ENSIKLOPEDIA BASIS DATA Dan PROGRAM KOMPUTER
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Evaluating a BASIC Approach to Sensor Network Node Programming
Evaluating A BASIC Approach to Sensor Network Node Programming J. Scott Miller Peter A. Dinda Robert P. Dick [email protected] [email protected] [email protected] Northwestern University Northwestern University University of Michigan Abstract 1 Introduction Sensor networks have the potential to empower domain Wireless sensor networks (WSNs) can be viewed as experts from a wide range of fields. However, presently they general purpose distributed computing platforms defined by are notoriously difficult for these domain experts to program, their spatial presence and an emphasis on environment mon- even though their applications are often conceptually simple. itoring. The most prominent applications of sensor networks We address this problem by applying the BASIC program- have thus far included monitoring applications with a variety ming language to sensor networks and evaluating its effec- of requirements, although WSNs need not be limited to these tiveness. BASIC has proven highly successful in the past in tasks. While WSNs are currently of great research interest, it allowing novices to write useful programs on home comput- is ultimately communities and users outside of these areas— ers. Our contributions include a user study evaluating how application domain experts—that have the most to gain from well novice (no programming experience) and intermediate the functionality that WSNs can provide. We focus on ap- (some programming experience) users can accomplish sim- plication domain experts who are programming novices and ple sensor network tasks in BASIC and in TinyScript (a prin- not WSN experts. Our goal is to make the development of cipally event-driven high-level language for node-oriented WSN applications by such individuals and groups tractable programming) and an evaluation of power consumption is- and, ideally, straightforward. -

Cost-Effective Compilation Techniques for Java Just-In-Time Compilers 3
IEICE TRANS. ??, VOL.Exx–??, NO.xx XXXX 200x 1 PAPER Cost-Effective Compilation Techniques for Java Just-in-Time Compilers Kazuyuki SHUDO†, Satoshi SEKIGUCHI†, Nonmembers, and Yoichi MURAOKA ††, Fel low SUMMARY Java Just-in-Time compilers have to satisfy a policies. number of requirements in conflict with each other. Effective execution of a generated code is not the only requirement, but 1. Ease of use as a base of researches. compilation time, memory consumption and compliance with the 2. Cost-effective development. Less labor and rela- Java Virtual Machine specification are also important. We have tively much effect. developed a Java Just-in-Time compiler keeping implementation 3. Adequate quality and performance for practical labor little. Another important objective is developing an ad- equate base of following researches which utilize this compiler. use. The proposed compilation techniques take low compilation cost and low development cost. This paper also describes optimization Compiler development involves much work on a methods implemented in the compiler, for instance, instruction parser, intermediate representations and a number of folding, exception handling with signals and code patching. optimizations. Because of it, we have to consider those key words: Runtime compilation, Java Virtual Machine, Stack human and engineering factor seriously in addition to caching, Instruction folding, Code patching technical requirements like performance. Our plan on the development of the JIT compiler was to have a prac- 1. Introduction tical compiler with work several man-month. Our an- other goal was specifically having a research base on Just-in-Time (JIT) compilers for Java bytecode have which we do following researches with less labor while to satisfy a number of requirements, which are differ- developing it with less work. -

Computer Supplement #19 ***********************
THE CRYPTOGRAM Summer 1994 *********************** COMPUTER SUPPLEMENT #19 *********************** In this issue: PATTERN SEARCHING BY COMPUTER | D MELIORA describes a method and gives a Pascal program to perform pattern word searching. SWAGMAN | BOATTAIL has some help for solving basic transposition ciphers like SWAG- MAN, and includes his Cipher library. INTERNET MAILING LIST | Three of the Krewe have started an electronic mailing list to help in solving cryptograms. REVIEWS | DAEDALUS has recommendations for three books and a software package. GW-BASIC CRACKING | A program to decrypt protected GW-BASIC programs. HIGH PRECISION BASIC | Details about a dialect of BASIC that handles large numbers with ease. Plus: News and notes for computerists interested in cryptography, and cryptographers in- terested in computers. Published in association with the American Cryptogram Association INTRODUCTORY MATERIAL The ACA and Your Computer (1p). Background on the ACA for computerists. (As printed in ACA and You, 1988 edition; [Also on Issue Disk #11] Using Your Home Computer (1p). Ciphering at the ACA level with a computer. (As printed in ACA and You, 1988 edition). Frequently Asked Questions (approx. 20p) with answers, from the Usenet newsgroup sci.crypt. REFERENCE MATERIAL BASICBUGS - Bugs and errors in GW-BASIC (1p). [Also on Issue Disk #11]. BBSFILES - List of filenames and descriptions of cryptographic files available on the ACA BBS (files also available on disk via mail). BIBLIOG | A bibliography of computer magazine articles and books dealing with cryptography. (Updated August 89). [available on Issue Disk #11]. CRYPTOSUB - Complete listing of Cryptographic Substitution Program as published by PHOENIX in sections in The Cryptogram 1983{1985. -

Picojava-II™ Programmer's Reference Manual
picoJava-II™ Programmer’s Reference Manual Sun Microsystems, Inc. 901 San Antonio Road Palo Alto, CA 94303 USA 650 960-1300 Part No.: 805-2800-06 March 1999 Copyright 1999 Sun Microsystems, Inc. 901 San Antonio Road, Palo Alto, California 94303 U.S.A. All rights reserved. The contents of this document are subject to the current version of the Sun Community Source License, picoJava Core (“the License”). You may not use this document except in compliance with the License. You may obtain a copy of the License by searching for “Sun Community Source License” on the World Wide Web at http://www.sun.com. See the License for the rights, obligations, and limitations governing use of the contents of this document. Sun, Sun Microsystems, the Sun logo and all Sun-based trademarks and logos, Java, picoJava, and all Java-based trademarks and logos are trademarks, registered trademarks, or service marks of Sun Microsystems, Inc. in the U.S. and other countries. All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International, Inc. in the U.S. and other countries. Products bearing SPARC trademarks are based upon an architecture developed by Sun Microsystems, Inc. DOCUMENTATION IS PROVIDED “AS IS” AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON- INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. THIS PUBLICATION COULD INCLUDE TECHNICAL INACCURACIES OR TYPOGRAPHICAL ERRORS. CHANGES ARE PERIODICALLY ADDED TO THE INFORMATION HEREIN; THESE CHANGES WILL BE INCORPORATED IN NEW EDITIONS OF THE PUBLICATION. -

Picojava-II™ Microarchitecture Guide
picoJava-II™ Microarchitecture Guide Sun Microsystems, Inc. 901 San Antonio Road Palo Alto, CA 94303 USA 650 960-1300 Part No.: 960-1160-11 March 1999 Copyright 1999 Sun Microsystems, Inc. 901 San Antonio Road, Palo Alto, California 94303 U.S.A. All rights reserved. The contents of this document are subject to the current version of the Sun Community Source License, picoJava Core (“the License”). You may not use this document except in compliance with the License. You may obtain a copy of the License by searching for “Sun Community Source License” on the World Wide Web at http://www.sun.com. See the License for the rights, obligations, and limitations governing use of the contents of this document. Sun, Sun Microsystems, the Sun logo and all Sun-based trademarks and logos, Java, picoJava, and all Java-based trademarks and logos are trademarks, registered trademarks, or service marks of Sun Microsystems, Inc. in the U.S. and other countries. All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International, Inc. in the U.S. and other countries. Products bearing SPARC trademarks are based upon an architecture developed by Sun Microsystems, Inc. DOCUMENTATION IS PROVIDED “AS IS” AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. THIS PUBLICATION COULD INCLUDE TECHNICAL INACCURACIES OR TYPOGRAPHICAL ERRORS. CHANGES ARE PERIODICALLY ADDED TO THE INFORMATION HEREIN; THESE CHANGES WILL BE INCORPORATED IN NEW EDITIONS OF THE PUBLICATION. -

C:\Andrzej\PDF\ABC Nagrywania P³yt CD\1 Strona.Cdr
IDZ DO PRZYK£ADOWY ROZDZIA£ SPIS TREFCI Wielka encyklopedia komputerów KATALOG KSI¥¯EK Autor: Alan Freedman KATALOG ONLINE T³umaczenie: Micha³ Dadan, Pawe³ Gonera, Pawe³ Koronkiewicz, Rados³aw Meryk, Piotr Pilch ZAMÓW DRUKOWANY KATALOG ISBN: 83-7361-136-3 Tytu³ orygina³u: ComputerDesktop Encyclopedia Format: B5, stron: 1118 TWÓJ KOSZYK DODAJ DO KOSZYKA Wspó³czesna informatyka to nie tylko komputery i oprogramowanie. To setki technologii, narzêdzi i urz¹dzeñ umo¿liwiaj¹cych wykorzystywanie komputerów CENNIK I INFORMACJE w ró¿nych dziedzinach ¿ycia, jak: poligrafia, projektowanie, tworzenie aplikacji, sieci komputerowe, gry, kinowe efekty specjalne i wiele innych. Rozwój technologii ZAMÓW INFORMACJE komputerowych, trwaj¹cy stosunkowo krótko, wniós³ do naszego ¿ycia wiele nowych O NOWOFCIACH mo¿liwoYci. „Wielka encyklopedia komputerów” to kompletne kompendium wiedzy na temat ZAMÓW CENNIK wspó³czesnej informatyki. Jest lektur¹ obowi¹zkow¹ dla ka¿dego, kto chce rozumieæ dynamiczny rozwój elektroniki i technologii informatycznych. Opisuje wszystkie zagadnienia zwi¹zane ze wspó³czesn¹ informatyk¹; przedstawia zarówno jej historiê, CZYTELNIA jak i trendy rozwoju. Zawiera informacje o firmach, których produkty zrewolucjonizowa³y FRAGMENTY KSI¥¯EK ONLINE wspó³czesny Ywiat, oraz opisy technologii, sprzêtu i oprogramowania. Ka¿dy, niezale¿nie od stopnia zaawansowania swojej wiedzy, znajdzie w niej wyczerpuj¹ce wyjaYnienia interesuj¹cych go terminów z ró¿nych bran¿ dzisiejszej informatyki. • Komunikacja pomiêdzy systemami informatycznymi i sieci komputerowe • Grafika komputerowa i technologie multimedialne • Internet, WWW, poczta elektroniczna, grupy dyskusyjne • Komputery osobiste — PC i Macintosh • Komputery typu mainframe i stacje robocze • Tworzenie oprogramowania i systemów komputerowych • Poligrafia i reklama • Komputerowe wspomaganie projektowania • Wirusy komputerowe Wydawnictwo Helion JeYli szukasz ]ród³a informacji o technologiach informatycznych, chcesz poznaæ ul. -

(19) United States (12) Patent Application Publication (10) Pub
US 20060190934A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2006/0190934 A1 Kielstra et al. (43) Pub. Date: Aug. 24, 2006 (54) METHOD AND APPARATUS FOR INLINING Publication Classi?cation NATIVE FUNCTIONS INTO COMPILED JAVA CODE (51) Int. Cl. G06F 9/45 (2006.01) (52) US. Cl. ............................................................ ..717/148 (75) Inventors: Allan Henry Kielstra, Ajax (CA); Levon Sassoon Stepanian, Toronto (CA); Kevin Alexander Stoodley, (57) ABSTRACT Richmond Hill (CA) A method, apparatus, and computer instructions are pro vided for inlining native functions into compiled Java code. Correspondence Address: A conversion engine is provided by the present invention for IBM CORP (YA) converting the intermediate representation of native func C/O YEE & ASSOCIATES PC tions to the just-in-time (JIT) compiler’s intermediate rep PO. BOX 802333 resentation. With the converted intermediate representation, DALLAS, TX 75380 (US) an inliner recursively inlines the converted JIT compiler’s intermediate representation into the native callsite to remove the need of invoking the native function and subsequent (73) Assignee: International Business Machines Cor native calls made by the function. The inlining process poration, Armonk, NY continues until either a call to an opaque function is encoun tered or until a JIT compiler intermediate representation groWth limits are reached. The inliner also replaces calls to (21) Appl. No.: 11/062,293 most native functions that are non-inlineable or opaque With calls -

Java and the JVM
Java and the JVM Martin Schöberl Overview History and Java features Java technology The Java language A first look into the JVM Disassembling of .class files Java and the JVM 2 History of a Young Java 1992 Oak for a PDA on a SPARC (*7) 1995 Official release as Java – Internet 1997 picoJava – Sun’s Java processor 1998 RTSJ specification start as JSR-01 1999 split into J2SE and J2EE 2000 J2ME 2002 RTSJ final release 2002 first version of JOP ;-) Java and the JVM 3 Java features Simple and object oriented Look and feel of C Simplified object model with single inheritance Portability Java compiler generates bytecodes Runtime systems for various platforms Size and behavior of basic data types defined Write once, run/debug anywhere Java and the JVM 4 Java features cont. Availability Windows, Linux, Solaris,… Embedded systems Compiler and runtime are free Free IDEs: Eclipse, Netbeans Library Rich class library Part of the definition Standard GUI toolkit Java and the JVM 5 Java features cont. Built-in model for concurrency Threads at the language level Synchronization Libraries are thread-safe Safety No Pointer! Extensive compile-time checking Runtime checking Automatic memory management – GC Java and the JVM 6 Java system overview Java and the JVM 7 Java Technology The Java programming language The library (JDK) The Java virtual machine (JVM) Instruction set Binary format Verification Java and the JVM 8 Java Primitive Data Types boolean either true or false char 16-bit Unicode character (unsigned) -

20 Years of Java
20 years of Java Vladimir Ivanov HotSpot JVM Compile r Twitter: @iwan0www Oracle Corp. OpenJDK: vlivanov 1 28.11.2015 Copyright © 2015, Oracle and/or its affiliates. All rights reserved 20 years of Java (The Platform) Vladimir Ivanov HotSpot JVM Compile r Twitter: @iwan0www Oracle Corp. OpenJDK: vlivanov 2 Copyright © 2015, Oracle and/or its affiliates. All rights reserved Safe Harbor Statement The preceding is intended to outline our general product direction. It is intended for information purposes only, and may not be incorporated into any contract. It is not a commitment to deliver any material, code, or functionality, and should not be relied upon in making purchasing decisions. The development, release, and timing of any features or functionality described for Oracle’s products remains at the sole discretion of Oracle. 3 Copyright © 2015, Oracle and/or its affiliates. All rights reserved About me Joined Sun Microsystems (SPBDC) to work JDK 1.0 on HotSpot JVM Now 1996 2002 2005 2010 2015 Wrote my first Became part of program in Java. Oracle Corp. after acquisition 4 Copyright © 2015, Oracle and/or its affiliates. All rights reserved 1991: Project Green 5 Copyright © 2015, Oracle and/or its affiliates. All rights reserved 1991: *7 (StarSeven) Oak programming language 6 Copyright © 2015, Oracle and/or its affiliates. All rights reserved 1991: *7 (StarSeven) Duke 7 Copyright © 2015, Oracle and/or its affiliates. All rights reserved 1994: WebRunner/HotJava browser 8 Copyright © 2015, Oracle and/or its affiliates. All rights reserved 1995: First release: 1.0a2 9 Copyright © 2015, Oracle and/or its affiliates. -

Building Secure ASP.NET Applications: Authentication, Authorization, and Secure Communication
Building Secure ASP.NET Applications: Authentication, Authorization, and Secure Communication http://msdn.microsoft.com/library/default.asp?url=/library/en-us/dnnetsec/html/secnetlpMSDN.asp Roadmap J.D. Meier, Alex Mackman, Michael Dunner, and Srinath Vasireddy Microsoft Corporation November 2002 Applies to: Microsoft® .NET Framework version 1.0 ASP.NET Enterprise Services Web services .NET Remoting ADO.NET Visual Studio® .NET SQL™ Server Windows® 2000 Summary: This guide presents a practical, scenario driven approach to designing and building secure ASP.NET applications for Windows 2000 and version 1.0 of the .NET Framework. It focuses on the key elements of authentication, authorization, and secure communication within and across the tiers of distributed .NET Web applications. (This roadmap: 6 printed pages; the entire guide: 608 printed pages) Download Download Building Secure ASP.NET Applications in .pdf format. (1.67 MB, 608 printed pages) Contents What This Guide Is About Part I, Security Models Part II, Application Scenarios Part III, Securing the Tiers Part IV, Reference Who Should Read This Guide? What You Must Know Feedback and Support Collaborators Recommendations and sample code in the guide were built and tested using Visual Studio .NET Version 1.0 and validated on servers running Windows 2000 Advanced Server SP 3, .NET Framework SP 2, and SQL Server 2000 SP 2. What This Guide Is About This guide focuses on: • Authentication (to identify the clients of your application) • Authorization (to provide access controls for those clients) • Secure communication (to ensure that messages remain private and are not altered by unauthorized parties) Why authentication, authorization, and secure communication? Security is a broad topic. -

Mathematical Sciences Meetings and Conferences Section
page 1349 Calendar of AMS Meetings and Conferences Thla calandar lists all meetings which have been approved prior to Mathematical Society in the issue corresponding to that of the Notices the date this issue of Notices was sent to the press. The summer which contains the program of the meeting, insofar as is possible. and annual meetings are joint meetings of the Mathematical Associ Abstracts should be submitted on special forms which are available in ation of America and the American Mathematical Society. The meet many departments of mathematics and from the headquarters office ing dates which fall rather far in the future are subject to change; this of the Society. Abstracts of papers to be presented at the meeting is particularly true of meetings to which no numbers have been as must be received at the headquarters of the Society in Providence, signed. Programs of the meetings will appear in the issues indicated Rhode Island, on or before the deadline given below for the meet below. First and supplementary announcements of the meetings will ing. Note that the deadline for abstracts for consideration for pre have appeared in earlier issues. sentation at special sessions is usually three weeks earlier than that Abatracta of papara presented at a meeting of the Society are pub specified below. For additional information, consult the meeting an lished in the journal Abstracts of papers presented to the American nouncements and the list of organizers of special sessions. Meetings Abstract Program Meeting# Date Place Deadline Issue -
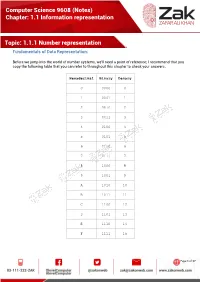
(Notes) Chapter: 1.1 Information Representation Topic
Computer Science 9608 (Notes) Chapter: 1.1 Information representation Topic: 1.1.1 Number representation Fundamentals of Data Representation: Before we jump into the world of number systems, we'll need a point of reference; I recommend that you copy the following table that you can refer to throughout this chapter to check your answers. Hexadecimal Binary Denary 0 0000 0 1 0001 1 2 0010 2 3 0011 3 4 0100 4 5 0101 5 6 0110 6 7 0111 7 8 1000 8 9 1001 9 A 1010 10 B 1011 11 C 1100 12 D 1101 13 E 1110 14 F 1111 15 Page 1 of 17 Computer Science 9608 (Notes) Chapter: 1.1 Information representation Topic: 1.1.1 Number representation Denary/Decimal Denary is the number system that you have most probably grown up with. It is also another way of saying base 10. This means that there are 10 different numbers that you can use for each digit, namely: 0,1,2,3,4,5,6,7,8,9 Notice that if we wish to say 'ten', we use two of the numbers from the above digits, 1 and 0. Thousands Hundreds Tens Units 10^3 10^2 10^1 10^0 1000 100 10 1 5 9 7 3 Using the above table we can see that each column has a different value assigned to it. And if we know the column values we can know the number, this will be very useful when we start looking at other base systems. Obviously, the number above is: five-thousands, nine-hundreds, seven-tens and three-units.