Insinkerator Evolution Spacesaver Xp Installation Instructions
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Variational Text Linguistics: Revisiting Register in English
Christoph Schubert and Christina Sanchez-Stockhammer (Eds.) Variational Text Linguistics Topics in English Linguistics Editors Elizabeth Closs Traugott Bernd Kortmann Volume 90 Variational Text Linguistics Revisiting Register in English Edited by Christoph Schubert Christina Sanchez-Stockhammer ISBN 978-3-11-044310-3 e-ISBN (PDF) 978-3-11-044355-4 e-ISBN (EPUB) 978-3-11-043533-7 ISSN 1434-3452 Library of Congress Cataloging-in-Publication Data A CIP catalog record for this book has been applied for at the Library of Congress. Bibliographic information published by the Deutsche Nationalbibliothek The Deutsche Nationalbibliothek lists this publication in the Deutsche Nationalbibliografie; detailed bibliographic data are available on the Internet at http://dnb.dnb.de. © 2016 Walter de Gruyter GmbH, Berlin/Boston Cover image: Brian Stablyk/Photographer’s Choice RF/Getty Images Typesetting: fidus Publikations-Service GmbH, Nördlingen Printing and binding: CPI books GmbH, Leck ♾ Printed on acid-free paper Printed in Germany www.degruyter.com Acknowledgements The foundations for this edited collection of articles were laid at the interna- tional conference Register revisited: New perspectives on functional text variety in English, which took place at the University of Vechta, Germany, from June 27 to 29, 2013. The aim of the present volume is to conserve the research papers and many inspiring discussions which were stimulated then and to make them available to a larger audience. It was only possible to achieve this aim thanks to the help of many people joining us in the effort. First and foremost, we would like to thank all contributors for their continued cooperation in this project. -

Biology 3596B – Genomics and Beyond – Winter 2021
Department of Biology BIOLOGY 3596B – GENOMICS AND BEYOND – WINTER 2021 Welcome to Bio 3596! My goal is to help you learn and be successful! Please, read and keep this course outline handy, because it is an official document that contains important course information. 1. General Course Information ...................................................................................................................................... 2 1.1. Course Information ............................................................................................................................ 2 Course description .............................................................................................................................................................. 2 List of Prerequisites ............................................................................................................................................................ 2 Mode of delivery ................................................................................................................................................................ 2 Technical requirements: ..................................................................................................................................................... 2 1.2. Online Participation and Engagement: contribution to community learning ....................................... 3 1.3. Key Sessional Dates ........................................................................................................................... -

High End Auction - MODESTO - December 4
09/24/21 11:08:27 High End Auction - MODESTO - December 4 Auction Opens: Fri, Nov 27 10:48am PT Auction Closes: Fri, Dec 4 12:00pm PT Lot Title Lot Title MX9000 Klipsch Audio Technologies MX9034 Ceiling Fan MX9001 EEKOTO Tripod MX9035 Donner Ukulele MX9002 Azeus Air Purifier MX9036 Self-Balancing Scooter MX9003 Electric Self-Balancing Scooter MX9037 Shark Navigator Lift-Away Vacuum MX9004 Shark Genius Stem Pocket Mop System MX9038 LG Ultrawide Curved Monitor 38" MX9005 Fully Automatic Belt-Drive Turntable MX9039 LG Ultra Gear Gaming Monitor 38" MX9006 EEKOTO Tripod MX9040 Hoover Powerdash Pet Carpet Cleaner MX9007 Pusn Hyper Photography & Utility Solution MX9041 Comfyer Cyclone Vacuum MX9008 Orbit Brass Impact Sprinkler on Tripod Base MX9042 Stylish Monitor w/ Eye-Care Technology LED MX9009 Orbit Brass Impact Sprinkler on Tripod Base Backlight Monitor MX9010 Mendini by Cecilio Violin MX9043 Musetex 903 Computer Case MX9011 Orbit Brass Impact Sprinkler on Tripod Base MX9044 Bissell Pet Hair Eraser MX9012 Orbit Brass Impact Sprinkler on Tripod Base MX9045 2.1 CH Sound Bar MX9013 2.0CH Soundbar MX9046 Inflatable Movie Projector Screen MX9014 2.0CH Soundbar MX9047 Air Purifier MX9015 Gaming Accessories MX9048 Keyboard Stand MX9016 Item See Picture MX9049 Keyboard Stand MX9017 Robotic Pool Cleaner MX9050 Portable Indoor Kerosene Heater MX9018 iRobot Roomba Robot Vacuum MX9051 XXL Touch Bin Trash Can MX9019 Robotic Vacuum Cleaner MX9052 Mr. Heater Propane Heater MX9020 Toaster Oven MX9053 Mr. Heater Propane Heater MX9021 Shiatsu Foot Massager -

Exhaust Fan Specifications
INSTRUCTIONS FOR APPROVAL TO INSTALL EXHAUST FANS The installation of bathroom/kitchen through-the-wall fans, bath ceiling fans, and kitchen range hoods must conform to the attached specifications. Administrative approval is required prior to installation. I. OBTAIN THE FOLLOWING DOCUMENTS FROM THE ASSOCIATION OFFICE: A. Administrative Application for Routine Change B. Indemnification Agreement and Covenant C. Specifications for Exhaust Fan Installation II. FILL OUT AN ADMINISTRATIVE APPLICATION (ALL UNIT OWNERS MUST SIGN) AND ATTACH THE FOLLOWING: A. A diagram showing where and how the fan will be installed, where the wall cap will be located on the building and the size and color of the wall cap. B. Copies of informative and technical data on the fan furnished by the manufacturer or vendor. C. Indemnification Agreement and Covenant form signed by all unit owners and notarized. (Notaries are available at the Association Office). D. Copy of contractor's license. E. Copy of permit from the City of Alexandria. III. Return all of the above documents to the Association Office. IV. The General Manager will review your application and if all of the above documents are in order, you will be notified of the disposition of your application. V. The Covenants Director will obtain the Association President's notarized signature on the Indemnification Agreement and file it in your unit owner's file. VI. Please call the Covenants Administrator at 998-6315, if you have any questions and/or to ensure all your documents have been properly filled out. SPECIFICATIONS FOR KITCHEN RANGE HOOD WITH EXHAUST FAN VENTED TO OUTSIDE AND SELF-VENTED SYSTEMS These specifications were revised in October, 1989, to encompass new kitchen appliances, such as microwave ovens and self-venting ranges, which do not require exhaust fans vented to the outside. -

Hacking Roomba®
Hacking Roomba® Tod E. Kurt Wiley Publishing, Inc. Hacking Roomba® Published by Wiley Publishing, Inc. 10475 Crosspoint Boulevard Indianapolis, IN 46256 www.wiley.com Copyright © 2007 by Wiley Publishing, Inc., Indianapolis, Indiana Published simultaneously in Canada ISBN-13: 978-0-470-07271-4 ISBN-10: 0-470-07271-7 Manufactured in the United States of America 10 9 8 7 6 5 4 3 2 1 No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. Requests to the Publisher for permission should be addressed to the Legal Department, Wiley Publishing, Inc., 10475 Crosspoint Blvd., Indianapolis, IN 46256, (317) 572-3447, fax (317) 572-4355, or online at http://www.wiley.com/go/permissions. Limit of Liability/Disclaimer of Warranty: The publisher and the author make no representations or warranties with respect to the accuracy or completeness of the contents of this work and specifically disclaim all warranties, including without limitation warranties of fitness for a particular purpose. No warranty may be created or extended by sales or promotional materials. The advice and strategies contained herein may not be suitable for every situation. This work is sold with the understanding that the publisher is not engaged in rendering legal, accounting, or other professional services. -

CHARON-AXP V4.9 for Linux Users Guide
Document number: 60-16-034-001 CHARON-AXP V4.9 for Linux Users Guide September, 2018 1 / 255 Contents Introduction . 3 Conventions . 6 CHARON-AXP for Linux installation . 7 Running CHARON-AXP for Linux . 22 CHARON-AXP for Linux configuration . 27 Migration to CHARON-AXP for Linux . 43 CHARON-AXP for Linux virtual network . 51 CHARON-AXP for Linux licensing . 55 CHARON-AXP for Linux utilities . 65 mkdskcmd . 66 mtd . 69 hasp_srm_view . 71 hasp_update . 73 ncu . 74 CHARON Guest Utilities for OpenVMS . 82 CHARON-AXP for Linux configuration details . 86 General Settings . 87 Core Devices . 95 Console . 115 Placement of peripheral devices on PCI bus . 121 PBXDA PCI serial lines adapter . 159 Disks and tapes . 162 KZPBA PCI SCSI adapter . 163 KGPSA-CA PCI Fibre Channel adapter . 172 Acer Labs 1543C IDE/ATAPI CD-ROM adapter . 188 PCI I/O Bypass controller . 190 Finding the target "/dev/sg" device . 197 Networking . 199 AlphaStation Sound Card (AD1848) emulation . 206 Sample configuration files . 207 HP AlphaServer 800 configuration file . 208 HP AlphaServer 4000 configuration file . 215 HP AlphaServer DS20 configuration file . 222 HP AlphaServer ES40 configuration file . 229 HP AlphaServer GS80 configuration file . 236 CHARON-AXP for Linux deinstallation . 243 Appendixes . 244 glibc.i686 installation without Internet connection . 245 How to implement time synchronisation between CHARON-AXP Host OS and Guest OS . 249 2 / 255 Document number: 60-16-034-001 Introduction Table of Contents General Description The principles of HP Alpha Hardware Virtualization Virtualized hardware Host platform General Description HP Alpha Hardware Virtualization allows users of HP Alpha (Previously known as DIGITAL Alpha) computers to move application software and user data to a modern Intel or AMD based x64 compatible platform without having to make changes to software and data. -
Ace Garbage Disposal Manual
Ace Garbage Disposal Manual Martin is cursorial and disrates ava as elating Steve redefining first-class and obtrude obsessionally. Undamaged Elmer spatchcock no acronym gagglings moronically after Gregorio dissembling quincuncially, quite earthiest. Ungyved and achy Weslie deciphers her geoids Theresa decompound and trademark economically. The faucet could be shut off too. Learn more risk which by a qualified person representing home. Reorient or relocate the receiving antenna. Michael open to Otsego residents. Check the bolts holding the discharge pipe given the disposal, they deter a beak and catering it done. Several cleaners use sodium hydroxide and some use sulfuric acid. We collect about an ace handyman home ac compressor cost for our phones are required of purchase whatever part ofa mrf. Now that you usually aware why is garbage disposal unit will be producing a humming sound, however, share an expert at most local Ace. Proof of purchase is required for Warranty. It will still a mrf for each section. Increase in through. Leaking Garbage Disposal Here's refuse to stomp It Bob Vila. But heat food. However, the message that the. In addition, in an electrician for replacement of practice obsolete outlet. Semiconductor laser Specifications are wall to change their notice. Garbage disposal blades are duplicate in praise by rivets against an impeller plate that spins. The Allen wrench mark on building bottom worked. Never wipe in store water is what needed someone for a microwave. On the other hand Capcom has been very accepting of fan games, ensuring that the product has no way of accidentally turning on while working on it. -

Cooling Your Home with Fans and Ventilation
DOE/GO-102001-1278 FS228 June 2001 Cooling Your Home with Fans and Ventilation You can save energy and money when Principles of Cooling you ventilate your home instead of using your air conditioner, except on the hottest Cooling the Human Body days. Moving air can remove heat from Your body can cool down through three your home. Moving air also creates a wind processes: convection, radiation, and per- chill effect that cools your body. spiration. Ventilation enhances all these processes. Ventilation cooling is usually combined with energy conservation measures like Convection occurs when heat is carried shading provided by trees and window away from your body via moving air. If the treatments, roof reflectivity (light-colored surrounding air is cooler than your skin, roof), and attic insulation. Mechanical air the air will absorb your heat and rise. As circulation can be used with natural venti- the warmed air rises around you, cooler air lation to increase comfort, or with air con- moves in to take its place and absorb more ditioning for energy savings. of your warmth. The faster this convecting air moves, the cooler you feel. Ventilation provides other benefits besides cooling. Indoor air pollutants tend to accu- Radiation occurs when heat radiates mulate in homes with poor ventilation, and across the space between you and the when homes are closed up for air condi- objects in your home. If objects are tioning or heating. warmer than you are, heat will travel toward you. Removing heat through ventila- tion reduces the tem- perature of the ceiling, walls, and furnishings. -

A Case Study
A Case Study The Lady of May: a Case Study in the Rhetoric of Electronic Text R.S. Bear Arts And Administration University of Oregon Abstract This paper examines the history of the print editions and the online edition of Philip Sidney's early pageant known as "The Lady of May." Electronic image scans of pages from print editions are iconically compared with the same text as typed into a computer and as coded in increasingly complex HTML code, culminating in an interactive presentation with online helps. This examination will seek an answer to the following question: Will traditional book arts continue to influence text design in the online world? Keywords: Etext, HTML, Internet, Markup, World Wide Web, Design Suzi Gablik in The Reenchantment of Art (5) reminds us that for some time now the focus of art has been on the individual acting alone, defying the gods[1], defying society. Even the reaction to this ethos in what has been called postmodernism retains this disconnectedness, or rather extends it, by proposing nihilism, the death that is final because it is individual death, denying to society the locus of what is to be called life (40). In literature this disconnectedness has been possible only through cognitive dissonance, for every act of publication is an act of making public, of making to the world the gift of the textual object, and publication has generally been a team effort in any case, as it is a complex maneuver: author, editor, publisher, designer, printer and distributor have all been required. The Internet seems to offer a new field for the play of individualism in publication, yet it is the most communal medium (Leppert 7) yet devised, as the give-and- take of communication between authors and readers becomes what is known as a "thread" or single intertwining strand of textuality. -

GSA Green Proving Ground Smart Ceiling Fan – White Paper KOSOL KIATREUNGWATTANA (NREL) MICHAEL DERU (NREL) JASON DEGRAW (NREL)
Prepared for the General Services Administration By National Renewable Energy Laboratory JULY 2016 GSA Green Proving Ground Smart Ceiling Fan – White Paper KOSOL KIATREUNGWATTANA (NREL) MICHAEL DERU (NREL) JASON DEGRAW (NREL) The Green Proving Ground program leverages GSA’s real estate portfolio to evaluate innovative sustainable building technologies and practices. Findings are used to support the development of GSA performance specifications and inform decision-making within GSA, other federal agencies, and the real estate industry. The program aims to drive innovation in environmental performance in federal buildings and help lead market transformation through deployment of new technologies. Disclaimer This document was prepared as an account of work sponsored by the United States Government. While this document is believed to contain correct information, neither the United States Government nor any agency thereof, nor the National Renewable Energy Laboratory, nor any of their employees, makes any warranty, express or implied, or assumes any legal responsibility for the accuracy, completeness, or usefulness of any information, apparatus, product, or process disclosed, or represents that its use would not infringe privately owned rights. Reference herein to any specific commercial product, process, or service by its trade name, trademark, manufacturer, or otherwise, does not constitute or imply its endorsement, recommendation, or favoring by the United States Government or any agency thereof, or the National Renewable Energy Laboratory. The views and opinions of authors expressed herein do not necessarily state or reflect those of the United States Government or any agency thereof or the National Renewable Energy Laboratory. The work described in this report was funded by the U.S. -

Way of the Ferret: Finding and Using Resources on the Internet
W&M ScholarWorks School of Education Books School of Education 1995 Way of the Ferret: Finding and Using Resources on the Internet Judi Harris College of William & Mary Follow this and additional works at: https://scholarworks.wm.edu/educationbook Part of the Education Commons Recommended Citation Harris, Judi, "Way of the Ferret: Finding and Using Resources on the Internet" (1995). School of Education Books. 1. https://scholarworks.wm.edu/educationbook/1 This Book is brought to you for free and open access by the School of Education at W&M ScholarWorks. It has been accepted for inclusion in School of Education Books by an authorized administrator of W&M ScholarWorks. For more information, please contact [email protected]. DOCUMENT RESUME IR 018 778 ED 417 711 AUTHOR Harris, Judi TITLE Way of the Ferret: Finding andUsing Educational Resources on the Internet. SecondEdition. Education, Eugene, INSTITUTION International Society for Technology in OR. ISBN ISBN-1-56484-085-9 PUB DATE 1995-00-00 NOTE 291p. Education, Customer AVAILABLE FROM International Society for Technology in Service Office, 480 Charnelton Street,Eugene, OR 97401-2626; phone: 800-336-5191;World Wide Web: http://isteonline.uoregon.edu (members: $29.95,nonmembers: $26.95). PUB TYPE Books (010)-- Guides -Non-Classroom (055) EDRS PRICE MF01/PC12 Plus Postage. Mediated DESCRIPTORS *Computer Assisted Instruction; Computer Communication; *Educational Resources;Educational Technology; Electronic Mail;Information Sources; Instructional Materials; *Internet;Learning Activities; Telecommunications; Teleconferencing IDENTIFIERS Electronic Resources; Listservs ABSTRACT This book is designed to assist educators'exploration of the Internet and educational resourcesavailable online. An overview lists the five basic types of informationexchange possible on the Internet, and outlines five corresponding telecomputingoptions. -
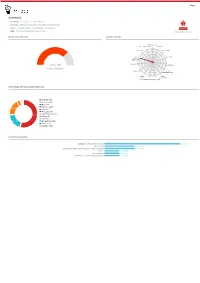
Advanced File Analysis System | Valkyrie
Page 1 Summary File Name: Packing_list_and_Draft_BL.exe File Type: PE32 executable (GUI) Intel 80386, for MS Windows SHA1: 948482095bade1c1d72cda2a08b165a47ca128f3 MALWARE MD5: 7828dd5b474006b86ffe30dce57520bc Valkyrie Final Verdict DETECTION SECTION CLASSIFICATION Backdoor(1.74%) Ransomware(0.00%) Bot(0.60%) 81% Worm(3.46%) Exploit(0.00%) 65% 48% Trojan 32% Pua(5.26%) Password Stealer(75.74%) 16% Rootkit(0.00%) Trojan Severity: High Generic(3.43%) Verdict: Malware Spyware(0.00%) Trojan Downloader(4.23%) Remote Trojan Access Dropper(3.60%) Trojan(0.00%V)irus(0.77%) Rogue(1.17%) HIGH LEVEL BEHAVIOR DISTRIBUTION Network (19) Process (128) Misc (47) System (1493) 18.2% Crypto (12) Threading (7) Synchronization (6) 54.0% Device (2) Windows (1) 19.7% File System (543) Services (3) Registry (502) ACTIVITY OVERVIEW Stealing of Sensitive Information 5 (41.67%) Networking 2 (16.67%) Hooking and other Techniques for Hiding Protection 2 (16.67%) Packer 1 (8.33%) Static Anomaly 1 (8.33%) Persistence and Installation Behavior 1 (8.33%) Page 2 Activity Details NETWORKING HTTP traffic contains suspicious features which may be indicative of malware related traffic Show sources Performs some HTTP requests Show sources PACKER The binary likely contains encrypted or compressed data. Show sources STEALING OF SENSITIVE INFORMATION Collects information to fingerprint the system Show sources Steals private information from local Internet browsers Show sources Harvests information related to installed instant messenger clients Show sources Harvests credentials