ஜ Idm Crack Tehparadox ஜ Скачать
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

HTTP Cookie - Wikipedia, the Free Encyclopedia 14/05/2014
HTTP cookie - Wikipedia, the free encyclopedia 14/05/2014 Create account Log in Article Talk Read Edit View history Search HTTP cookie From Wikipedia, the free encyclopedia Navigation A cookie, also known as an HTTP cookie, web cookie, or browser HTTP Main page cookie, is a small piece of data sent from a website and stored in a Persistence · Compression · HTTPS · Contents user's web browser while the user is browsing that website. Every time Request methods Featured content the user loads the website, the browser sends the cookie back to the OPTIONS · GET · HEAD · POST · PUT · Current events server to notify the website of the user's previous activity.[1] Cookies DELETE · TRACE · CONNECT · PATCH · Random article Donate to Wikipedia were designed to be a reliable mechanism for websites to remember Header fields Wikimedia Shop stateful information (such as items in a shopping cart) or to record the Cookie · ETag · Location · HTTP referer · DNT user's browsing activity (including clicking particular buttons, logging in, · X-Forwarded-For · Interaction or recording which pages were visited by the user as far back as months Status codes or years ago). 301 Moved Permanently · 302 Found · Help 303 See Other · 403 Forbidden · About Wikipedia Although cookies cannot carry viruses, and cannot install malware on 404 Not Found · [2] Community portal the host computer, tracking cookies and especially third-party v · t · e · Recent changes tracking cookies are commonly used as ways to compile long-term Contact page records of individuals' browsing histories—a potential privacy concern that prompted European[3] and U.S. -

Discontinued Browsers List
Discontinued Browsers List Look back into history at the fallen windows of yesteryear. Welcome to the dead pool. We include both officially discontinued, as well as those that have not updated. If you are interested in browsers that still work, try our big browser list. All links open in new windows. 1. Abaco (discontinued) http://lab-fgb.com/abaco 2. Acoo (last updated 2009) http://www.acoobrowser.com 3. Amaya (discontinued 2013) https://www.w3.org/Amaya 4. AOL Explorer (discontinued 2006) https://www.aol.com 5. AMosaic (discontinued in 2006) No website 6. Arachne (last updated 2013) http://www.glennmcc.org 7. Arena (discontinued in 1998) https://www.w3.org/Arena 8. Ariadna (discontinued in 1998) http://www.ariadna.ru 9. Arora (discontinued in 2011) https://github.com/Arora/arora 10. AWeb (last updated 2001) http://www.amitrix.com/aweb.html 11. Baidu (discontinued 2019) https://liulanqi.baidu.com 12. Beamrise (last updated 2014) http://www.sien.com 13. Beonex Communicator (discontinued in 2004) https://www.beonex.com 14. BlackHawk (last updated 2015) http://www.netgate.sk/blackhawk 15. Bolt (discontinued 2011) No website 16. Browse3d (last updated 2005) http://www.browse3d.com 17. Browzar (last updated 2013) http://www.browzar.com 18. Camino (discontinued in 2013) http://caminobrowser.org 19. Classilla (last updated 2014) https://www.floodgap.com/software/classilla 20. CometBird (discontinued 2015) http://www.cometbird.com 21. Conkeror (last updated 2016) http://conkeror.org 22. Crazy Browser (last updated 2013) No website 23. Deepnet Explorer (discontinued in 2006) http://www.deepnetexplorer.com 24. Enigma (last updated 2012) No website 25. -

What Are Kernel-Mode Rootkits?
www.it-ebooks.info Hacking Exposed™ Malware & Rootkits Reviews “Accessible but not dumbed-down, this latest addition to the Hacking Exposed series is a stellar example of why this series remains one of the best-selling security franchises out there. System administrators and Average Joe computer users alike need to come to grips with the sophistication and stealth of modern malware, and this book calmly and clearly explains the threat.” —Brian Krebs, Reporter for The Washington Post and author of the Security Fix Blog “A harrowing guide to where the bad guys hide, and how you can find them.” —Dan Kaminsky, Director of Penetration Testing, IOActive, Inc. “The authors tackle malware, a deep and diverse issue in computer security, with common terms and relevant examples. Malware is a cold deadly tool in hacking; the authors address it openly, showing its capabilities with direct technical insight. The result is a good read that moves quickly, filling in the gaps even for the knowledgeable reader.” —Christopher Jordan, VP, Threat Intelligence, McAfee; Principal Investigator to DHS Botnet Research “Remember the end-of-semester review sessions where the instructor would go over everything from the whole term in just enough detail so you would understand all the key points, but also leave you with enough references to dig deeper where you wanted? Hacking Exposed Malware & Rootkits resembles this! A top-notch reference for novices and security professionals alike, this book provides just enough detail to explain the topics being presented, but not too much to dissuade those new to security.” —LTC Ron Dodge, U.S. -

Web Design.” I Found Books on Everything from HTML to XML and from Web Graphics to Web Usability
Free ebooks ==> www.ebook777.com Free ebooks ==> www.ebook777.com Web Design: A Beginner’s Guide Second Edition www.ebook777.com Free ebooks ==> www.ebook777.com About the Author Wendy Willard is a designer, consultant, writer, and educator who has been involved in web design for about 15 years. She is the author of HTML: A Beginner’s Guide, Fourth Edition, and other books. Wendy is a graduate of Art Center College of Design in Pasadena, California. About the Technical Editor Kathi McCracken-Dente is a user experience strategist with an expertise in designing for e-commerce, communities, and web applications. Before starting McCracken Design, a web design agency in Oakland, California, she was a designer at frog design, Addwater, and Intuit. Her clients include Yahoo!, Intuit, PowerReviews, and LeapFrog. She is a graduate of Duke University and Art Center College of Design. Free ebooks ==> www.ebook777.com Web Design: A Beginner’s Guide Second Edition Wendy Willard New York Chicago San Francisco Lisbon London Madrid Mexico City Milan New Delhi San Juan Seoul Singapore Sydney Toronto Free ebooks ==> www.ebook777.com Copyright © 2010 by The McGraw-Hill Companies. All rights reserved. Except as permitted under the United States Copyright Act of 1976, no part of this publication may be reproduced or distributed in any form or by any means, or stored in a database or retrieval system, without the prior written permission of the publisher. ISBN: 978-0-07-170135-8 MHID: 0-07-170135-4 The material in this eBook also appears in the print version of this title: ISBN: 978-0-07-170134-1, MHID: 0-07-170134-6. -
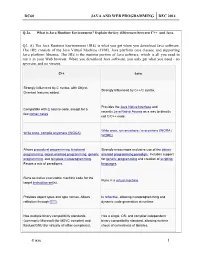
Dc60 Java and Web Programming Dec 2014
DC60 JAVA AND WEB PROGRAMMING DEC 2014 Q.2 a. What is Java Runtime Environment? Explain the key differences between C++ and Java. Q2. A) The Java Runtime Environment (JRE) is what you get when you download Java software. The JRE consists of the Java Virtual Machine (JVM), Java platform core classes, and supporting Java platform libraries. The JRE is the runtime portion of Java software, which is all you need to run it in your Web browser. When you download Java software, you only get what you need - no spyware, and no viruses. C++ Java Strongly influenced by C syntax, with Object- Strongly influenced by C++/C syntax. Oriented features added. Provides the Java Native Interface and Compatible with C source code, except for a recently Java Native Access as a way to directly few corner cases. call C/C++ code. Write once, run anywhere / everywhere (WORA / Write once, compile anywhere (WOCA). WORE). Allows procedural programming, functional Strongly encourages exclusive use of the object- programming, object-oriented programming, generic oriented programming paradigm. Includes support programming, and template metaprogramming. for generic programming and creation of scripting Favors a mix of paradigms. languages. Runs as native executable machine code for the Runs in a virtual machine. target instruction set(s). Provides object types and type names. Allows Is reflective, allowing metaprogramming and reflection through RTTI. dynamic code generation at runtime. Has multiple binary compatibility standards Has a single, OS- and compiler-independent (commonly Microsoft (for MSVC compiler) and binary compatibility standard, allowing runtime Itanium/GNU (for virtually all other compilers)). check of correctness of libraries. -

A Reference Architecture for Web Browsers
A Reference Architecture for Web Browsers Alan Grosskurth and Michael W. Godfrey School of Computer Science University of Waterloo Waterloo, ON N2L 3G1 Canada {agrossku,migod}@uwaterloo.ca Abstract The web browser is perhaps the most widely used soft- ware application in history and has evolved significantly A reference architecture for a domain captures the fun- over the past fifteen years; today, users run web browsers damental subsystems common to systems of that domain as on diverse types of hardware, from cell phones and tablet well as the relationships between these subsystems. Hav- PCs to regular desktop computers. A reference architec- ing a reference architecture available can aid both during ture for web browsers can help implementors to understand maintenance and at design time: it can improve under- trade-offs when designing new systems, and can also assist standing of a given system, it can aid in analyzing trade- maintainers in understanding legacy code. offs between different design options, and it can serve as In this paper, we present a reference architecture for a template for designing new systems and re-engineering web browsers that has been derived from the source code existing ones. In this paper, we examine the history of the of two existing open source systems and validate our find- web browser domain and identify several underlying phe- ings against two additional systems. We explain how the nomena that have contributed to its evolution. We develop evolutionary history of the web browser domain has influ- a reference architecture for web browsers based on two enced this reference architecture, and we identify underly- well known open source implementations, and we validate ing phenomena that can help to explain current trends. -

HTML: a Beginner’S Guide
HTML: A Beginner’s Guide Fourth Edition About the Author Wendy Willard is a freelance consultant offering design and art direction services to clients. She also teaches and writes on these topics, and is the author of several other books including Web Design: A Beginner’s Guide (also published by McGraw-Hill). She holds a degree in Illustration from Art Center College of Design in Pasadena, California, where she first learned HTML in 1995. Wendy enjoys all aspects of digital design, reading, cooking, and anything related to the Web. She lives and works in Maryland with her husband, Wyeth, and their two daughters. About the Technical Editor Todd Meister has been developing and using Microsoft technologies for over ten years. He’s been a technical editor on over 50 titles ranging from SQL Server to the .NET Framework. Besides serving as a technical editor for titles, he is an assistant director for Computing Services at Ball State University in Muncie, Indiana. He lives in central Indiana with his wife, Kimberly, and their four remarkable children. HTML: A Beginner’s Guide Fourth Edition Wendy Willard New York Chicago San Francisco Lisbon London Madrid Mexico City Milan New Delhi San Juan Seoul Singapore Sydney Toronto Copyright © 2009 by The McGraw-Hill Companies. All rights reserved. Except as permitted under the United States Copyright Act of 1976, no part of this publication may be reproduced or distributed in any form or by any means, or stored in a database or retrieval system, without the prior written permission of the publisher. ISBN: 978-0-07-161144-2 MHID: 0-07-161144-4 The material in this eBook also appears in the print version of this title: ISBN: 978-0-07-161143-5, MHID: 0-07-161143-6. -

Shake the Microsoft Habit Column by Jim Justen
Shake the Microsoft Habit Column By Jim Justen icrosoft Internet Explorer (IE) is MOZILLA designers their artistic vision. Still, there are the Web browser of choice for well times when you simply cannot view a page if Mover 90%1 of desktop computer Netscape has many virtues and is an obvi- using Opera as your browser. users, and chances are, it’s on your computer as ous alternative browser with many fans. Alas, The other shortcoming of Opera is the $39 well. But is it truly chosen, or is it simply there Netscape as a commercial product has largely price tag. It’s a tough sell when so many as a result of ubiquity and Microsoft’s marketing ‘lost the war’.2 Nevertheless, Netscape’s tech- browsers are free, as Microsoft has correctly practices? I’ll leave that for the courts to decide. nology lives on in the parallel open-source surmised. But for heavy Web users, it may be Still, it is pre-installed on most windows PCs, browser “Mozilla.” A large, dedicated group worth the price. Opera may be had for free if and many non-technical users are literally of volunteer programmers soldier on with the you are willing to accept an unobtrusive ad- unaware of available alternatives. Even profes- free, open-source browser, adding features far banner display. sionals use it simply because, as climber George beyond those of any commercial product. Returning to the positives, Opera has excellent Mallory said of Mount Everest, “It’s there.” Mozilla is a complete suite of Internet utili- cookie and privacy control, terrific multi-language Is Microsoft’s browser the superior product? ties; mail, chat and a page editor are among its support and good Web kiosk and lockdown Although the current version of Internet Explorer elements. -

Linkman PDF Manual
Outertech Linkman Linkman is a bookmark management solution which supports 10 different browsers and integrates with Firefox, Internet Explorer and Maxthon. Linkman calls upon many powerful features that replace the browser's native URL management and allow to browse faster and more efficiently. To give you a better impression a Linkman tutorial video can be watched at http://linkmanvideo.outertech.com You can choose between two editions. Linkman Lite (Freeware) http://linkmanlite.outertech.com Linkman Lite is free for private non-commercial use as well as for use in charity organizations and educational use. Private use is only when used by individuals at home on their private PC. Educational use is by students for education in school or university. Linkman Pro ($25 | EUR19 for single computer license) http://linkmanpro.outertech.com This edition is intended for the professional user. Linkman Pro contains all features of Linkman Lite. In addition these abilities are included: * Synchronize links between two (or more) computers * Ability to check URLs for dead links, intelligent (only major) content changes, and page movements * Add all links on a single webpage * Improved keyword features (e.g. Keyword List) * Replace feature * Improved Database backup * Retrieve URL meta tags * Editable Export Templates (XML, TSV...) with UTF8 support * Optional installation on USB sticks for mobile usage Linkman 3 Table of Content Foreword 0 Part I Introduction 7 1 .O...v..e...r.v..i.e...w.............................................................................................................................. 7 2 .W...h...a..t.'.s.. .n..e..w............................................................................................................................ 9 3 ...O...t.h..e...r. .s..o..f..t.w...a..r.e................................................................................................................... 21 Part II Frequently Asked Questions 23 Part III Tutorial 27 1 ...F..i.r..s..t. -

(12) United States Patent (10) Patent No.: US 7,574.433 B2 Engel (45) Date of Patent: Aug
US007574.433B2 (12) United States Patent (10) Patent No.: US 7,574.433 B2 Engel (45) Date of Patent: Aug. 11, 2009 (54) CLASSIFICATION-EXPANDED INDEXING 6,598,046 B1* 7/2003 Goldberg et al. ............... 707/5 AND RETRIEVAL OF CLASSIFIED 6,625,596 B1 9/2003 Nunez ........................... 707/3 DOCUMENTS 6,711,585 B1* 3/2004 Copperman et al. ...... TO7 104.1 6,778,979 B2 * 8/2004 Grefenstette et al. ........... 707/3 (75)75 Inventor: Alan Kent Engel, Villanova, PA (US) 6,928,4256,820,075 B2 * 1 8/20051/2004 GrefenstetteShanahan et al.et al............... ........... 707/2707/3 7,031,961 B2 * 4/2006 Pitkow et al. .................. 7O7/4 (73) Assignee: Paterra, Inc., Kerrville, TX (US) 7, 177,904 B1* 2/2007 Mathur et al. ............... TO9.204 2002/0147738 A1 10, 2002 Read (*) Notice: Subject to any disclaimer, the term of this 2003,0229626 A1 12/2003 s patent is extended or adjusted under 35 2004/01770.15 A1 9, 2004 Galai et al. U.S.C. 154(b) by 566 days. FOREIGN PATENT DOCUMENTS (21) Appl. No.: 10/960,725 JP 2003-345950 A 12/2003 (22) Filed: Oct. 8, 2004 * cited by examiner (65) Prior Publication Data Primary Examiner Shahid A. Alam (74) Attorney, Agent, or Firm Gianna Julian-Arnold; Miles US 2006/0242118A1 Oct. 26, 2006 & Stockbridge P.C. (51) Int. Cl. 57 ABSTRACT G06F 7/30 (2006.01) (57) (52) U.S. Cl. ................. 707/4; 707/3; 707/5; 707/104.1 Document classification systems are valuable tools for (58) Field of Classification Search .................... -
SCAN 31 the PROJECT HONEYNET Dophine V. Britanico
SCAN 31 THE PROJECT HONEYNET http://www.honeynet.org Dophine V. Britanico INFOSEC Technical Document April 28,2004 :. CopyLeft (c) 2004 Dophine Britanico :. [email protected] Acknowledgment This work was prepared in response to Project Honeynet Challenge 31. The findings, tools and observation discuss in this paper is published for the general interest of the Computer Security Community and It was intended for highly technical audience, Some information maybe incorrect, out-dated, obscured, and all false. Typographical errors are all mine. No pixels were damage during the documentation and preparation of this technical document. TO GOD AND TO MY LOVING DAUGTHERS. Challenge Overview This month's challenge is to analyze web server log files looking for signs of abuse. The Honeypots: Monitoring and Forensics Project deployed a specially configured Apache web server, designed specifically for use as a honeypot open proxy server or ProxyPot. Questions 1. How do you think the attackers found the honeyproxy? It was quite probable that it was discovered by a proxy hunter. 2. What different types of attacks can you identify? This where attacks that’s generated most noise on the audit_log and catch my attention. 2.1 Probing of exploitable server using Automated scanner like Nessus looking for holes like IIS Unicode Directory Traversal exploit, It was also possible that the attacker used Proxy scanner, and Open SSL scanner. 2.2 Scan Open E-Mail relay gateway, probably to be used later by the attacker to spoof e-mail or to be utilized in SPAM. 2.3 Brute force login name and password of sites such as yahoo.com, icq.com, microsoft, mail.sina.com and etc. -

Slobodan Softver (Open Source Software)
Slobodan softver Slobodan softver (en. free (Open Source Software) software), je softver koji se može koristiti, kopirati, mjenjati Lista besplatnog softvera i redistribuirati bez ikakvih restrikcija. 3D Graphics SpyBot Search & Destroy - http://spybot.safer- Sloboda od 3Delight Free - http://www.3delight.com/index.htm networking.de/ restrikcija je Anim8or - http://www.anim8or.com/ centralni koncept, SpywareBlaster - http:// a suprotno je od Blender - http://www.blender3d.org/ www.javacoolsoftware.com/spywareblaster.html slobodnog Now3D - http://digilander.libero.it/giulios/Eng/ softvera koji je WinPatrol - http://www.winpatrol.com/ vlasnički softver homepage.htm (ne odnosi se na OpenFX - http://www.openfx.org Anti-Virus razliku da li softver košta ili POV-Ray - http://www.povray.org/ AntiVir - http://www.free-av.com/ ne). Uobičajni Terragen - http://www.planetside.co.uk/terragen/ Avast - http://www.avast.com/i_idt_1018.html način distribucije softvera kao Toxic - http://www.toxicengine.org/ AVG - http://free.grisoft.com/ slobodnog je za Wings 3D - http://www.wings3d.com/ BitDefender - http://www.bitdefender.com softver koji je licenciran pod ClamWin - http://www.clamwin.com/ slobodnom Anti-spam programs CyberHawk - http://www.novatix.com/cyberhawk/ licencom (ili kao K9 - http://www.keir.net/k9.html javno vlasništvo), Beta te da je izvorni MailWasher- http://www.mailwasher.net/ kod javno POPFile - http://popfile.sourceforge.net/ Audio Players dostupan. SpamBayes - http://spambayes.sourceforge.net/ Billy - http://www.sheepfriends.com/?page=billy