Windows NT/2000 History N Windows NT (Henceforth Just NT) Is Produced by Microsoft Co
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Windows XP History and Versions
Lecture 23: Windows XP History and Versions n Mid-80ies Microsoft and IBM cooperated to develop OS/2 n Windows XP is produced by Microsoft Co. n 1988 - Microsoft started to develop its own new technology (NT) OS n XP is multi-user, multi-process, preemptive multitasking OS, 30M lines of source code capable of running OS/2, Windows and Unix apps. Hired Dave Cutler - architect of DEC VAX/VMS to head the design n It is developed to support multiple platforms and targeted towards enterprise workstations and server market as well as n NT v. 3.1 first released commercially July 1993 desktops n NT v 4.0 adopted Windows 95 user interface, graphics code moved into kernel to improve performance n In today’s lecture n 2000 – improved networking and laptop support, support for plug-and- u XP’s predecessors, the history of XP design, XP versions play devices, support for more processors (up to 8) and memory, u design principles becomes true multi-user through terminal server u components n XP (released Oct 2001) – update for 2000 replacement for 95/98 F hardware abstraction layer u simplifies user interface, improved reliability, performance F executive improvements, partial 64-bit support F environmental subsystems n versions F file system u desktop: XP personal – 95/98 replacement, professional – advanced features like POSIX support, some network features 1 u server: .NET – support for web/print service, clusters, large memory2 and multiple processors Design goals Components n XP is microkernel-based, modular n security – NT was C-2 certified (US -

Unifying the User and Kernel Environments
Unifying the User and Kernel Environments Richard P. Draves Scott M. Cutshall March 12, 1997 Technical Report MSR-TR-97-10 Microsoft Research Microsoft Corporation One Microsoft Way Redmond, WA 98052 Unifying the User and Kernel Environments Richard P. Draves and Scott M. Cutshall Microsoft Research One Microsoft Way Redmond, WA 98052 http://www.research.microsoft.com Abstract Vendors of commercial operating systems today invest resources in two very different environments—one for user- level (application or server) programming and one for kernel-level (device driver or subsystem) programming. The kernel environment is typically more restrictive, with completely different interfaces and programming conventions. Based on our experience developing and deploying an operating system for an interactive TV system, we believe that it is desirable to unify the user and kernel environments. We structured our operating system to provide common programming and run-time environments for user-level code and kernel-level code. For example, modules loaded into the kernel did not have any restrictions on their use of shared libraries or stack space. We found that unifying the user and kernel environments with common interfaces and run-time requirements, common documentation, and a common debugger produced significant software-engineering benefits. In addition, we could transparently collocate trusted server code in the kernel to reduce memory usage and improve performance. 1. Introduction We advocate structuring operating systems to unify the user and kernel environments. The operating system should present a single environment, with common interfaces or APIs, common run-time characteristics for scheduling, paging, stack usage, and shared libraries, common debugger and development tools, etc. -

Roadmap for Section 1.2
Unit OS1: Overview of Operating Systems 1.2. The Evolution of Operating Systems Windows Operating System Internals - by David A. Solomon and Mark E. Russinovich with Andreas Polze Roadmap for Section 1.2. History of Operating Systems Tasks of an Operating System OS as extension of the hardware Main concepts: processes, files, system calls Operating system structuring 3 1 Operating Systems Concepts System software manages resources OS hides complexity of underlying hardware Layered architectures Banking Airline Web browser Application programs system reservation Command Compilers Editors interpreter System programs Operating system Machine language Microprogramming Hardware Physical devices 4 History of operating systems Batch processing The elements of the basic IBM 1401 system are the 1401 Processing Unit, 1402 Card Read-Punch, and 1403 Printer. Punching cards Multiprocessing programming Job 3 Job 2 Memory Job 1 partitions OS 5 2 The Evolution of Operating System Functionality Batch Job Processing Linkage of library routines to programs Management of files, I/O devices, secondary storage Multiprogramming Resource managment and sharing for multiple programs Quasi-simultaneous program execution Single user Multiuser/Timesharing Systems Management of multiple simultaneous users interconnected via terminals Fair resource management: CPU scheduling, spooling, mutual exclusion Real-Time Systems (process control systems) Management of time-critical processes High requirements with respect to reliability and availability 6 Tasks of an Operating -

VAX VMS at 20
1977–1997... and beyond Nothing Stops It! Of all the winning attributes of the OpenVMS operating system, perhaps its key success factor is its evolutionary spirit. Some would say OpenVMS was revolutionary. But I would prefer to call it evolutionary because its transition has been peaceful and constructive. Over a 20-year period, OpenVMS has experienced evolution in five arenas. First, it evolved from a system running on some 20 printed circuit boards to a single chip. Second, it evolved from being proprietary to open. Third, it evolved from running on CISC-based VAX to RISC-based Alpha systems. Fourth, VMS evolved from being primarily a technical oper- ating system, to a commercial operat- ing system, to a high availability mission-critical commercial operating system. And fifth, VMS evolved from time-sharing to a workstation environment, to a client/server computing style environment. The hardware has experienced a similar evolution. Just as the 16-bit PDP systems laid the groundwork for the VAX platform, VAX laid the groundwork for Alpha—the industry’s leading 64-bit systems. While the platforms have grown and changed, the success continues. Today, OpenVMS is the most flexible and adaptable operating system on the planet. What start- ed out as the concept of ‘Starlet’ in 1975 is moving into ‘Galaxy’ for the 21st century. And like the universe, there is no end in sight. —Jesse Lipcon Vice President of UNIX and OpenVMS Systems Business Unit TABLE OF CONTENTS CHAPTER I Changing the Face of Computing 4 CHAPTER II Setting the Stage 6 CHAPTER -

MICROSOFT WINDOWS Early Versions Main Articles: Windows 1.0
MICROSOFT WINDOWS Early versions Main articles: Windows 1.0, Windows 2.0, and Windows 2.1x Windows 1.0, the first version, released in 1985 The history of Windows dates back to September 1981, when Chase Bishop, a computer scientist, designed the first model of an electronic device and project "Interface Manager" was started. It was announced in November 1983 (after the Apple Lisa, but before the Macintosh) under the name "Windows", but Windows 1.0 was not released until November 1985.[5] Windows 1.0 achieved little popularity and was to compete with Apple's own operating system. Windows 1.0 is not a complete operating system; rather, it extends MS-DOS. The shell of Windows 1.0 is a program known as the MS- DOS Executive. Components included Calculator, Calendar, Cardfile, Clipboard viewer, Clock, Control Panel, Notepad, Paint, Reversi, Terminal and Write. Windows 1.0 does not allow overlapping windows. Instead all windows are tiled. Only modal dialog boxes may appear over other windows. Windows 2.0 was released in December 1987 and was more popular than its predecessor. It features several improvements to the user interface and memory management.[citation needed] Windows 2.03 changed the OS from tiled windows to overlapping windows. The result of this change led to Apple Computer filing a suit against Microsoft alleging infringement on Apple's copyrights.[6][7] Windows 2.0 also introduced more sophisticated keyboard shortcuts and could make use of expanded memory. Windows 2.1 was released in two different versions: Windows/286 and Windows/386. Windows/386 uses the virtual 8086 mode of Intel 80386 to multitask several DOS programs and the paged memory model to emulate expanded memory using available extended memory. -

Thesis May Never Have Been Completed
UvA-DARE (Digital Academic Repository) Digital Equipment Corporation (DEC): A case study of indecision, innovation and company failure Goodwin, D.T. Publication date 2016 Document Version Final published version Link to publication Citation for published version (APA): Goodwin, D. T. (2016). Digital Equipment Corporation (DEC): A case study of indecision, innovation and company failure. General rights It is not permitted to download or to forward/distribute the text or part of it without the consent of the author(s) and/or copyright holder(s), other than for strictly personal, individual use, unless the work is under an open content license (like Creative Commons). Disclaimer/Complaints regulations If you believe that digital publication of certain material infringes any of your rights or (privacy) interests, please let the Library know, stating your reasons. In case of a legitimate complaint, the Library will make the material inaccessible and/or remove it from the website. Please Ask the Library: https://uba.uva.nl/en/contact, or a letter to: Library of the University of Amsterdam, Secretariat, Singel 425, 1012 WP Amsterdam, The Netherlands. You will be contacted as soon as possible. UvA-DARE is a service provided by the library of the University of Amsterdam (https://dare.uva.nl) Download date:26 Sep 2021 Digital Equipment Corporation (DEC) (DEC) Corporation Digital Equipment David Thomas David Goodwin Digital Equipment Corporation (DEC): A Case Study of Indecision, Innovation and Company Failure David Thomas Goodwin Digital Equipment Corporation (DEC): A Case Study of Indecision, Innovation and Company Failure David Thomas Goodwin 1 Digital Equipment Corporation (DEC): A Case Study of Indecision, Innovation and Company Failure ACADEMISCH PROEFSCHRIFT ter verkrijging van de graad van doctor aan de Universiteit van Amsterdam op gezag van de Rector Magnificus prof. -
![2.5 Win-History [Read-Only]](https://docslib.b-cdn.net/cover/5064/2-5-win-history-read-only-2655064.webp)
2.5 Win-History [Read-Only]
Unit OS2: Operating System Principles 2.5. History of the Windows NT/2000/XP/2004 OS Windows Operating System Internals - by David A. Solomon and Mark E. Russinovich with Andreas Polze Copyright Notice © 2000-2005 David A. Solomon and Mark Russinovich These materials are part of the Windows Operating System Internals Curriculum Development Kit, developed by David A. Solomon and Mark E. Russinovich with Andreas Polze Microsoft has licensed these materials from David Solomon Expert Seminars, Inc. for distribution to academic organizations solely for use in academic environments (and not for commercial use) Windows Operating System Internals - by David A. Solomon and Mark E. Russinovich with Andreas Polze 2 1 Roadmap for Section 2.5. History of NT Windows Release History and Versions New features in Windows XP/2003 Original Windows Design Goals/Culture How Development Processes evolved throughout Windows NT 3.1 Development and Windows 2000 Development Windows Operating System Internals - by David A. Solomon and Mark E. Russinovich with Andreas Polze 3 NT Timeline first 10 years 2/89 Coding Begins 7/93 NT 3.1 Ships 9/94 NT 3.5 Ships 5/95 NT 3.51 Ships 7/96 NT 4.0 Ships 12/99 NT 5.0 a.k.a. Windows 2000 ships Windows Operating System Internals - by David A. Solomon and Mark E. Russinovich with Andreas Polze 4 2 Unix Timeline first 20 years ’69 Coding Begins ’71 First Edition – PDP 11/20 ’73 Fourth Edition – Rewritten in C ’75 Fifth Edition – Leaves Bell Labs, basis for BSD 1.x ’79 Seventh Edition – One of the best ’82 System III ’84 4.2 BSD ’89 SVR4 Unification of Xenix, BSD, System V NT development begins Windows Operating System Internals - by David A. -

Larry Portner, Bob Puffer. Andy Knowles Was Important, Particularly in the Way We Worked, There Was Enormous Stress Between Marketing and Engineering
DEC -- Gordon Bell, 6/28/91 EDITED AND APPROVED Tape 1, Page 1 GB: Probably you want [to get on tape] Larry Portner, Bob Puffer. Andy Knowles was important, particularly in the way we worked, there was enormous stress between marketing and engineering. The more you can try to center it into the different activities, the better off it is. Because it's a complex story, and you want to try to keep it that way and then talk about the interactions between the various forces. There is a way of doing it a little bit chronologically, too. When Glenn Rifkin approached me about his book he had an outline. He wanted to come interview. I said, "Vo, don't do that. I'd like to think a lot more about this. Why don't you give me every question you want and I will answer the questions and think about them in that context." I did that. He had an outline and I gave him comments on it, how I would organize it. There's a lot of stuff in here, essentially a lot of stories. As we go through the questions I'll try to remember it. He came back after that several times. [BELL HANDS OVER 20+ PAGES OF NOTES HE WROTE FOR RIFKIN'S BOOK.] I talked to Henry Burckhardt the other day, and I was out talking to Dave Cutler. Henry said, "Well, it turns aut it takes eight years to get it out of your system. You're just able to be calm about it now." So it's been roughly eight years, and eight days now since I left. -

Unit 1: Introduction and Overview
Unit 1: Introduction and Overview 1.2. The Evolution of Operating Systems AP 9/01 Operating Systems Concepts • System software manages resources • OS hides complexity of underlying hardware • Layered architectures Banking Airline Web browser Application programs system reservation Command Compilers Editors interpreter System programs Operating system Machine language Microprogramming Hardware Physical devices AP 9/01 History of operating systems • Batch processing • Punching cards Multi programming AP 9/01 The Evolution of Operating System Functionality • Batch Job Processing – Linkage of library routines to programs – Management of files, I/O devices, secondary storage • Multiprogramming – Resource managment and sharing for multiple programs – quasi-simultaneous program execution – single user • Multiuser/Timesharing Systems – Management of multiple simultaneous users interconnected via terminals – Fair resource management: CPU scheduling, spooling, mutual exclusion • Real-Time Systems (process control systems) – Management of time-critical processes – High requirements with respect to reliability and availability Silberschatz AP 9/01 Tasks of an Operating System • Processor management - Scheduling – Fairness – Non-blocking behavior – Priorities • Memory management – Virtual versus physical memory, memory hierarchy – Protection of competing/conurrent programs • Storage management – File system – Access to external storage media • Device management – Hiding of hardware dependencies – Management of concurrent accesses • Batch processing -

Digital Equipment Corporation: Greg Scott
Digital Equipment Corporation: R.I.P. or Future Lean and Mean Competitor? Greg Scott MBMG708 Management of the Firm in Trouble Spring Semester, 1994 Scott Consulting internet: [email protected] Table of Contents Introduction .........................................................................................................................4 Pre-turnaround Situation ...................................................................................................5 Brief product history and milestones .......................................................................................................... 6 Seeds of destruction .................................................................................................................................... 7 Abandoned markets ................................................................................................................................ 7 Closed Architecture ................................................................................................................................ 7 Restrictive Business Practices ................................................................................................................ 8 Hiring Binge ........................................................................................................................................... 8 Competition ............................................................................................................................................ 9 VAX 9000 Failure ................................................................................................................................. -

DEC: the Mistakes That Led to Its Downfall
DEC: The mistakes that led to its downfall David T. Goodwin, Roger G. Johnson Birkbeck College, University of London [email protected] , [email protected] In 1987 Digital Equipment Corporation (DEC) was the number two computer manufacturer in the world with its founder being named the “‘most successful entrepreneur in the history of American business” by Fortune magazine. This paper looks at the later history of Digital Equipment Corporation and asks how an organisation that was so successful in 1988 could sink to become a takeover target for a PC hardware company ten years later. The management styles and company culture have been extensively described in Edgar Schein’s book “DEC is dead, long live DEC” but there is much more to the story. The technology that the company developed and the business decisions made in the development and the direction of that technology had a major bearing on the fate of the company. Many mistakes were made over the last fifteen years of the company’s existence and this paper offers a suggestion as to what those mistakes were. In this paper, extensive use is made of interviews with people involved at the time as well as material from the Ken Olsen Archives at Gordon College which contain many of the memos that Ken Olsen sent in his long career at DEC. It considers DEC as a case study set in the context of literature on business change and the impact of downsizing. It looks at DEC’s initial attempt to break into the business market for personal computers in 1983, the personalities involved and the competing products that the company developed. -
![[12] Case Study: Windows Nt](https://docslib.b-cdn.net/cover/6036/12-case-study-windows-nt-4936036.webp)
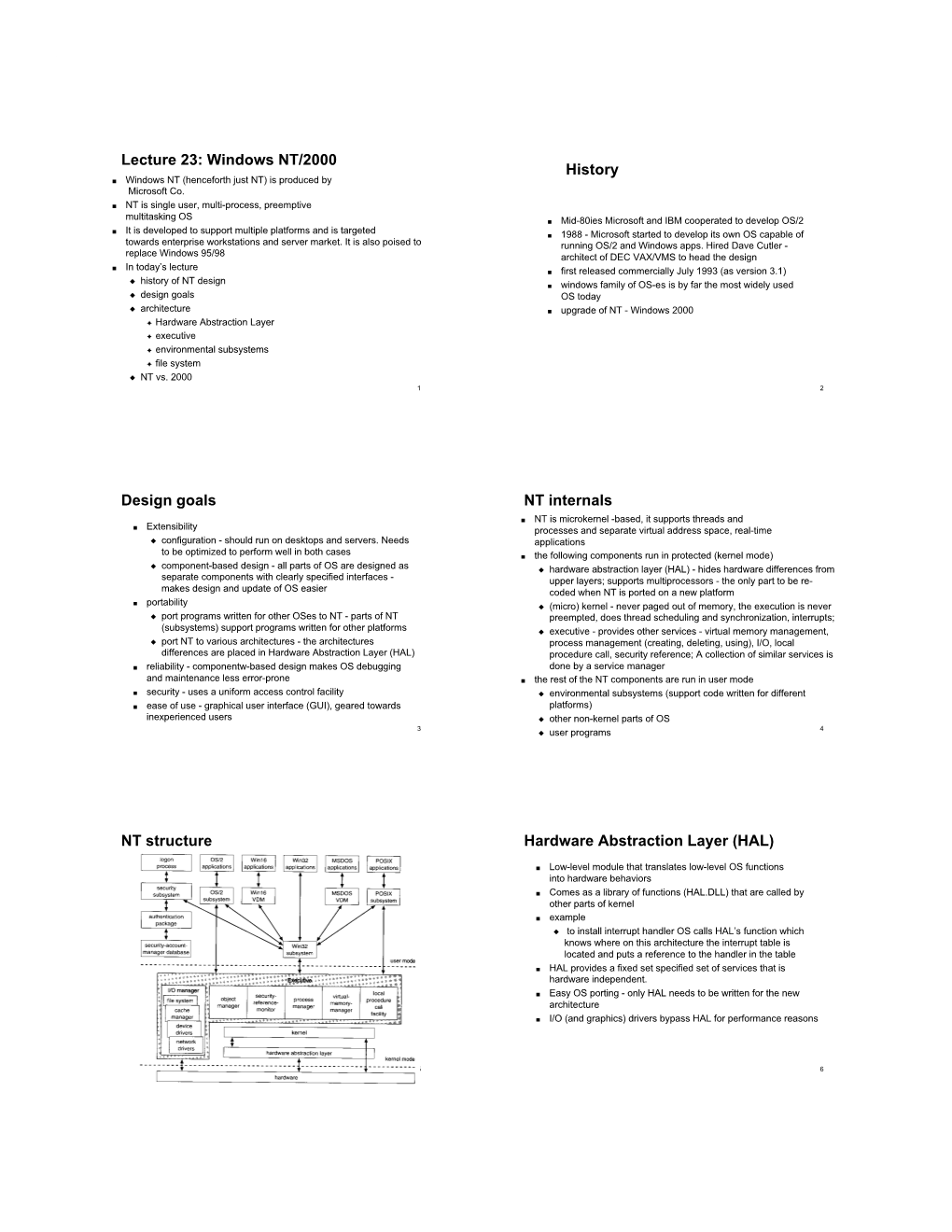
[12] Case Study: Windows Nt
[12] CASE STUDY: WINDOWS NT 1 . 1 OUTLINE Introduction Design Principles Design Structural HAL, Kernel Processes and Threads, Scheduling Environmental Subsystems Objects Manager, Namespace Other Managers: Process, VM, Security Reference, IO, Cache Filesystems FAT16, FAT32, NTFS NTFS: Recovery, Fault Tolerance, Other Features Summary 1 . 2 INTRODUCTION Introduction Design Principles Design Objects Filesystems Summary 2 . 1 PRE-HISTORY Microsoft and IBM co-developed OS/2 — in hand-written 80286 assembly! As a result, portability and maintainability weren't really strong features so in 1988 Microsoft decided to develop a "new technology" portable OS supporting both OS/2 and POSIX APIs Goal: A 32-bit preemptive multitasking operating system for modern microprocessors Originally, NT was supposed to use the OS/2 API as its native environment, but during development NT was changed to use the Win32 API, reflecting the popularity of Windows 3.0 2 . 2 NEW TECHNOLOGY After OS/2, MS decide they need "New Technology": 1988: Dave Cutler recruited from DEC 1989: team (~10 people) starts work on a new OS with a micro-kernel architecture Team grew to about 40 by the end, with overall effort of 100 person-years July 1993: first version (3.1) introduced. Sucked September 1994: NT 3.5 released, providing mainly size and performance optimisations May 1995: NT 3.51 with support for the Power PC, and more performance tweaks July 1996: NT 4.0 with "new" (Windows 95) look 'n' feel. Saw some desktop use but mostly limited to servers. Various functions pushed back into the kernel, notably graphics rendering 2 . 3 CONTINUED EVOLUTION Feb 2000: NT 5.0 aka Windows 2000.