Building Secure ASP.NET Applications: Authentication, Authorization, and Secure Communication
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Evaluating a BASIC Approach to Sensor Network Node Programming
Evaluating A BASIC Approach to Sensor Network Node Programming J. Scott Miller Peter A. Dinda Robert P. Dick [email protected] [email protected] [email protected] Northwestern University Northwestern University University of Michigan Abstract 1 Introduction Sensor networks have the potential to empower domain Wireless sensor networks (WSNs) can be viewed as experts from a wide range of fields. However, presently they general purpose distributed computing platforms defined by are notoriously difficult for these domain experts to program, their spatial presence and an emphasis on environment mon- even though their applications are often conceptually simple. itoring. The most prominent applications of sensor networks We address this problem by applying the BASIC program- have thus far included monitoring applications with a variety ming language to sensor networks and evaluating its effec- of requirements, although WSNs need not be limited to these tiveness. BASIC has proven highly successful in the past in tasks. While WSNs are currently of great research interest, it allowing novices to write useful programs on home comput- is ultimately communities and users outside of these areas— ers. Our contributions include a user study evaluating how application domain experts—that have the most to gain from well novice (no programming experience) and intermediate the functionality that WSNs can provide. We focus on ap- (some programming experience) users can accomplish sim- plication domain experts who are programming novices and ple sensor network tasks in BASIC and in TinyScript (a prin- not WSN experts. Our goal is to make the development of cipally event-driven high-level language for node-oriented WSN applications by such individuals and groups tractable programming) and an evaluation of power consumption is- and, ideally, straightforward. -

Servicio Fitosanitario Del Estado Risk Advisory
Servicio Fitosanitario del Estado Risk Advisory Informe de Control Interno “Resultados del estudio de auditoría relativo a la evaluación del sistema de control interno en materia de tecnologías de la información, implementado para cumplir con lo dispuesto en el Decreto Ejecutivo N.° 37549-JP (Reglamento para la Protección de los Programas de Cómputo en los Ministerios e Instituciones adscritas al Gobierno Central)” Ref.: N° AI-SFE-SA-INF-005-2016 00 Servicio Fitosanitario del Estado | Tabla de contenido Tabla de contenido Tabla de contenido 1 Resumen ejecutivo 3 Introducción 4 Resultados del estado de los inventarios y del licenciamiento 14 Seguimiento al informe AI-SFE-SA-INF-005- 2015 34 Resultados - Hallazgos 36 Anexos 61 01 Servicio Fitosanitario del Estado | TablaInforme de decontenido Control Interno “Resultados del estudio de auditoría relativo a la evaluación del sistema de control interno en materia de tecnologías de la información, implementado para cumplir con lo dispuesto en el Decreto Ejecutivo N. 37549-JP (Reglamento Informe de Control Interno “Resultados del estudio de auditoría relativo a la evaluación del sistema de control interno en materia de tecnologías de la información, implementado para cumplir con lo dispuesto en el Decreto Ejecutivo N.° 37549-JP (Reglamento para la Protección de los Programas de Cómputo en los Ministerios e Instituciones adscritas al Gobierno Central)” 02 Servicio Fitosanitario del Estado | Resumen ejecutivo Resumen ejecutivo Objetivo El presente estudio de auditoría relacionado con la “Evaluación del sistema de control interno en materia de tecnologías de la información, implementado para cumplir con lo dispuesto en el Decreto Ejecutivo N.° 37549-JP (Reglamento para la Protección de los Programas de Cómputo en los Ministerios e Instituciones Adscritas al Gobierno Central)”, se llevó a cabo en atención al Plan Anual de Labores (2016) de la Auditoría Interna del Servicio Fitosanitario del Estado (SFE). -

Middleware in Action 2007
Technology Assessment from Ken North Computing, LLC Middleware in Action Industrial Strength Data Access May 2007 Middleware in Action: Industrial Strength Data Access Table of Contents 1.0 Introduction ............................................................................................................. 2 Mature Technology .........................................................................................................3 Scalability, Interoperability, High Availability ...................................................................5 Components, XML and Services-Oriented Architecture..................................................6 Best-of-Breed Middleware...............................................................................................7 Pay Now or Pay Later .....................................................................................................7 2.0 Architectures for Distributed Computing.................................................................. 8 2.1 Leveraging Infrastructure ........................................................................................ 8 2.2 Multi-Tier, N-Tier Architecture ................................................................................. 9 2.3 Persistence, Client-Server Databases, Distributed Data ....................................... 10 Client-Server SQL Processing ......................................................................................10 Client Libraries .............................................................................................................. -

Computer Supplement #19 ***********************
THE CRYPTOGRAM Summer 1994 *********************** COMPUTER SUPPLEMENT #19 *********************** In this issue: PATTERN SEARCHING BY COMPUTER | D MELIORA describes a method and gives a Pascal program to perform pattern word searching. SWAGMAN | BOATTAIL has some help for solving basic transposition ciphers like SWAG- MAN, and includes his Cipher library. INTERNET MAILING LIST | Three of the Krewe have started an electronic mailing list to help in solving cryptograms. REVIEWS | DAEDALUS has recommendations for three books and a software package. GW-BASIC CRACKING | A program to decrypt protected GW-BASIC programs. HIGH PRECISION BASIC | Details about a dialect of BASIC that handles large numbers with ease. Plus: News and notes for computerists interested in cryptography, and cryptographers in- terested in computers. Published in association with the American Cryptogram Association INTRODUCTORY MATERIAL The ACA and Your Computer (1p). Background on the ACA for computerists. (As printed in ACA and You, 1988 edition; [Also on Issue Disk #11] Using Your Home Computer (1p). Ciphering at the ACA level with a computer. (As printed in ACA and You, 1988 edition). Frequently Asked Questions (approx. 20p) with answers, from the Usenet newsgroup sci.crypt. REFERENCE MATERIAL BASICBUGS - Bugs and errors in GW-BASIC (1p). [Also on Issue Disk #11]. BBSFILES - List of filenames and descriptions of cryptographic files available on the ACA BBS (files also available on disk via mail). BIBLIOG | A bibliography of computer magazine articles and books dealing with cryptography. (Updated August 89). [available on Issue Disk #11]. CRYPTOSUB - Complete listing of Cryptographic Substitution Program as published by PHOENIX in sections in The Cryptogram 1983{1985. -

Microsoft Windows Server 2008 PKI and Deploying the Ncipher Hardware Security Module
This is a joint nCipher and IdentIT authored whitepaper Microsoft Windows Server 2008 PKI and Deploying the nCipher Hardware Security Module Abstract This paper discusses the benefits that are unique to deploying the integrated solution of the Windows Server 2008 PKI and the nCipher nShield and netHSM hardware security modules (HSM). This includes the essential concepts and technologies used to deploy a PKI and the best practice security and life cycle key management features provided by nCipher HSMs.. MicrosofT WIndoWs server 2008 PKI and dePloyIng The nCipher hardWare seCurity Module Introduction...............................................................................................................................................................................................3 PKI – A Crucial Component to Securing e-commerce ......................................................................................................................4 Microsoft Windows Server 2008 ...............................................................................................................................................................4 nCipher Hardware Security Modules ......................................................................................................................................................4 Best.Practice.Security.–.nCipher.HSMs.with.Windows.Server.2008.PKI................................................................................5 Overview...............................................................................................................................................................................................................5 -

Patch Management Vendor and Application List
Patch Management Vendor and Application List Vendor Application 7-Zip 7-Zip 7-Zip 3 7-Zip 7-Zip 4 7-Zip 7-Zip 9 7-Zip 7-Zip 15 7-Zip 7-Zip 16 7-Zip 7-Zip 18 Acro Software Acro Software CutePDF Writer 2 Acro Software CutePDF Writer 3 Adobe Adobe Acrobat 5 Adobe Acrobat 6 Adobe Acrobat 7 Adobe Acrobat 8 Adobe Acrobat 9 Adobe Acrobat X Adobe Acrobat XI Adobe Acrobat DC Adobe Acrobat DC 17 Adobe Acrobat DC 18 Adobe Acrobat DC 19 Adobe Adobe Photoshop 11 Adobe Adobe Photoshop 12 Adobe Adobe Photoshop 13 Adobe Adobe Photoshop 15 Adobe Adobe Photoshop 16 Adobe After Effects 13.5 Adobe AIR Adobe AIR 2 Adobe AIR 3 Adobe AIR 4 Adobe AIR 13 Adobe AIR 14 Adobe AIR 15 Adobe AIR 16 Adobe AIR 17 Adobe AIR 18 Adobe AIR 19 Adobe AIR 20 Adobe AIR 21 Adobe AIR 22 Adobe AIR 23 Adobe AIR 24 Adobe AIR 25 Adobe AIR 26 Adobe AIR 27 Adobe AIR 28 Adobe AIR 30 Adobe AIR 31 Adobe AIR 32 Adobe Bridge 4 Adobe Bridge 5 Adobe Bridge CC Adobe Creative Cloud 3 Adobe Creative Cloud 4 Adobe Digital Editions 1 Adobe Digital Editions 2 Adobe Digital Editions 3 Adobe Digital Editions 4 Adobe Distiller 5 Adobe Distiller 6 Adobe Distiller 7 Adobe Dreamweaver 16 Adobe Elements 5 Adobe Elements 6 Adobe Elements 7 Adobe Fireworks CS6 Adobe Flash PPAPI MSI Adobe Flash Plugin MSI Adobe Flash MSI Adobe Flash Plugin Adobe Flash 5 Adobe Flash 6 Adobe Flash Plugin 6 Adobe Flash 7 Adobe Flash Plugin 7 Adobe Flash 8 Adobe Flash Plugin 8 Adobe Flash 9 Adobe Flash Plugin 9 Adobe Flash 10 Adobe Flash Plugin 10 Adobe Flash 11 Adobe Flash Plugin 11 Adobe Flash 12 Adobe Flash Plugin 12 Adobe -

Mcafee Exploit Prevention Content 11535 Release Notes | 2021-06-15
McAfee Exploit Prevention Content 11535 Release Notes | 2021-06-15 Content package version for – McAfee Endpoint Security Exploit Prevention: 10.6.0.115351 McAfee Host Intrusion Prevention: 8.0.0.115352 1 - Applicable on all versions of McAfee Endpoint Security Exploit Prevention including version 10.7.x 2 - Applicable on all versions of McAfee Host Intrusion Prevention content including Host IPS 8.0 Patch 16. IMPORTANT: McAfee V3 Virus Definition Updates (DATs) version 3786 or above is a mandatory prerequisite for this Exploit prevention content update on McAfee Endpoint Security versions 10.5.x and 10.6.x only. Refer to the below KB for more information: https://kc.mcafee.com/corporate/index?page=content&id=KB91867 IMPORTANT: Either of the below McAfee Host IPS 8.0 Extension packages is a mandatory prerequisite for receiving the new security or policy updates for this content 1. Host IPS 8.0 Patch 15 Extension (build 8.0.0.1334) – Applicable for Host IPS 8.0 Patch 15 and below 2. Host IPS 8.0 Patch 14 Extension Hotfix 114831 (build 8.0.0.1326) – Applicable for Host IPS 8.0 Patch 14 and below Refer to the below KB for more information: https://kc.mcafee.com/corporate/index?page=content&id=KB92596 Minimum Supported New Windows Signatures Product version Host Intrusion Endpoint Security Prevention Exploit Prevention Signature 6204: HTTP Protocol Stack Remote Code Execution Vulnerability 8.0.0 10.6.0 (Patch 13) Description: - HTTP.sys is a web server for ASP.NET Core that only runs on Windows independently or in conjunction with IIS. -

Mathematical Sciences Meetings and Conferences Section
page 1349 Calendar of AMS Meetings and Conferences Thla calandar lists all meetings which have been approved prior to Mathematical Society in the issue corresponding to that of the Notices the date this issue of Notices was sent to the press. The summer which contains the program of the meeting, insofar as is possible. and annual meetings are joint meetings of the Mathematical Associ Abstracts should be submitted on special forms which are available in ation of America and the American Mathematical Society. The meet many departments of mathematics and from the headquarters office ing dates which fall rather far in the future are subject to change; this of the Society. Abstracts of papers to be presented at the meeting is particularly true of meetings to which no numbers have been as must be received at the headquarters of the Society in Providence, signed. Programs of the meetings will appear in the issues indicated Rhode Island, on or before the deadline given below for the meet below. First and supplementary announcements of the meetings will ing. Note that the deadline for abstracts for consideration for pre have appeared in earlier issues. sentation at special sessions is usually three weeks earlier than that Abatracta of papara presented at a meeting of the Society are pub specified below. For additional information, consult the meeting an lished in the journal Abstracts of papers presented to the American nouncements and the list of organizers of special sessions. Meetings Abstract Program Meeting# Date Place Deadline Issue -

Client WAP Stack Activex Component
Winwap Technologies Oy Client WAP Stack ActiveX component Application Programming Interface WAP stack version 2.6 WAP specification version: 2.0 Document dated: 06-Jan-2006 WAP Stack ActiveX http://www.winwap.com Notice of Confidentiality This document contains proprietary and confidential information that belongs to Winwap Technolo- gies Oy. The recipient agrees to maintain this information in confidence and to not reproduce or otherwise disclose this information to any person outside of the group directly responsible for the evaluation of the content. Revision history Date Author Description 06-Jan-2006 S Markelov Initial version of the WAP Stack ActiveX API specification. Preamble The reader of this document should be familiar with all or some of the following in order to fully understand and evaluate the information in this document: • Basic knowledge in programming techniques. • Basic understanding of networking connections and client/server architecture where user- agents retrieve and render information (e.g. Internet browsers and servers with services). • The interaction between a WAP user-agent, a WAP Gateway and a WEB Server. • Basic knowledge in ActiveX technique. c Winwap Technologies Oy 1 WAP Stack ActiveX http://www.winwap.com Contents 1 Normative references2 2 Getting started3 2.1 What is the WAP Stack ActiveX?...........................3 2.2 System requirements..................................4 2.3 Installation.......................................5 2.4 Simple program for Microsoft Visual Basic 6.0....................6 2.5 Simple program for Microsoft Visual C++ 6.0....................8 2.6 Simple program for Microsoft .NET/C#....................... 12 2.7 Simple program for Borland Delphi 7.0........................ 14 3 API specification 16 3.1 Declarations..................................... -
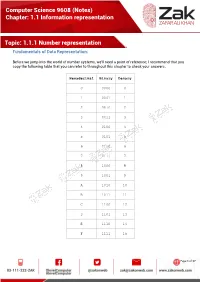
(Notes) Chapter: 1.1 Information Representation Topic
Computer Science 9608 (Notes) Chapter: 1.1 Information representation Topic: 1.1.1 Number representation Fundamentals of Data Representation: Before we jump into the world of number systems, we'll need a point of reference; I recommend that you copy the following table that you can refer to throughout this chapter to check your answers. Hexadecimal Binary Denary 0 0000 0 1 0001 1 2 0010 2 3 0011 3 4 0100 4 5 0101 5 6 0110 6 7 0111 7 8 1000 8 9 1001 9 A 1010 10 B 1011 11 C 1100 12 D 1101 13 E 1110 14 F 1111 15 Page 1 of 17 Computer Science 9608 (Notes) Chapter: 1.1 Information representation Topic: 1.1.1 Number representation Denary/Decimal Denary is the number system that you have most probably grown up with. It is also another way of saying base 10. This means that there are 10 different numbers that you can use for each digit, namely: 0,1,2,3,4,5,6,7,8,9 Notice that if we wish to say 'ten', we use two of the numbers from the above digits, 1 and 0. Thousands Hundreds Tens Units 10^3 10^2 10^1 10^0 1000 100 10 1 5 9 7 3 Using the above table we can see that each column has a different value assigned to it. And if we know the column values we can know the number, this will be very useful when we start looking at other base systems. Obviously, the number above is: five-thousands, nine-hundreds, seven-tens and three-units. -

Attacks & Solutions Royal Holloway
Enhancing End User Security | Attacks & Solutions Adil M. Alsaid Technical Report RHUL{MA{2007{1 2 February 2007 Royal Holloway University of London Department of Mathematics Royal Holloway, University of London Egham, Surrey TW20 0EX, England http://www.rhul.ac.uk/mathematics/techreports Enhancing End User Security | Attacks & Solutions Adil M. Alsaid Thesis submitted to the University of London for the degree of Doctor of Philosophy Information Security Group Department of Mathematics Royal Holloway, University of London 2006 To my wife, Samira 2 Declaration These doctoral studies were conducted under the supervision of Professor Chris Mitchell and Professor Peter Wild. The work presented in this thesis is the result of original research carried out by myself, in collaboration with others, whilst enrolled in the Depart- ment of Mathematics as a candidate for the degree of Doctor of Philosophy. This work has not been submitted for any other degree or award in any other university or educational establishment. Adil Alsaid July 2006 3 Acknowledgements I would like to thank my supervisor Professor Chris J. Mitchell for his invaluable support, interest, patience and guidance throughout my studies at Royal Holloway. His style of supervision along with his important com- ments and suggestions for improvements have encouraged me to pursue my ideas. Special thanks to my advisor Peter Wild for his support. I give special recognition to my wife Samira, for her understanding, endless support and encouragement over the last few years. I would like to thank my children Faisal, Fay, Mohammed, and Saud for being patient while I was doing my research. -

Standard Vorlage
SIE MACHEN IHREN JOB. WIR MACHEN IHRE IT. Vom CLPA-Agent unterstützte „Non Microsoft“ Applikationen: Vendor Product ActiveState Software Inc. ActivePython AOE media FileZilla Client Apache OpenOffice OpenOffice.org Apache Group Apache Web Server ** Apple Incorporated Apple QuickTime Apple iTunes Apple Safari Adobe Systems Incorporated Adobe Acrobat Adobe Acrobat DC Adobe Acrobat DC-Classic Adobe Air Adobe Flash Player Adobe Illustrator Adobe InDesign Adobe PhotoShop Adobe Reader Adobe Reader DC Adobe Reader DC-Classic Adobe Shockwave Player AudacityTeam.org Audacity Bandisoft.com Bandizip Box BoxSync Bullzip.com COMPUTERS & LESSONS GmbH Geschäftsführer: Stefan Körbel Tel.: 06021 8483-0 Magnolienweg 12 Handelsregister Aschaffenburg HRB 5334 Fax: 06021 8483-19 63741 Aschaffenburg USt-IDNr.: DE 1604 189 65 www.comless.de [email protected] Seite 1 von 12 SIE MACHEN IHREN JOB. WIR MACHEN IHRE IT. Bullzip PDF Printer Canneverbe Limited CDBurnerXP Citrix Systems Inc. GoToMeeting Core FTP Core FTP Don Ho Notepad++ dotPDN LLC Paint.NET Evernote Corporation Evernote Foxit Corporation Foxit PhantomPDF Foxit Reader Fyodor Nmap Google Google Chrome * Google Drive Google Earth Google Picasa ideaMK STP Viewer gor Pavlov 7-Zip Irfan Skiljan IrfanView JAM Software TreeSize Free Lightning UK COMPUTERS & LESSONS GmbH Geschäftsführer: Stefan Körbel Tel.: 06021 8483-0 Magnolienweg 12 Handelsregister Aschaffenburg HRB 5334 Fax: 06021 8483-19 63741 Aschaffenburg USt-IDNr.: DE 1604 189 65 www.comless.de [email protected] Seite 2 von 12 SIE MACHEN IHREN JOB. WIR