Identity-Based Key Exchange on In-Vehicle Networks: CAN-FD & Flexray
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

J1939/J1708 to USB Adapter
5940 South Ernest Drive Terre Haute, IN 47802 812-418-0526 wwww.simmasoftware.com Simma Software Introduces New Low Cost J1939/J1708 to USB Adapter Simma Software, Inc. 5940 South Ernest Drive Terre Haute, IN 47802 Heavy Duty Vehicle Network Adapter (VNA) Release date: November 7, 2011 March 17, 2011, Terre Haute, IN – Simma Software, Inc. announced today that they are introducing a new low cost high-performance J1939/J1708 Adapter for the heavy-duty and commercial vehicle market. The VNA product family supports dual J1939 networks and a single J1587/J1708 network. The VNA product will allow OEMs, fleets, and service providers, for heavy duty and commercial vehicles, to connect in real-time to their vehicle networks, allowing them to instantly gather critical information such as active diagnostic faults and fuel economy metrics. For connections back to the host computer, mobile computing device, or a handheld device, the VNA family supports USB, RS-232, and an Ethernet connection. To learn more, see our J1939 to USB Adapter page. Future devices planned for May of 2011 will support wireless connections such as Bluetooth and WiFi (802.11). "The industry loves our new VNA product line and its low price point. Typically devices of this class sell for around $750, but by using new technology and our proven J1939 software, we are able to reach a 5K price point as low as $74.95 depending on volume and options". said JR Simma, the President of Simma Software. About Simma Software, Inc. Simma Software, Inc. specializes in real-time embedded software for the automotive, military, and industrial automation industry. -

Univerzita Pardubice Dopravní Fakulta Jana Pernera Diagnostika Nákladních Vozidel Pomocí Převodníku Pierre Litvák Bakalá
Univerzita Pardubice Dopravní fakulta Jana Pernera Diagnostika nákladních vozidel pomocí převodníku Pierre Litvák Bakalářská práce 2014 Prohlášení autora Prohlašuji, že jsem tuto práci vypracoval samostatně. Veškeré literární prameny a informace, které jsem v práci využil, jsou uvedeny v seznamu použité literatury. Byl jsem seznámen s tím, že se na moji práci vztahují práva a povinnosti vyplývající ze zákona č. 121/2000 Sb., autorský zákon, zejména se skutečností, že Univerzita Pardubice má právo na uzavření licenční smlouvy o užití této práce jako školního díla podle § 60 odst. 1 autorského zákona, a s tím, že pokud dojde k užití této práce mnou nebo bude poskytnuta licence o užití jinému subjektu, je Univerzita Pardubice oprávněna ode mne požadovat přiměřený příspěvek na úhradu nákladů, které na vytvoření díla vynaložila, a to podle okolností až do jejich skutečné výše. Souhlasím s prezenčním zpřístupněním své práce v Univerzitní knihovně. V Pardubicích dne 29. 5. 2014 Pierre Litvák Poděkování Rád bych poděkoval mému vedoucímu bakalářské práce panu Ing. Václavu Lenochovi a konzultantovi panu Ing. Zdeňku Maškovi, Ph.D. za odborné vedení, trpělivost a odbornou pomoc, rodině za podporu a důvěru ve mě vloženou, zejména pak bratrovi, mému kamarádovi Filipovi za pozitivní myšlenky a netradiční náhled na svět, spolužákům za výbornou spolupráci. V neposlední řadě bych dále poděkoval všem pracovníkům KEEZ DFJP za ochotu a pomoc po celou dobu mého studia. Anotace Bakalářská práce je rozdělena na teoretickou a praktickou část. V teoretické části je popsána automobilová diagnostika, komunikace na sběrnici CAN, převodník STN1110 a vývojové prostředí LabVIEW. V praktické části je cílem této bakalářské práce vypracovat návrh převodníku dle doporučeného schématu výrobcem a na základě tohoto návrhu vytvořit přípravek, kterým bude možno sledovat komunikaci na sběrnici CAN v nákladních vozidlech, na kterých se dnes používá pro komunikaci protokol SAE J1939. -

OXYGEN Training CAN CAN-FD Flexray
THE MEASURABLE DIFFERENCE. OXYGEN Training CAN CAN-FD FlexRay © DEWETRON GmbH | June 21 PUBLIC 1 CAN CAN bus available on > TRION-CAN (2/4 buses) > TRION-2402-MULTI (1 bus) > CAN (Control Area Network) is a serial bus system and was > TRION-1802/1600-dLV (1 bus) initiated 1983 by BOSCH and is mainly used in the 21 June > TRION-1820-MULTI (1 bus) > TRION(3)-18x0-MULTI (1 bus) automotive industries > Differential data transmission, CAN-High, CAN-Low ref. to CAN-GND > High Speed CAN (1 Mbaud) for short distances and much data vs. | GmbH DEWETRON © Low Speed CAN (125 kBaud) for long distances and reduced data > Data: 0-8 times 8-bit 2 CAN – CHANNEL SETUP ① In case of TRION-CAN and TRION- 1802/1600-dLV, go to the channel setup ⑥ of the respective CAN channel ① ② In case of TRION-MULTI: CAN bus is 21 June available on AI 1; Turn AI 1 into CAN mode and enable the CAN bus at the bottom of the Channel List ③ Open the CAN channel setup afterwards ② ④ Select the baudrate of the CAN bus © DEWETRON GmbH | GmbH DEWETRON © ⑤ Select Termination True if no termination is applied at the end of the transmission line to apply a 120 Ohm resistance ⑥ If all settings are correct, the frame ④ preview will show the received message ⑤ and the included data bits; ③ ⑤ 3 CAN – CHANNEL SETUP ⑦ Load the proper dbc- or arxml-file ⑧ A channel selection dialog will open; Select either all channels or only certain channels to be decoded and recorded 21 June ⑨ The decoded channels will appear as separate channels in the Channel List ⑦ and contain a preview of the decoded ⑩ signal ⑨ More channels can be selected and decoded by reloading the dbc-file and ⑧ | GmbH DEWETRON © selecting additional channels ⑩ Channels can be deleted by pressing the Clear all button It is also possible to decode the CAN stream offline by recording only the raw CAN stream and perform the steps ⑦ and ⑧ during data analysis 4 CAN – SHOW ONLY ACTIVE MESSAGES ① If Show only active messages is selected, all available messages from the loaded dbc-file with the actual bus traffic will be filtered. -

WAGO-I/O-SYSTEM 750 CAN Gateway
WAGO-I/O-SYSTEM 750 CAN Gateway SAEJ1939 Sold & Serviced By: ELECTROMATE Toll Free Phone (877) SERVO98 Toll Free Fax (877) SERV099 www.electromate.com [email protected] WAGO-I/O-SYSTEM 750 CAN Gateway The compact, 12mm wide CAN gateway module provides a link between CAN networks and other popular fieldbuses such as MODBUS, EtherNet/IP, Profinet, and more. Supporting both the CAN 11 bit and 29 bit identifier protocols, this module can be configured as a CANopen or SAE J1939 master/ slave within a WAGO-I/O-SYSTEM node. Three operating modes offer additional flexibility for your control system strategy. • Mapped Mode – enables CAN telegrams to be generated directly from the process image or selectively copied from received telegrams, which can then be mapped in the PLC program. • Sniffer Mode – reads CAN telegrams with passive snooping without affecting the network. • Transparent Mode – sends and receives CAN telegrams as an active device on the network. Furthermore, module configuration is simplified via WAGO-I/O-CHECK or pre-engineered function blocks. • Use with couplers or controllers to leverage the Flexible and power of the WAGO-I/O-SYSTEM • Flexible gateway to popular fieldbuses: MODBUS, EtherNet/IP, Profibus, Profinet, etc. Configurable • One module supports CANopen and SAE J1939 protocols • User-friendly configuartion via WAGO-I/O- CHECK or pre-engineered function blocks Sold & Serviced By: ELECTROMATE Toll Free Phone (877) SERVO98 Toll Free Fax (877) SERV099 www.electromate.com [email protected] WAGO-I/O-SYSTEM 750 CAN Gateway Module features: • Gateway for all CAN protocols • 11 and 29 bit identifiers (CAN 2.0A and 2.0B) • Send/receive buffer • Six configurable CAN ID filters • Auto baud rate detection or manual configuration • Operating modes: Mapped, Sniffer, Transparent • Approvals: – Conformity Mark 1 – Shipbuilding (GL) – r UL 508 (pending) Part Number: 750-658 Types of Application Sold & Serviced By: ELECTROMATE Toll Free Phone (877) SERVO98 Toll Free Fax (877) SERV099 www.electromate.com [email protected]. -

Networking Heavy-Duty Vehicles Based on SAE J1939 from Parameter Group to Plug-And-Play Application
Networking Heavy-Duty Vehicles Based on SAE J1939 From Parameter Group to plug-and-play Application In networking ECUs in heavy-duty vehicles, it is the J1939 protocol that plays a key role. J1939 networks are based on the CAN bus (high-speed CAN per ISO11898); they are primarily used in powertrain and chassis components. The protocol creates a uniform basis for communication between electronic control units, and it supports the plug-and-play principle. Special J1939 tools and software components spare developers from needing to train in the details of the J1939 protocol, and they improve the quality of the development process. The J1939 protocol – founded in the USA and defined by the ardization aspects, J1939 gives OEMs sufficient freedom Society of Automotive Engineers (SAE) – serves above all for customized extension of communication. This is espe- to preserve a uniform perspective and uniform handling of cially important in promoting innovations, because no OEM the most common vehicle components of various vehicle wants to announce or discuss plans in working committees types and manufacturers. In this context, it is interesting to before their implementation. note certain distinct differences between the European and North-American heavy-duty vehicle markets. For ex- ISO Layers Model decouples the Application from ample, heavy-duty vehicle buyers in the USA have pre- Transmission Physics scribed to OEMs which components they need to install in From the perspective of the ISO/OSI network model, J1939 specific vehicles. In Europe, on the other hand, it is the is essentially based on the Application Layer (Layer 7), Net- OEMs who fully define the design of the entire vehicle, in- work Layer (Layer 3), Data Link Layer (Layer 2) and Physi- cluding the components and their configuration. -

SAMTEC Automotive Software & Electronics
SAMTEC Automotive Software & Electronics PRODUCT CATALOG 2016 AUTOMOTIVE www.samtec.de PUBLICATION DETAILS 2 CONTACT samtec automotive software & electronics gmbh Einhornstr. 10, D-72138 Kirchentellinsfurt - Germany Phone +49-7121-9937-0 Telefax +49-7121-9937-177 Internet www.samtec.de E-mail [email protected] DISCLAIMER The information contained in this catalog corresponds to the technical status at the time of printing and is passed on with the best of our knowledge. The information in this catalog is in no event a basis for warranty claims or contractual agreements concerning the described products and may especially not be deemed as warranty concerning the quality and durability pursuant to Sec. 443 German Civil Code. samtec automotive software & electronics gmbh reserves the right to make any alterations to this catalog without prior notice. The actual design of products may deviate from the information contained in the catalog if technical alterations and product improvements so require. In any cases, only the proposal made by samtec automotive software & electronics gmbh for a concrete application or product will be binding. All mentioned product names are either registered or unregistered trademarks of their respective owners. Errors and omissions excepted. This catalog has been made available to our customers and interested parties free of charge. It may not, in part or in its entirety, be reproduced in any form without our prior consent. All rights reserved. LEGAL NOTICE samtec automotive software & electronics gmbh Managing directors: René von Stillfried, Dr. Wolfgang Trier Registered office: Kirchentellinsfurt Date: March 2016 Commercial register: Stuttgart, HRB 224968 PREFACE Dear readers, 3 Many of you already know us! You deploy electronic control units, we provide you with the diagnostic solutions. -

Holger Zeltwanger the OSI Model
CAN Holger Zeltwanger A personal review and an outlook © CiA CAN The OSI model Text (application software) Vocabulary + phrases * Grammar rules (Translation services) Normally (Start and stop indications) not used in single- (Page numbering) segment networks (Routing) Character set Paper, pen, or laser-beam * Including “confirmation” and “encryption” procedures © CiA CAN First 11898 transceivers 15 of 35 is +16V. CAN_L and V members 6. Description of the MediumCAN_H Access Unit 6.1 Physical Medium Attachment Sublayer Specification (Transceiver) exhibited on See /3/. The maximum rating for V Galvanic isolation between the bus nodes is optional. the first CiA 6.2 Medium Dependent Interface Specification (Bus connector) joint booth 6.2.1 Electrical Parameters See /3/. The output voltage at pin 9 (external positive supply) shall be +7 V < V+ < +13 V at an output current of up to 100 mA (current consumption of module). Modules are not allowed to source current into this pin. The electrical parameters for pin 9 (V+) refer to the proposal of the working group "Physical Note: Layer". They are not yet agreed upon by the General Assembly of CAN in Automation. 6.2.2 Mechanical Parameters The connector used to plug electronic modules to the bus line is a 9-pin D-Sub connector according to /4/. Its pinning is fixed as follows Pin Signal Description 1 - Reserved 2 CAN_L CAN_L bus line (dominant low) 3 CAN_GND CAN Ground 4 - Reserved 5 (CAN_SHLD) Optional CAN Shield 6 (GND) Optional CAN Ground 7 CAN_H CAN_H bus line (dominant(dedicated high) for supply of transceiver and optocouplers, CANshow if galvanic isolation of the bus nodes applies) 8 - Reserved (error line) 9 (CAN_V+) Optional CAN external positive supply at Interkama 1992 CiA® 102 © CiA Each bus node has to provide a male connector, meeting the above-mentioned specification. -

Product Information Canbedded
CANbedded Product Information CANbedded Table of Contents 1 Solutions with CANb edded ..................................................................................................................................................... 4 1.1 CANbedded ................................................................................................................................................................................ 4 1.2 Advantages of CANbedded ...................................................................................................................................................... 4 1.3 Your Partner Right From the Start ......................................................................................................................................... 4 1.4 Uniform Solution ....................................................................................................................................................................... 4 2 CANbedded - Basic Software for CAN Communication ....................................................................................................... 4 2.1 Overview of Advantages: ......................................................................................................................................................... 5 2.2 Application Areas ...................................................................................................................................................................... 5 2.3 Functions................................................................................................................................................................................... -

Tecchhnical Man Uuaal
TTeecchhnniiccaall MMaannuuaall Absolute Singleturn Encoder Series M3658, M3678 Technical Manual Absolute Singleturn Encoder with SAE J1939 © Fritz Kübler GmbH Copyright Protection The contents of this documentation are protected by copyright © Fritz Kübler GmbH. The contents of this documentation may not be altered, expanded, reproduced nor circulated to third parties, without the prior written agreement of Fritz Kübler GmbH. Liability to modification without notice As a result of ongoing efforts to improve our products, we reserve the right to make changes at any time to technical information contained in the document to hand. Warranty Disclaimer Fritz Kübler GmbH provides no guarantee, neither tacit nor express, in respect of the whole manual (whether this applies to the original German text or to the English translation) and assumes no liability for any damage, neither direct nor indirect, however caused. Document information Revised 11‐2009 Fritz Kübler GmbH Schubertstr.47 78054 VS‐Schwenningen / Germany Tel. +49 (0) 7720‐3903‐0 Fax +49 (0) 7720‐21564 E‐Mail: [email protected] Internet: www.kuebler.com R.800.012 1-2 of 23 Technical Manual Absolute Singleturn Encoder with SAE J1939 Table of Contents 1 GENERAL ..................................................................... 1‐4 2 THE SAE J1939 SET OF PROFILES .................................. 2‐5 3 PARAMETER GROUPS (PG) ........................................... 3‐7 4 NETWORK MANAGEMENT .......................................... 4‐8 5 TRANSPORT PROTOCOLS ............................................. 5‐9 6 POWER SUPPLY AND CAN‐BUS CONNECTION ............. 6‐10 7 DEFAULT SETTINGS ON DELIVERY ............................... 7‐11 8 PROCESS DATA PGN ASSIGNMENTS .......................... 8‐12 9 SETUP PGN ................................................................ 9‐14 10 REQUEST _SETUP PGN ............................................. 10‐15 11 SETUP PARAMETER IN DETAIL .................................. 11‐16 12 LED STATES ............................................................. -
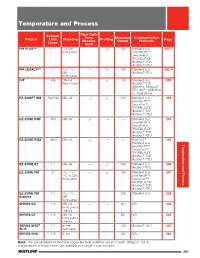
Controller Catalog (Section)
Temperature and Process Fiber Optic Control/ Temp. Maximum Communication Product Limit Mounting Measure- Profiling Output Protocols Page Loops ment 1 PM PLUS™ 1/1 /16 DIN — ✓ 15A Standard bus, 252-1 front panel EtherNet/IP™, DeviceNet™, PROFIBUS DP, Modbus® TCP, Modbus® RTU PM LEGACY™ 1/1 1/32, 1/16 — 1/32 15A Standard bus, 252-9 DIN Modbus® RTU front panel F4T 4/4 DIN-rail, — ✓ 12A Standard bus, 253 Flush mount Modbus® TCP (Ethernet), Modbus® RTU, SCPI, USB Host (2), USB device ® EZ-ZONE RM 152/192 DIN-rail — ✓ 15A Standard bus, 254 EtherNet/IP™, DeviceNet™, PROFIBUS DP, Modbus® TCP, Modbus® RTU EZ-ZONE RMF 8/0 DIN-rail ✓ — — Standard bus, 255 EtherNet/IP™, DeviceNet™, PROFIBUS DP, Modbus® TCP, Modbus® RTU ® EZ-ZONE RMZ 48/0 DIN-rail ✓ — — EtherCAT 255 Standard bus, Temperature and Process EtherNet/IP™, DeviceNet™, PROFIBUS DP, Modbus® TCP, Modbus® RTU EZ-ZONE ST 1/1 DIN-rail — ✓ 75A Standard bus, 256 Modbus® RTU 1 1 EZ-ZONE PM 2/1 /32, /16, — ✓ 15A Standard bus, 257 1/8, 1/4 DIN EtherNet/IP™, front panel DeviceNet™, PROFIBUS DP, Modbus® TCP, Modbus® RTU EZ-ZONE PM 1/1 1/32, 1/16 — — 15A Standard bus 258 Express DIN front panel SERIES CV 1/0 DIN-rail, — — 8A N/A 259 Front panel, chassis SERIES CF 1/0 DIN-rail, — — 8A N/A 262 Front panel, chassis SERIES EHG® 1/1 In-line/ — — 10A Modbus® RTU 265 SL10 Sub panel SERIES EHG 1/0 In-line — — 10A N/A 266 Note: The specifications in the table above are best available values in each category. -

SAE J1939 Serial Control and Communications Vehicle Network
SAE J1939 Serial Control and Communications Vehicle Network Presented by Wilfred Voss esd electronics, Inc. 525 Bernardston Road Greenfield, MA 01038 http://www.esd-electronics.us Download/View this presentation at: http://www.canseminar.com/Tutorials.html/ © esd electronics, Inc. • 525 Bernardston Road • Greenfield, MA 01301 Literature Literature on Controller Area Network, CANopen and SAE J1939 © esd electronics, Inc. • 525 Bernardston Road • Greenfield, MA 01301 Page 2 esd Product Line esd electronics provides: • CAN Hardware Interfaces – PCI, cPCI, VME, PMC, PC104, ISA, and more • CAN Gateways – USB, EtherNet, Bluetooth, IEEE488, and more • CAN Converters – CANopen, DeviceNet, Profibus, and more • CAN Embedded Controllers • Drivers and APIs for various operating systems • Free CAN Analyzer software – included with driver esd electronics, Inc. 525 Bernardston Road Greenfield, MA 01301 Tel.: 413-773-3170 Fax: 413-773-3171 http://www.esd-electronics-usa.com © esd electronics, Inc. • 525 Bernardston Road • Greenfield, MA 01301 What is SAE J1939 – General Aspects • Higher-layer protocol based on Controller Area Network (CAN) • Provides serial data communications between Electronic Control Units (ECU) in any kind of heavy duty vehicles. • Protocol features based on J1708 (RS485) + J1587 • Ingenious protocol design with very little protocol overhead • Driven by data, not myriad of functions as other HLPs • Takes full advantage of all CAN features • Detailed documentation only available through SAE © esd electronics, Inc. • 525 Bernardston Road • Greenfield, MA 01301 Page 4 SAE J1939 Applications J1939-based protocols are used in: • Diesel power-train applications • In-Vehicle networks for trucks and buses • Agriculture and forestry machinery (ISO 11783) • Truck-Trailer connections • Military vehicles (MiLCAN) • Fleet management systems • Recreational vehicles • Marine navigation systems (NMEA2000) © esd electronics, Inc. -

Absolute Encoders - Modular Bus Covers High Resolution, Blind Hollow Shaft Optical Single and Multiturn Encoders 18 Bit ST / 13 Bit MT
Absolute encoders - modular bus covers High resolution, blind hollow shaft Optical single and multiturn encoders 18 bit ST / 13 bit MT GBAMS, GBMMS Features – Encoder single- or multiturn / bus cover – Optical sensing method – Total resolution up to 31 bit – Blind hollow shaft ø12...ø15 mm – CANopen®/DeviceNet/EtherCAT/EtherNet-IP SAEJ1939/PROFINET/POWERLINK/Profibus/SSI – Cost-efficient mounting – Code continuity check optional by bus – Maximum resistant against magnetic fields GBMMS with modular bus cover Technical data - electrical ratings Technical data - mechanical design Voltage supply 10...30 VDC Size (flange) ø58 mm Reverse polarity protection Yes Shaft type ø12...15 mm (blind hollow shaft) Consumption w/o load ≤100 mA (24 VDC) Protection DIN EN 60529 IP 54, IP 65 (optional) Initializing time typ. 250 ms after power on Operating speed ≤6000 rpm (mechanical) Interfaces CANopen®, DeviceNet, ≤6000 rpm (electric) EtherCAT, EtherNet/IP, Profibus, Starting acceleration ≤1000 U/s² PROFINET, POWERLINK, Starting torque ≤0.015 Nm (+25 °C) SAE J1939, SSI Rotor moment of inertia 20 gcm² Device adress Rotary switches in bus cover Materials Housing: aluminium Steps per revolution ≤262144 / 18 bit Flange: aluminium Absolute accuracy ±0.01 ° Bus cover: zinc die-cast Sensing method Optical Operating temperature -25...+85 °C Code Binary -40...+85 °C (optional) Code sequence CW/CCW programmable Relative humidity 95 % non-condensing Interference immunity DIN EN 61000-6-2 Resistance DIN EN 60068-2-6 Vibration 10 g, 16-2000 Hz Emitted interference DIN EN 61000-6-4 DIN EN 60068-2-27 Programmable Steps per revolution Shock 200 g, 6 ms parameters Number of revolutions Weight approx.