(Notes) Chapter: 1.1 Information Representation Topic
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Evaluating a BASIC Approach to Sensor Network Node Programming
Evaluating A BASIC Approach to Sensor Network Node Programming J. Scott Miller Peter A. Dinda Robert P. Dick [email protected] [email protected] [email protected] Northwestern University Northwestern University University of Michigan Abstract 1 Introduction Sensor networks have the potential to empower domain Wireless sensor networks (WSNs) can be viewed as experts from a wide range of fields. However, presently they general purpose distributed computing platforms defined by are notoriously difficult for these domain experts to program, their spatial presence and an emphasis on environment mon- even though their applications are often conceptually simple. itoring. The most prominent applications of sensor networks We address this problem by applying the BASIC program- have thus far included monitoring applications with a variety ming language to sensor networks and evaluating its effec- of requirements, although WSNs need not be limited to these tiveness. BASIC has proven highly successful in the past in tasks. While WSNs are currently of great research interest, it allowing novices to write useful programs on home comput- is ultimately communities and users outside of these areas— ers. Our contributions include a user study evaluating how application domain experts—that have the most to gain from well novice (no programming experience) and intermediate the functionality that WSNs can provide. We focus on ap- (some programming experience) users can accomplish sim- plication domain experts who are programming novices and ple sensor network tasks in BASIC and in TinyScript (a prin- not WSN experts. Our goal is to make the development of cipally event-driven high-level language for node-oriented WSN applications by such individuals and groups tractable programming) and an evaluation of power consumption is- and, ideally, straightforward. -

Computer Supplement #19 ***********************
THE CRYPTOGRAM Summer 1994 *********************** COMPUTER SUPPLEMENT #19 *********************** In this issue: PATTERN SEARCHING BY COMPUTER | D MELIORA describes a method and gives a Pascal program to perform pattern word searching. SWAGMAN | BOATTAIL has some help for solving basic transposition ciphers like SWAG- MAN, and includes his Cipher library. INTERNET MAILING LIST | Three of the Krewe have started an electronic mailing list to help in solving cryptograms. REVIEWS | DAEDALUS has recommendations for three books and a software package. GW-BASIC CRACKING | A program to decrypt protected GW-BASIC programs. HIGH PRECISION BASIC | Details about a dialect of BASIC that handles large numbers with ease. Plus: News and notes for computerists interested in cryptography, and cryptographers in- terested in computers. Published in association with the American Cryptogram Association INTRODUCTORY MATERIAL The ACA and Your Computer (1p). Background on the ACA for computerists. (As printed in ACA and You, 1988 edition; [Also on Issue Disk #11] Using Your Home Computer (1p). Ciphering at the ACA level with a computer. (As printed in ACA and You, 1988 edition). Frequently Asked Questions (approx. 20p) with answers, from the Usenet newsgroup sci.crypt. REFERENCE MATERIAL BASICBUGS - Bugs and errors in GW-BASIC (1p). [Also on Issue Disk #11]. BBSFILES - List of filenames and descriptions of cryptographic files available on the ACA BBS (files also available on disk via mail). BIBLIOG | A bibliography of computer magazine articles and books dealing with cryptography. (Updated August 89). [available on Issue Disk #11]. CRYPTOSUB - Complete listing of Cryptographic Substitution Program as published by PHOENIX in sections in The Cryptogram 1983{1985. -

Management of Data Elements in Information Processing
PB-249-530 MANAGEMENT OF DATA ELEMENTS IN INFORMATION PROCESSING U.S. DEPARTMENT OF COMMERCE / National Bureau of Standards SECOND NATIONAL SYMPOSIUM NATIONAL BUREAU OF STANDARDS GAITHERSBURG, MARYLAND 1975 OCTOBER 23-24 Available by purchase from the National Technical Information Service, 5285 Port Royal Road, Springfield, Va. 221 Price: $9.25 hardcopy; $2.25 microfiche. National Technical Information Service U. S. DEPARTMENT OF COMMERCE PB-249-530 Management of Data Elements in Information Processing Proceedings of a Second Symposium Sponsored by the American National Standards Institute and by The National Bureau of Standards 1975 October 23-24 NBS, Gaithersburg, Maryland Hazel E. McEwen, Editor Institute for Computer Sciences and Technology National Bureau of Standards Washington, D.C. 20234 U.S. DEPARTMENT OF COMMERCE, Elliot L. Richardson, Secrefary NATIONAL BUREAU OF STANDARDS, Ernest Ambler, Acfing Direc/or Table of Contents Page Introduction to the Program of the Second National Symposium on The Management of Data Elements in Information Processing ix David V. Savidge, Program Chairman On-Line Tactical Data Inputting: Research in Operator Training and Performance 1 Irving Alderman, Ph.D. "Turning the Corner" on MIS, A Proposed Program of Data Standards in Post-Secondary Education 9 Donald R. Arnold, Ph.D. ASCII - The Data Alphabet That Will Endure 17 Robert W. Bemer Techniques in Developing Standard Procedures for Data Editing 23 George W. Covill An Adaptive File Management Systems 45 Dennis L. Dance and Udo W. Pooch (Given by Dance) A Focus on the Role of the Data Manager 57 Ruth M, Davis, Ph.D. A Proposed Standard Routine for Generating Proposed Standard Check Characters 61 Paul -Andre Desjardins Methodology for Development of Standard Data Elements within Multiple Public Agencies 69 L. -

H/W3 Binary to Denary
Name ___________________________________ Form ________ H/W Year 8 Homework Booklet Theme 1 Data Representation Computers themselves, and “ software yet to be developed, will revolutionize “ the way we learn. - Steve Jobs Founder of Apple Introduction What language does a computer understand? How does a computer represent data, information and images? Soon, you will be able to answer the questions above! In this theme we will explore the different ways in which data is represented by the computer, ranging from numbers to images. We will learn and understand the number bases and conversions between denary and binary. We will also be looking at units of information, binary addition and how we can convert binary data into a black and white image! See the key below to find out what the icons below mean: Self Assessment: You will mark your work at the start of next lesson. ENSURE YOU COMPELTE HOMEWORK AS MARKS WILL BE COLLECTED IN! Edmodo Quiz: The will be a quiz the start of next lesson based on your homework. SO MAKE SURE YOU REVISE! Peer Assessment: Homework marked by your class mate at the start of next lesson. MAKE SURE YOU HAVE YOUR HOMEWORK DONE SO YOU CAN SWAP WITH ANOTHER PUPIL! Stuck? Got a question? Email your teacher. Mr Rifai (Head of Computing) [email protected] Miss Davison [email protected] Miss Pascoe [email protected] 2 Due Date: H/W1 Data & Number Bases Read and digest the information below. You will be quizzed next lesson! Any set of characters gathered and translated for What is Data? some purpose. -

On Identifying Basic Discourse Units in Speech: Theoretical and Empirical Issues
Discours Revue de linguistique, psycholinguistique et informatique. A journal of linguistics, psycholinguistics and computational linguistics 4 | 2009 Linearization and Segmentation in Discourse On identifying basic discourse units in speech: theoretical and empirical issues Liesbeth Degand and Anne Catherine Simon Electronic version URL: http://journals.openedition.org/discours/5852 DOI: 10.4000/discours.5852 ISSN: 1963-1723 Publisher: Laboratoire LATTICE, Presses universitaires de Caen Electronic reference Liesbeth Degand and Anne Catherine Simon, « On identifying basic discourse units in speech: theoretical and empirical issues », Discours [Online], 4 | 2009, Online since 30 June 2009, connection on 10 December 2020. URL : http://journals.openedition.org/discours/5852 ; DOI : https://doi.org/ 10.4000/discours.5852 Discours est mis à disposition selon les termes de la licence Creative Commons Attribution - Pas d'Utilisation Commerciale - Pas de Modification 4.0 International. Discours 4 | 2009, Linearization and Segmentation in Discourse (Special issue) On identifying basic discourse units in speech: theoretical and empirical issues Liesbeth Degand1,2, Anne Catherine Simon2 1FNRS, 2Université catholique de Louvain Abstract: In spite of its crucial role in discourse segmentation and discourse interpretation, there is no consensus in the literature on what a discourse unit is and how it should be identified. Working with spoken data, we claim that the basic discourse unit (BDU) is a multi-dimensional unit that should be defined in terms of two linguistic criteria: prosody and syntax. In this paper, we explain which criteria are used to perform the prosodic and syntactic segmentation, and how these levels are mapped onto one another. We discuss three types BDUs (one-to-one, syntax-bound, prosody- bound) and open up a number of theoretical issues with respect to their function in discourse interpretation. -

Lecture Notes
CSCI E-84 A Practical Approach to Data Science Ramon A. Mata-Toledo, Ph.D. Professor of Computer Science Harvard University Unit 1 - Lecture 1 January, Wednesday 27, 2016 Required Textbooks Main Objectives of the Course This course is an introduction to the field of data science and its applicability to the business world. At the end of the semester you should be able to: • Understand how data science fits in an organization and gather, select, and model large amounts of data. • Identify the appropriate data and the methods that will allow you to extract knowledge from this data using the programming language R. What This Course is NOT is an in-depth calculus based statistic research environment . What is this course all about? It IS is a practical “hands-on approach” to understanding the methodology and tools of Data Science from a business prospective. Some of the technical we will briefly consider are: • Statistics • Database Querying • SQL • Data Warehousing • Regression Analysis • Explanatory versus Predictive Modeling Brief History of Data Science/Big Data The term data science can be considered the result of three main factors: • Evolution of data processing methods • Internet – particularly the Web 2.0 • Technological Advancements in computer processing speed/storage and development of algorithms for extracting useful information and knowledge from big data Brief History of Data Science/Big Data (continuation) However, “…Already seventy years ago we encounter the first attempts to quantify the growth rate in the volume of data or what has popularly been known as the “information explosion” (a term first used in 1941, according to the Oxford English Dictionary). -

Download Full Book
Introduction to Computing Explorations in Language, Logic, and Machines David Evans University of Virginia For the latest version of this book and supplementary materials, visit: http://computingbook.org Version: August 19, 2011 Attribution-Noncommercial-Share Alike 3.0 United States License Contents 1 Computing 1 1.1 Processes, Procedures, and Computers . 2 1.2 Measuring Computing Power . 3 1.2.1 Information . 3 1.2.2 Representing Data . 8 1.2.3 Growth of Computing Power . 12 1.3 Science, Engineering, and the Liberal Arts . 13 1.4 Summary and Roadmap . 16 Part I: Defining Procedures 2 Language 19 2.1 Surface Forms and Meanings . 19 2.2 Language Construction . 20 2.3 Recursive Transition Networks . 22 2.4 Replacement Grammars . 26 2.5 Summary . 32 3 Programming 35 3.1 Problems with Natural Languages . 36 3.2 Programming Languages . 37 3.3 Scheme . 39 3.4 Expressions . 40 3.4.1 Primitives . 40 3.4.2 Application Expressions . 41 3.5 Definitions . 44 3.6 Procedures . 45 3.6.1 Making Procedures . 45 3.6.2 Substitution Model of Evaluation . 46 3.7 Decisions . 48 3.8 Evaluation Rules . 50 3.9 Summary . 52 4 Problems and Procedures 53 4.1 Solving Problems . 53 4.2 Composing Procedures . 54 4.2.1 Procedures as Inputs and Outputs . 55 4.3 Recursive Problem Solving . 56 4.4 Evaluating Recursive Applications . 64 4.5 Developing Complex Programs . 67 4.5.1 Printing . 68 4.5.2 Tracing . 69 4.6 Summary . 73 5 Data 75 5.1 Types . 75 5.2 Pairs . -

Experimental Museology
EXPERIMENTAL MUSEOLOGY Experimental Museology scrutinizes innovative endeavours to transform museum interactions with the world. Analysing cutting-edge cases from around the globe, the volume demonstrates how museums can design, apply and assess new modes of audience engagement and participation. Written by an interdisciplinary group of researchers and research-led professionals, the book argues that museum transformations must be focussed on conceptualising and documenting the everyday challenges and choices facing museums, especially in relation to wider social, political and economic ramifications. In order to illuminate the complexity of these challenges, the volume is structured into three related key dimensions of museum practice – namely institutions, representations and users. Each chapter is based on a curatorial design proposed and performed in collaboration between university-based academics and a museum. Taken together, the chapters provide insights into a diversity of geographical contexts, fields and museums, thus building a comprehensive and reflexive repository of design practices and formative experiments that can help strengthen future museum research and design. Experimental Museology will be of great value to academics and students in the fieldsof museum, gallery and heritage studies, as well as architecture, design, communication and cultural studies. It will also be of interest to museum professionals and anyone else who is interested in learning more about experimentation and design as resources in museums. Marianne Achiam has a PhD in science education, and is an associate professor at the Department of Science Education, University of Copenhagen, Denmark. Michael Haldrup is a professor (wsr) in visual culture and performance design at Roskilde University, Denmark. Kirsten Drotner is a professor of media studies at the University of Southern Denmark and director of two national R&D programmes DREAM and Our Museum. -

Building Secure ASP.NET Applications: Authentication, Authorization, and Secure Communication
Building Secure ASP.NET Applications: Authentication, Authorization, and Secure Communication http://msdn.microsoft.com/library/default.asp?url=/library/en-us/dnnetsec/html/secnetlpMSDN.asp Roadmap J.D. Meier, Alex Mackman, Michael Dunner, and Srinath Vasireddy Microsoft Corporation November 2002 Applies to: Microsoft® .NET Framework version 1.0 ASP.NET Enterprise Services Web services .NET Remoting ADO.NET Visual Studio® .NET SQL™ Server Windows® 2000 Summary: This guide presents a practical, scenario driven approach to designing and building secure ASP.NET applications for Windows 2000 and version 1.0 of the .NET Framework. It focuses on the key elements of authentication, authorization, and secure communication within and across the tiers of distributed .NET Web applications. (This roadmap: 6 printed pages; the entire guide: 608 printed pages) Download Download Building Secure ASP.NET Applications in .pdf format. (1.67 MB, 608 printed pages) Contents What This Guide Is About Part I, Security Models Part II, Application Scenarios Part III, Securing the Tiers Part IV, Reference Who Should Read This Guide? What You Must Know Feedback and Support Collaborators Recommendations and sample code in the guide were built and tested using Visual Studio .NET Version 1.0 and validated on servers running Windows 2000 Advanced Server SP 3, .NET Framework SP 2, and SQL Server 2000 SP 2. What This Guide Is About This guide focuses on: • Authentication (to identify the clients of your application) • Authorization (to provide access controls for those clients) • Secure communication (to ensure that messages remain private and are not altered by unauthorized parties) Why authentication, authorization, and secure communication? Security is a broad topic. -

Mathematical Sciences Meetings and Conferences Section
page 1349 Calendar of AMS Meetings and Conferences Thla calandar lists all meetings which have been approved prior to Mathematical Society in the issue corresponding to that of the Notices the date this issue of Notices was sent to the press. The summer which contains the program of the meeting, insofar as is possible. and annual meetings are joint meetings of the Mathematical Associ Abstracts should be submitted on special forms which are available in ation of America and the American Mathematical Society. The meet many departments of mathematics and from the headquarters office ing dates which fall rather far in the future are subject to change; this of the Society. Abstracts of papers to be presented at the meeting is particularly true of meetings to which no numbers have been as must be received at the headquarters of the Society in Providence, signed. Programs of the meetings will appear in the issues indicated Rhode Island, on or before the deadline given below for the meet below. First and supplementary announcements of the meetings will ing. Note that the deadline for abstracts for consideration for pre have appeared in earlier issues. sentation at special sessions is usually three weeks earlier than that Abatracta of papara presented at a meeting of the Society are pub specified below. For additional information, consult the meeting an lished in the journal Abstracts of papers presented to the American nouncements and the list of organizers of special sessions. Meetings Abstract Program Meeting# Date Place Deadline Issue -
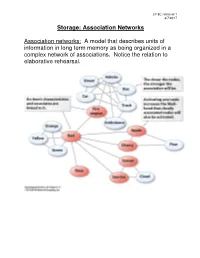
Storage: Association Networks Association Networks: a Model That
LP 8C retrieval 1 3/7/2017 Storage: Association Networks Association networks: A model that describes units of information in long term memory as being organized in a complex network of associations. Notice the relation to elaborative rehearsal. LP 8C retrieval 2 3/7/2017 Broken Associations Make Retrieval Difficult LP 8C retrieval 3 3/7/2017 Schemas and Encoding Schemas: Cognitive structures that help us perceive, organize, process and use information ( page 280). In the following example, a schema helps organize the seemingly random and obscure statements. Instructions: Take a minute to read through this paragraph. After a minute, try to recall as much information about the paragraph as you can. Do the best you can, exact word for word recall is not required as long as it is close. The procedure is actually quite simple. First arrange things into different groups. Of course, one pile may be sufficient depending on how much there is to do. If you have to go somewhere else due to lack of facilities that is the next step, otherwise you are pretty well set. It is important not to overdo things. That is, it is better to do too few things at once than too many. In the short run this may not seem important but complications can easily arise. A mistake can be expensive as well. At first, the whole procedure will seem complicated. Soon, however, it will become just another facet of life. It is difficult to foresee any end of the necessity for this task in the immediate future, but then one never can tell. -

THE ULTIMATE GAMES and 4K ENTERTAINMENT SYSTEM Xbox One S with FIFA 17 Bundle from £249.99
DECEMBER 2016 zavvi.com THE ULTIMATE GAMES AND 4K ENTERTAINMENT SYSTEM Xbox One S with FIFA 17 Bundle from £249.99 Up to 4K HDR 40% 1TB Ultra HD High Dynamic Range Smaller Storage The coolest, exclusively designed shirts with a book or graphic novel - every month! ALL FOR ONLY £9.99 Issue #9 On Sale Now! Find out more at zavvi.com/threads P2 // THREADS by ZBOX WWW.ZAVVI.COM ‘The best games console ever made’ - Shortlist 4 // MUST WATCH BOX SETS 16-18 // THE GADGET LIST Get cosy with Game of Thrones, Grey’s Anatomy Drones, speakers and audio gadgets for the and more. big kids. 5 // 2016’S HOTTEST MOVIES 19 // WRAP UP There’s something for all the family from The BFG Update your style for the season with knits and to Suicide Squad. shirts from Jack & Jones, Brave Soul and more. 6 // ON TOUR 20 // SANTA SUPERHEROES Go on tour with The Beatles, Oasis and Bolt in our Give your inner superhero a festive twist with top documentaries from 2016. Christmas sweatshirts. 7 // STEELBOOKS 21-22 // NEW SEASON FASHION Complete your collection with this year’s ‘Tis the season to lounge with our collection of top releases. loungewear and knitwear. 8-9 // WINTER READY BOX SETS 23-24 // THE GIFT OF GEEK Chill this winter with your favourite box sets. Give the gift of geek this Christmas with our out of this world collection 10-11 // ESSENTIAL PS4 Everything you need to enhance your 25-27 // MUST-HAVE CHRISTMAS TOYS PS4 experience. Look no further for the top toys this Christmas.