Security Target
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Reference & Manual
DynaPDF 4.0 Reference & Manual API Reference Version 4.0.59 September 16, 2021 Legal Notices Copyright: © 2003-2021 Jens Boschulte, DynaForms GmbH. All rights reserved. DynaForms GmbH Burbecker Street 24 D-58285 Gevelsberg, Germany Trade Register HRB 9770, District Court Hagen CEO Jens Boschulte Phone: ++49 23 32-666 78 37 Fax: ++49 23 32-666 78 38 If you have questions please send an email to [email protected], or contact us by phone. This publication and the information herein is furnished as is, is subject to change without notice, and should not be construed as a commitment by DynaForms GmbH. DynaForms assumes no responsibility or liability for any errors or inaccuracies, makes no warranty of any kind (express, implied or statutory) with respect to this publication, and expressly disclaims any and all warranties of merchantability, fitness for particular purposes and no infringement of third-party rights. Adobe, Acrobat, and PostScript are trademarks of Adobe Systems Inc. AIX, IBM, and OS/390, are trademarks of International Business Machines Corporation. Microsoft, Windows, and Windows NT are trademarks of Microsoft Corporation. Apple, Mac OS, and Safari are trademarks of Apple Computer, Inc. registered in the United States and other countries. TrueType is a trademark of Apple Computer, Inc. Unicode and the Unicode logo are trademarks of Unicode, Inc. UNIX is a trademark of The Open Group. Solaris is a trademark of Sun Microsystems, Inc. Tru64 is a trademark of Hewlett-Packard. Linux is a trademark of Linus Torvalds. Other company product and service names may be trademarks or service marks of others. -

Cyinpenc.Pdf
1 The Cyrillic codepages There are several widely used Cyrillic codepages. Currently, we define here the following codepages: • cp 866 is the standard MS-DOS Russian codepage. There are also several codepages in use, which are very similar to cp 866. These are: so-called \Cyrillic Alternative codepage" (or Alternative Variant of cp 866), Modified Alternative Variant, New Alternative Variant, and experimental Tatarian codepage. The differences take place in the range 0xf2{0xfe. All these `Alternative' codepages are also supported. • cp 855 is the standard MS-DOS Cyrillic codepage. • cp 1251 is the standard MS Windows Cyrillic codepage. • pt 154 is a Windows Cyrillic Asian codepage developed in ParaType. It is a variant of Windows Cyrillic codepage. • koi8-r is a standard codepage widely used in UNIX-like systems for Russian language support. It is specified in RFC 1489. The situation with koi8-r is somewhat similar to the one with cp 866: there are also several similar codepages in use, which coincide with koi8-r for all Russian letters, but add some other Cyrillic letters. These codepages include: koi8-u (it is a variant of the koi8-r codepage with some Ukrainian letters added), koi8-ru (it is described in a draft RFC document specifying the widely used character set for mail and news exchange in the Ukrainian internet community as well as for presenting WWW information resources in the Ukrainian language), and ISO-IR-111 ECMA Cyrillic Code Page. All these codepages are supported also. • ISO 8859-5 Cyrillic codepage (also called ISO-IR-144). • Apple Macintosh Cyrillic (Microsoft cp 10007) codepage. -

Catalogue 1986-99
PUBLICATIONS BY SUBJECT LIFE SCIENCES .............................................................................................................................................. 1 Nuclear Medicine (including Radiopharmaceuticals) ............................................................................ 1 Radiation Biology........................................................................................................................................ 2 Medical Physics (including Dosimetry) .................................................................................................... 2 FOOD AND AGRICULTURE ............................................................................................................................ 4 Food Irradiation .......................................................................................................................................... 4 Insect and Pest Control.............................................................................................................................. 5 Mutation Plant Breeding............................................................................................................................ 6 Plant Biotechnology.................................................................................................................................... 7 Soil Fertility and Irrigation.......................................................................................................................... 7 Agrochemicals ........................................................................................................................................... -

Javapos Driver Outline
PT330/PT331 POSPrinter, CashDrawer Application Programmer's Guide of Java for Retail POS Driver for Serial/ USB Interface Table of Contents Preface........................................................................................................................................... 1 1. Outline ................................................................................................................................4 1.1. Subject Scope of this document........................................................................................4 1.2. JavaPOS Driver Outline....................................................................................................5 1.3. Restrictions .......................................................................................................................7 1.4. Connection Way to POS Printer........................................................................................9 1.5. About install....................................................................................................................11 1.6. Setting Program Usage ...................................................................................................12 2. Using JavaPOS Driver ...................................................................................................... 16 2.1. Common .........................................................................................................................16 2.2. POS Printer .....................................................................................................................16 -

INIS Progress and Activity Report 2000
631-L2-TC-441.29/2 Twenty Ninth Consultative Meeting of INIS Liaison Officers Vienna, 2-4 May 2001 INIS Progress and Activity Report 2000 Reproduced by the IAEA Vienna, Austria, 2001 The material in this document has been supplied by the authors and has not been edited by the IAEA. The views expressed remain the responsibility of the named authors and do not necessarily reflect those of the government(s) of the designating Member State(s). In particular, neither the IAEA nor any other organisation or body sponsoring this meeting can be held responsible for any material reproduced in this document. Table of Contents HIGHLIGHTS OF INIS ACTIVITIES 2000.............................................................................. 5 INIS PROGRESS AND ACTIVITY REPORT 2000 ................................................................ 9 A. GENERAL STATISTICS...................................................................................................... 9 A.1 Summary......................................................................................................................................................9 A.2 Member States and International Organisations participating in INIS ......................................................11 A.3 INIS Membership ......................................................................................................................................14 A.4 Countries receiving Atomindex Files on In-house produced CD-ROMs....................................................15 A.5 Revisions of the -

Electronic Document Preparation Pocket Primer
Electronic Document Preparation Pocket Primer Vít Novotný December 4, 2018 Creative Commons Attribution 3.0 Unported (cc by 3.0) Contents Introduction 1 1 Writing 3 1.1 Text Processing 4 1.1.1 Character Encoding 4 1.1.2 Text Input 12 1.1.3 Text Editors 13 1.1.4 Interactive Document Preparation Systems 13 1.1.5 Regular Expressions 14 1.2 Version Control 17 2 Markup 21 2.1 Meta Markup Languages 22 2.1.1 The General Markup Language 22 2.1.2 The Extensible Markup Language 23 2.2 Markup on the World Wide Web 28 2.2.1 The Hypertext Markup Language 28 2.2.2 The Extensible Hypertext Markup Language 29 2.2.3 The Semantic Web and Linked Data 31 2.3 Document Preparation Systems 32 2.3.1 Batch-oriented Systems 35 2.3.2 Interactive Systems 36 2.4 Lightweight Markup Languages 39 3 Design 41 3.1 Fonts 41 3.2 Structural Elements 42 3.2.1 Paragraphs and Stanzas 42 iv CONTENTS 3.2.2 Headings 45 3.2.3 Tables and Lists 46 3.2.4 Notes 46 3.2.5 Quotations 47 3.3 Page Layout 48 3.4 Color 48 3.4.1 Theory 48 3.4.2 Schemes 51 Bibliography 53 Acronyms 61 Index 65 Introduction With the advent of the digital age, typesetting has become available to virtually anyone equipped with a personal computer. Beautiful text documents can now be crafted using free and consumer-grade software, which often obviates the need for the involvement of a professional designer and typesetter. -

Abkürzungs-Liste ABKLEX
Abkürzungs-Liste ABKLEX (Informatik, Telekommunikation) W. Alex 1. Juli 2021 Karlsruhe Copyright W. Alex, Karlsruhe, 1994 – 2018. Die Liste darf unentgeltlich benutzt und weitergegeben werden. The list may be used or copied free of any charge. Original Point of Distribution: http://www.abklex.de/abklex/ An authorized Czechian version is published on: http://www.sochorek.cz/archiv/slovniky/abklex.htm Author’s Email address: [email protected] 2 Kapitel 1 Abkürzungen Gehen wir von 30 Zeichen aus, aus denen Abkürzungen gebildet werden, und nehmen wir eine größte Länge von 5 Zeichen an, so lassen sich 25.137.930 verschiedene Abkür- zungen bilden (Kombinationen mit Wiederholung und Berücksichtigung der Reihenfol- ge). Es folgt eine Auswahl von rund 16000 Abkürzungen aus den Bereichen Informatik und Telekommunikation. Die Abkürzungen werden hier durchgehend groß geschrieben, Akzente, Bindestriche und dergleichen wurden weggelassen. Einige Abkürzungen sind geschützte Namen; diese sind nicht gekennzeichnet. Die Liste beschreibt nur den Ge- brauch, sie legt nicht eine Definition fest. 100GE 100 GBit/s Ethernet 16CIF 16 times Common Intermediate Format (Picture Format) 16QAM 16-state Quadrature Amplitude Modulation 1GFC 1 Gigabaud Fiber Channel (2, 4, 8, 10, 20GFC) 1GL 1st Generation Language (Maschinencode) 1TBS One True Brace Style (C) 1TR6 (ISDN-Protokoll D-Kanal, national) 247 24/7: 24 hours per day, 7 days per week 2D 2-dimensional 2FA Zwei-Faktor-Authentifizierung 2GL 2nd Generation Language (Assembler) 2L8 Too Late (Slang) 2MS Strukturierte -

International Register of Coded Character Sets to Be Used with Escape Sequences for Information Interchange in Data Processing
INTERNATIONAL REGISTER OF CODED CHARACTER SETS TO BE USED WITH ESCAPE SEQUENCES 1 Introduction 1.1 General This document is the ISO International Register of Coded Character Sets To Be Used With Escape Sequences for information interchange in data processing. It is compiled in accordance with the provisions of ISO/IEC 2022, "Code Extension Technique" and of ISO 2375 "Procedure for Registration of Escape Sequences". This International Register contains coded character sets which have been registered in accordance with procedures given in ISO 2375. Its purpose is to identify widely used coded character sets and associate with each a unique escape sequence by means of which it can be designated according to ISO/IEC 2022 and ISO/IEC 4873. The publication of this International Register should promote compatibility in international information interchange and avoid duplication of effort in developing application-oriented coded character sets. Registration provides an identification for a coded character set but implies nothing about its status; it may or may not be part of a standard of an international, national or a corporate body. However, if such a standard is published subsequently to the registration, it would be appropriate for the escape sequence identifying the character set to be specified in the standard. If it is desired to register a set, application should be made to the Registration Authority through an appropriate Sponsoring Authority as specified in ISO 2375. Any character set can be a candidate for registration if it meets the requirements of ISO 2375. The Registration Authority ascertains that the proposals received are formally in accordance with this International Standard, technically in accordance with ISO/IEC 2022, and, where applicable, with ISO/IEC 646 and ISO/IEC 4873, and meet the presentation practice of the Registration Authority. -
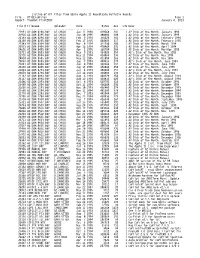
Listing of All Files from Genie Apple II Roundtable Bulletin
Listing of All Files from GEnie Apple II Roundtable Bulletin Boards File: AllGEnieFiles Page 1 Report: TimeOut Print2PDF January 8, 2013 File#Filename Uploader Date Bytes Acc LibDesc ------- ----------------- -------------- ------------- -------- ----- ----- ------------------------------------ 21951 A2.DOM.0194.BXY A2.CHUCK Jan 11 1994 429568 241 1 A2 Disk of the Month, January 1994 23926 A2.DOM.0195.BXY A2.CHUCK Jan 18 1995 388480 328 1 A2 Disk of the Month, January 1995 22183 A2.DOM.0294.BXY A2.CHUCK Feb 9 1994 356224 341 1 A2 Disk of the Month, February 1994 24169 A2.DOM.0295.BXY A2.CHUCK Feb 17 1995 444800 317 1 A2 Disk of the Month, February 1995 22383 A2.DOM.0394.BXY A2.CHUCK Mar 8 1994 311936 260 1 A2 Disk of the Month, March 1994 22591 A2.DOM.0494.BXY A2.CHUCK Apr 13 1994 478464 291 1 A2 Disk of the Month, April 1994 24696 A2.DOM.0495.BXY A2.CHUCK Apr 5 1995 360704 288 1 A2 Disk of the Month, Mar/Apr 1995 20721 A2.DOM.0593.BXY A2.CHUCK May 9 1993 464000 254 1 A2's Disk of the Month, May 1993 22726 A2.DOM.0594.BXY A2.CHUCK May 11 1994 424064 236 1 A2 Disk of the Month, May 1994 24924 A2.DOM.0595.BXY A2.CHUCK May 12 1995 411904 266 1 A2 Disk of the Month, May 1995 20860 A2.DOM.0693.BXY A2.CHUCK Jun 7 1993 450816 270 1 A2's Disk of the Month, June 1993 22841 A2.DOM.0694.BXY A2.CHUCK Jun 8 1994 330368 302 1 A2 Disk of the Month, June 1994 25190 A2.DOM.0695.BXY A2.CHUCK Jun 15 1995 456064 258 1 A2 Disk of the Month, June 1995 21003 A2.DOM.0793.BXY A2.CHUCK Jul 4 1993 480640 355 1 A2's Disk of the Month, July 1993 23059 A2.DOM.0794.BXY -
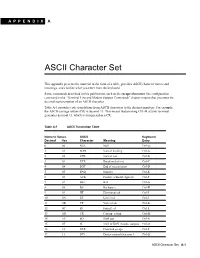
ASCII Character Set
APPENDIX A ASCII Character Set This appendix presents the material in the form of a table, provides ASCII character names and meanings, and clarifies what you enter from the keyboard. Some commands described in this publication, such as the escape-character line configuration command in the “Terminal Line and Modem Support Commands” chapter require that you enter the decimal representation of an ASCII character. Table A-1 provides code translations from ASCII characters to the decimal numbers. For example, the ASCII carriage return (CR) is decimal 13. This means that pressing Ctrl-M at your terminal generates decimal 13, which is interpreted as a CR. Table A-1 ASCII Translation Table Numeric Values ASCII Keyboard Decimal Hex Character Meaning Entry 0 00 NUL Null Ctrl-@ 1 01 SOH Start of heading Ctrl-A 2 02 STX Start of text Ctrl-B 3 03 ETX Break/end of text Ctrl-C 4 04 EOT End of transmission Ctrl-D 5 05 ENQ Enquiry Ctrl-E 6 06 ACK Positive acknowledgment Ctrl-F 7 07 BEL Bell Ctrl-G 8 08 BS Backspace Ctrl-H 9 09 HT Horizontal tab Ctrl-I 10 0A LF Line feed Ctrl-J 11 0B VT Vertical tab Ctrl-K 12 0C FF Form feed Ctrl-L 13 0D CR Carriage return Ctrl-M 14 0E SO Shift out Ctrl-N 15 0F SI Shift in/XON (resume output) Ctrl-O 16 10 DLE Data link escape Ctrl-P 17 11 DC1 Device control character 1 Ctrl-Q ASCII Character Set A-1 Numeric Values ASCII Keyboard Decimal Hex Character Meaning Entry 18 12 DC2 Device control character 2 Ctrl-R 19 13 DC3 Device control character 3 Ctrl-S 20 14 DC4 Device control character 4 Ctrl-T 21 15 NAK Negative Acknowledgment Ctrl-U 22 16 SYN Synchronous idle Ctrl-V 23 17 ETB End of transmission block Ctrl-W 24 18 CAN Cancel Ctrl-X 25 19 EM End of medium Ctrl-Y 26 1A SUB substitute/end of file Ctrl-Z 27 1B ESC Escape Ctrl-[ 28 1C FS File separator Ctrl-\ 29 1D GS Group separator Ctrl-] 30 1E RS Record separator Ctrl-^ 31 1F US Unit separator Ctrl-_ 32 20 SP Space Space 33 21 ! ! ! 34 22 " " " 35 23 # # # 36 24 $ $ $ 37 25 % % % 38 26 & & & 39 27 ’ ’ ’ 40 28 ( ( ( 41 29 ) ) ) 42 2A * * * 43 2B + + + 44 2C , , , 45 2D - - - 46 2E . -

MISP Objects
MISP Objects MISP Objects Introduction. 7 Funding and Support . 9 MISP objects. 10 ail-leak . 10 ais-info . 11 android-app. 12 android-permission. 13 annotation . 15 anonymisation . 16 asn . 20 attack-pattern . 22 authentication-failure-report . 22 authenticode-signerinfo . 23 av-signature. 24 bank-account. 25 bgp-hijack. 29 bgp-ranking . 30 blog . 30 boleto . 32 btc-transaction . 33 btc-wallet . 34 cap-alert . 35 cap-info. 39 cap-resource . 43 coin-address . 44 command . 46 command-line. 46 cookie . 47 cortex . 48 cortex-taxonomy . 49 course-of-action . 49 covid19-csse-daily-report . 51 covid19-dxy-live-city . 53 covid19-dxy-live-province . 54 cowrie . 55 cpe-asset . 57 1 credential . 67 credit-card . 69 crypto-material. 70 cytomic-orion-file. 73 cytomic-orion-machine . 74 dark-pattern-item. 74 ddos . 75 device . 76 diameter-attack . 77 dkim . 79 dns-record . .. -

Fonts Reference, Version 12.2.1
Start Oracle® Documaker Fonts Reference version 12.2 Part number: E41180-01 August 2013 Notice Copyright © 2009, 2013, Oracle and/or its affiliates. All rights reserved. The Programs (which include both the software and documentation) contain proprietary information; they are provided under a license agreement containing restrictions on use and disclosure and are also protected by copyright, patent, and other intellectual and industrial property laws. Reverse engineering, disassembly, or decompilation of the Programs, except to the extent required to obtain interoperability with other independently created software or as specified by law, is prohibited. The information contained in this document is subject to change without notice. If you find any problems in the documentation, please report them to us in writing. This document is not warranted to be error-free. Except as may be expressly permitted in your license agreement for these Programs, no part of these Programs may be reproduced or transmitted in any form or by any means, electronic or mechanical, for any purpose. If the Programs are delivered to the United States Government or anyone licensing or using the Programs on behalf of the United States Government, the following notice is applicable: U.S. GOVERNMENT RIGHTS Programs, software, databases, and related documentation and technical data delivered to U.S. Government customers are "commercial computer software" or "commercial technical data" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, use, duplication, disclosure, modification, and adaptation of the Programs, including documentation and technical data, shall be subject to the licensing restrictions set forth in the applicable Oracle license agreement, and, to the extent applicable, the additional rights set forth in FAR 52.227-19, Commercial Computer Software--Restricted Rights (June 1987).