to four different nautical codes. There are messages to decode, questions to answer for curious and some fun facts to share with friends and family. 5-7 year olds FLAG IT UP These bright, colorful flags are known as signal flags. There is one flag for each letter of the alphabet. 1. What is the right-hand side of a ship called? Use the flags to decode the answer! 3. Draw and color the flag that represents the first letter of your name. 2. Draw and color flags to spell out this message: SHIP AHOY SH I P AHOY FUN FACT Each flag also has its own To purchase your copy of meaning when it's flown by 2. Alpha, Bravo, Charlie visit phaidon.com/childrens2016 itself. For example, the N flag by STARBOARD 1. itself means "No" or "Negative". Answers: ALPHA OSCAR KILO The Phonetic alphabet matches every letter with a word so that letters can’t be mixed up and sailors don’t get the wrong message. 1. Write in the missing first letters from these words in the Phonetic alphabet. What word have you spelled out? Write it in here: HINT: The word for things that are transported by ship. 2. Can you decode the answer to this question: What types of cargo did Clipper ships carry in the 1800s? 3. Use the Phonetic alphabet to spell out your first name. FUN FACT The Phonetic alphabet’s full name is the GOLD AND WOOL International Radiotelephony Spelling Alphabet. -
UNIT 2 Braille
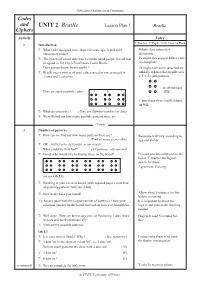
Mathematics Enhancement Programme Codes and UNIT 2 Braille Lesson Plan 1 Braille Ciphers Activity Notes T: Teacher P: Pupil Ex.B: Exercise Book 1 Introduction T: What code, designed more than 150 years ago, is still used Whole class interactive extensively today? discussion. T: The system of raised dots which enables blind people to read was Ps might also suggest Morse code designed in 1833 by a Frenchman, Louis Braille. or semaphore. Does anyone know how it works? Ps might have some ideas but are T: Braille uses a system of dots, either raised or not, arranged in unlikely to know that Braille uses 3 rows and 2 columns. a 32× configuration. on whiteboard Here are some possible codes: ape (WB). T puts these three Braille letters on WB. T: What do you notice? (They use different numbers of dots) T: We will find out how many possible patterns there are. 10 mins 2 Number of patterns T: How can we find out how many patterns there are? Response will vary according to (Find as many as possible) age and ability. T: OK – but let us be systematic in our search. What could we first find? (All patterns with one dot) T: Good; who would like to display these on the board? P(s) put possible solutions on the board; T stresses the logical search for these. Agreement. Praising. (or use OS 2.1) T: Working in your exercise books (with squared paper), now find all possible patterns with just 2 dots. T: How many have you found? Allow about 5 minutes for this before reviewing. -

Hieroglyphs for the Information Age: Images As a Replacement for Characters for Languages Not Written in the Latin-1 Alphabet Akira Hasegawa
Rochester Institute of Technology RIT Scholar Works Theses Thesis/Dissertation Collections 5-1-1999 Hieroglyphs for the information age: Images as a replacement for characters for languages not written in the Latin-1 alphabet Akira Hasegawa Follow this and additional works at: http://scholarworks.rit.edu/theses Recommended Citation Hasegawa, Akira, "Hieroglyphs for the information age: Images as a replacement for characters for languages not written in the Latin-1 alphabet" (1999). Thesis. Rochester Institute of Technology. Accessed from This Thesis is brought to you for free and open access by the Thesis/Dissertation Collections at RIT Scholar Works. It has been accepted for inclusion in Theses by an authorized administrator of RIT Scholar Works. For more information, please contact [email protected]. Hieroglyphs for the Information Age: Images as a Replacement for Characters for Languages not Written in the Latin- 1 Alphabet by Akira Hasegawa A thesis project submitted in partial fulfillment of the requirements for the degree of Master of Science in the School of Printing Management and Sciences in the College of Imaging Arts and Sciences of the Rochester Institute ofTechnology May, 1999 Thesis Advisor: Professor Frank Romano School of Printing Management and Sciences Rochester Institute ofTechnology Rochester, New York Certificate ofApproval Master's Thesis This is to certify that the Master's Thesis of Akira Hasegawa With a major in Graphic Arts Publishing has been approved by the Thesis Committee as satisfactory for the thesis requirement for the Master ofScience degree at the convocation of May 1999 Thesis Committee: Frank Romano Thesis Advisor Marie Freckleton Gr:lduate Program Coordinator C. -

Portable Paper
Volume 2, Number 2 The HP Portable/Portable Plus Users Newsletter March / April, 1987 PortableTHE Paper Special Feature: Database Software Management Publisher's Message ...................... I Special Feature: Database Management Letters Software Charge Portable Off Car Lighter .............. 2 Introduction ............................ 16 Portable To Macintosh ..................... 4 Database Management Product Summary ...... 16 110% Lotus As A Database Manager . 18 New HP Portable? ......................... '; Executive Card Manager ................... 18 Updates on Personalized Software Products ..... 5 dBASE II ............................... 22 Buying Disks ............................ 6 Turbo Pascal Toolbox ..................... 2-} X-rays And The Portable .................... 6 PC File III .............................. 24 More Info On Backlighting ................. 33 T/Master ............................... 25 HP-IL Link Program ........ .............. 33 Condor Junior .......................... 25 Foundations Conclusion ............................. 25 Built-in Self-Test .......................... 8 PLUS Notes Six Ways To Restart Your Portable ............. 8 Lotus 2.01 and HAL ...................... 25 Getting Program To Run . ..... 8 B Drive RAM Cards With Greater Capacity ........... 26 EPROM Update .......................... 26 DOS AID Software Drawer & SPC ................ 27 Bypassing PAM ............................ 11 1erminal Through The Looking Glass ............ 27 CompuServe Autologon, Uploading Revisited .... -

INTERSKILL MAINFRAME QUARTERLY December 2011
INTERSKILL MAINFRAME QUARTERLY December 2011 Retaining Data Center Skills Inside This Issue and Knowledge Retaining Data Center Skills and Knowledge 1 Interskill Releases - December 2011 2 By Greg Hamlyn Vendor Briefs 3 This the final chapter of this four part series that briefly Taking Care of Storage 4 explains the data center skills crisis and the pros and cons of Learning Spotlight – Managing Projects 5 implementing a coaching or mentoring program. In this installment we will look at some of the steps to Tech-Head Knowledge Test – Utilizing ISPF 5 implementing a program such as this into your data center. OPINION: The Case for a Fresh Technical If you missed these earlier installments, click the links Opinion 6 below. TECHNICAL: Lost in Translation Part 1 - EBCDIC Code Pages 7 Part 1 – The Data Center Skills Crisis MAINFRAME – Weird and Unusual! 10 Part 2 – How Can I Prevent Skills Loss in My Data Center? Part 3 – Barriers to Implementing a Coaching or Mentoring Program should consider is the GROW model - Determine whether an external consultant should be Part Four – Implementing a Successful Coaching used (include pros and cons) - Create a basic timeline of the project or Mentoring Program - Identify how you will measure the effectiveness of the project The success of any project comes down to its planning. If - Provide some basic steps describing the coaching you already believe that your data center can benefit from and mentoring activities skills and knowledge transfer and that coaching and - Next phase if the pilot program is deemed successful mentoring will assist with this, then outlining a solid (i.e. -

IBM Unica Campaign: Administrator's Guide to Remove a Dimension Hierarchy
IBM Unica Campaign Version 8 Release 6 February, 2013 Administrator's Guide Note Before using this information and the product it supports, read the information in “Notices” on page 385. This edition applies to version 8, release 6, modification 0 of IBM Unica Campaign and to all subsequent releases and modifications until otherwise indicated in new editions. © Copyright IBM Corporation 1998, 2013. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Chapter 1. Administration in IBM Unica To view system table contents .......27 Campaign ..............1 Working with user tables ..........28 Campaign-related administrative tasks in IBM Unica About working with user tables ......28 Marketing ...............1 Guidelines for mapping user tables .....28 To access data sources from within a flowchart 29 Chapter 2. Managing security in IBM Working with user tables while editing a flowchart ..............29 Unica Campaign ...........3 Working with user tables from the Campaign About security policies ...........3 Settings page .............30 The global security policy .........3 Working with data dictionaries ........39 How Campaign evaluates permissions.....4 To open a data dictionary.........39 Using the Owner and Folder Owner roles . 4 To apply changes to a data dictionary ....40 Guidelines for designing security policies....5 When to use a data dictionary .......40 Security scenarios.............5 Data dictionary syntax..........40 Scenario 1: Company with a single division . 5 To manually create a new data dictionary . 40 Scenario 2: Company with multiple separate Working with table catalogs .........41 divisions...............7 To access table catalogs .........41 Scenario 3: Restricted access within a division . -

Base64 Character Encoding and Decoding Modeling
Base64 Character Encoding and Decoding Modeling Isnar Sumartono1, Andysah Putera Utama Siahaan2, Arpan3 Faculty of Computer Science,Universitas Pembangunan Panca Budi Jl. Jend. Gatot Subroto Km. 4,5 Sei Sikambing, 20122, Medan, Sumatera Utara, Indonesia Abstract: Security is crucial to maintaining the confidentiality of the information. Secure information is the information should not be known to the unreliable person, especially information concerning the state and the government. This information is often transmitted using a public network. If the data is not secured in advance, would be easily intercepted and the contents of the information known by the people who stole it. The method used to secure data is to use a cryptographic system by changing plaintext into ciphertext. Base64 algorithm is one of the encryption processes that is ideal for use in data transmission. Ciphertext obtained is the arrangement of the characters that have been tabulated. These tables have been designed to facilitate the delivery of data during transmission. By applying this algorithm, errors would be avoided, and security would also be ensured. Keywords: Base64, Security, Cryptography, Encoding I. INTRODUCTION Security and confidentiality is one important aspect of an information system [9][10]. The information sent is expected to be well received only by those who have the right. Information will be useless if at the time of transmission intercepted or hijacked by an unauthorized person [7]. The public network is one that is prone to be intercepted or hijacked [1][2]. From time to time the data transmission technology has developed so rapidly. Security is necessary for an organization or company as to maintain the integrity of the data and information on the company. -

Man'yogana.Pdf (574.0Kb)
Bulletin of the School of Oriental and African Studies http://journals.cambridge.org/BSO Additional services for Bulletin of the School of Oriental and African Studies: Email alerts: Click here Subscriptions: Click here Commercial reprints: Click here Terms of use : Click here The origin of man'yogana John R. BENTLEY Bulletin of the School of Oriental and African Studies / Volume 64 / Issue 01 / February 2001, pp 59 73 DOI: 10.1017/S0041977X01000040, Published online: 18 April 2001 Link to this article: http://journals.cambridge.org/abstract_S0041977X01000040 How to cite this article: John R. BENTLEY (2001). The origin of man'yogana. Bulletin of the School of Oriental and African Studies, 64, pp 5973 doi:10.1017/S0041977X01000040 Request Permissions : Click here Downloaded from http://journals.cambridge.org/BSO, IP address: 131.156.159.213 on 05 Mar 2013 The origin of man'yo:gana1 . Northern Illinois University 1. Introduction2 The origin of man'yo:gana, the phonetic writing system used by the Japanese who originally had no script, is shrouded in mystery and myth. There is even a tradition that prior to the importation of Chinese script, the Japanese had a native script of their own, known as jindai moji ( , age of the gods script). Christopher Seeley (1991: 3) suggests that by the late thirteenth century, Shoku nihongi, a compilation of various earlier commentaries on Nihon shoki (Japan's first official historical record, 720 ..), circulated the idea that Yamato3 had written script from the age of the gods, a mythical period when the deity Susanoo was believed by the Japanese court to have composed Japan's first poem, and the Sun goddess declared her son would rule the land below. -

File Formats
man pages section 4: File Formats Sun Microsystems, Inc. 4150 Network Circle Santa Clara, CA 95054 U.S.A. Part No: 817–3945–10 September 2004 Copyright 2004 Sun Microsystems, Inc. 4150 Network Circle, Santa Clara, CA 95054 U.S.A. All rights reserved. This product or document is protected by copyright and distributed under licenses restricting its use, copying, distribution, and decompilation. No part of this product or document may be reproduced in any form by any means without prior written authorization of Sun and its licensors, if any. Third-party software, including font technology, is copyrighted and licensed from Sun suppliers. Parts of the product may be derived from Berkeley BSD systems, licensed from the University of California. UNIX is a registered trademark in the U.S. and other countries, exclusively licensed through X/Open Company, Ltd. Sun, Sun Microsystems, the Sun logo, docs.sun.com, AnswerBook, AnswerBook2, and Solaris are trademarks or registered trademarks of Sun Microsystems, Inc. in the U.S. and other countries. All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International, Inc. in the U.S. and other countries. Products bearing SPARC trademarks are based upon an architecture developed by Sun Microsystems, Inc. The OPEN LOOK and Sun™ Graphical User Interface was developed by Sun Microsystems, Inc. for its users and licensees. Sun acknowledges the pioneering efforts of Xerox in researching and developing the concept of visual or graphical user interfaces for the computer industry. Sun holds a non-exclusive license from Xerox to the Xerox Graphical User Interface, which license also covers Sun’s licensees who implement OPEN LOOK GUIs and otherwise comply with Sun’s written license agreements. -

ISO Basic Latin Alphabet
ISO basic Latin alphabet The ISO basic Latin alphabet is a Latin-script alphabet and consists of two sets of 26 letters, codified in[1] various national and international standards and used widely in international communication. The two sets contain the following 26 letters each:[1][2] ISO basic Latin alphabet Uppercase Latin A B C D E F G H I J K L M N O P Q R S T U V W X Y Z alphabet Lowercase Latin a b c d e f g h i j k l m n o p q r s t u v w x y z alphabet Contents History Terminology Name for Unicode block that contains all letters Names for the two subsets Names for the letters Timeline for encoding standards Timeline for widely used computer codes supporting the alphabet Representation Usage Alphabets containing the same set of letters Column numbering See also References History By the 1960s it became apparent to thecomputer and telecommunications industries in the First World that a non-proprietary method of encoding characters was needed. The International Organization for Standardization (ISO) encapsulated the Latin script in their (ISO/IEC 646) 7-bit character-encoding standard. To achieve widespread acceptance, this encapsulation was based on popular usage. The standard was based on the already published American Standard Code for Information Interchange, better known as ASCII, which included in the character set the 26 × 2 letters of the English alphabet. Later standards issued by the ISO, for example ISO/IEC 8859 (8-bit character encoding) and ISO/IEC 10646 (Unicode Latin), have continued to define the 26 × 2 letters of the English alphabet as the basic Latin script with extensions to handle other letters in other languages.[1] Terminology Name for Unicode block that contains all letters The Unicode block that contains the alphabet is called "C0 Controls and Basic Latin". -

The Unicode Cookbook for Linguists: Managing Writing Systems Using Orthography Profiles
Zurich Open Repository and Archive University of Zurich Main Library Strickhofstrasse 39 CH-8057 Zurich www.zora.uzh.ch Year: 2017 The Unicode Cookbook for Linguists: Managing writing systems using orthography profiles Moran, Steven ; Cysouw, Michael DOI: https://doi.org/10.5281/zenodo.290662 Posted at the Zurich Open Repository and Archive, University of Zurich ZORA URL: https://doi.org/10.5167/uzh-135400 Monograph The following work is licensed under a Creative Commons: Attribution 4.0 International (CC BY 4.0) License. Originally published at: Moran, Steven; Cysouw, Michael (2017). The Unicode Cookbook for Linguists: Managing writing systems using orthography profiles. CERN Data Centre: Zenodo. DOI: https://doi.org/10.5281/zenodo.290662 The Unicode Cookbook for Linguists Managing writing systems using orthography profiles Steven Moran & Michael Cysouw Change dedication in localmetadata.tex Preface This text is meant as a practical guide for linguists, and programmers, whowork with data in multilingual computational environments. We introduce the basic concepts needed to understand how writing systems and character encodings function, and how they work together. The intersection of the Unicode Standard and the International Phonetic Al- phabet is often not met without frustration by users. Nevertheless, thetwo standards have provided language researchers with a consistent computational architecture needed to process, publish and analyze data from many different languages. We bring to light common, but not always transparent, pitfalls that researchers face when working with Unicode and IPA. Our research uses quantitative methods to compare languages and uncover and clarify their phylogenetic relations. However, the majority of lexical data available from the world’s languages is in author- or document-specific orthogra- phies. -

Unicode and Code Page Support
Natural for Mainframes Unicode and Code Page Support Version 4.2.6 for Mainframes October 2009 This document applies to Natural Version 4.2.6 for Mainframes and to all subsequent releases. Specifications contained herein are subject to change and these changes will be reported in subsequent release notes or new editions. Copyright © Software AG 1979-2009. All rights reserved. The name Software AG, webMethods and all Software AG product names are either trademarks or registered trademarks of Software AG and/or Software AG USA, Inc. Other company and product names mentioned herein may be trademarks of their respective owners. Table of Contents 1 Unicode and Code Page Support .................................................................................... 1 2 Introduction ..................................................................................................................... 3 About Code Pages and Unicode ................................................................................ 4 About Unicode and Code Page Support in Natural .................................................. 5 ICU on Mainframe Platforms ..................................................................................... 6 3 Unicode and Code Page Support in the Natural Programming Language .................... 7 Natural Data Format U for Unicode-Based Data ....................................................... 8 Statements .................................................................................................................. 9 Logical