Chapter 11 Case Study 2: Windows Vista
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

When Using the Wireless Function with a Windows Vista Computer 3. Computer Network Settings 1. Projector Settings 2. Computer IP
2. Computer IP address settings When using the wireless function with a Windows Vista computer 1 Select [Start] → [Network]. “Wireless Manager mobile edition 3.0”, which is stored on the CD-ROM that is provided, does not work when using the wireless function with a Windows Vista computer. “Wireless Manager mobile edition 3.0a” is a version that is compatible with Windows Vista. Use this version by downloading and installing it from the URL below. However, please be aware it will still not be possible to use the functions described below. URL: http://panasonic.co.jp/pavc/global/projector/download/ 2 Select [Network and Sharing Center]. Functions that cannot be used: • Easy wireless set up (automatic set up of the wireless network) • Sound transmission • Wireless prompter (secondary display transmission) • Selective area transmission • Check with your system administrator before performing the network settings with the procedures below. Select [Manage network connections]. If network settings have already been made for using the computer in a wireless 3 environment for a different purpose, and after changing the settings as described in these instructions you want to go back to using the computer for the original purpose, then remember to return the network settings to their previous condition. • See “Wireless Function Edition”, the Operating Instructions in the provided CD-ROM, for details on the projector network settings and the wireless function. 1. Projector settings 4 Right click the mouse and open the Select [MENU] → [WIRELESS] → [NETWORK], and change to [USER1]. Wireless Network Connection Properties. Default settings of USER1 DHCP OFF IP ADDRESS 192.168.10.100 SUBNETMASK 255.255.255.0 SSID Panasonic Projector MODE ADHOC Enter [TCP/IPv4] as the setting and press 5 [OK]. -

Windows XP History and Versions
Lecture 23: Windows XP History and Versions n Mid-80ies Microsoft and IBM cooperated to develop OS/2 n Windows XP is produced by Microsoft Co. n 1988 - Microsoft started to develop its own new technology (NT) OS n XP is multi-user, multi-process, preemptive multitasking OS, 30M lines of source code capable of running OS/2, Windows and Unix apps. Hired Dave Cutler - architect of DEC VAX/VMS to head the design n It is developed to support multiple platforms and targeted towards enterprise workstations and server market as well as n NT v. 3.1 first released commercially July 1993 desktops n NT v 4.0 adopted Windows 95 user interface, graphics code moved into kernel to improve performance n In today’s lecture n 2000 – improved networking and laptop support, support for plug-and- u XP’s predecessors, the history of XP design, XP versions play devices, support for more processors (up to 8) and memory, u design principles becomes true multi-user through terminal server u components n XP (released Oct 2001) – update for 2000 replacement for 95/98 F hardware abstraction layer u simplifies user interface, improved reliability, performance F executive improvements, partial 64-bit support F environmental subsystems n versions F file system u desktop: XP personal – 95/98 replacement, professional – advanced features like POSIX support, some network features 1 u server: .NET – support for web/print service, clusters, large memory2 and multiple processors Design goals Components n XP is microkernel-based, modular n security – NT was C-2 certified (US -

No More Excuses: Windows 7 Makes It Easy to Manage Computer Power
• Products that earn the ENERGY STAR® prevent greenhouse gas emissions by meeting strict energy efficiency guidelines set by the U.S. Environmental Protection Agency and the U.S. Department of Energy. www.energy star.gov NO MORE EXCUSES: WINDOWS 7 MAKES IT EASY TO MANAGE COMPUTER POWER CONSUMPTION ORGANIZATION-WIDE Here’s how you can take advantage of Windows 7’s new power management features The University of Wisconsin at Oshkosh is no stranger to the idea of sustainability. In 2003 it became the first university in the state to join the Environmental Protection Agency’s Green Power Partnership. Its green initiatives also earned the university high marks from the Sierra Club, which ranked the university nationally in its Cool Schools survey. Given this commitment to green, it’s no surprise that the university first deployed computer power management back in 2005, and that it was one of the first Energy Star power management success stories. At that time, the University’s computers ran the Windows XP and Windows 2000 operating systems, neither of which included native tools for the central administration of power management features. To implement power management settings on these machines, the University used third-party software from ENERGY STAR called EZ GPO. For detailed information and resources concerning Now that Windows 7 has CPM client management features built in, it’s much the power management of easier to administer power management. This case study will show you how the University of Wisconsin at Oshkosh took full advantage of computer power PCs running Windows XP, management features on Windows Vista and Windows 7 clients managed by please see the ENERGY STAR Windows Server 2008. -

Unifying the User and Kernel Environments
Unifying the User and Kernel Environments Richard P. Draves Scott M. Cutshall March 12, 1997 Technical Report MSR-TR-97-10 Microsoft Research Microsoft Corporation One Microsoft Way Redmond, WA 98052 Unifying the User and Kernel Environments Richard P. Draves and Scott M. Cutshall Microsoft Research One Microsoft Way Redmond, WA 98052 http://www.research.microsoft.com Abstract Vendors of commercial operating systems today invest resources in two very different environments—one for user- level (application or server) programming and one for kernel-level (device driver or subsystem) programming. The kernel environment is typically more restrictive, with completely different interfaces and programming conventions. Based on our experience developing and deploying an operating system for an interactive TV system, we believe that it is desirable to unify the user and kernel environments. We structured our operating system to provide common programming and run-time environments for user-level code and kernel-level code. For example, modules loaded into the kernel did not have any restrictions on their use of shared libraries or stack space. We found that unifying the user and kernel environments with common interfaces and run-time requirements, common documentation, and a common debugger produced significant software-engineering benefits. In addition, we could transparently collocate trusted server code in the kernel to reduce memory usage and improve performance. 1. Introduction We advocate structuring operating systems to unify the user and kernel environments. The operating system should present a single environment, with common interfaces or APIs, common run-time characteristics for scheduling, paging, stack usage, and shared libraries, common debugger and development tools, etc. -
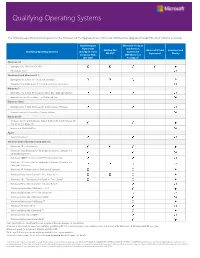
Qualifying Operating Systems
Qualifying Operating Systems The following operating systems qualify for the Windows 10 Pro Upgrade and/or Windows 10 Enterprise Upgrade through Microsoft Volume Licensing. New Enterprise Microsoft Products Agreement and Services Existing EA/ Microsoft Cloud Academic and Qualifying Operating Systems (EA)/Open Value Agreement OV-CW2 Agreement Charity Company-Wide (MPSA)/Select (OV-CW)1 Plus/Open3 Windows 10 4 Enterprise (N, KN) , Pro (N, KN) Education, Home Windows 8 and Windows 8.1 Enterprise (N, K, KN), Pro (N, K, KN, diskless) Windows 8 and Windows 8.1 (including Single Language) Windows 7 Enterprise (N, K, KN), Professional (N, K, KN, diskless), Ultimate Home Premium, Home Basic, or Starter Edition Windows Vista Enterprise (N, K, KN), Business (N, K, KN, Blade), Ultimate Home Premium, Home Basic, Starter Edition Windows XP Professional (N, K, KN, Blade), Tablet Edition (N, K, KN, Blade), XP Pro N, XP Pro Blade PC Home and Starter Edition Apple Apple Macintosh Windows Embedded Operating Systems Windows 10 IoT Enterprise Windows Vista Business for Embedded Systems, Ultimate for Embedded Systems Windows 2000 Professional for Embedded Systems Windows 7 Professional for Embedded Systems, Ultimate for Embedded Systems Windows XP Professional for Embedded Systems Windows Embedded 8 and 8.1 Pro, Industry Pro Windows 10 IoT Enterprise for Retail or Thin Clients5 5 Windows Embedded 8 and 8.1 Industry Retail Windows Embedded POSReady 7 Pro5 5 Windows Embedded for Point of Service Windows Embedded POSReady 20095 5 Windows Embedded POSReady 7 5 Windows XP Embedded Windows Embedded Standard 75 5 Windows Embedded 2009 5 Windows Embedded 8 Standard 1Also applicable to Qualified Devices acquired through merger or acquisition. -

Windows 10 Download for Windows Vista Windows 10 Download for Windows Vista
windows 10 download for windows vista Windows 10 download for windows vista. Dummies has always stood for taking on complex concepts and making them easy to understand. Dummies helps everyone be more knowledgeable and confident in applying what they know. Whether it’s to pass that big test, qualify for that big promotion or even master that cooking technique; people who rely on dummies, rely on it to learn the critical skills and relevant information necessary for success. Learning Made Easy. Copyright © 2021 & Trademark by John Wiley & Sons, Inc. All rights reserved. Upgrade from Windows Vista to Windows 10 or 8.1? If you pay for 7 and then try for a free upgrade to 10 you may not get it as that offer expired in 2016. And 10 is cheaper than 7 to buy. But check everything first:: It depends on the hardware requirements of later operating systems and also whether the computer/laptop manufacturer supports and supplies drivers for the later operating systems as to whether it is possible or feasible to upgrade or not. There is no free upgrade from Vista to 7, 8.1 or 10. Follow these steps before you buy Windows 7; extended support Windows 7 SP1 until January 14, 2020 . Microsoft no longer sells 7; try amazon.com. Go to your Computer / Laptop Manufacturer's website and see if Windows 7 Drivers are available for your Make and Model Computer / Laptop. If not available, Windows 7 will not work correctly for you. Run the "Windows 7 Upgrade Advisor" Check to see if your System Specifications are compatible for Windows 7: "Windows 7 system requirements" Windows 7 Upgrade paths: Follow these steps before you buy and Upgrade (clean install) to Windows 8.1; extended support ends January 10, 2023 . -

Transcript of Rick Rashid's Keynote Address
TechFest 2013 Keynote Rick Rashid March 5, 2013 ANNOUNCER: Ladies and gentlemen, please welcome Microsoft Chief Research Officer, Rick Rashid. (Applause.) RICK RASHID: Hi there. Well, hopefully this will be a very fun day for all of you. For me, it's interesting. It feels like we've been doing TechFest for a really, long time, but it's actually only been since 2001. So, technically, I think, this is the 13th TechFest event for Microsoft Research. Of course, in the first TechFest, it wasn't nearly as big an event as this. It was just for employees. We didn't take up nearly as much space. And we didn't even know how many people would really show up. I was actually one of the strongest skeptics about this whole idea of creating this technology show for our employees, because I wasn't really sure how many people would show up. I kept saying, “Well, gosh, it seems like it's going to be a lot of work, and I'm not sure it's going to be really valuable and worthwhile, but if you guys really think you want to do it, okay.” Of course, what happened that year was we had, I think, about 4,000 of our Puget Sound employees come over a two-day period. And of course Microsoft was a much smaller company back then, so that was just a huge fraction of our Puget Sound workforce at that time. And everybody was really excited. I mean, the researchers came away from the event really excited about being able to talk to so many of our employees, be able to interact with them, and to sort of sell their ideas, and show off what they've been doing. -

Microsoft Plays Hardball: Use of Exclusionary Pricing and Technical
Antitrust Bulletin, XL:2, Summer 1995, 265-315 MICROSOFT PLAYS HARDBALL: The Use of Exclusionary Pricing and Technical Incompatibility to Maintain Monopoly Power in Markets for Operating System Software† by KENNETH C. BASEMAN* FREDERICK R. WARREN-BOULTON* and GLENN A. WOROCH** May 1995 ___________________ * Principals, MiCRA: Microeconomic Consulting and Research Associates, Inc., Washington, DC. ** University of California, Berkeley. † Forthcoming, Antitrust Bulletin, June 1995. We would like to express our appreciation for helpful comments and other assistance to Sturge Sobin, Linnet Harlan, Paul Dennis and the participants at the Columbia Business School's Institute for Tele-Information's Seminar on Sustaining Competition in Network Industries through Regulating and Pricing Access, especially Janusz Ordover and Bobby Willig. TABLE OF CONTENTS I. INTRODUCTION AND SUMMARY ................................... 1 II. BACKGROUND .................................................... 3 A. THE MARKET FOR PERSONAL COMPUTER OPERATING SYSTEMS ............................................................ 3 TABLE: NEW SHIPMENTS OF PERSONAL COMPUTER OPERATING SYSTEMS .............................................. 8 B. MICROSOFT'S PRACTICES ..................................... 9 III. FIRST-DEGREE PRICE DISCRIMINATION vs. INEFFICIENT SUBSTITUTION ................................................... 15 A. FIRST-DEGREE PRICE DISCRIMINATION ........................ 16 B. INEFFICIENT SUBSTITUTION ................................. 20 IV. ANTIFRAUD AND ANTIPIRACY -

Why I Hate Microsoft by F.W
Why I hate Microsoft by F.W. van Wensveen Why I hate Microsoft "A personal, lengthy, but highly articulate outburst" by F.W. van Wensveen Table of contents Introduction A brief introduction, or why this paper needed to be written Abstract The management summary 1. From the people who brought you EDLIN Microsoft and innovation 2. The not-so-good, the bad and the ugly The general quality of Microsoft products 3. The power to bind Formats and standards 4. World domination From business to megalomania 5. Bad practice, foul play Exploring the limits of lawful conduct 6. Caveat Emptor Think before you buy 7. Where are you forced to go today? Price gouging and other monopolist practices 8. The road ahead On diminishing returns and continuing trends Appendix A A brief overview of Windows' most serious design flaws Appendix B Links Introduction "One OS to bring them all and in the darkness bind them..." From the title of this paper you may have guessed that I am not very impressed with the guys in Redmond. One might even say that my dislike for Microsoft is a pet hate gone out of control in an almost quixotic fashion. Why is this? Of course I have been accused of personal antipathy, of being jealous of Bill Gates and his billions, and of being prejudiced against all things Microsoft without any reason whatsoever. None of this is true. I have nothing personal against Bill Gates. Why should I? I don't know the man, I've never met him. I agree with those who say he might be the most successful salesman in history. -

3.3. Cloud Computing
國 立 交 通 大 學 企業管理碩士學位學程 碩 士 論 文 網路泡沫化危機的十年之後: 谷歌個案研究 10 years after the dot-com bubble: A Case Study of Google 研 究 生:張倍菁 指導教授:劉芬美 中華民國一百零一年一月 10 years after the dot-com bubble: A Case Study of Google 研 究 生:張倍菁 Student: Penny Pei-ching Chang 指導教授:劉芬美 Advisor: Dr. Fen-May Liou 國 立 交 通 大 學 管理學院 企業管理碩士學位學程 碩 士 論 文 A Thesis Submitted to Master Degree Program of Global Business Administration College of Management National Chiao Tung University In partial Fulfillment of the Requirements For the Degree of Master in Business Administration January 2012 Hsinchu, Taiwan, Republic of China 中華民國一百零一年一月 National Chiao Tung University College of Management Global Master of Business Administration Program Thesis 網路泡沫化危機的十年之後: 谷歌個案研究 10 years after the dot-com bubble: A Case Study of Google Student: Penny Pei-ching Chang Advisor: Dr. Fen-May Liou Abstract Google is a legendary company famous with its rapid growth no matter being through dot-com bubble or even in the latest global financial crisis in 2008. Google started from web search engine then online keyword advertising. Recently it even moves its step into mobile and cloud computing areas. In this research, there are not only a wide vision of Google’s key success factors being discussed but a comprehensive corporate comparison among Google main competitors Yahoo! and Microsoft. This research first gives a fundamental analysis among these three companies by comparing their products development and key milestone. Then look into the business model they have been deployed. Although it seems to have the similarity among these three internet giants, this research points out the distinction between Google and other competitors. -

Roadmap for Section 1.2
Unit OS1: Overview of Operating Systems 1.2. The Evolution of Operating Systems Windows Operating System Internals - by David A. Solomon and Mark E. Russinovich with Andreas Polze Roadmap for Section 1.2. History of Operating Systems Tasks of an Operating System OS as extension of the hardware Main concepts: processes, files, system calls Operating system structuring 3 1 Operating Systems Concepts System software manages resources OS hides complexity of underlying hardware Layered architectures Banking Airline Web browser Application programs system reservation Command Compilers Editors interpreter System programs Operating system Machine language Microprogramming Hardware Physical devices 4 History of operating systems Batch processing The elements of the basic IBM 1401 system are the 1401 Processing Unit, 1402 Card Read-Punch, and 1403 Printer. Punching cards Multiprocessing programming Job 3 Job 2 Memory Job 1 partitions OS 5 2 The Evolution of Operating System Functionality Batch Job Processing Linkage of library routines to programs Management of files, I/O devices, secondary storage Multiprogramming Resource managment and sharing for multiple programs Quasi-simultaneous program execution Single user Multiuser/Timesharing Systems Management of multiple simultaneous users interconnected via terminals Fair resource management: CPU scheduling, spooling, mutual exclusion Real-Time Systems (process control systems) Management of time-critical processes High requirements with respect to reliability and availability 6 Tasks of an Operating -

Using History to Teach Computer Science and Related Disciplines
Computing Research Association Using History T o T eachComputer Science and Related Disciplines Using History To Teach Computer Science and Related Disciplines Edited by Atsushi Akera 1100 17th Street, NW, Suite 507 Rensselaer Polytechnic Institute Washington, DC 20036-4632 E-mail: [email protected] William Aspray Tel: 202-234-2111 Indiana University—Bloomington Fax: 202-667-1066 URL: http://www.cra.org The workshops and this report were made possible by the generous support of the Computer and Information Science and Engineering Directorate of the National Science Foundation (Award DUE- 0111938, Principal Investigator William Aspray). Requests for copies can be made by e-mailing [email protected]. Copyright 2004 by the Computing Research Association. Permission is granted to reproduce the con- tents, provided that such reproduction is not for profit and credit is given to the source. Table of Contents I. Introduction ………………………………………………………………………………. 1 1. Using History to Teach Computer Science and Related Disciplines ............................ 1 William Aspray and Atsushi Akera 2. The History of Computing: An Introduction for the Computer Scientist ……………….. 5 Thomas Haigh II. Curricular Issues and Strategies …………………………………………………… 27 3. The Challenge of Introducing History into a Computer Science Curriculum ………... 27 Paul E. Ceruzzi 4. History in the Computer Science Curriculum …………………………………………… 33 J.A.N. Lee 5. Using History in a Social Informatics Curriculum ....................................................... 39 William Aspray 6. Introducing Humanistic Content to Information Technology Students ……………….. 61 Atsushi Akera and Kim Fortun 7. The Synergy between Mathematical History and Education …………………………. 85 Thomas Drucker 8. Computing for the Humanities and Social Sciences …………………………………... 89 Nathan L. Ensmenger III. Specific Courses and Syllabi ………………………………………....................... 95 Course Descriptions & Syllabi 9.