Commercial Call-Off Contract Schedule 2.1
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Create, Edit and Review Content with the Light-Weight HP Slate 500 Tablet PC, Offering a Full-Featured Windows-Based Experience and Touch Capabilities
HP Slate 500 Tablet PC The Right Business Touch Create, edit and review content with the light-weight HP Slate 500 Tablet PC, offering a full-featured Windows-based experience and touch capabilities. Windows®. Life without Walls TM. HP recommends Windows 7. The HP Slate 500 Tablet PC is ideal for those who use custom The integrated VGA webcam on the front of the HP Slate 500 applications built for the familiar and secure Windows® enables video conferencing,7 while the 3MP camera on the environment. It also enables employees with jobs that back of the Slate 500 can be used for still-image and video frequently take them away from a traditional desk to stay capture. connected and remain productive. Stay connected Touch it or write it Cut the cords and stay connected. With Wi-Fi CERTIFIED™ Get your work done more intuitively. The capacitive multi-touch WLAN, you can send and receive e-mails or access the display of the HP Slate 500 lets you navigate on the screen internet—at work, at home and at your favorite hotspots.2 with the touch of your fingers. Use the HP Slate Digital Pen and Plus, the Bluetooth® technology provides wireless short-range Evernote® software to handwrite e-mail messages and take communication or connectivity between other Bluetooth notes easily. devices such as printers, mice and headsets. Stay productive Expand your workspace With a starting weight of only 1.5 lb (0.68 kg), the HP Slate Rest the HP Slate 500 in the HP Slate Dock and gain a 500 enables professionals to check e-mail, browse the desktop experience with two additional USB 2.0 ports and an Internet,2 read and edit documents, presentations, HDMI port. -

The Effects of the Size and Weight of a Mobile Device on an Educational Game
The effects of the size and weight of a mobile device on an educational game 1 1 1,* 2 2 David Furió , Santiago González-Gancedo , M.-Carmen Juan , Ignacio Seguí , María Costa 1 Instituto Universitario de Automática e Informática Industrial, Universitat Politècnica de València, Camino de Vera, s/n. 46022 Valencia, Spain * e-mail: [email protected], [email protected] 2 AIJU, Ibi, Alicante, Spain Abstract In this paper, we present an educational game for an iPhone and a Tablet PC. The main objective of the game was to reinforce children’s knowledge about the water cycle. The game included different interaction forms like the touch screen and the accelerometer and combined AR mini-games with non-AR mini-games for better gameplay immersion. The main differences between the two devices were screen size and weight. A comparative study to check how these differences affect different aspects was carried out. Seventy-nine children from 8 to 10 years old participated in the study. From the results, we observed that the different characteristics (screen size and weight) of the devices did not influence the children’s acquired knowledge, engagement, satisfaction, ease of use, or AR experience. There was only a statistically significant difference for the global score in which the iPhone was scored higher. We would like to highlight that the scores for the two devices and for all the questions were very high with means of over 4 (on a scale from 1 to 5). These positive results suggest that games of this kind could be appropriate educational games and that the mobile device used may not be a decisive factor. -
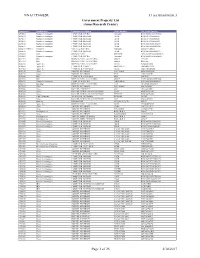
Attachment 3 Page 1 of 25 2/10/2017
NNA17554082R J.1(a) Attachment 3 Government Property List (Ames Research Center) Equipment # Manufacturer Equipment Description Model Number Mfr. Serial Number 2390683 Mazda Technologies COMPUTER, MICRO Tornado6 BTO16021075616500035 1630572 Mazda Technologies COMPUTER, SERVER 1243R BTO812764380800524 1630571 Mazda Technologies COMPUTER, SERVER 1243R BTO812764380800525 1630570 Mazda Technologies COMPUTER, SERVER 1243R BTO812764380800523 2580842 Mazda Technologies COMPUTER, SERVER 1245R BTO1206915856100279 2580841 Mazda Technologies COMPUTER, SERVER 1245R BTO1206915852900278 2580840-VM010 Unknown VIRTUAL MACHINE Unknown 2580840-VM010 2580840 Mazda Technologies COMPUTER, SERVER 1245R BTO1206915852900277 2405303 Seiki DISPLAY UNIT SM40UNP 1SY152700150820D000676 2390684 Mazda Technologies COMPUTER, MICRO Tornado6 BTO16021075616500038 2074375 Dell DISPLAY UNIT, FLAT PANEL 2000FP 1C91004 2074372 Dell DISPLAY UNIT, FLAT PANEL 2000FP IBN105L 3026776 Apple, Inc. DISPLAY UNIT, FLAT PANEL A1316 W82052U56JL 1630634 Apple, Inc. COMPUTER, TABLET MB294LL/A GB024D6NZ3A 1631469 Apple, Inc. COMPUTER, PORTABLE A1286 C02G73HJDRJM 3029439 Cisco SWITCH, ETHERNET WS-C6509E SMG1116N0AB 3029434 Cisco SWITCH, ETHERNET 4948 FOX11040EPE 3028548 Dell COMPUTER, PORTABLE M90 6HJJXB1 3001695 Dell DISPLAY UNIT, FLAT PANEL 2000FP CN09E2494663339F084L 2290190 Mazda Technologies COMPUTER, MICRO TORNADO5 BTO1402986493000010 2104176 Samsung DISPLAY UNIT, FLAT PANEL 181T GH18H4KT602811T 3031474 Cisco SWITCH, ETHERNET WS-C4900M JAE1310544C 3030346 Cisco ROUTER, ETHERNET 2821 -

Zerohack Zer0pwn Youranonnews Yevgeniy Anikin Yes Men
Zerohack Zer0Pwn YourAnonNews Yevgeniy Anikin Yes Men YamaTough Xtreme x-Leader xenu xen0nymous www.oem.com.mx www.nytimes.com/pages/world/asia/index.html www.informador.com.mx www.futuregov.asia www.cronica.com.mx www.asiapacificsecuritymagazine.com Worm Wolfy Withdrawal* WillyFoReal Wikileaks IRC 88.80.16.13/9999 IRC Channel WikiLeaks WiiSpellWhy whitekidney Wells Fargo weed WallRoad w0rmware Vulnerability Vladislav Khorokhorin Visa Inc. Virus Virgin Islands "Viewpointe Archive Services, LLC" Versability Verizon Venezuela Vegas Vatican City USB US Trust US Bankcorp Uruguay Uran0n unusedcrayon United Kingdom UnicormCr3w unfittoprint unelected.org UndisclosedAnon Ukraine UGNazi ua_musti_1905 U.S. Bankcorp TYLER Turkey trosec113 Trojan Horse Trojan Trivette TriCk Tribalzer0 Transnistria transaction Traitor traffic court Tradecraft Trade Secrets "Total System Services, Inc." Topiary Top Secret Tom Stracener TibitXimer Thumb Drive Thomson Reuters TheWikiBoat thepeoplescause the_infecti0n The Unknowns The UnderTaker The Syrian electronic army The Jokerhack Thailand ThaCosmo th3j35t3r testeux1 TEST Telecomix TehWongZ Teddy Bigglesworth TeaMp0isoN TeamHav0k Team Ghost Shell Team Digi7al tdl4 taxes TARP tango down Tampa Tammy Shapiro Taiwan Tabu T0x1c t0wN T.A.R.P. Syrian Electronic Army syndiv Symantec Corporation Switzerland Swingers Club SWIFT Sweden Swan SwaggSec Swagg Security "SunGard Data Systems, Inc." Stuxnet Stringer Streamroller Stole* Sterlok SteelAnne st0rm SQLi Spyware Spying Spydevilz Spy Camera Sposed Spook Spoofing Splendide -

HP Slate 500
HP Slate 500 Maintenance and Service Guide © Copyright 2010 Hewlett-Packard Development Company, L.P. Bluetooth is a trademark owned by its proprietor and used by Hewlett- Packard Company under license. Intel is a trademark of Intel Corporation in the U.S. and other countries. Microsoft, Windows, and Windows Vista are U.S. registered trademarks of Microsoft Corporation. SD Logo is a trademark of its proprietor. The information contained herein is subject to change without notice. The only warranties for HP products and services are set forth in the express warranty statements accompanying such products and services. Nothing herein should be construed as constituting an additional warranty. HP shall not be liable for technical or editorial errors or omissions contained herein. First Edition: September 2010 Document Part Number: 633016-001 Safety warning notice WARNING! To reduce the possibility of heat-related injuries or of overheating the device, do not place the device directly on your lap or obstruct the device air vents. Use the device only on a hard, flat surface. Do not allow another hard surface, such as an adjoining optional printer, or a soft surface, such as pillows or rugs or clothing, to block airflow. Also, do not allow the AC adapter to contact the skin or a soft surface, such as pillows or rugs or clothing, during operation. The device and the AC adapter comply with the user-accessible surface temperature limits defined by the International Standard for Safety of Information Technology Equipment (IEC 60950). iii iv Safety warning notice Table of contents 1 Product description ........................................................................................................... 1 2 External component identification .................................................................................... -

Hot Promotion! April Business Boosters
HPSupporting our Channel PartnerPartner Community with Product Information + News On Promotions, EventsWeekly & Training 12 April 2011 Issue #131 HP PARTNER HP IPG PSG ESSN ANNOUNCEMENTS SERVICES SOFTWARE 1 of 12 CLOSE CONTACT US HPPW PRINT IT LEARNING NETWORKING Contents “Discover with HP Software” Hot promotion! April Business Boosters - “Discover with HP Software” – Las Vegas June 2011 $1 upgrades! – Las Vegas June 2011 1 Hot promotion! April Business Boosters - Amongst the chaos and energy, plenty of fun awaits you: including exclusive HP is very excited to announce an exciting new end-user promotion that is $1 upgrades! 1 attendance to HP Discover – our largest EVER customer facing event in history! guaranteed to give your customers a boost this April! We are offering four (4) The first-ever HP DISCOVER will showcase game-changing innovations in incredible opportunities to upgrade size, capacity, and specifications for just $1. Enterprise Servers and These offers will be available from 1 – 30 April 2011. Storage Networking software, hardware, services, and networking that will shape your IT for the next decade. In addition to this exciting opportunity we have a great itinerary Announcing “Discover with HP Software” Offer 1: Purchase an HP ProBook 6550b Series Notebook PCs get an HP 90W – Las Vegas June 2011 2 planned including fantastic shows and tours. Basic Docking Station for just $1 A win for intelligent power [APJ] 3 Personal Systems Group Offer 2: HP Pro 4000 SFF Desktop PC with Intel® Celeron™ E3400 Processor^, Hot promotion! April Business Boosters - 2GB DDR3 Memory, 250GB Hard Drive. RRP $699. For $1 extra, upgrade to $1 upgrades! 4 HP Pro 4000 Pro SFF Desktop PC with Intel® Celeron™ E6700 Processor^, 4GB Introducing the new HP ProBook b series DDR3 Memory, 320GB Hard Drive notebooks! 5 Imaging and Printing Group Offer 3: HP Pro 4000 SFF Desktop PC with Intel® Core™ 2 Duo E7600 Innovative HP LaserJet Product Line Up 6 Processor^, 4GB DDR3 Memory, 320GB Hard Drive. -

Usability of Tablet Computers to Facilitate Instant Written Feedback
University of Huddersfield Repository Prigmore, Martyn and Gledhill, Duke Usability of tablet computers to facilitate instant written feedback Original Citation Prigmore, Martyn and Gledhill, Duke (2015) Usability of tablet computers to facilitate instant written feedback. Innovation in Teaching and Learning in Information and Computer Sciences (ITALICS). ISSN 1473-7507 This version is available at http://eprints.hud.ac.uk/id/eprint/19904/ The University Repository is a digital collection of the research output of the University, available on Open Access. Copyright and Moral Rights for the items on this site are retained by the individual author and/or other copyright owners. Users may access full items free of charge; copies of full text items generally can be reproduced, displayed or performed and given to third parties in any format or medium for personal research or study, educational or not-for-profit purposes without prior permission or charge, provided: • The authors, title and full bibliographic details is credited in any copy; • A hyperlink and/or URL is included for the original metadata page; and • The content is not changed in any way. For more information, including our policy and submission procedure, please contact the Repository Team at: [email protected]. http://eprints.hud.ac.uk/ Usability of tablet computers to facilitate instant written feedback Authors and affiliations: Dr Martyn Prigmore, University of Huddersfield Dr Duke Gledhill, University of Huddersfield Type of Article: Research article Keywords: Feedback; tablet computer; usability; handwriting recognition Word count: 4767 Corresponding author: Dr Martyn Prigmore School of Computing and Engineering University of Huddersfield Queensgate Huddersfield HD1 3DH Tel: 01484 472083 Email: [email protected] Copyright permissions: None required Signed contributors’ agreement sent: Yes Abstract We undertake a usability evaluation of tablet computers and handwriting capture and recognition software for use in the classroom. -

Media Tablets: 2010 to 2014 Analyzing How Media Tablets Will Change Personal Computing
Media Tablets: 2010 to 2014 Analyzing How Media Tablets will Change Personal Computing CONTENTS REPORT HIGHLIGHTS EXECUTIVE SUMMARY MARKET OVERVIEW PERSONAL COMPUTERS (PCS) Desktop PCs Definition and Examples Market Size and Growth Prospects Notebooks Definition and Examples Market Size and Growth Prospects Price Competition Cannibalization Mechanism 1 Cannibalization Mechanism 2 Ultrathin Notebooks Tablet PCs Definition and Examples Market Size and Growth Prospects NETBOOKS Definition and Examples Market Size and Growth Prospects MOBILE PHONES Smartphones Non-Smartphones MOBILE INTERNET DEVICES (MIDs) Definition Analysis INTERNET TABLETS SMARTBOOKS SMARTPADS EREADERS Definition Market Size and Growth Prospects MEDIA TABLETS DEFINTION USE CASES APPLICATIONS Definition Browser Model Application Model IMPLICATIONS FOR VENDORS MARKET SIZING AND GROWTH PROSPECTS VENDOR PROFILES AND ANALYSIS APPLE: iPAD Company Overview Corporate Transformation Basis for Growth Fortuitous Timing Point of Inflexion Multiple Inflexion Points Ability to Execute Incumbent Media Companies: Common Requirements ‘Vendor Selection' Criteria Case Study: iPhone and AppStore Background Quality User Experience: Vertical Integration Powerful Business Strategy: Platform Approach Business-Critical Market ‘360-degree' Platform Model Increased Stakes for Market Entry Superior, Differentiated User Experience Critical Mass: Advertisers, Online Brands, Publishers and Content Providers iPad Specifications Product Variants and Pricing User Experience eReading Quality: Clearly Differentiated, -

EASY USE Lagerprodukte Aktualisiert Donnerstag, Den 19
EASY USE Lagerprodukte Aktualisiert Donnerstag, den 19. März 2020 um 16:07 Uhr EASY USE - Produkt-/ Lagerliste Stand: 15.03.2020 ( Preisanpassungen vorbehalten ) Alle Preise inkl. MwSt., zzgl. Versand Aktuelle Lager-Artikel - bestellbar per Mail an [email protected] oder Tel.: 08551 9139319 Artikelnr. Kurztext Matchcode HPDOCKU565 HP USB Docking Cradle f. Jornada 560 Serie (565,568) mit USB-Kabel F2903A FXC371BATCE Batteriefachabdeckung f. iPAQ rx3715 verwendet mit extended AkkuFXC371BATCE FXC65COVT HP Screen Protector f. iPAQ hw6000 Serie (hw6510, hw6515, hw6910, 398326-001 hw6915) HP39XACR HP Netzteil f. iPAQ h3800, h3900, h1900, h2200, h6300, hx4700, 389145-021 hx2000, rz1700, 253628-021 rx3700, hw6000, h5000 FXC221IRC Ersatzteil : Abdeckung schwarz über Infrarot Port f. iPAQ h2200 FXC221IRCSerie (h2210, h2215) HP651DOCK HP Docking Cradle USB f. hw6000 Serie (hw6510, hw6515, hw6910, 383749-001 hw6915) 366854-005 370526-007 1 / 94 EASY USE Lagerprodukte Aktualisiert Donnerstag, den 19. März 2020 um 16:07 Uhr RPL19XBAT HP Standard Akku f. iPAQ h1900 Serie (h1910,h1930,h1940) 900mAh FA114A Li-Ion 311315-B21 311340-001 311349 HP170PENS HP 3er Pack Stifte f. iPAQ hx2000, rz1710, rx3715, hx4700, hw6000 FA261A Serien 367202-001 FXCHX241BATCE Batteriefachabdeckung f. iPAQ hx2000 Serie verwendet mit extended FXCHX241BATCE Akku HPGLANUSB3A HP USB 3.0 kompatibel 2.0 an Gigabit LAN RJ45 Adapter N7P47AA 829834-001 829941-001 HPSP65BLTC HP Gürtelhalterung mit Clip schwarz f. iPAQ hw6000 Serie (hw6510, 383744-001 hw6515, hw6910, hw6915) HPNB4720KITL HP Tastatur international / US Englisch f. ProBook4720s 598692-B31 HPSP65HEADP HP Headphone mit Mikrophonef. hw6000 Serie + Voice Messenger 383748-001 514 445667-001 2 / 94 EASY USE Lagerprodukte Aktualisiert Donnerstag, den 19. -

Resolution Declaring Property Surplus
Resolution # 2019-032 RESOLUTION DECLARING MISCELLANEOUS PERSONAL PROPERTY SURPLUS WHEREAS the below-described property is no longer necessary, useful or suitable for municipal purposes NOW, THEREFORE, BE IT RESOLVED that the following property be declared surplus and disposed of according to state statutes, including release to insurance company due to total loss: 2019 Annual City Auction AIRPORT – Items on Airport Resolution 2019-03 & 2019-05 HP ELITE DESK 800 System# S1855 2UA41626H9 HP ELITE DESK 800 System# S1856 2UA41626H8 22" HP Computer Monitor 22" Samsung Computer Monitor 15" Gateway Computer Monitor Smart UPS-1500 SUA1500RM2U AS0737232070 Smart UPS-1500 SUA1500RM2U AS0349310734 Smart UPS-1500 SUA1500RM2U Minuteman UPS 3-Ring Binders-Assorted Sizes Assorted Office Desks 2003 Chevrolet Tahoe 1GNEK13V03J246310 Condition: Needs a Transmission Mileage: Unknown-Cluster won't light up Brother Inkjet Printer LC75/LC71 Series MFC-J430W Assorted Interior Doors Slotted Display Wall Boards Assorted Wall Tiles Assorted Floor Tiles Assorted Rolls of Wall Paper Pallet of Stone Lounge Chairs - Used 47" Monitors (Qty 20)-Not working Small Display Cabinets Outdoor Display Lights (Qty 4) AIR QUALITY (708) 1 2002 Dodge Durango VIN #1B8HS38N52F172728 CIVIC CENTER (913) 1993 Ford Ranger – CTY1400 Vin number 1FTCR14U5PTA45398 (does not run) Walk behind mower (does not run) 55 Theater Lights 16 Work Lights Pallet fork with Stinger 1- JITAI Xtreme Scooter (does not run) 19 – Electric Hand Dryers 3 – Display Cabinets 5’ wide x 56” tall 1 – Six Burner -

Mitchell Technical College July 2021 Surplus Items – Sealed Bid Auction List
Mitchell Technical College July 2021 Surplus Items – Sealed Bid Auction List The following items are up for sealed bid by the Mitchell Technical College. Bids should be submitted in a sealed envelope with the item number and description of all item(s) you are bidding on plainly written on the outside. Inside the envelope should include the same information including the quantity of items and price as well as bidder’s name, address and phone number. (Envelope can contain multiple bids) Bids may be dropped off or mailed to: Mitchell Tech Attn. Business Office 1800 East Spruce Street Mitchell, SD 57301 Bids will be accepted until 10:00 AM Wednesday, July 28th, 2021 at which time they will be opened in a public bid award meeting at the address listed above. Information on the items included in this sealed bid auction can be requested from the the Mitchell Tech campus by contacting the Business Office at 605.995.3022. Successful bidders will have 5 days to remove equipment from the Mitchell Tech Campus. All items included in this list have or will be declared surplus prior to the date of the bid opening. Mitchell Tech reserves the right to remove any items from the sale up to and including the date of bid opening. Item # Quantity Item/Description Automotive Items 1 (1) 2013 Chrysler 200 LX - 161,370 miles 2 (1) coats tire machine - manual 3 (1) blue tire machine - works only 1 direction 4 (1) blue tire balancer - works, but missing some parts 5 (1) Overhead Gantry Homemade 14x 14 with 2 ton chain hoist 6 (4) AGCO Rogator Tires & rims - 380/90R46 -
Launching Efforts Needed for a High-Tech Product
LAUNCHING EFFORTS NEEDED FOR A HIGH-TECH PRODUCT PhD Student Lavinia DOVLEAC Transilvania University of Brasov, Romania Email: [email protected] Abstract: This paper aims the difficult problem of creating new product concepts in the area of high-technology and innovation. Because of scientific discoveries and impressive development of technology, many companies compete for market supremacy on the technological innovations market. In a global market, which is currently in an economic and financial crisis, consumers make a new hierarchy of priorities in terms of expenditure and consumption. Therefore, companies that create new products must be very careful about 2 aspects, so the new product may not become a failure: the products positioning on the market and the target group which they address to. This paper belongs to the marketing area by bringing into discussion theoretical concepts, by analyzing the stages crossed by a company in the process of launching a new high- tech product and crossing the abyss in the product adoption process by consumers. Key words: high-tech product, product adoption process, launching process, product lifecycle, innovators, PC tablet Introduction innovations of the past 30 years, made This paper aims to approach in a by Knowledge @ Wharton magazine theoretically and practically manner the (www.wall-street.ro), are included many main aspects of launching a new high- products or services using advanced tech product. There will be analyzed technology: the Internet, laptop, mobile one by one all the stages of the telephony, fiber optics, digital photo or launching process of a new product, ATM. Industries with "advanced taking as example an Apple product: the technology" use intensively research iPad.