Copyrighted Material
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

1 Dynamisches Tool Zur (Grafischen) Datenanalyse
Statistik-Software Kommerzielle Software Freeware S-Plus www.insightful.com/products/splus/ R www.r-project.org/ SPSS www.spss.com/ PSPP www.gnu.org/software/pspp/pspp.html NCSS www.ncss.com/ Matlab www.mathworks.de/ Octave, Scilab www.scilab.org/ Eviews www.eviews.com PD Dr. Matthias Fischer Ox www.oxmetrics.net/ SAS www.sas.com/ [email protected] STATA www.stata.com/ LIMDEP www.limdep.com/ JMultiwww.jmulti.de/ Version 2.0 Matthias Fischer () Einf¨uhrung in R Version 2.0 1 / 95 Matthias Fischer () Einf¨uhrung in R Version 2.0 2 / 95 Warum R? R-Homepage http://www.r-project.org/ 1 Dynamisches Tool zur (grafischen) Datenanalyse 2 Taschenrechnerfunktion 3 Programmiersprache 4 Freeware-Version von S-PLUS 5 Alternative zu MATLAB, GAUSS, OX, etc. 6 Erg¨anzung zu Excel oder SPSS Download, Dokumentation, Newsgroups Matthias Fischer () Einf¨uhrung in R Version 2.0 3 / 95 Matthias Fischer () Einf¨uhrung in R Version 2.0 4 / 95 R-Installation 1/4 Start der Datei R-2.2.1-win32.exe Installation Matthias Fischer () Einf¨uhrung in R Version 2.0 5 / 95 Matthias Fischer () Einf¨uhrung in R Version 2.0 6 / 95 R-Installation 2/4 R-Installation 3/4 Matthias Fischer () Einf¨uhrung in R Version 2.0 7 / 95 Matthias Fischer () Einf¨uhrung in R Version 2.0 8 / 95 R-Installation 4/4 Literatur Matthias Fischer () Einf¨uhrung in R Version 2.0 9 / 95 Matthias Fischer () Einf¨uhrung in R Version 2.0 10 / 95 R-B¨ucher R-B¨ucher Everitt Behr An R and S-Plus Companion to Multivariate Analysis. -

Applied Econometrics Using MATLAB
Applied Econometrics using MATLAB James P. LeSage Department of Economics University of Toledo CIRCULATED FOR REVIEW October, 1998 2 Preface This text describes a set of MATLAB functions that implement a host of econometric estimation methods. Toolboxes are the name given by the MathWorks to related sets of MATLAB functions aimed at solving a par- ticular class of problems. Toolboxes of functions useful in signal processing, optimization, statistics, nance and a host of other areas are available from the MathWorks as add-ons to the standard MATLAB software distribution. I use the termEconometrics Toolbox to refer to the collection of function libraries described in this book. The intended audience is faculty and students using statistical methods, whether they are engaged in econometric analysis or more general regression modeling. The MATLAB functions described in this book have been used in my own research as well as teaching both undergraduate and graduate econometrics courses. Researchers currently using Gauss, RATS, TSP, or SAS/IML for econometric programming might nd switching to MATLAB advantageous. MATLAB software has always had excellent numerical algo- rithms, and has recently been extended to include: sparse matrix algorithms, very good graphical capabilities, and a complete set of object oriented and graphical user-interface programming tools. MATLAB software is available on a wide variety of computing platforms including mainframe, Intel, Apple, and Linux or Unix workstations. When contemplating a change in software, there is always the initial investment in developing a set of basic routines and functions to support econometric analysis. It is my hope that the routines in the Econometrics Toolbox provide a relatively complete set of basic econometric analysis tools. -
Rice Research Versus Rice Imports in Malaysia: a Dynamic Spatial Equilibrium Model
COPYRIGHT AND USE OF THIS THESIS This thesis must be used in accordance with the provisions of the Copyright Act 1968. Reproduction of material protected by copyright may be an infringement of copyright and copyright owners may be entitled to take legal action against persons who infringe their copyright. Section 51 (2) of the Copyright Act permits an authorized officer of a university library or archives to provide a copy (by communication or otherwise) of an unpublished thesis kept in the library or archives, to a person who satisfies the authorized officer that he or she requires the reproduction for the purposes of research or study. The Copyright Act grants the creator of a work a number of moral rights, specifically the right of attribution, the right against false attribution and the right of integrity. You may infringe the author’s moral rights if you: - fail to acknowledge the author of this thesis if you quote sections from the work - attribute this thesis to another author - subject this thesis to derogatory treatment which may prejudice the author’s reputation For further information contact the University’s Director of Copyright Services sydney.edu.au/copyright RICE RESEARCH VERSUS RICE IMPORTS IN MALAYSIA: A DYNAMIC SPATIAL EQUILIBRIUM MODEL Deviga Vengedasalam A thesis submitted in fulfilment of the requirements for the degree of Doctor of Philosophy Department of Agricultural and Resource Economics Faculty of Agriculture and Environment The University of Sydney New South Wales Australia February 2013 STATEMENT OF ORIGINALITY I hereby certify that the substance of the material used in this study is my own research and has not been submitted or is not currently being submitted for any other degree. -

A Study on the Utilization of E-Resources Among College Students
International Journal of Knowledge Engineering, Vol. 6, No. 1, June 2020 A Study on the Utilization of e-Resources among College Students Rebilyn G. Roman, Charles Spencer P. Trobada, Ferginia P. Gaton, Catherine Kate Gania, Solomon Ayodele Oluyinka, Heidie O. Cuenco, and Richard G. Daenos libraries more convenient. Libraries need to prioritize and Abstract—E-resources are information resources that can be acquire materials that are relevant to the fields of study of the accessed through the use of electronic devices. With the fast user community and supplement these materials with development of technology, it is imperative that libraries also e-resources. adapt to the changing times. Libraries are now incorporating e-resources to their collection to accommodate the needs of their The management of information in university libraries has clients. Gale is an electronic database that houses e-books and greatly changed due to the advent of electronic information e-journals. This study examined the factors that affect the resources [6]. With the use of electronic resources, this made utilization of the Gale electronic resources among college it possible for researchers to gather and use the information students. Questionnaires were randomly distributed to a total of needed anytime thus getting updated with the current trends 201 3rd year and 4th year students. The factors identified, and developments of the field [7]. E-resources serve as a Awareness, Usefulness and Challenges were derived from related studies. The collected data were analyzed using solution to save space and regulate the flow of information in SmartPLS. The results showed that the aforementioned factors libraries [8], [9]. -

Agricultural Policy Analysis Project
AGRICULTURAL POLICY ANALYSIS PROJECT Science and Technology, Office of Agriculture Under contract to the Agency for International Development, Bureau for Project Office 4250 Connecticut Avenue, N.W. Washington, D.C 20008 * Telephone: (202) 362-2800 AGRICULTURAL POLICY ANALYSIS TOOLS FOR ECONOMIC DEVELOPMENT APAP MAIN DOCUMENT NO. 2 By: LUTHER G. TWEETEN, Editor, et. al. NOVEMBER, 1988 Submitted to: Dr. William Goodwin U.S. Agency ior International Development S&T/AGR, SA-18 Reor 403 Washington, D.C. 20523 Prime Contractor: At Associates Inc., 55 Wheeler Street. Cambridge. Massachusetts 02138 (617) 492-7100 Subcontractors: Robert R. Nathan Associates, Inc. 1301 Pennsylvania Avenue, NW.. Washington. DC 20004 (202) 393-2700 Abel, Daft & Earigy, 1339 Wisconsin Avenue. NW.. Washington. DC 20007 (202) 342-7620 Oklahoma State University, Department o Agricultural Economics. Stillwater. Oklahoma 74078 (405) 624-6157 AGENCY FOR INTERNATIONAL DEVELOPMENT PPC/CDIE/DI REPORT PROCESSING FORM ENTER INFOPMATION ONLY IF NOT INCLUDED ON COVER OR TITLE PAGE OF DOCUMENT 1. Proiect/Subproiect Number 2. Contract/Grant Number 3. Publication Date APAP/936-4084 DAN-4084-C-00-3087-00 November, 1988 4. Document Title/Translated Title Agricultural Policy Analysis Tools for Economic Development L 5. Author(s) I. Luther G. Tweeten editor, et. al. 3. 6 Contributing Organization(s) IAbt Associates, In., Cambridge, MA ;Robert R. Nathan Associates, Inc., Washington, D.C. Abel, Daft and Earley, Inc., Alexandria, VA A.W Z State ni iv ept. f A-r. nllcwntpr OK 7. a.maon. ort '". SSmberonsorin A I. l-.6 ice_ 393 PAP Main Docunt[ AD/ST/AGR/EPP 10. Abstract (optional - .50 word limit) "Tools" provides approaches to and techniques useful in analyzing very real world problems in agricultural policy analysis. -

Models De Dades Dels SIG a Internet. Aspectes Teòrics I Aplicats
Models de dades dels SIG a Internet. Aspectes teòrics i aplicats Internet GIS Data models. Theoretical and applied aspects Tesi Doctoral Doctorat en Geografia Facultat de Filosofia i Lletres Universitat Autònoma de Barcelona Doctorand: Joan Masó Pau Director: Dr. Xavier Pons Fernández Juny del 2012 La portada l’aquest document es basa en una composició RGB en color fals obtinguda amb 3 canals espectrals (Infraroig proper, infraroig mitjà i vermell) que provenen d’un mosaic d’escenes Landsat 7 preses l’agost de 2003 i que es pot obtenir del servidor SatCat. (www.opengis.uab.cat/wms/satcat). Per a realitzar la portada s’ha escollit una regió de Catalunya que no contingués mar ni zones fora de l’àmbit. Per a la contraportada (a l’esquerra) i per a la portada (a la dreta), la regió s’ha dividit en sengles parts La imatge té 20 m de costat de píxel i ha estat tallada en tessel∙les de 256x256 píxels amb els procediments de preparació de capes del MiraMon per accelerar el rendiment en proporcionar una capa en un servei conforme a l’estàndard WMTS. La tessel∙lació consta de 55x55 tessel∙les de les qual finalment es fa servir una matriu de 24x17, començant a la tessel∙la (12,12) i acabant a la tessel∙la (28,35). “You're being confused by irrelevant data. Ignore it.” Seven of Nine from: Survival Instinct (1999) Star Trek Voyager series “This was just a first step. In time you’ll take another. Small moves, Ellie. Small moves.” Ted Arroway from: Contact (1997) movie ÍNDEX/TABLE OF CONTENTS Índex general/Table of contents ÍNDEX/TABLE OF CONTENTS ........................................................................................... -

TMS320C6652 and TMS320C6654 Fixed and Floating-Point Digital Signal Processor Datasheet
Product Order Technical Tools & Support & Folder Now Documents Software Community TMS320C6652, TMS320C6654 SPRS841E –MARCH 2012–REVISED OCTOBER 2019 TMS320C6652 and TMS320C6654 Fixed and Floating-Point Digital Signal Processor 1 Device Overview 1.1 Features 1 • One TMS320C66x DSP Core Subsystem – 32-Bit DDR3 Interface (CorePac) – DDR3-1066 – C66x Fixed- and Floating-Point CPU Core: Up – 4GB of Addressable Memory Space to 850 MHz for C6654 and 600 MHz for C6652 – 16-Bit EMIF • Multicore Shared Memory Controller (MSMC) – Universal Parallel Port – Memory Protection Unit for DDR3_EMIF – Two Channels of 8 Bits or 16 Bits Each • Multicore Navigator – Supports SDR and DDR Transfers – 8192 Multipurpose Hardware Queues with – Two UART Interfaces Queue Manager – Two Multichannel Buffered Serial Ports – Packet-Based DMA for Zero-Overhead (McBSPs) Transfers – I2C Interface • Peripherals – 32 GPIO Pins – PCIe Gen2 (C6654 Only) – SPI Interface – Single Port Supporting 1 or 2 Lanes – Semaphore Module – Supports up to 5 GBaud Per Lane – Eight 64-Bit Timers – Gigabit Ethernet (GbE) Subsystem (C6654 – Two On-Chip PLLs Only) • Commercial Temperature: – One SGMII Port (C6654 Only) – 0°C to 85°C – Supports 10-, 100-, and 1000-Mbps • Extended Temperature: Operation – –40°C to 100°C 1.2 Applications • Power Protection Systems • Medical Imaging • Avionics and Defense • Other Embedded Systems • Currency Inspection and Machine Vision • Industrial Transportation Systems 1.3 Description The C6654 and C6652 are high performance fixed- and floating-point DSPs that are based on TI's KeyStone multicore architecture. Incorporating the new and innovative C66x DSP core, this device can run at a core speed of up to 850 MHz for C6654 and 600 MHz for C6652. -

Participating Addendum Contract #0000000000000000000028963
PARTICIPATING ADDENDUM CONTRACT #0000000000000000000028963 NASPO ValuePoint Software Value Added Reseller (SVAR) Administrated by the State of Arizona (hereinafter “Lead State”) MASTER AGREEMENT SHI International Corporation Master Agreement No: ADSPO16-130651 (hereinafter “Contractor”) And The State of Indiana acting by and through the Indiana State Police (“ISP”) (hereinafter “Participating State/Entity”) 1. Scope: This addendum covers the Software Value Added Reseller contract led by the State of Arizona for use by state agencies and other entities located in the Participating State authorized by that state’s statutes to utilize State contracts with the prior approval of the state’s chief procurement official. 2. Participation: Use of specific NASPO ValuePoint cooperative contracts by agencies, political subdivisions and other entities (including cooperatives) authorized by an individual state’s statutes to use State contracts are subject to the prior approval of the respective State Chief Procurement Official. Issues of interpretation and eligibility for participation are solely within the authority of the State Chief Procurement Official. 3. Participating State Modifications or Additions to Master Agreement: (These modifications or additions apply only to actions and relationships within the Participating Entity.) Participating State/Entity must check one of the boxes below. [__] No changes to the terms and conditions of the Master Agreement are required. [ X ] The following changes are modifying or supplementing the Master Agreement terms and conditions. Exhibit A, hereby attached and incorporated by reference, is the Supplement covering compliance with State laws. The Supplement is incorporated into and made a part of the Master Agreement Number ADSPO16-130651 (Exhibit B) and applies to all transactions under this Participating Addendum. -

A Study on Defect Reduction in IT Based on Six Sigma Patterns Prabhu Thangavelu1, Research Scholar, HITS University, Chennai, Tamil Nadu,India Dr M
The International journal of analytical and experimental modal analysis ISSN NO:0886-9367 A Study on Defect Reduction in IT based on Six Sigma Patterns Prabhu Thangavelu1, Research Scholar, HITS University, Chennai, Tamil Nadu,India Dr M. Rajeswari2, Associate Professor, HITS University, Chennai, TamilNadu, India ABSTRACT Anything done by human is error prone. Software is not an exception to that. If software development has its buzz, a bisection of the buzz is because of the fault reduction. As long as there is software, there also will be fault reduction with its own hype. Both are interrelated. But getting a bird view of the software won’t suffice when it comes to pointing faults and defects. It is a painstaking task to get a holistic view to reach the quality’s pinnacle. According to GOST R ISO 9000-2001, quality is "the degree, to which the inherent characteristics of the product meet the requirements," which may not be interpreted in the field of software development. Each software has its own goal with reaching the perfect stage of functional, operational and technicality. If the product works as per the requirement in the superlative degree of it performing the operations confined to the requirement, then it is said to have quality. Six Sigma is a strategy used for defect reduction. It is a statistics-based, process-focused, data-driven strategy and methodology, coupled with management concepts and lean tools, that aims to improve the quality of process outputs. Six Sigma seeks to identify the causes of failures and minimize variability in key industrial processes in areas, such as healthcare, manufacturing, and service. -
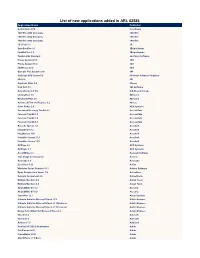
List of New Applications Added in ARL #2586
List of new applications added in ARL #2586 Application Name Publisher NetCmdlets 2016 /n software 1099 Pro 2009 Corporate 1099 Pro 1099 Pro 2020 Enterprise 1099 Pro 1099 Pro 2008 Corporate 1099 Pro 1E Client 5.1 1E SyncBackPro 9.1 2BrightSparks FindOnClick 2.5 2BrightSparks TaxAct 2002 Standard 2nd Story Software Phone System 15.5 3CX Phone System 16.0 3CX 3CXPhone 16.3 3CX Grouper Plus System 2021 3M CoDeSys OPC Server 3.1 3S-Smart Software Solutions 4D 15.0 4D Duplicate Killer 3.4 4Team Disk Drill 4.1 508 Software NotesHolder 2.3 Pro A!K Research Labs LibraryView 1.0 AB Sciex MetabolitePilot 2.0 AB Sciex Advanced Find and Replace 5.2 Abacre Color Picker 2.0 ACA Systems Password Recovery Toolkit 8.2 AccessData Forensic Toolkit 6.0 AccessData Forensic Toolkit 7.0 AccessData Forensic Toolkit 6.3 AccessData Barcode Xpress 7.0 AccuSoft ImageGear 17.2 AccuSoft ImagXpress 13.6 AccuSoft PrizmDoc Server 13.1 AccuSoft PrizmDoc Server 12.3 AccuSoft ACDSee 2.2 ACD Systems ACDSync 1.1 ACD Systems Ace Utilities 6.3 Acelogix Software True Image for Crucial 23. Acronis Acrosync 1.6 Acrosync Zen Client 5.10 Actian Windows Forms Controls 16.1 Actipro Software Opus Composition Server 7.0 ActiveDocs Network Component 4.6 ActiveXperts Multiple Monitors 8.3 Actual Tools Multiple Monitors 8.8 Actual Tools ACUCOBOL-GT 5.2 Acucorp ACUCOBOL-GT 8.0 Acucorp TransMac 12.1 Acute Systems Ultimate Suite for Microsoft Excel 13.2 Add-in Express Ultimate Suite for Microsoft Excel 21.1 Business Add-in Express Ultimate Suite for Microsoft Excel 21.1 Personal Add-in Express -
Troubleshooting Riverbed® Steelhead® WAN Optimizers Edwin Groothuis Public Document Public Document
Troubleshooting Riverbed® Steelhead® WAN Optimizers Edwin Groothuis Public Document Public Document Troubleshooting Riverbed® Steelhead® WAN Optimizers Edwin Groothuis Publication date Mon 19 May 2014 10:59:17 Copyright © 2011, 2012, 2013, 2014 Riverbed Technology, Inc Abstract General: All rights reserved. This book may be distributed outside Riverbed to Riverbed customers via the Riverbed Support website. Except for the foregoing, no part of this book may be further redistributed, reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying, recording, or by any information storage and retrieval system, without written permission from Riverbed Technology, Inc.. Warning and disclaimer: This book provides foundational information about the troubleshooting of the Riverbed WAN optimization im- plementation and appliances. Every effort has been made to make this book as complete and accurate as possible, but no warranty or fitness is implied. The information is provided on as "as is" basis. The author and Riverbed Technology shall have neither liability nor responsibility to any person or entity with respect to any loss or damages arising from the information contained in this book. The opinions expressed in this book belong to the author and are not necessarily those of Riverbed Technology. Riverbed and any Riverbed product or service name or logo used herein are trademarks of Riverbed Technology, Inc. All other trademarks used herein belong to their respetive owners. Feedback Information: If you have any comments regarding how the quality of this book could be improved, please contact the author. He can be reached via email at [email protected] or at [email protected], his personal website can be found at http://www.mavetju.org/. -
The Development of a Statistical Software Resource for Medical Research
The University of Manchester Research The development of a statistical software resource for medical research Link to publication record in Manchester Research Explorer Citation for published version (APA): Buchan, I. E. (2000). The development of a statistical software resource for medical research. University of Liverpool. Citing this paper Please note that where the full-text provided on Manchester Research Explorer is the Author Accepted Manuscript or Proof version this may differ from the final Published version. If citing, it is advised that you check and use the publisher's definitive version. General rights Copyright and moral rights for the publications made accessible in the Research Explorer are retained by the authors and/or other copyright owners and it is a condition of accessing publications that users recognise and abide by the legal requirements associated with these rights. Takedown policy If you believe that this document breaches copyright please refer to the University of Manchester’s Takedown Procedures [http://man.ac.uk/04Y6Bo] or contact [email protected] providing relevant details, so we can investigate your claim. Download date:04. Oct. 2021 The Development of a Statistical Computer Software Resource for Medical Research Thesis submitted in accordance with the requirements of the University of Liverpool For the degree of Doctor of Medicine By Iain Edward Buchan November 2000 Liverpool, England To my parents… PREFACE Preface Declaration This thesis is the result of my own work. The material contained in this thesis has not been presented, nor is currently being presented, either wholly or in part for any other degree or other qualification.