Flash Memory 'Bumping'
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

08-02-2021 Agenda Packet.Pdf
AGENDA DELANO CITY COUNCIL REGULAR MEETING August 2, 2021 DELANO CITY HALL, 1015 – 11th Avenue 5:30 P.M. IN ACCORDANCE WITH THE GOVERNOR NEWSOM’S EXECUTIVE ORDER #N-08-21, THIS MEETING WILL BE CONDUCTED FULLY VIA TELECONFERENCE, DUE TO THE CURRENT RESTRICTIONS BY SAID ORDER AND CENTERS FOR DISEASES CONTROL AND PREVENTION (CDC) GUIDELINES. THE PUBLIC WILL HAVE ACCESS TO CALL IN, LISTEN TO THE MEETING AND PROVIDE PUBLIC COMMENT. IN ACCORDANCE WITH GOVERNOR NEWSOM’S EXECUTIVE ORDER N-08-21, THERE WILL NOT BE A PHYSICAL LOCATION FROM WHICH THE PUBLIC MAY ATTEND. IN ORDER TO CALL INTO TH E MEETING PLEASE SEE THE DIRECTIONS BELOW. CALL TO ORDER INVOCATION FLAG SALUTE ROLL CALL PRESENTATIONS AND AWARDS Featured Pet – Tabitha PUBLIC COMMENT: The public may address the Council on items which do not appear on the agenda. The Council cannot respond nor take action on items that do not appear on the agenda but may refer the item to staff for further study or for placement on a future agenda. Comments are limited to 3 minutes for each person and 15 minutes on each subject. Please state your name and address for the record. CONSENT AGENDA: The Consent Agenda consists of items that in staff’s opinion are routine and non-controversial. These items are approved in one motion unless a Councilmember or member of the public removes a particular item. 1) Authorization to waive the reading of any ordinance in its entirety and consenting to the reading of such ordinances by title only 2) Warrant Register in the amount of $3,044,398.54 3) Minutes of regular City Council Meeting of July 19, 2021 4) Acceptance and Approval of the City of Delano Quarterly Investment Report 5) Resolution adopting the 2020-2021 Kern Multi-Jurisdiction Hazard Mitigation Plan (MJHMP) 6) Approval of agreement with Youth Educational Sports, Inc. -

8-Bit All Flash 78K0 Microcontrollers 78K0S
For further information, please contact: NEC Electronics Corporation 1753, Shimonumabe, Nakahara-ku, Kawasaki, Kanagawa 211-8668, Japan Tel: 044-435-5111 http://www.necel.com/ [America] [Europe] [Asia & Oceania] NEC Electronics America, Inc. NEC Electronics (Europe) GmbH NEC Electronics (China) Co., Ltd 8-bit All Flash 2880 Scott Blvd. Arcadiastrasse 10 7th Floor, Quantum Plaza, No. 27 ZhiChunLu Haidian Santa Clara, CA 95050-2554, U.S.A. 40472 Düsseldorf, Germany District, Beijing 100083, P.R.China Tel: 408-588-6000 Tel: 0211-65030 Tel: 010-8235-1155 800-366-9782 http://www.eu.necel.com/ http://www.cn.necel.com/ http://www.am.necel.com/ Hanover Office Shanghai Branch Podbielskistrasse 166 B Room 2509-2510, Bank of ChinaTower, 30177 Hannover 200Y incheng Road Central, Tel: 0 511 33 40 2-0 Pudong New Area, Shanghai, P.R.China P.C:200120 Tel:021-5888-5400 Munich Office http://www.cn.necel.com/ Werner-Eckert-Strasse 9 81829 München Shenzhen Branch Tel: 0 89 92 10 03-0 Unit 01, 39/F, Excellence Times Square Building, Stuttgart Office No. 4068 Yi Tian Road, Futian District, Shenzhen, Industriestrasse 3 P.R.China P.C:518048 70565 Stuttgart Tel:0755-8282-9800 Tel: 0 711 99 01 0-0 http://www.cn.necel.com/ United Kingdom Branch NEC Electronics Hong Kong Ltd. Cygnus House, Sunrise Parkway Unit 1601-1613, 16/F., Tower 2, Grand Century Place, Linford Wood, Milton Keynes 193 Prince Edward Road West, Mongkok, Kowloon, Hong Kong MK14 6NP, U.K. Tel: 2886-9318 Tel: 01908-691-133 http://www.hk.necel.com/ Succursale Française 9, rue Paul Dautier, B.P. -

Familias De Microcontroladores
INTRODUCCION Un microcontrolador es un circuito integrado tiene en su interior todas las características de un computador, es decir, programa y circuitos periféricos para CPU, RAM, una memoria de entrada y salida. Muy regularmente los microcontroladores poseen además convertidores análogo - digital, temporizadores, contadores y un sistema para permitir la comunicación en serie y en paralelo. Se pueden crear muchas aplicaciones con los microcontroladores. Estas aplicaciones de los microcontroladores son ilimitadas, entre ellas podemos mencionar: sistemas de alarmas, iluminación, paneles publicitarios, etc. Controles automáticos para la Industria en general. Entre ellos control de motores DC/AC y motores de paso a paso, control de máquinas, control de temperatura, tiempo; adquisición de datos mediante sensores, etc. HISTORIA El primer microprocesador fue el Intel 4004 de 4 bits, lanzado en 1971, seguido por el Intel 8008 y otros más capaces. Sin embargo, ambos procesadores requieren circuitos adicionales para implementar un sistema de trabajo, elevando el costo del sistema total. Los ingenieros de Texas Instruments Gary Boone y Michael Cochran lograron crear el primer microcontrolador, TMS 1000, en 1971; fue comercializado en 1974. Combina memoria ROM, memoria RAM, microprocesador y reloj en un chip y estaba destinada a los sistemas embebidos.2 Debido en parte a la existencia del TMS 1000,3 Intel desarrolló un sistema de ordenador en un chip optimizado para aplicaciones de control, el Intel 8048, que comenzó a comercializarse en 1977.3 Combina memoria RAM y ROM en el mismo chip y puede encontrarse en más de mil millones de teclados de compatible IBM PC, y otras numerosas aplicaciones. El en ese momento presidente de Intel, Luke J. -

Renesas Microcomputer All Flash 78K Microcontroller
Renesas Microcomputer All Flash 78K Renesas Microcomputer Sales Strategic Planning Div. Nippon Bldg., 2-6-2, Ohte-machi, Chiyoda-ku, Tokyo 100-0004, Japan Notes: 1. All information included in this document is current as of the date this document is issued. Such information, however, is subject to change without any prior notice. Before purchasing or using any Renesas Electronics products listed herein, please confirm the latest product information with a Renesas Electronics sales office. Also, please pay regular and careful attention to additional and different information to be disclosed by Renesas Electronics such as that disclosed through our website. 2. Renesas Electronics does not assume any liability for infringement of patents, copyrights, or other intellectual property rights of third parties by or arising from the use of Renesas Electronics products or All Flash 78K technical information described in this document. No license, express, implied or otherwise, is granted hereby under any patents, copyrights or other intellectual property rights of Renesas Electronics or others. 3. You should not alter, modify, copy, or otherwise misappropriate any Renesas Electronics product, whether in whole or in part. Microcontroller 4. Descriptions of circuits, software and other related information in this document are provided only to illustrate the operation of semiconductor products and application examples. You are fully responsible for the incorporation of these circuits, software, and information in the design of your equipment. Renesas Electronics assumes no responsibility for any losses incurred by you or third parties arising from the use of these circuits, software, or information. 5. When exporting the products or technology described in this document, you should comply with the applicable export control laws and regulations and follow the procedures required by such laws and regulations. -

The Anatomy of the ARM Cortex-M0+ Processor
The Anatomy of the ARM Cortex-M0+ Processor Joseph Yiu Embedded Technology Specialist 1 What is the Cortex-M0+ Processor? . 2009 – ARM® Cortex™-M0 processor released . Low gate count . High performance . Easy to use . Debug features . 2012 – Cortex-M0+ processor released . Same instruction set . Supports all existing features of Cortex-M0 . New features . Higher energy efficiency . Ready for future applications 2 What’s new? . Even better power efficiency . Clean sheet design – 2 stage pipeline . Better performance at the same frequency . Unprivileged execution level . 8 region Memory Protection Unit (MPU) . Faster I/O accesses . Vector table relocation . Low cost trace solution available . Various silicon integration features (e.g.16-bit flash support) 3 Why a New Design? Energy is the Key . Embedded products need even longer battery life . Need to have lower active power . But not compromise on performance . Low power control applications . Need to have faster I/O capability . But not higher operating frequency . Smarter designs . Need more sophisticated features . But not bigger silicon 4 Overview of the Cortex-M0+ Processor . Processor . ARMv6-M architecture . Easy to use, C friendly . Cortex-M series compatibility . Nested Vectored Interrupt Controller (NVIC) . Flexible interrupt handling . WIC support . Memory Protection Unit (MPU) . Debug from just 2 pins 5 Compact Instruction Set . Only 56 Instructions . 100% compatible with existing Cortex-M0 processor . Mostly 16-bit instructions . All instructions operate on the 32-bit registers . Option for single cycle 32x32 Maximum reuse of multiply Upwardexisting compatibility tools to andthe ARM Cortexecosystem-M3/Cortex -M4 6 Interrupt Handling . Nested Vectored Interrupt Cortex-M0+ Controller (NVIC) NMI NVIC Core . -

Rodney B. Bonser
Rodney B. Bonser Embedded System Programming and Engineering: System Level Firmware Design Application Firmware Programming Hardware Test Firmware C and Assembly Language Programming Real-Time Operating System (RTOS) Programming and Integration Embedded Linux Applications Nucleus Plus, CMX I/O Drivers Tensilica Xtensa, ARM, Motorola 68XXX Software State Machines GDB and IDE Debugging Codewright, CodeWarrior PERL and C Software Utilities State & Task Diagramming Firmware Documentation EXPERIENCE Please Note: My expertise varies among the following tasks. Please inquire about experience with a particular skill or task. ALLERO Design Meadow Vista, CA 1/02 - Present Consulting Engineer Software: Embedded Linux on single board computer platform Temperature and humidity sensor monitoring PERL and C daemons & utilities Hardware: Portable preamp / amp for electric guitar Luxxon Corporation Mountain View, CA 12/00 - 1/02 Senior Firmware Engineer Firmware for the LUX2 Multimedia Processor chip Firmware: Member of the system level firmware design team Assembly and C language for Tensilica Xtensa RISC processor Programming under the Nucleus Plus RTOS Video / Audio synchronization Test and design verification firmware for the chip audio subsystem Debugging with GDB CodeWright IDE Software: PERL and C utilities Documentation: Firmware descriptions State & task relationship diagrams Wireless Link, Inc. Milpitas, CA 3/99 - 5/00 Consultant Engineering for cellular telephone products Firmware: Assembly and C language for ARM RISC processor Ported Nucleus Plus RTOS to ARM-based platform Simulated RTOS port under ARMulator (ARM processor simulator) CodeWarrior IDE Assembly and C language for NEC 78K IV microprocessor Multiple tasks running under CMX RTOS Remote programming of firmware into FLASH memory Software state machine for Telephone ringing Hook detection Tone generation DTMF detection and decoding CodeWright IDE Hardware: Level shifter board for serial communication Documentation: Firmware descriptions State & task relationship diagrams Schematic Vista Labs, Inc. -

MIPS, HPS, Two-Level Branch Prediction, and Compressed Code RISC Processor
Awards ................................................................................................................................................................ Common Bonds: MIPS, HPS, Two-Level Branch Prediction, and Compressed Code RISC Processor ONUR MUTLU ETH Zurich RICH BELGARD ......We are continuing our series of of performance optimization on the com- sions made in the MIPS project that retrospectives for the 10 papers that piler and keep the hardware design sim- passed the test of time. The retrospective received the first set of MICRO Test of ple. The compiler is responsible for touches on the design tradeoffs made to Time (“ToT”) Awards in December generating and scheduling simple instruc- couple the hardware and the software, 2014.1,2 This issue features four retro- tions, which require little translation in the MIPS project’s effect on the later spectives written for six of the award- hardware to generate control signals to development of “fabless” semiconductor winning papers. We briefly introduce control the datapath components, which companies, and the use of benchmarks these papers and retrospectives and in turn keeps the hardware design simple. as a method for evaluating end-to-end hope that you will enjoy reading them as Thus, the instructions and hardware both performance of a system as, among much as we have. If anything ties these remain simple, whereas the compiler others, contributions of the MIPS project works together, it is the innovation they becomes much more important (and that have stood the test of time. delivered by taking a strong position in likely complex) because it must schedule the RISC/CISC debates of their decade. instructions well to ensure correct and High-Performance Systems We hope the IEEE Micro audience, espe- high-performance use of a simple pipe- The second retrospective addresses three cially younger generations, will find the line. -

TTL and CMOS Logic 74 Series
TTL and CMOS logic 74 Series TTL and CMOS logic 74 Series ! Datasheets ¡¡ CLICK HERE for the TTL and CMOS logic listings! CLICK HERE for links to other useful datasheet sites! This page contains links to datasheets for all the IC's used in my projects, click the part number to read the datasheet. Some of these I scanned myself, others are located on others' pages or the manufacturer's website. If there are any broken links tell me. To read these datasheets you need to install Adobe Acrobat if you haven't already done so. The scanned datasheets are sometimes easiest to read if you select "Actual Size" in Adobe Acrobat's "View" menu. A number of these parts are obsolete, and several more will probably become obsolete very soon. I have saved local copies of all of the datasheets linked here, so that they will be preserved if the manufacturers decide to remove the datasheets from their websites. In this case I will replace the URL with a local link. If you find any broken links, let me know. Many IC's are made by multiple manufacturers, and there have been many rounds of mergers, aquisitions and consolidations in the semiconductor industry. Therefore the manufacturers listed here are not necessarily the ones whose IC's I used, but in all cases chips from a different manufacturer should be interchangeable. In general 74nn chips and 74LSnn chips can also be interchanged, I simply used what was available to me at the time. Part Description Manufacturer Size Notes ¡¡ ¡¡ ¡¡ ¡¡ ¡¡ http://www.datasheet4u.com/TTL/TTL.html (1 z 22)1.10.2007 17:46:45 -
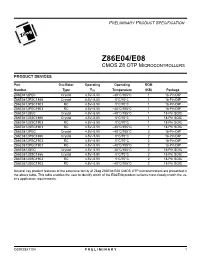
Z86e04/E08 1 Cmos Z8 Otp Microcontrollers
PRELIMINARY PRODUCT SPECIFICATION 1 Z86E04/E08 1 CMOS Z8 OTP MICROCONTROLLERS PRODUCT DEVICES Part Oscillator Operating Operating ROM Number Type VCC Temperature (KB) Package Z86E0412PEC Crystal 4.5V–5.5V –40°C/105°C 1 18-Pin DIP Z86E0412PSC1866 Crystal 4.5V–5.5V 0°C/70°C 1 18-Pin DIP Z86E0412PSC1903 RC 4.5V–5.5V 0°C/70°C 1 18-Pin DIP Z86E0412PEC1903 RC 4.5V–5.5V –40°C/105°C 1 18-Pin DIP Z86E0412SEC Crystal 4.5V–5.5V –40°C/105°C 1 18-Pin SOIC Z86E0412SSC1866 Crystal 4.5V–5.5V 0°C/70°C 1 18-Pin SOIC Z86E0412SSC1903 RC 4.5V–5.5V 0°C/70°C 1 18-Pin SOIC Z86E0412SEC1903 RC 4.5V–5.5V –40°C/105°C 1 18-Pin SOIC Z86E0812PEC Crystal 4.5V–5.5V –40°C/105°C 2 18-Pin DIP Z86E0812PSC1866 Crystal 4.5V–5.5V 0°C/70°C 2 18-Pin DIP Z86E0812PSC1903 RC 4.5V–5.5V 0°C/70°C 2 18-Pin DIP Z86E0812PEC1903 RC 4.5V–5.5V –40°C/105°C 2 18-Pin DIP Z86E0812SEC Crystal 4.5V–5.5V –40°C/105°C 2 18-Pin SOIC Z86E0812SSC1866 Crystal 4.5V–5.5V 0°C/70°C 2 18-Pin SOIC Z86E0812SSC1903 RC 4.5V–5.5V 0°C/70°C 2 18-Pin SOIC Z86E0812SEC1903 RC 4.5V–5.5V –40°C/105°C 2 18-Pin SOIC Several key product features of the extensive family of Zilog Z86E04/E08 CMOS OTP microcontrollers are presented in the above table. -

Renesas Mpus & Mcus 78K MCU Selection Guide
Renesas MPUs & MCUs 78K MCU Selection Guide www.renesas.com 2012.12 8-bit Single-Chip MCUs 78K0 and 78K0S MCUs Device Memory Clock I/O Bus Timer Serial Interface OCD Peripheral Functions Other ash fl C Commercial 2 C Applications Product name 2 I CSI CAN A/D converter IEBus name UART CSI, I CPU core I/O ports 8-bit timer ROM type UART, CSI UART, ΔΣ 16-bit timer Watch timer Watch Other timers PWM output External bus reception function (data/address) ROM size [KB] Other functions Watchdog timer Watchdog Multiplier/divider frequency [MHz] Emulation board RAM size [bytes] Real-time counter In-circuit emulator 8-bit A/D converter converter 8-bit D/A On-chip debugging Single voltage Maximum operating 10-bit A/D converter Package (size [mm]) UART supporting LIN UART [bits × bits, bits ÷ bits] On-chip oscillator [Hz] Subclock (32.768 kHz) 16-bit CSI with automatic transmission/ LCD [segments × commons] Power supply voltage [V] UART supporting LIN, CSI UART 78K0S/KU1+ μPD78F9200 1 Flash √ 128 10 8 M, − 8 −/− 11 −−−1 16 bits × 1, −−−−−−−−−−− − −4 −− −POC (2.1 V ± 0.1 V), 2.0 to 5.5 10-SSOP QB-MINI2 240 k 8 bits × 1 LVI (5.72) (MINICUBE2) μPD78F9201 2 78K0S QB-78K0SKX1 μPD78F9202 4 (IECUBE) μPD78F9500 1 − 8 bits × 1 − μPD78F9501 2 μPD78F9502 4 78K0S/KY1+ μPD78F9210 1 Flash √ 128 10 8 M, − 14 −/− 11 −−−1 16 bits × 1, −−−−−−−−−−− − −4 −− −POC (2.1 V ± 0.1 V), 2.0 to 5.5 16-SSOP 240 k 8 bits × 1 LVI Thickness: 1.44 mm, μPD78F9211 2 (5.72) 1.5 mm (4.4 × 5) μPD78F9212 4 16-WLBGA (2 × 2.3) 16-SDIP General Purpose (All Flash) (7.62) μPD78F9510 1 − 16-SSOP -

Cortex M7 Instruction Set
Cortex m7 instruction set Continue ARM Cortex-M0 and Microcontroller Cortex-M3 of NXP and Silicon Labs (Energy Micro) die from microcontrol STM32F100C4T6B IC.24 MHz ARM Cortex-M3 with 16 KB of flash memory, 4 KB of RAM. Manufactured by STMicroelectronics. ARM Cortex-M is a group of 32-bit RISC ARM processor cores licensed by Arm Holdings. These cores are optimized for low-cost and energy efficient microcontrollers that have been introduced into tens of billions of consumer devices. The cores consist of Cortex-M0, Cortex-M0, Cortex-M1, Cortex-M3, Cortex-M4, Cortex-M7, Cortex-M23, Cortex-M33, Cortex-M35P, Cortex-M55. The cores of Cortex-M4/M7/M33/M35P/M55 have a silicon version of FPU, and when incorporated into silicon, these nuclei are sometimes referred to as Cortex-Mx with FPU or Cortex-MxF, where x is the main number. 2004 Cortex-M3 2007 Cortex-M1 2009 Cortex-M0 2010 Cortex-M4 2012 Cortex-M0' 2014 Cortex-M7 2016 Cortex- M7 2016 Cortex-M0-M4 2014 Cortex-M7 2016 Cortex-M4 M2 3 2016 Cortex-M33 2018 Cortex-M35P 2020 Cortex-M See also: ARM Architecture and ARM Cortex-M Cores are ARM Cores, which are designed to be used in microcontrollers, ASICs, ASSPs, FPGAs, and SoCs. Cortex-M cores are commonly used as dedicated microcontrollers, but are also hidden inside SoC chips as power control controllers, i/O controllers, system controllers, touch screen controllers, smart battery controllers, and sensor controllers. While 8-bit microcontrollers have been very popular in the past, Cortex-M has slowly chipped away at the 8-bit market as prices for low-end Cortex-M chips have moved down. -
![[Upgrade to Revision] CS+ Integrated Development](https://docslib.b-cdn.net/cover/8257/upgrade-to-revision-cs-integrated-development-3238257.webp)
[Upgrade to Revision] CS+ Integrated Development
RENESAS TOOL NEWS [Upgrade to revision] R20TS0724EJ0100 Rev.1.00 CS+ Integrated Development Environment V8.06.00 Jul. 16, 2021 Overview We will be revising the CS+ integrated development environment from V8.05.00 to V8.06.00. 1. Version to Be Updated ➢ CubeSuite+ Common Programs: V1.00.00 to V1.03.00 and V2.00.00 to V2.02.00 ➢ CS+ Common Programs: V3.00.00 to V3.03.00, V4.00.00 to V4.03.00, V5.00.00, V6.00.00 to V6.01.00, V7.00.00, V8.00.01, V8.01.00 to V8.05.00 For how to confirm which version you currently have, refer to the following URL. https://www.renesas.com/cs+_ver 2. Topics of Revision Description The function described below has been added and enhanced in CS+ for CC. - Improvement of the MCU search function for dialog boxes such as the Create New Project dialog box (applicable MCUs: RH850 family, RX family, and RL78 family) The function was improved so that if a microcontroller name containing a detailed package code is entered in the microcontroller search box for the following dialog boxes, the microcontroller name containing package code"x" is hit: Create Project dialog box, Project Convert Setting dialog box, or Change Microcontroller dialog box Example: When "R5F51105AAF" is entered in the microcontroller search box, R5F51105AxFK is hit. 3. Items Revised 3.1 CS+ Common Programs (with building, debugging, analysis, and other capabilities) - The common programs of CS+ for CC (for RX, RH850, and RL78) have been updated from V8.05.00 to V8.06.00.