UNIX: Introduction Unix Family Tree (Simplified) Design Features
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Windows XP History and Versions
Lecture 23: Windows XP History and Versions n Mid-80ies Microsoft and IBM cooperated to develop OS/2 n Windows XP is produced by Microsoft Co. n 1988 - Microsoft started to develop its own new technology (NT) OS n XP is multi-user, multi-process, preemptive multitasking OS, 30M lines of source code capable of running OS/2, Windows and Unix apps. Hired Dave Cutler - architect of DEC VAX/VMS to head the design n It is developed to support multiple platforms and targeted towards enterprise workstations and server market as well as n NT v. 3.1 first released commercially July 1993 desktops n NT v 4.0 adopted Windows 95 user interface, graphics code moved into kernel to improve performance n In today’s lecture n 2000 – improved networking and laptop support, support for plug-and- u XP’s predecessors, the history of XP design, XP versions play devices, support for more processors (up to 8) and memory, u design principles becomes true multi-user through terminal server u components n XP (released Oct 2001) – update for 2000 replacement for 95/98 F hardware abstraction layer u simplifies user interface, improved reliability, performance F executive improvements, partial 64-bit support F environmental subsystems n versions F file system u desktop: XP personal – 95/98 replacement, professional – advanced features like POSIX support, some network features 1 u server: .NET – support for web/print service, clusters, large memory2 and multiple processors Design goals Components n XP is microkernel-based, modular n security – NT was C-2 certified (US -

Marjn Norling November 2012
Mar$n Norling November 2012 UNIX Lecture Goals • Goal 1: Know basic UNIX commands and their use from memory. • Goal 2: Know how to find informaon on more advanced UNIX commands and their use. • Goal 3: Understand the basics of regular expression paerns. • Goal 4: Know the basic loops and condi$onals for shell scrip$ng and understand how to use them. UNIX Schedule Thursday Friday 09.00-09.45 UNIX introduc$on 09.00-09.45 Bash Scrip$ng 10.00-10.45 UNIX basics 10.00-10.45 Tutorial: Bash scrip$ng 11.00-12.00 Redirects to regexp 11.00-12.00 Tips & Quesons 12.00-13.00 Lunch 12.00-13.00 Lunch 13.00-16.00 Tutorial: Basics 13.00-16.00 Tutorial: finishing up UNIX HISTORY UNIX History • 1969 – First Version of UNIX developed at Bell Labs by AT&T • 1975 – UNIX 6, the first to be widely available outside Bell Labs. The first “Berkeley So]ware Distribu$on” (BSD) is released. • 1989 – UNIX System V, the last tradi$onal UNIX version. • 1991 – Linus Torvalds begin developing Linux. “UNIX-like” • Today – UNIX itself, what’s now called “tradi$onal UNIX” is not used, except by enthusiasts. • There are many “UNIX-like” systems (also known as *nix or UN*X) that are similar to UNIX while not conforming to the Single UNIX Specificaon. • In fact, most operang systems today except windows are “UNIX like”. Single UNIX Specificaon (SUS) • Developed and maintained by the Aus$n Group, based on earlier work by the IEee and The Open Group. -

AXIS NPS 630/632 User's Manual
Preface Preface Thank you for purchasing the Axis NPS 630/632 Network Print Server. Our goal in developing this product is to enable you to connect your printers anywhere in your network, allowing all network users access to shared printer resources. About Axis Axis Communications, founded in 1984, is one of the world’s fastest growing companies in the printer interface and network print server market. The head quarters are located in Lund, Sweden, with subsidiaries in Boston, Tokyo, and Hong Kong. Axis Communications has a distributor network operating in more than 60 countries world-wide, marketing three product lines: Network CD- CD-ROM servers provide a flexible and cost-efficient solution for sharing ROM Servers CD-ROMs across the network. They are available in Ethernet and Token Ring versions, with or without built in drive option. Network Print These intelligent Ethernet and Token Ring print servers support a wide Servers range of LAN protocols. The Axis NPS 530, 532, 550, AXIS 150 and 152 are Ethernet print servers, and the Axis NPS 630, 632 and 650 are Token Ring print servers. IBM Mainframe These products include a wide range of plug-in interfaces and free and S/3x – AS/ standing products such as the Cobra+ and the AFP IPDS-to-PostScript 400 Printer converter. Interfaces Axis NPS 630/632 User’s Manual Version 2.0 Part No.:13768 October 1995 Copyright © Axis Communications AB Axis NPS 630/632 User’s Manual 1 Preface About this manual This manual will guide you through a simple step-by-step installation and configuration procedure. -

Unifying the User and Kernel Environments
Unifying the User and Kernel Environments Richard P. Draves Scott M. Cutshall March 12, 1997 Technical Report MSR-TR-97-10 Microsoft Research Microsoft Corporation One Microsoft Way Redmond, WA 98052 Unifying the User and Kernel Environments Richard P. Draves and Scott M. Cutshall Microsoft Research One Microsoft Way Redmond, WA 98052 http://www.research.microsoft.com Abstract Vendors of commercial operating systems today invest resources in two very different environments—one for user- level (application or server) programming and one for kernel-level (device driver or subsystem) programming. The kernel environment is typically more restrictive, with completely different interfaces and programming conventions. Based on our experience developing and deploying an operating system for an interactive TV system, we believe that it is desirable to unify the user and kernel environments. We structured our operating system to provide common programming and run-time environments for user-level code and kernel-level code. For example, modules loaded into the kernel did not have any restrictions on their use of shared libraries or stack space. We found that unifying the user and kernel environments with common interfaces and run-time requirements, common documentation, and a common debugger produced significant software-engineering benefits. In addition, we could transparently collocate trusted server code in the kernel to reduce memory usage and improve performance. 1. Introduction We advocate structuring operating systems to unify the user and kernel environments. The operating system should present a single environment, with common interfaces or APIs, common run-time characteristics for scheduling, paging, stack usage, and shared libraries, common debugger and development tools, etc. -

Roadmap for Section 1.2
Unit OS1: Overview of Operating Systems 1.2. The Evolution of Operating Systems Windows Operating System Internals - by David A. Solomon and Mark E. Russinovich with Andreas Polze Roadmap for Section 1.2. History of Operating Systems Tasks of an Operating System OS as extension of the hardware Main concepts: processes, files, system calls Operating system structuring 3 1 Operating Systems Concepts System software manages resources OS hides complexity of underlying hardware Layered architectures Banking Airline Web browser Application programs system reservation Command Compilers Editors interpreter System programs Operating system Machine language Microprogramming Hardware Physical devices 4 History of operating systems Batch processing The elements of the basic IBM 1401 system are the 1401 Processing Unit, 1402 Card Read-Punch, and 1403 Printer. Punching cards Multiprocessing programming Job 3 Job 2 Memory Job 1 partitions OS 5 2 The Evolution of Operating System Functionality Batch Job Processing Linkage of library routines to programs Management of files, I/O devices, secondary storage Multiprogramming Resource managment and sharing for multiple programs Quasi-simultaneous program execution Single user Multiuser/Timesharing Systems Management of multiple simultaneous users interconnected via terminals Fair resource management: CPU scheduling, spooling, mutual exclusion Real-Time Systems (process control systems) Management of time-critical processes High requirements with respect to reliability and availability 6 Tasks of an Operating -

VAX VMS at 20
1977–1997... and beyond Nothing Stops It! Of all the winning attributes of the OpenVMS operating system, perhaps its key success factor is its evolutionary spirit. Some would say OpenVMS was revolutionary. But I would prefer to call it evolutionary because its transition has been peaceful and constructive. Over a 20-year period, OpenVMS has experienced evolution in five arenas. First, it evolved from a system running on some 20 printed circuit boards to a single chip. Second, it evolved from being proprietary to open. Third, it evolved from running on CISC-based VAX to RISC-based Alpha systems. Fourth, VMS evolved from being primarily a technical oper- ating system, to a commercial operat- ing system, to a high availability mission-critical commercial operating system. And fifth, VMS evolved from time-sharing to a workstation environment, to a client/server computing style environment. The hardware has experienced a similar evolution. Just as the 16-bit PDP systems laid the groundwork for the VAX platform, VAX laid the groundwork for Alpha—the industry’s leading 64-bit systems. While the platforms have grown and changed, the success continues. Today, OpenVMS is the most flexible and adaptable operating system on the planet. What start- ed out as the concept of ‘Starlet’ in 1975 is moving into ‘Galaxy’ for the 21st century. And like the universe, there is no end in sight. —Jesse Lipcon Vice President of UNIX and OpenVMS Systems Business Unit TABLE OF CONTENTS CHAPTER I Changing the Face of Computing 4 CHAPTER II Setting the Stage 6 CHAPTER -

MICROSOFT WINDOWS Early Versions Main Articles: Windows 1.0
MICROSOFT WINDOWS Early versions Main articles: Windows 1.0, Windows 2.0, and Windows 2.1x Windows 1.0, the first version, released in 1985 The history of Windows dates back to September 1981, when Chase Bishop, a computer scientist, designed the first model of an electronic device and project "Interface Manager" was started. It was announced in November 1983 (after the Apple Lisa, but before the Macintosh) under the name "Windows", but Windows 1.0 was not released until November 1985.[5] Windows 1.0 achieved little popularity and was to compete with Apple's own operating system. Windows 1.0 is not a complete operating system; rather, it extends MS-DOS. The shell of Windows 1.0 is a program known as the MS- DOS Executive. Components included Calculator, Calendar, Cardfile, Clipboard viewer, Clock, Control Panel, Notepad, Paint, Reversi, Terminal and Write. Windows 1.0 does not allow overlapping windows. Instead all windows are tiled. Only modal dialog boxes may appear over other windows. Windows 2.0 was released in December 1987 and was more popular than its predecessor. It features several improvements to the user interface and memory management.[citation needed] Windows 2.03 changed the OS from tiled windows to overlapping windows. The result of this change led to Apple Computer filing a suit against Microsoft alleging infringement on Apple's copyrights.[6][7] Windows 2.0 also introduced more sophisticated keyboard shortcuts and could make use of expanded memory. Windows 2.1 was released in two different versions: Windows/286 and Windows/386. Windows/386 uses the virtual 8086 mode of Intel 80386 to multitask several DOS programs and the paged memory model to emulate expanded memory using available extended memory. -

Thesis May Never Have Been Completed
UvA-DARE (Digital Academic Repository) Digital Equipment Corporation (DEC): A case study of indecision, innovation and company failure Goodwin, D.T. Publication date 2016 Document Version Final published version Link to publication Citation for published version (APA): Goodwin, D. T. (2016). Digital Equipment Corporation (DEC): A case study of indecision, innovation and company failure. General rights It is not permitted to download or to forward/distribute the text or part of it without the consent of the author(s) and/or copyright holder(s), other than for strictly personal, individual use, unless the work is under an open content license (like Creative Commons). Disclaimer/Complaints regulations If you believe that digital publication of certain material infringes any of your rights or (privacy) interests, please let the Library know, stating your reasons. In case of a legitimate complaint, the Library will make the material inaccessible and/or remove it from the website. Please Ask the Library: https://uba.uva.nl/en/contact, or a letter to: Library of the University of Amsterdam, Secretariat, Singel 425, 1012 WP Amsterdam, The Netherlands. You will be contacted as soon as possible. UvA-DARE is a service provided by the library of the University of Amsterdam (https://dare.uva.nl) Download date:26 Sep 2021 Digital Equipment Corporation (DEC) (DEC) Corporation Digital Equipment David Thomas David Goodwin Digital Equipment Corporation (DEC): A Case Study of Indecision, Innovation and Company Failure David Thomas Goodwin Digital Equipment Corporation (DEC): A Case Study of Indecision, Innovation and Company Failure David Thomas Goodwin 1 Digital Equipment Corporation (DEC): A Case Study of Indecision, Innovation and Company Failure ACADEMISCH PROEFSCHRIFT ter verkrijging van de graad van doctor aan de Universiteit van Amsterdam op gezag van de Rector Magnificus prof. -
![2.5 Win-History [Read-Only]](https://docslib.b-cdn.net/cover/5064/2-5-win-history-read-only-2655064.webp)
2.5 Win-History [Read-Only]
Unit OS2: Operating System Principles 2.5. History of the Windows NT/2000/XP/2004 OS Windows Operating System Internals - by David A. Solomon and Mark E. Russinovich with Andreas Polze Copyright Notice © 2000-2005 David A. Solomon and Mark Russinovich These materials are part of the Windows Operating System Internals Curriculum Development Kit, developed by David A. Solomon and Mark E. Russinovich with Andreas Polze Microsoft has licensed these materials from David Solomon Expert Seminars, Inc. for distribution to academic organizations solely for use in academic environments (and not for commercial use) Windows Operating System Internals - by David A. Solomon and Mark E. Russinovich with Andreas Polze 2 1 Roadmap for Section 2.5. History of NT Windows Release History and Versions New features in Windows XP/2003 Original Windows Design Goals/Culture How Development Processes evolved throughout Windows NT 3.1 Development and Windows 2000 Development Windows Operating System Internals - by David A. Solomon and Mark E. Russinovich with Andreas Polze 3 NT Timeline first 10 years 2/89 Coding Begins 7/93 NT 3.1 Ships 9/94 NT 3.5 Ships 5/95 NT 3.51 Ships 7/96 NT 4.0 Ships 12/99 NT 5.0 a.k.a. Windows 2000 ships Windows Operating System Internals - by David A. Solomon and Mark E. Russinovich with Andreas Polze 4 2 Unix Timeline first 20 years ’69 Coding Begins ’71 First Edition – PDP 11/20 ’73 Fourth Edition – Rewritten in C ’75 Fifth Edition – Leaves Bell Labs, basis for BSD 1.x ’79 Seventh Edition – One of the best ’82 System III ’84 4.2 BSD ’89 SVR4 Unification of Xenix, BSD, System V NT development begins Windows Operating System Internals - by David A. -
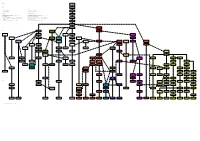
Unix History 2.6 Unix Geschichte 2.6 1972
1960 AT&T UNICS 1969 1970 UNIX 1 1971 UNIX 2 Unix history 2.6 Unix Geschichte 2.6 1972 Small UNIX history Kleine UNIX-Geschichte UNIX 3 1973 Represented are only the origin lines. Dargestellt sind nur die Ursprungslinien. The different influences are shown only with Apple, since they impair Die verschiedenen Einflüsse sind nur bei Apple abgebildet, da sie die the clarity strongly. Übersichtlichkeit stark beeinträchtigen. UNIX 4 Further data are: Manufacturer, operating system name as well as the Weitere Daten sind: Hersteller, Betriebssystem-Name sowie das 1973 feature year of the software. The individual versions are listed only with Erscheinungsjahr der Software. Die einzelnen Versionen sind nur bei UNIX and Linux. UNIX und Linux aufgelistet. More detailed list under: http://www.levenez.com/unix/ Detailliertere Liste unter: http://www.levenez.com/unix/ UNIX 5 1974 UNIX 6 1976 UNIX 7 Berkeley Software 1979 Distribution: BSD 1978 1980 UNIX System III Microsoft BSD 4.1 1981 XENIX 1981 1980 UNIX V UNIX 8 SUN SPIX QUNIX 1983 1985 Sun OS 1.0 1982 1981 1982 UNIX V.2 Microsoft/SCO Siemens UNIX 9 Sun OS 2.0 Dynix Venix 1984 XENIX 3.0 Sinix 1.0 1986 1985 1984 1985 1984 1984 HP IBM UNIX 10 MIPS BSD 4.2 GNU Sun OS 3.0 Andrew S. Mach HP-UX AIX/RT 2 End: 1989 MIPS OS 1985 Trix 1986 Tanenbaum: Minix 1985 1986 1986 1985 1986 1987 UNIX V.3 SGI Mach 2.0 Minix 1.0 NonStop-UX 1986 IRIX 1996 1987 1987 1988 UNIX V.4 AIX/6000 v3 BOS MIPS OS NeXT A/UX 1988 1989 1989 End: 1989 NeXTSTEP 1988 1988 1990 UNIX V.x Trusted AIX 3.1 IRIX 4.0 Mach 3.0 Linus Torvalds -

Operating System Selection
EARTH STATION CONTROL COMPUTER - OPERATING SYSTEM SELECTION D. Varney and L. D'Ad.dario June 11, 1991 Abstract This report describes a survey of real-time operating systems that may form a suitable platform for construction of the control software for the Green Bank OVLBI Earth Station. After considering the performance requirements, desire for standardization, hardware and software costs, and several other factors, we have selected Venix, by VenturCom, Inc. This includes a fully-preemptable real-time kernel that is compliant with UNIX interface standards, including SVID, Posix 1003.1 and 1003.4, and ABI/386. It runs on 80386 processors in the IBM-AT architecture. 1 Introduction The software requirements for the OVLBI Earth Station control computer were outlined in OVLBI- ES Memo No. 8. In the present memo, we discuss the implications for the choice of operating system (OS), evaluate several candidate OS's, and report the final selection. This will have a strong effect on the choice of hardware platform, which will be discussed in a subsequent memo. The main requirements on the OS are (1) that it provide good real-time performance for time- critical tasks, including predictable interrupt response and task switching times regardless of system loading; and (2) that it provide good support for networking, both local-- and wide-area, including the protocols commonly used at the NRAO for remote access and file transfer, namely TCP/IP. To this we add a desire for good debugging facilities to ease development, especially for real-time tasks. UNIX has become the most standard and portable operating system available. -

Advanced Programming in the UNIX Environment
CS631-AdvancedProgrammingintheUNIXEnvironment Slide1 CS631 - Advanced Programming in the UNIX Environment Department of Computer Science Stevens Institute of Technology Jan Schaumann [email protected] https://www.cs.stevens.edu/~jschauma/631/ Lecture 01: Introduction, UNIX history, UNIX Programming Basics August 27, 2018 CS631-AdvancedProgrammingintheUNIXEnvironment Slide2 New Rules Close your laptops! Lecture 01: Introduction, UNIX history, UNIX Programming Basics August 27, 2018 CS631-AdvancedProgrammingintheUNIXEnvironment Slide3 New Rules Close your laptops! Open your eyes! (Mind, too.) Lecture 01: Introduction, UNIX history, UNIX Programming Basics August 27, 2018 CS631-AdvancedProgrammingintheUNIXEnvironment Slide4 So far, so good... What questions do you have? Lecture 01: Introduction, UNIX history, UNIX Programming Basics August 27, 2018 CS631-AdvancedProgrammingintheUNIXEnvironment Slide5 About this class The class is called “Advanced Programming in the UNIX Environment”. It is not called: “An Introduction to Unix” “An Introduction to Programming” “An introduction to C” Lecture 01: Introduction, UNIX history, UNIX Programming Basics August 27, 2018 CS631-AdvancedProgrammingintheUNIXEnvironment Slide6 What is it? https://www.bell-labs.com/usr/dmr/www/chist.html Lecture 01: Introduction, UNIX history, UNIX Programming Basics August 27, 2018 CS631-AdvancedProgrammingintheUNIXEnvironment Slide7 In a nutshell: the ”what” $ ls /bin [ csh ed ls pwd sleep cat date expr mkdir rcmd stty chio dd hostname mt rcp sync chmod df kill mv