Technical Report RHUL–ISG–2021–2 10 March 2021
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Recent Developments in Cybersecurity Melanie J
American University Business Law Review Volume 2 | Issue 2 Article 1 2013 Fiddling on the Roof: Recent Developments in Cybersecurity Melanie J. Teplinsky Follow this and additional works at: http://digitalcommons.wcl.american.edu/aublr Part of the Law Commons Recommended Citation Teplinsky, Melanie J. "Fiddling on the Roof: Recent Developments in Cybersecurity." American University Business Law Review 2, no. 2 (2013): 225-322. This Article is brought to you for free and open access by the Washington College of Law Journals & Law Reviews at Digital Commons @ American University Washington College of Law. It has been accepted for inclusion in American University Business Law Review by an authorized administrator of Digital Commons @ American University Washington College of Law. For more information, please contact [email protected]. ARTICLES FIDDLING ON THE ROOF: RECENT DEVELOPMENTS IN CYBERSECURITY MELANIE J. TEPLINSKY* TABLE OF CONTENTS Introduction .......................................... ..... 227 I. The Promise and Peril of Cyberspace .............. ........ 227 II. Self-Regulation and the Challenge of Critical Infrastructure ......... 232 III. The Changing Face of Cybersecurity: Technology Trends ............ 233 A. Mobile Technology ......................... 233 B. Cloud Computing ........................... ...... 237 C. Social Networking ................................. 241 IV. The Changing Face of Cybersecurity: Cyberthreat Trends ............ 244 A. Cybercrime ................................. ..... 249 1. Costs of Cybercrime -

HSBC Investdirect Plus Terms & Conditions
C M Y K HSBC InvestDirect Plus PMS ??? PMS ??? PMS ??? PMS ??? Sharedealing and Investment Non-printing Terms and Conditions Colours Non-print 1 Non-print 2 These terms are effective for all InvestDirect JOB LOCATION: PRINERGY 3 Plus customers on and from 13 January 2018. HSB-MCP49730.indd 1 28/12/2017 10:08 2 Part F – Ending the Service 47 Contents Page Section 1 – How you end the Service 47 Introduction 3 Section 2 – How we end the Service 48 Glossary 4 Section 3 – Set-off (using money in one account to meet a debt on another account) 50 Part A – Introducing the Service 8 Section 4 – Dormancy 51 Section 1 – Protecting yourself 8 General Information 52 Section 2 – Contacting you 8 Annex A: Important information about Investment dealing 54 Part B – Your Investment Account 9 Annex B: Important information about using our website 55 Section 1 – Key features of Investment dealing 9 Annex C: Best Execution Disclosure Statement 56 Section 2 – Dealing in Investments 11 Annex D: Our Conflicts of interest policy in relation to our Investment services 58 Section 3 – Settling orders 13 Need to contact us? 59 Section 4 – Best Execution 15 Section 5 – Operating your Investment Account 16 Section 6 – Corporate Actions 19 Section 7 – Tax and reporting of income 21 Introduction Part C – Your Cash Account 23 This document sets out the general terms and conditions which govern the HSBC InvestDirect Plus Service (the Service) we provide to you. It may be supplemented by other documents including: Section 1 – Key features of your Cash Accounts 23 • the Key Features Document and the Rates and Fees Page; Section 2 – Making payments from your Cash Account 23 • our Online Banking Terms and Conditions; Section 3 – Domestic payments 27 • a Trading Reserve Facility Letter; and Section 4 – International payments 28 • documents confirming any other additional items and conditions we introduce in accordance Section 5 – Receiving money into your Cash Account 29 with the change provisions set out elsewhere in this document. -

FOI6236-Information Provided Annex A
FRN Firm Name Status (Current) Dual Regulation Indicator Data Item Code 106052 MF Global UK Limited Authorised N FSA001 FSA002 110134 CCBI METDIST GLOBAL COMMODITIES (UK) LIMITED Authorised N FSA001 FSA002 113942 Gain Capital UK Limited Authorised N FSA001 FSA002 113980 Kepler Cheuvreux UK Limited Authorised N FSA001 FSA002 114031 J.P. Morgan Markets Limited Authorised N FSA001 FSA002 114059 IG Index Limited Authorised N FSA001 FSA002 114097 Record Currency Management Limited Authorised N FSA001 FSA002 114120 R.J. O'Brien Limited Authorised N FSA001 FSA002 114159 Berkeley Futures Ltd Authorised N FSA001 FSA002 114233 Sabre Fund Management Ltd Authorised N FSA001 FSA002 114237 GF Financial Markets (UK) Limited Authorised N FSA001 FSA002 114239 Sucden Financial Limited Authorised N FSA001 FSA002 114265 Stockdale Securities Limited Authorised N FSA001 FSA002 114294 Man Investments Ltd Authorised N FSA001 FSA002 114318 Whitechurch Securities Limited Authorised N FSA001 FSA002 114324 Bordier & Cie (UK) PLC Authorised N FSA001 FSA002 114354 Thesis Asset Management Limited Authorised N FSA001 FSA002 114402 Wilfred T. Fry (Personal Financial Planning) Limited Authorised N FSA001 FSA002 114428 Maunby Investment Management Ltd Authorised N FSA001 FSA002 114432 Investment Funds Direct Limited Authorised N FSA001 FSA002 114503 Amundi (UK) Ltd Authorised N FSA001 FSA002 114563 Richmond House Investment Management Limited Authorised N FSA001 FSA002 114617 Birchwood Investment Management Limited Authorised N FSA001 FSA002 114621 IFDC Ltd Authorised N -
Mcafee Labs Threats Report August 2014
McAfee Labs Threats Report August 2014 Heartbleed Heartbleed presents a new cybercrime opportunity. 600,000 To-do lists The Heartbleed vulnerability Lists of Heartbleed-vulnerable exposed an estimated 600,000 websites are helpful to users but websites to information theft. can also act as “to-do” lists for cyber thieves. Unpatched websites Black market Despite server upgrades, many Criminals continue to extract websites remain vulnerable. information from Heartbleed- vulnerable websites and are selling it on the black market. McAfee Phishing Quiz Phishing continues to be an effective tactic for infiltrating enterprise networks. Average Score by Department (percent of email samples correctly identified) Only 6% of all test takers correctly 65% identified all ten email samples as phishing or legitimate. 60% 80% 55% of all test takers fell for at least one of the seven phishing emails. 50% 88% of test takers in Accounting & 0 Finance and HR fell for at least one of the seven phishing emails. Accounting & Finance Human Resources Other Departments The McAfee Phishing Quiz tested business users’ ability to detect online scams. Operation Tovar During Operation Tovar—The Gameover Zeus and CryptoLocker takedown: For CryptoLocker For Gameover Zeus more than 125,000 more than 120,000 domains were blocked. domains were sinkholed. Since the announcement of Operation Tovar: 80,000 times Copycats ****** McAfee Stinger, a free ****** are on the rise, creating tool that detects and ****** new ransomware or removes malware financial-targeting (including Gameover Zeus malware using the leaked and CryptoLocker), was Zeus source code. downloaded more than 80,000 times. McAfee joined global law enforcement agencies and others to take down Gameover Zeus and CryptoLocker. -

Consolidated Approved Company List
Consolidated approved company list CONSOLIDATED APPROVED COMPANY LIST CONSOLIDATED APPROVED COMPANY NORMS STATE INSTITUTE ACTION UNIQUE COMPANY LIST CATEGORY ID CODE 3M INDIA LIMITED ELITE E00001 ABB INDIA LIMITED ELITE E00519 ACCENTURE SOLUTIONS PRIVATE ELITE EXCEPTION CATEGORY S05819 LIMITED CHANGE ADANI ENTERPRISES LIMITED ELITE E00002 (FORMERLY ADANI EXPORTS LIMITED) ADANI PORTS AND SPECIAL ECONOMIC ELITE E00003 ZONE LIMITED ADITYA BIRLA FINANCE LIMITED ELITE E00006 ADITYA BIRLA FINANCIAL SERVICES ELITE E00007 GROUP ADITYA BIRLA GROUP POWER PROJECTS ELITE E00008 ADITYA PHARMACARE PRIVATE LIMITED ELITE NAME E00011 (formerly ADITYA PHARMA PRIVATE CHANGE LIMITED) AKZO NOBEL INDIA LIMITED ELITE E00013 ALKALOIDA CHEMICAL COMPANY ZRT. ELITE E00014 ALKEM LABORATORIES LIMITED ELITE E00015 ALLAHABAD BANK ELITE E00016 AMARA RAJA BATTERIES LIMITED ELITE E00020 AMAZON DEVELOPMENT CENTRE (INDIA) ELITE CATEGORY S00220 PRIVATE LIMITED CHANGE AMBUJA CEMENTS LIMITED ELITE E00021 AMDOCS DEVELOPMENT CENTER INDIA ELITE CATEGORY S00230 LLP CHANGE AMERICAN EXPRESS(INDIA) PRIVATE ELITE CATEGORY S00236 LIMITED CHANGE ANDHRA BANK ELITE E00022 ANZ OPERATIONS AND TECHNOLOGY ELITE CATEGORY S00280 PRIVATE LIMITED CHANGE APOLLO HOSPITALS ENTERPRISE ELITE E00023 LIMITED CATEGORY S05823 ARVIND LIMITED ELITE CHANGE CATEGORY P01165 ASEA BROWN BOVERI(PABBL) ELITE CHANGE ASHOK LEYLAND LIMITED ELITE E00025 ASIAN PAINTS LIMITED ELITE E00026 ASSOCIATED BUILDING COMPANY ELITE E00027 ASSOCIATED CEMENT COS LIMITED ELITE E00028 (ACC LIMITED) ATOS INDIA PRIVATE LIMITED ELITE -

Exchange Council Election Eurex Deutschland Preliminary Voter List – As of 16 August 2019
Exchange Council Election Eurex Deutschland Preliminary Voter List – as of 16 August 2019 Voter group 1a cooperative credit institutions Company State DZ BANK AG Deutsche Zentral-Genossenschaftsbank Germany Page - 1 - Exchange Council Election Eurex Deutschland Preliminary Voter List – as of 16 August 2019 Voter group 1b credit institutions under public law Company State Bayerische Landesbank Germany DekaBank Deutsche Girozentrale Germany Hamburger Sparkasse AG Germany Kreissparkasse Köln Germany Landesbank Hessen-Thüringen Girozentrale Germany Landesbank Saar Germany Norddeutsche Landesbank - Girozentrale Germany NRW.BANK Germany Sparkasse Pforzheim Calw Germany Page - 2 - Exchange Council Election Eurex Deutschland Preliminary Voter List – as of 16 August 2019 Voter group 1c other credit institutions Company State ABN AMRO Bank N.V. Netherlands ABN AMRO Clearing Bank N.V. Netherlands B. Metzler seel. Sohn & Co. KGaA Germany Baader Bank Aktiengesellschaft Germany Banca Akros S.p.A. Italy Banca IMI S.p.A Italy Banca Sella Holding S.p.A. Italy Banca Simetica S.p.A. Italy Banco Bilbao Vizcaya Argentaria S.A. Spain Banco Comercial Português S.A. Portugal Banco Santander S.A. Spain Bank J. Safra Sarasin AG Switzerland Bank Julius Bär & Co. AG Switzerland Bank Vontobel AG Switzerland Bankhaus Lampe KG Germany Bankia S.A. Spain Bankinter Spain Banque de Luxembourg Luxemburg Banque Lombard Odier & Cie SA Switzerland Banque Pictet & Cie SA Switzerland Barclays Bank Ireland Plc Ireland Barclays Bank PLC United Kingdom Basler Kantonalbank Switzerland Berner Kantonalbank AG Switzerland Bethmann Bank AG Germany BNP Paribas United Kingdom BNP Paribas (Suisse) SA Switzerland BNP Paribas Fortis SA/NV Belgium BNP Paribas S.A. Niederlassung Deutschland Germany BNP Paribas Securities Services S.C.A. -
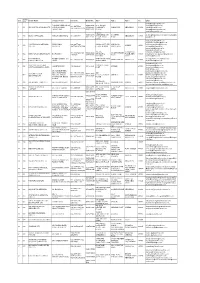
S.No. Broker Code Broker Name Contact Person Phone No. Mobile
Broker S.no. Broker Name Contact Person Phone No. Mobile No. Add 1 Add 2 Add 3 Pin Email Code [email protected]; RUCHIKA RAINA SINGH, 9899636606, 25, C BLOCK [email protected]; 011-45675504, 1 001 SPA CAPITAL ADVISORS LTD. VARUN KAUSHIK, 9873486360, COMMUNITY JANAK PURI NEW DELHI 110058 [email protected]; 45675588,45675528 SANJAY JAIN 9910234032 CENTRE [email protected]; [email protected]; HARISH 9999114500, SABHARWAL 5TH 97, NEHRU [email protected];aparnarazdan@ba 2 002 BAJAJ CAPITAL LTD. HARISH SABHARWAL 011-41693000 NEW DELHI 110019 9811121101 FLOOR, BAJAJ PLACE jajcapital.com HOUSE [email protected]; [email protected]; J. M. FINANCIAL SERVICES PRADYUMNA 022-30877349, PALM COURT, 4TH LINK ROAD [email protected]; 3 003 MUMBAI 400064 PVT LTD SATPATHY 30877000, 67617000 FLOOR, M WING MALAD WEST [email protected]; [email protected]; [email protected] 105-108, CONNAUGHT [email protected]; 011-61127438, 040- 9989836349, 19, BARAKHAMBA 4 004 KARVY STOCK BROKING LTD. B V R NAIDU ARUNACHAL PLACE, NEW 110001 [email protected]; [email protected]; 44677536 9177401508 ROAD BUILDING DELHI [email protected] R. R. FINANCIAL RAJEEV SAXENA, S K 47 M M ROAD, RANI [email protected]; [email protected]; 5 005 011-23636362-63 9717553830 JHANDEWALAN NEW DELHI 110055 CONSULTANTS LTD. SINGH JHANSI MARG [email protected] [email protected]; HSBC SECURITIES AND 52/60 M. G. ROAD [email protected]; 6 006 SHWETANK DEV 022-40854280 9811374741 MUMBAI 400001 CAPITAL MARKETS (I) P LTD FORT [email protected]; [email protected] MR. -

Bank of Scotland Share Dealing Terms & Conditions
Share Dealing Terms and Conditions Effective from 1st April 2021 Contents 1. These terms and conditions and 14. Information about the agreement between us 1 your account 21 2. About us 1 15. Complaints and compensation 23 3. Definitions 2 16. Changing this agreement 4. The service and your account 7 and termination 23 5. Opening an account 8 17. Our liability, governing law, 6. Using the service 10 regulation and tax reporting 24 7. Funding and withdrawing 18. TradePlan 25 amounts from your account 11 19. Regular investments and 8. Dealing 13 subscriptions 27 9. Settlement 15 20. Dividend Reinvestment Plan (DRIP) 27 10. Holding investments and cash in your account 16 21. Supplementary Conditions for ISAs 28 11. Our right to use your assets 18 How to complain 33 12. Corporate actions 19 13. Costs and Charges 20 Bank of Scotland Share Dealing Service 1. These terms and conditions and the 1.6 Throughout these terms and conditions, the agreement between us words in bold have the meanings given to them in Condition 3. 1.1 These terms and conditions set out terms which apply to the Bank of Scotland Share 1.7 We also use the words: Dealing Service. ► “we”, “us” and “our” to mean Halifax Share 1.2 These terms and conditions, together with the Dealing Limited, the provider Bank of Scot- current Bank of Scotland Share Dealing brochure land Share Dealing Service (and ISA manager, and any other information or documents we if applicable); and give to you such as your application and any ► “you” and “your” to mean the person(s) who charging schedule govern the legal agreement have made an application and are registered between you and us and set out your and our to use the service. -

List of British Entities That Are No Longer Authorised to Provide Services in Spain As from 1 January 2021
LIST OF BRITISH ENTITIES THAT ARE NO LONGER AUTHORISED TO PROVIDE SERVICES IN SPAIN AS FROM 1 JANUARY 2021 Below is the list of entities and collective investment schemes that are no longer authorised to provide services in Spain as from 1 January 20211 grouped into five categories: Collective Investment Schemes domiciled in the United Kingdom and marketed in Spain Collective Investment Schemes domiciled in the European Union, managed by UK management companies, and marketed in Spain Entities operating from the United Kingdom under the freedom to provide services regime UK entities operating through a branch in Spain UK entities operating through an agent in Spain ---------------------- The list of entities shown below is for information purposes only and includes a non- exhaustive list of entities that are no longer authorised to provide services in accordance with this document. To ascertain whether or not an entity is authorised, consult the "Registration files” section of the CNMV website. 1 Article 13(3) of Spanish Royal Decree-Law 38/2020: "The authorisation or registration initially granted by the competent UK authority to the entities referred to in subparagraph 1 will remain valid on a provisional basis, until 30 June 2021, in order to carry on the necessary activities for an orderly termination or transfer of the contracts, concluded prior to 1 January 2021, to entities duly authorised to provide financial services in Spain, under the contractual terms and conditions envisaged”. List of entities and collective investment -

Filed by the Lion Electric Company Pursuant to Rule 425 of The
Filed by The Lion Electric Company pursuant to Rule 425 of the Securities Act of 1933, as amended and deemed filed pursuant to Rule 14a-12 under the Securities and Exchange Act of 1934, as amended Subject Company: Northern Genesis Acquisition Corp. Commission File No. 001-39451 The following communication was made available by The Lion Electric Company (the “Company”) on its website at https://www.thelionelectric.com/, directing viewers to a webpage on Northern Genesis Acquisition Corp.’s (“NGA”) website at https://www.northerngenesis.com/, on March 24, 2021: The following communication was made available by NGA on its website at http://www.northerngenesis.com/ on March 24, 2021: Your vote matters We encourage you to vote in favor of the business combination with Lion Electric today! Voting is Simple Every vote is important. Regardless of the number of shares you hold, we encourage you to vote and make your voice heard. If you owned Northern Genesis (NYSE: NGA) stock as of the close of business on March 18, 2021, you are entitled to vote and are urged to vote as soon as possible before April 23, 2021. Voting online or via telephone are the easiest ways to vote – and they are both free: Vote Online (Highly recommended): Follow the instructions provided by your broker, bank or other nominee on the Voting Instruction Form mailed (or e-mailed) to you. To vote online, you will need your voting control number, which is included on the Voting Instruction Form. CHECK YOUR EMAIL FOR VOTING! If you hold at Robinhood or Interactive Brokers from g Proxydocs.com For all others check for an email from g Proxyvote.com Vote by Telephone: Follow the instructions provided by your broker, bank or other nominee on the Voting Instruction Form mailed (or e-mailed) to you. -

The Internet Organised Crime Threat Assessment (IOCTA) 2015
The Internet Organised Crime Threat Assessment (IOCTA) 2015 2 THE INTERNET ORGANISED CRIME THREAT ASSESSMENT (IOCTA) 2015 THE INTERNET ORGANISED CRIME THREAT ASSESSMENT (IOCTA) 2015 3 TABLE OF FOREWORD 5 CONTENTS ABBREVIATIONS 6 EXECUTIVE SUMMARY 7 KEY FINDINGS 10 KEY RECOMMENDATIONS 12 SUGGESTED OPERATIONAL PRIORITIES 15 INTRODUCTION 16 MALWARE 18 ONLINE CHILD SEXUAL EXPLOITATION 29 PAYMENT FRAUD 33 SOCIAL ENGINEERING 37 DATA BREACHES AND NETWORK ATTACKS 40 ATTACKS ON CRITICAL INFRASTRUCTURE 44 CRIMINAL FINANCES ONLINE 46 CRIMINAL COMMUNICATIONS ONLINE 50 DARKNETS 52 BIG DATA, IOT AND THE CLOUD 54 THE GEOGRAPHICAL DISTRIBUTION OF CYBERCRIME 57 GENERAL OBSERVATIONS 62 APPENDICES 67 A1. THE ENCRYPTION DEBATE 67 A2. AN UPDATE ON CYBER LEGISLATION 70 A3. COMPUTER CRIME, FOLLOWED BY CYBERCRIME FOLLOWED BY …. ROBOT AND AI CRIME? 72 4 THE INTERNET ORGANISED CRIME THREAT ASSESSMENT (IOCTA) 2015 FOREWORD These include concrete actions under the three main mandated Threat Assessment (IOCTA), the annual presentation of the areas – child sexual exploitation, cyber attacks, and payment I am pleased to present the 2015 Internet Organised Crime fraud – such as targeting certain key services and products Centre (EC3). offered as part of the Crime-as-a-Service model, addressing the cybercrime threat landscape by Europol’s European Cybercrime growing phenomenon of live-streaming of on-demand abuse of children, or targeted actions with relevant private sector partners ofUsing cybercrime the 2014 for report the asperiod a baseline, under this consideration. assessment Itcovers offers the a cross-cutting crime enablers such as bulletproof hosting, illegal viewkey developments, predominantly changes from a lawand enforcement emerging threats perspective in the based field tradingagainst onlinesites on payment Darknets fraud. -

A Step Ahead Focus on Security
A STEP AHEAD FOCUS ON SECURITY IN THIS ISSUE: HOW MCAFEE UNCOVERED A CYBERCRIME GANG AND AIDED IN THEIR ARREST THE FUTURE OF CYBERSECURITY BIG THREATS, CRITICAL MOVES & ONGOING TRENDS WHAT WE SHOULD AND SHOULD NOT DO IN 2018 INSIGHTS AND TIPS FROM THE WORLD’S MOST FAMOUS FORMER HACKER Think you’re secure? ThinkWhy you you’re may secure? be surprised. Why you may be surprised. With more than 50,000 security threats emerging each day, IT managers like you have a challenging job. Even with carefully crafted policies, the biggest threat Over half of U.S. may come from inside your organization. Firewalls, antivirus software, rules and employees who regulations can only do so much. The final barrier is employee behavior and, when print, scan or you’re waging the war against laid-back attitudes, culprits can be everywhere. copy confidential information never, or rarely, worry that Did you know? those items will remain secure. Intellectual % property (IP) 98 theft has reached Why you should of compromises took “unprecedented” just minutes, or less, levels, costing the be worried: to perpetrate.1 U.S. an estimated $300B a year.2 54% of workers copy, scan or print Who’s ignoring the rules? confidential work. 87% of employees work 1 in 10 rarely or never 1.5 in 10 are not aware of at a company that has follow the policy. what the security policies are. an IT security policy. % However: 60 of workers are not prompted to enter a password before printing. What can you do? With the right balance of people, processes and technology, Make your IT security policy more than a written you can protect sensitive data wherever it resides.