Sketching for M-Estimators: a Unified Approach to Robust Regression
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Von Mises' Frequentist Approach to Probability
Section on Statistical Education – JSM 2008 Von Mises’ Frequentist Approach to Probability Milo Schield1 and Thomas V. V. Burnham2 1 Augsburg College, Minneapolis, MN 2 Cognitive Systems, San Antonio, TX Abstract Richard Von Mises (1883-1953), the originator of the birthday problem, viewed statistics and probability theory as a science that deals with and is based on real objects rather than as a branch of mathematics that simply postulates relationships from which conclusions are derived. In this context, he formulated a strict Frequentist approach to probability. This approach is limited to observations where there are sufficient reasons to project future stability – to believe that the relative frequency of the observed attributes would tend to a fixed limit if the observations were continued indefinitely by sampling from a collective. This approach is reviewed. Some suggestions are made for statistical education. 1. Richard von Mises Richard von Mises (1883-1953) may not be well-known by statistical educators even though in 1939 he first proposed a problem that is today widely-known as the birthday problem.1 There are several reasons for this lack of recognition. First, he was educated in engineering and worked in that area for his first 30 years. Second, he published primarily in German. Third, his works in statistics focused more on theoretical foundations. Finally, his inductive approach to deriving the basic operations of probability is very different from the postulate-and-derive approach normally taught in introductory statistics. See Frank (1954) and Studies in Mathematics and Mechanics (1954) for a review of von Mises’ works. This paper is based on his two English-language books on probability: Probability, Statistics and Truth (1936) and Mathematical Theory of Probability and Statistics (1964). -

Robust Statistics Part 3: Regression Analysis
Robust Statistics Part 3: Regression analysis Peter Rousseeuw LARS-IASC School, May 2019 Peter Rousseeuw Robust Statistics, Part 3: Regression LARS-IASC School, May 2019 p. 1 Linear regression Linear regression: Outline 1 Classical regression estimators 2 Classical outlier diagnostics 3 Regression M-estimators 4 The LTS estimator 5 Outlier detection 6 Regression S-estimators and MM-estimators 7 Regression with categorical predictors 8 Software Peter Rousseeuw Robust Statistics, Part 3: Regression LARS-IASC School, May 2019 p. 2 Linear regression Classical estimators The linear regression model The linear regression model says: yi = β0 + β1xi1 + ... + βpxip + εi ′ = xiβ + εi 2 ′ ′ with i.i.d. errors εi ∼ N(0,σ ), xi = (1,xi1,...,xip) and β =(β0,β1,...,βp) . ′ Denote the n × (p + 1) matrix containing the predictors xi as X =(x1,..., xn) , ′ ′ the vector of responses y =(y1,...,yn) and the error vector ε =(ε1,...,εn) . Then: y = Xβ + ε Any regression estimate βˆ yields fitted values yˆ = Xβˆ and residuals ri = ri(βˆ)= yi − yˆi . Peter Rousseeuw Robust Statistics, Part 3: Regression LARS-IASC School, May 2019 p. 3 Linear regression Classical estimators The least squares estimator Least squares estimator n ˆ 2 βLS = argmin ri (β) β i=1 X If X has full rank, then the solution is unique and given by ˆ ′ −1 ′ βLS =(X X) X y The usual unbiased estimator of the error variance is n 1 σˆ2 = r2(βˆ ) LS n − p − 1 i LS i=1 X Peter Rousseeuw Robust Statistics, Part 3: Regression LARS-IASC School, May 2019 p. 4 Linear regression Classical estimators Outliers in regression Different types of outliers: vertical outlier good leverage point • • y • • • regular data • ••• • •• ••• • • • • • • • • • bad leverage point • • •• • x Peter Rousseeuw Robust Statistics, Part 3: Regression LARS-IASC School, May 2019 p. -

Autocorrelation and Frequency-Resolved Optical Gating Measurements Based on the Third Harmonic Generation in a Gaseous Medium
Appl. Sci. 2015, 5, 136-144; doi:10.3390/app5020136 OPEN ACCESS applied sciences ISSN 2076-3417 www.mdpi.com/journal/applsci Article Autocorrelation and Frequency-Resolved Optical Gating Measurements Based on the Third Harmonic Generation in a Gaseous Medium Yoshinari Takao 1,†, Tomoko Imasaka 2,†, Yuichiro Kida 1,† and Totaro Imasaka 1,3,* 1 Department of Applied Chemistry, Graduate School of Engineering, Kyushu University, 744, Motooka, Nishi-ku, Fukuoka 819-0395, Japan; E-Mails: [email protected] (Y.T.); [email protected] (Y.K.) 2 Laboratory of Chemistry, Graduate School of Design, Kyushu University, 4-9-1, Shiobaru, Minami-ku, Fukuoka 815-8540, Japan; E-Mail: [email protected] 3 Division of Optoelectronics and Photonics, Center for Future Chemistry, Kyushu University, 744, Motooka, Nishi-ku, Fukuoka 819-0395, Japan † These authors contributed equally to this work. * Author to whom correspondence should be addressed; E-Mail: [email protected]; Tel.: +81-92-802-2883; Fax: +81-92-802-2888. Academic Editor: Takayoshi Kobayashi Received: 7 April 2015 / Accepted: 3 June 2015 / Published: 9 June 2015 Abstract: A gas was utilized in producing the third harmonic emission as a nonlinear optical medium for autocorrelation and frequency-resolved optical gating measurements to evaluate the pulse width and chirp of a Ti:sapphire laser. Due to a wide frequency domain available for a gas, this approach has potential for use in measuring the pulse width in the optical (ultraviolet/visible) region beyond one octave and thus for measuring an optical pulse width less than 1 fs. -
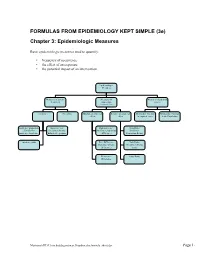
FORMULAS from EPIDEMIOLOGY KEPT SIMPLE (3E) Chapter 3: Epidemiologic Measures
FORMULAS FROM EPIDEMIOLOGY KEPT SIMPLE (3e) Chapter 3: Epidemiologic Measures Basic epidemiologic measures used to quantify: • frequency of occurrence • the effect of an exposure • the potential impact of an intervention. Epidemiologic Measures Measures of disease Measures of Measures of potential frequency association impact (“Measures of Effect”) Incidence Prevalence Absolute measures of Relative measures of Attributable Fraction Attributable Fraction effect effect in exposed cases in the Population Incidence proportion Incidence rate Risk difference Risk Ratio (Cumulative (incidence density, (Incidence proportion (Incidence Incidence, Incidence hazard rate, person- difference) Proportion Ratio) Risk) time rate) Incidence odds Rate Difference Rate Ratio (Incidence density (Incidence density difference) ratio) Prevalence Odds Ratio Difference Macintosh HD:Users:buddygerstman:Dropbox:eks:formula_sheet.doc Page 1 of 7 3.1 Measures of Disease Frequency No. of onsets Incidence Proportion = No. at risk at beginning of follow-up • Also called risk, average risk, and cumulative incidence. • Can be measured in cohorts (closed populations) only. • Requires follow-up of individuals. No. of onsets Incidence Rate = ∑person-time • Also called incidence density and average hazard. • When disease is rare (incidence proportion < 5%), incidence rate ≈ incidence proportion. • In cohorts (closed populations), it is best to sum individual person-time longitudinally. It can also be estimated as Σperson-time ≈ (average population size) × (duration of follow-up). Actuarial adjustments may be needed when the disease outcome is not rare. • In an open populations, Σperson-time ≈ (average population size) × (duration of follow-up). Examples of incidence rates in open populations include: births Crude birth rate (per m) = × m mid-year population size deaths Crude mortality rate (per m) = × m mid-year population size deaths < 1 year of age Infant mortality rate (per m) = × m live births No. -

Fundamental Frequency Detection
Fundamental Frequency Detection Jan Cernock´y,ˇ Valentina Hubeika cernocky|ihubeika @fit.vutbr.cz { } DCGM FIT BUT Brno Fundamental Frequency Detection Jan Cernock´y,ValentinaHubeika,DCGMFITBUTBrnoˇ 1/37 Agenda Fundamental frequency characteristics. • Issues. • Autocorrelation method, AMDF, NFFC. • Formant impact reduction. • Long time predictor. • Cepstrum. • Improvements in fundamental frequency detection. • Fundamental Frequency Detection Jan Cernock´y,ValentinaHubeika,DCGMFITBUTBrnoˇ 2/37 Recap – speech production and its model Fundamental Frequency Detection Jan Cernock´y,ValentinaHubeika,DCGMFITBUTBrnoˇ 3/37 Introduction Fundamental frequency, pitch, is the frequency vocal cords oscillate on: F . • 0 The period of fundamental frequency, (pitch period) is T = 1 . • 0 F0 The term “lag” denotes the pitch period expressed in samples : L = T Fs, where Fs • 0 is the sampling frequency. Fundamental Frequency Detection Jan Cernock´y,ValentinaHubeika,DCGMFITBUTBrnoˇ 4/37 Fundamental Frequency Utilization speech synthesis – melody generation. • coding • – in simple encoding such as LPC, reduction of the bit-stream can be reached by separate transfer of the articulatory tract parameters, energy, voiced/unvoiced sound flag and pitch F0. – in more complex encoders (such as RPE-LTP or ACELP in the GSM cell phones) long time predictor LTP is used. LPT is a filter with a “long” impulse response which however contains only few non-zero components. Fundamental Frequency Detection Jan Cernock´y,ValentinaHubeika,DCGMFITBUTBrnoˇ 5/37 Fundamental Frequency Characteristics F takes the values from 50 Hz (males) to 400 Hz (children), with Fs=8000 Hz these • 0 frequencies correspond to the lags L=160 to 20 samples. It can be seen, that with low values F0 approaches the frame length (20 ms, which corresponds to 160 samples). -

Pearson-Fisher Chi-Square Statistic Revisited
Information 2011 , 2, 528-545; doi:10.3390/info2030528 OPEN ACCESS information ISSN 2078-2489 www.mdpi.com/journal/information Communication Pearson-Fisher Chi-Square Statistic Revisited Sorana D. Bolboac ă 1, Lorentz Jäntschi 2,*, Adriana F. Sestra ş 2,3 , Radu E. Sestra ş 2 and Doru C. Pamfil 2 1 “Iuliu Ha ţieganu” University of Medicine and Pharmacy Cluj-Napoca, 6 Louis Pasteur, Cluj-Napoca 400349, Romania; E-Mail: [email protected] 2 University of Agricultural Sciences and Veterinary Medicine Cluj-Napoca, 3-5 M ănăş tur, Cluj-Napoca 400372, Romania; E-Mails: [email protected] (A.F.S.); [email protected] (R.E.S.); [email protected] (D.C.P.) 3 Fruit Research Station, 3-5 Horticultorilor, Cluj-Napoca 400454, Romania * Author to whom correspondence should be addressed; E-Mail: [email protected]; Tel: +4-0264-401-775; Fax: +4-0264-401-768. Received: 22 July 2011; in revised form: 20 August 2011 / Accepted: 8 September 2011 / Published: 15 September 2011 Abstract: The Chi-Square test (χ2 test) is a family of tests based on a series of assumptions and is frequently used in the statistical analysis of experimental data. The aim of our paper was to present solutions to common problems when applying the Chi-square tests for testing goodness-of-fit, homogeneity and independence. The main characteristics of these three tests are presented along with various problems related to their application. The main problems identified in the application of the goodness-of-fit test were as follows: defining the frequency classes, calculating the X2 statistic, and applying the χ2 test. -

Quantile Regression for Overdispersed Count Data: a Hierarchical Method Peter Congdon
Congdon Journal of Statistical Distributions and Applications (2017) 4:18 DOI 10.1186/s40488-017-0073-4 RESEARCH Open Access Quantile regression for overdispersed count data: a hierarchical method Peter Congdon Correspondence: [email protected] Abstract Queen Mary University of London, London, UK Generalized Poisson regression is commonly applied to overdispersed count data, and focused on modelling the conditional mean of the response. However, conditional mean regression models may be sensitive to response outliers and provide no information on other conditional distribution features of the response. We consider instead a hierarchical approach to quantile regression of overdispersed count data. This approach has the benefits of effective outlier detection and robust estimation in the presence of outliers, and in health applications, that quantile estimates can reflect risk factors. The technique is first illustrated with simulated overdispersed counts subject to contamination, such that estimates from conditional mean regression are adversely affected. A real application involves ambulatory care sensitive emergency admissions across 7518 English patient general practitioner (GP) practices. Predictors are GP practice deprivation, patient satisfaction with care and opening hours, and region. Impacts of deprivation are particularly important in policy terms as indicating effectiveness of efforts to reduce inequalities in care sensitive admissions. Hierarchical quantile count regression is used to develop profiles of central and extreme quantiles according to specified predictor combinations. Keywords: Quantile regression, Overdispersion, Poisson, Count data, Ambulatory sensitive, Median regression, Deprivation, Outliers 1. Background Extensions of Poisson regression are commonly applied to overdispersed count data, focused on modelling the conditional mean of the response. However, conditional mean regression models may be sensitive to response outliers. -

Robust Linear Regression: a Review and Comparison Arxiv:1404.6274
Robust Linear Regression: A Review and Comparison Chun Yu1, Weixin Yao1, and Xue Bai1 1Department of Statistics, Kansas State University, Manhattan, Kansas, USA 66506-0802. Abstract Ordinary least-squares (OLS) estimators for a linear model are very sensitive to unusual values in the design space or outliers among y values. Even one single atypical value may have a large effect on the parameter estimates. This article aims to review and describe some available and popular robust techniques, including some recent developed ones, and compare them in terms of breakdown point and efficiency. In addition, we also use a simulation study and a real data application to compare the performance of existing robust methods under different scenarios. arXiv:1404.6274v1 [stat.ME] 24 Apr 2014 Key words: Breakdown point; Robust estimate; Linear Regression. 1 Introduction Linear regression has been one of the most important statistical data analysis tools. Given the independent and identically distributed (iid) observations (xi; yi), i = 1; : : : ; n, 1 in order to understand how the response yis are related to the covariates xis, we tradi- tionally assume the following linear regression model T yi = xi β + "i; (1.1) where β is an unknown p × 1 vector, and the "is are i.i.d. and independent of xi with E("i j xi) = 0. The most commonly used estimate for β is the ordinary least square (OLS) estimate which minimizes the sum of squared residuals n X T 2 (yi − xi β) : (1.2) i=1 However, it is well known that the OLS estimate is extremely sensitive to the outliers. -

A Guide to Robust Statistical Methods in Neuroscience
A GUIDE TO ROBUST STATISTICAL METHODS IN NEUROSCIENCE Authors: Rand R. Wilcox1∗, Guillaume A. Rousselet2 1. Dept. of Psychology, University of Southern California, Los Angeles, CA 90089-1061, USA 2. Institute of Neuroscience and Psychology, College of Medical, Veterinary and Life Sciences, University of Glasgow, 58 Hillhead Street, G12 8QB, Glasgow, UK ∗ Corresponding author: [email protected] ABSTRACT There is a vast array of new and improved methods for comparing groups and studying associations that offer the potential for substantially increasing power, providing improved control over the probability of a Type I error, and yielding a deeper and more nuanced understanding of data. These new techniques effectively deal with four insights into when and why conventional methods can be unsatisfactory. But for the non-statistician, the vast array of new and improved techniques for comparing groups and studying associations can seem daunting, simply because there are so many new methods that are now available. The paper briefly reviews when and why conventional methods can have relatively low power and yield misleading results. The main goal is to suggest some general guidelines regarding when, how and why certain modern techniques might be used. Keywords: Non-normality, heteroscedasticity, skewed distributions, outliers, curvature. 1 1 Introduction The typical introductory statistics course covers classic methods for comparing groups (e.g., Student's t-test, the ANOVA F test and the Wilcoxon{Mann{Whitney test) and studying associations (e.g., Pearson's correlation and least squares regression). The two-sample Stu- dent's t-test and the ANOVA F test assume that sampling is from normal distributions and that the population variances are identical, which is generally known as the homoscedastic- ity assumption. -

STAT 830 the Basics of Nonparametric Models The
STAT 830 The basics of nonparametric models The Empirical Distribution Function { EDF The most common interpretation of probability is that the probability of an event is the long run relative frequency of that event when the basic experiment is repeated over and over independently. So, for instance, if X is a random variable then P (X ≤ x) should be the fraction of X values which turn out to be no more than x in a long sequence of trials. In general an empirical probability or expected value is just such a fraction or average computed from the data. To make this precise, suppose we have a sample X1;:::;Xn of iid real valued random variables. Then we make the following definitions: Definition: The empirical distribution function, or EDF, is n 1 X F^ (x) = 1(X ≤ x): n n i i=1 This is a cumulative distribution function. It is an estimate of F , the cdf of the Xs. People also speak of the empirical distribution of the sample: n 1 X P^(A) = 1(X 2 A) n i i=1 ^ This is the probability distribution whose cdf is Fn. ^ Now we consider the qualities of Fn as an estimate, the standard error of the estimate, the estimated standard error, confidence intervals, simultaneous confidence intervals and so on. To begin with we describe the best known summaries of the quality of an estimator: bias, variance, mean squared error and root mean squared error. Bias, variance, MSE and RMSE There are many ways to judge the quality of estimates of a parameter φ; all of them focus on the distribution of the estimation error φ^−φ. -

Robust Bayesian General Linear Models ⁎ W.D
www.elsevier.com/locate/ynimg NeuroImage 36 (2007) 661–671 Robust Bayesian general linear models ⁎ W.D. Penny, J. Kilner, and F. Blankenburg Wellcome Department of Imaging Neuroscience, University College London, 12 Queen Square, London WC1N 3BG, UK Received 22 September 2006; revised 20 November 2006; accepted 25 January 2007 Available online 7 May 2007 We describe a Bayesian learning algorithm for Robust General Linear them from the data (Jung et al., 1999). This is, however, a non- Models (RGLMs). The noise is modeled as a Mixture of Gaussians automatic process and will typically require user intervention to rather than the usual single Gaussian. This allows different data points disambiguate the discovered components. In fMRI, autoregressive to be associated with different noise levels and effectively provides a (AR) modeling can be used to downweight the impact of periodic robust estimation of regression coefficients. A variational inference respiratory or cardiac noise sources (Penny et al., 2003). More framework is used to prevent overfitting and provides a model order recently, a number of approaches based on robust regression have selection criterion for noise model order. This allows the RGLM to default to the usual GLM when robustness is not required. The method been applied to imaging data (Wager et al., 2005; Diedrichsen and is compared to other robust regression methods and applied to Shadmehr, 2005). These approaches relax the assumption under- synthetic data and fMRI. lying ordinary regression that the errors be normally (Wager et al., © 2007 Elsevier Inc. All rights reserved. 2005) or identically (Diedrichsen and Shadmehr, 2005) distributed. In Wager et al. -

Approximate Maximum Likelihood Method for Frequency Estimation
Statistica Sinica 10(2000), 157-171 APPROXIMATE MAXIMUM LIKELIHOOD METHOD FOR FREQUENCY ESTIMATION Dawei Huang Queensland University of Technology Abstract: A frequency can be estimated by few Discrete Fourier Transform (DFT) coefficients, see Rife and Vincent (1970), Quinn (1994, 1997). This approach is computationally efficient. However, the statistical efficiency of the estimator de- pends on the location of the frequency. In this paper, we explain this approach from a point of view of an Approximate Maximum Likelihood (AML) method. Then we enhance the efficiency of this method by using more DFT coefficients. Compared to 30% and 61% efficiency in the worst cases in Quinn (1994) and Quinn (1997), respectively, we show that if 13 or 25 DFT coefficients are used, AML will achieve at least 90% or 95% efficiency for all frequency locations. Key words and phrases: Approximate Maximum Likelihood, discrete Fourier trans- form, efficiency, fast algorithm, frequency estimation, semi-sufficient statistics. 1. Introduction A model that has been discussed widely in Time Series Analysis and Signal Processing is the following: xt = Acos(tω + φ)+ut,t=0,...,T − 1, (1) where 0 <A,0 <ω<π,and {ut} is a stationary sequence satisfying certain conditions to be specified later. The objective is to estimate the frequency ω from the observations {xt}. After obtaining an estimator of the frequency, the amplitude A and the phase φ can be estimated by a standard linear least squares method. Two topics have been of interest in the study of this model: estimation efficiency and computational complexity. Following the idea of Best Asymp- totic Normal estimation (BAN), the efficiency hereafter is measured by the ratio of the Cramer - Rao Bound (CRB) for unbiased estimators over the variance of the asymptotic distribution of the estimator.