Iot Communications a 5G Smart Cities Case Study Approach
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Configuring DNS
Configuring DNS The Domain Name System (DNS) is a distributed database in which you can map hostnames to IP addresses through the DNS protocol from a DNS server. Each unique IP address can have an associated hostname. The Cisco IOS software maintains a cache of hostname-to-address mappings for use by the connect, telnet, and ping EXEC commands, and related Telnet support operations. This cache speeds the process of converting names to addresses. Note You can specify IPv4 and IPv6 addresses while performing various tasks in this feature. The resource record type AAAA is used to map a domain name to an IPv6 address. The IP6.ARPA domain is defined to look up a record given an IPv6 address. • Finding Feature Information, page 1 • Prerequisites for Configuring DNS, page 2 • Information About DNS, page 2 • How to Configure DNS, page 4 • Configuration Examples for DNS, page 13 • Additional References, page 14 • Feature Information for DNS, page 15 Finding Feature Information Your software release may not support all the features documented in this module. For the latest caveats and feature information, see Bug Search Tool and the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the feature information table at the end of this module. Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required. -

Adopting Encrypted DNS in Enterprise Environments
National Security Agency | Cybersecurity Information Adopting Encrypted DNS in Enterprise Environments Executive summary Use of the Internet relies on translating domain names (like “nsa.gov”) to Internet Protocol addresses. This is the job of the Domain Name System (DNS). In the past, DNS lookups were generally unencrypted, since they have to be handled by the network to direct traffic to the right locations. DNS over Hypertext Transfer Protocol over Transport Layer Security (HTTPS), often referred to as DNS over HTTPS (DoH), encrypts DNS requests by using HTTPS to provide privacy, integrity, and “last mile” source authentication with a client’s DNS resolver. It is useful to prevent eavesdropping and manipulation of DNS traffic. While DoH can help protect the privacy of DNS requests and the integrity of responses, enterprises that use DoH will lose some of the control needed to govern DNS usage within their networks unless they allow only their chosen DoH resolver to be used. Enterprise DNS controls can prevent numerous threat techniques used by cyber threat actors for initial access, command and control, and exfiltration. Using DoH with external resolvers can be good for home or mobile users and networks that do not use DNS security controls. For enterprise networks, however, NSA recommends using only designated enterprise DNS resolvers in order to properly leverage essential enterprise cybersecurity defenses, facilitate access to local network resources, and protect internal network information. The enterprise DNS resolver may be either an enterprise-operated DNS server or an externally hosted service. Either way, the enterprise resolver should support encrypted DNS requests, such as DoH, for local privacy and integrity protections, but all other encrypted DNS resolvers should be disabled and blocked. -

Chapter 2. Application Layer Table of Contents 1. Context
Chapter 2. Application Layer Table of Contents 1. Context ........................................................................................................................................... 1 2. Introduction .................................................................................................................................... 2 3. Objectives ....................................................................................................................................... 2 4. Network application software ....................................................................................................... 2 5. Process communication ................................................................................................................. 3 6. Transport Layer services provided by the Internet ....................................................................... 3 7. Application Layer Protocols ........................................................................................................... 4 8. The web and HTTP .......................................................................................................................... 4 8.1. Web Terminology ................................................................................................................... 5 8.2. Overview of HTTP protocol .................................................................................................... 6 8.3. HTTP message format ........................................................................................................... -

Analysis of Malware and Domain Name System Traffic
Analysis of Malware and Domain Name System Traffic Hamad Mohammed Binsalleeh A Thesis in The Department of Computer Science and Software Engineering Presented in Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy at Concordia University Montréal, Québec, Canada July 2014 c Hamad Mohammed Binsalleeh, 2014 CONCORDIA UNIVERSITY Division of Graduate Studies This is to certify that the thesis prepared By: Hamad Mohammed Binsalleeh Entitled: Analysis of Malware and Domain Name System Traffic and submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy complies with the regulations of this University and meets the accepted standards with respect to originality and quality. Signed by the final examining committee: Chair Dr. Christian Moreau External Examiner Dr. Nadia Tawbi Examiner to Program Dr. Lingyu Wang Examiner Dr. Peter Grogono Examiner Dr. Olga Ormandjieva Thesis Co-Supervisor Dr. Mourad Debbabi Thesis Co-Supervisor Dr. Amr Youssef Approved by Chair of the CSE Department 2014 Dean of Engineering ABSTRACT Analysis of Malware and Domain Name System Traffic Hamad Mohammed Binsalleeh Concordia University, 2014 Malicious domains host Command and Control servers that are used to instruct in- fected machines to perpetuate malicious activities such as sending spam, stealing creden- tials, and launching denial of service attacks. Both static and dynamic analysis of malware as well as monitoring Domain Name System (DNS) traffic provide valuable insight into such malicious activities and help security experts detect and protect against many cyber attacks. Advanced crimeware toolkits were responsible for many recent cyber attacks. In order to understand the inner workings of such toolkits, we present a detailed reverse en- gineering analysis of the Zeus crimeware toolkit to unveil its underlying architecture and enable its mitigation. -

Internet Domain Name System
IINNTTEERRNNEETT DDOOMMAAIINN NNAAMMEE SSYYSSTTEEMM http://www.tutorialspoint.com/internet_technologies/internet_domain_name_system.htm Copyright © tutorialspoint.com Overview When DNS was not into existence, one had to download a Host file containing host names and their corresponding IP address. But with increase in number of hosts of internet, the size of host file also increased. This resulted in increased traffic on downloading this file. To solve this problem the DNS system was introduced. Domain Name System helps to resolve the host name to an address. It uses a hierarchical naming scheme and distributed database of IP addresses and associated names IP Address IP address is a unique logical address assigned to a machine over the network. An IP address exhibits the following properties: IP address is the unique address assigned to each host present on Internet. IP address is 32 bits 4bytes long. IP address consists of two components: network component and host component. Each of the 4 bytes is represented by a number from 0 to 255, separated with dots. For example 137.170.4.124 IP address is 32-bit number while on the other hand domain names are easy to remember names. For example, when we enter an email address we always enter a symbolic string such as [email protected]. Uniform Resource Locator URL Uniform Resource Locator URL refers to a web address which uniquely identifies a document over the internet. This document can be a web page, image, audio, video or anything else present on the web. For example, www.tutorialspoint.com/internet_technology/index.html is an URL to the index.html which is stored on tutorialspoint web server under internet_technology directory. -

Secure Shell- Its Significance in Networking (Ssh)
International Journal of Application or Innovation in Engineering & Management (IJAIEM) Web Site: www.ijaiem.org Email: [email protected] Volume 4, Issue 3, March 2015 ISSN 2319 - 4847 SECURE SHELL- ITS SIGNIFICANCE IN NETWORKING (SSH) ANOOSHA GARIMELLA , D.RAKESH KUMAR 1. B. TECH, COMPUTER SCIENCE AND ENGINEERING Student, 3rd year-2nd Semester GITAM UNIVERSITY Visakhapatnam, Andhra Pradesh India 2.Assistant Professor Computer Science and Engineering GITAM UNIVERSITY Visakhapatnam, Andhra Pradesh India ABSTRACT This paper is focused on the evolution of SSH, the need for SSH, working of SSH, its major components and features of SSH. As the number of users over the Internet is increasing, there is a greater threat of your data being vulnerable. Secure Shell (SSH) Protocol provides a secure method for remote login and other secure network services over an insecure network. The SSH protocol has been designed to support many features along with proper security. This architecture with the help of its inbuilt layers which are independent of each other provides user authentication, integrity, and confidentiality, connection- oriented end to end delivery, multiplexes encrypted tunnel into several logical channels, provides datagram delivery across multiple networks and may optionally provide compression. Here, we have also described in detail what every layer of the architecture does along with the connection establishment. Some of the threats which Ssh can encounter, applications, advantages and disadvantages have also been mentioned in this document. Keywords: SSH, Cryptography, Port Forwarding, Secure SSH Tunnel, Key Exchange, IP spoofing, Connection- Hijacking. 1. INTRODUCTION SSH Secure Shell was first created in 1995 by Tatu Ylonen with the release of version 1.0 of SSH Secure Shell and the Internet Draft “The SSH Secure Shell Remote Login Protocol”. -

A Diversified Set of Security Features for XMPP Communication Systems
International Journal on Advances in Security, vol 6 no 3 & 4, year 2013, http://www.iariajournals.org/security/ 99 A Diversified Set of Security Features for XMPP Communication Systems Useful in Cloud Computing Federation Antonio Celesti, Massimo Villari, and Antonio Puliafito DICIEAMA, University of Messina Contrada di Dio, S. Agata, 98166 Messina, Italy. e-mail: facelesti, mvillari, apuliafi[email protected] Abstract—Nowadays, in the panorama of Cloud Computing, Presence Protocol (XMPP), i.e., an open-standard commu- finding a right compromise between interactivity and security nications protocol for message-oriented middleware based is not trivial at all. Currently, most of Cloud providers base on the XML (Extensible Markup Language). On one hand, their communication systems on the web service technology. The problem is that both Cloud architectures and services the XMPP is able to overcome the disadvantages of web have started as simple but they are becoming increasingly services in terms of performance, but on the other hand complex. Consequently, web services are often inappropriate. it lacks of native security features for addressing the new Recently, many operators in both academia and industry are emerging Cloud computing scenarios. evaluating the eXtensible Messaging and Presence Protocol for In this paper, we discuss how the XMPP can be adopted the implementation of Cloud communication systems. In fact, the XMPP offers many advantages in term of real-time capa- for the development of secure Cloud communication sys- bilities, efficient data distribution, service discovery, and inter- tems. In particular, we combine and generalize the assump- domain communication compared to web service technologies. tions made in our previous works respectively regarding how Nevertheless, the protocol lacks of native security features. -

Domain Name System System Work?
What is the DNS? - how it works Isaac Maposa | Dev Anand Teelucksingh | Beran Gillen Community Onboarding Program | 11 March 2017 Agenda 1 2 3 What is the Domain Structure of the How does the Name System? Domain Name Domain Name System System Work? 4 5 6 Who makes the Stakeholders in the Engage with ICANN Domain Name Domain Name ??? System Work? System. | 2 What is the Domain Name System (DNS)? The Internet, what is it..? ● The Internet is a network of networks that interconnects devices to exchange information. ● In order to “talk” to each other, all of these devices must have a unique numerical address called an Internet Protocol address or IP Address. An example of an IP address is 94.127.53.132 ● When you visit a website from your browser, you are requesting the website from your device’s IP address to the web server’s IP address. ● However, you don’t type in the ip address of the web server, rather the domain name of for example www.google.com ● In so doing, you have queried the DNS. ● So what is this DNS???? | 4 What is the Domain Name System? ● The Domain Name System or DNS overcomes this problem of remembering IP addresses by mapping domain names to IP addresses. ● While this sounds like a phone book, it is not a centralised database. ● The DNS is a distributed database across a hierarchy of networks of servers and provide ways for devices and software (like browsers and email) to query the DNS to get an IP address. ● Domain names must be unique. -

Electronic Mail
Electronic Mail • The protocols used for Internet email can be divided into three broad categories transfer program interface application interface application 33 The Simple Mail Transfer Protocol (()SMTP) • The Simple Mail Transfer Protocol (SMTP) is the standard protocol that a mail transfer program uses • SMTP can be characterized as: – Follows a stream paradigm – Uses textual control messages – Only transfers text messages – Allows a sender to specify recipients’ names and check each name • SMTP can sen d a s ing le message to mu ltilltiple rec iiipien ts – The protocol allows a client to list users and then send a single copy of a message for all users on the list • SMTP has a restriction to send only textual content – MIME standard that allows email to include attachments such as graphic images or binary files – MIME: Multipurpose Internet Mail Extension 34 Response of the server with a code Establishing a session! linefeed and Carriage Return John (on example.edu) is sending an email to Math and Paul on somewhere.com 35 linefeed and Carriage Return Other commands 36 ISPs, Mail Servers, and Mail Access • ISPs began offer email services – An ISP runs an email server and provides a mailbox for each user • each ISP provides interface that allows a user to access their mailbox • Email access follows one of two forms: – A special-purpose email interface application (OUTLOOK) –A web browser that accesses an email web page 37 ISPs, Mail Servers, and Mail Access • The web browser approach is straightforward: – an ISP provides a special -

Federal Register/Vol. 80, No. 193/Tuesday, October 6, 2015
Federal Register / Vol. 80, No. 193 / Tuesday, October 6, 2015 / Notices 60363 identification card for access to federal and capabilities, but no earlier than Based Security for Electronic Mail facilities if such license or identification November 5, 2015. When the building Building Block. The full building block card is issued by a state that is block has been completed, NIST will description can be viewed at: http:// compliant with the REAL ID Act of 2005 post a notice on the Domain Name nccoe.nist.gov/DNSSecuredEmail. (P.L. 109–13), or by a state that has an System-Based Security for Electronic Interested parties should contact NIST extension for REAL ID compliance. Mail Building Block Web site at using the information provided in the NIST currently accepts other forms of http://nccoe.nist.gov/DNSSecuredEmail FOR FURTHER INFORMATION CONTACT federal-issued identification in lieu of a announcing the completion of the section of this notice. NIST will then state-issued driver’s license. For building block and informing the public provide each interested party with a detailed information please contact Ms. that it will no longer accept letters of letter of interest template, which the Young or visit: http://www.nist.gov/ interest for this building block. party must complete, certify that it is public_affairs/visitor/. ADDRESSES: The NCCoE is located at accurate, and submit to NIST and which 9600 Gudelsky Drive, Rockville, MD identifies the organization requesting Richard Cavanagh, 20850. Letters of interest must be participation in the Domain Name Acting Associate Director for Laboratory submitted to [email protected] System-Based Security for Electronic Programs. -

M-Link Administration Guide M-Link Administration Guide Ii
MLINKADM-17.0 M-Link Administration Guide M-Link Administration Guide ii Table of Contents Chapter 1 Isode M-Link Overview............................................................................................. 1 This chapter gives an overview of Isode M-Link. Chapter 2 M-Link: Getting Started........................................................................................... 4 This chapter discusses M-Link Server creation. Chapter 3 Domains.................................................................................................................... 47 This chapter describes how M-Link Console can be used to view, modify, create and delete domains. Chapter 4 Con®guring Groups................................................................................................. 52 This chapter discusses how M-Link Console can be used to view, modify, create and delete groups for an M-Link service. Chapter 5 Con®guring TLS...................................................................................................... 54 This chapter discusses how to manage TLS con®guration of an M-Link service. Chapter 6 M-Link User Management...................................................................................... 68 This chapter discusses provisioning of user, user authentication and authorization, and groups. Chapter 7 Security Labels in XMPP........................................................................................ 90 This chapter discusses M-Link con®guration of security labels. Chapter 8 M-Link Edge, Peers -
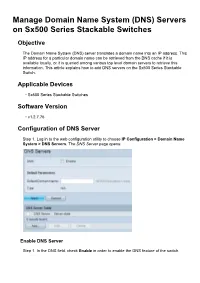
Manage Domain Name System (DNS) Servers on Sx500 Series Stackable Switches
Manage Domain Name System (DNS) Servers on Sx500 Series Stackable Switches Objective The Domain Name System (DNS) server translates a domain name into an IP address. This IP address for a particular domain name can be retrieved from the DNS cache if it is available locally, or it is queried among various top level domain servers to retrieve this information. This article explains how to add DNS servers on the Sx500 Series Stackable Switch. Applicable Devices • Sx500 Series Stackable Switches Software Version • v1.2.7.76 Configuration of DNS Server Step 1. Log in to the web configuration utility to choose IP Configuration > Domain Name System > DNS Servers. The DNS Server page opens: Enable DNS Server Step 1. In the DNS field, check Enable in order to enable the DNS feature of the switch. Step 2. In the Default Domain Name field in the Default Parameters area, enter the domain name that you want to configure as Fully Qualified Domain Name (FQDN). The switch appends this domain name to non-fully qualified domain names to make them FQDNs. Note: The switch identifies the default domain name server type in the Type field. • DHCP — Default name is given dynamically by the DHCP Server. • Static — Default name is user-defined. • N/A — No default domain name. Step 3. Click Apply to save the DNS settings. Add DNS Server Step 1. In the DNS Server Table, click Add at the bottom of the table to add DNS servers so that the switch can query the IP address of domain names. Step 2. In the IP Version field, click either the Version 4 radio button or the Version 6 radio button based upon the type of server IP address (IPv4 or IPv6).