A Comprehensive Evaluation of Third-Party Cookie Policies
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

A Generic Data Exchange System for F2F Networks
The Retroshare project The GXS system Decentralize your app! A Generic Data Exchange System for F2F Networks Cyril Soler C.Soler The GXS System 03 Feb. 2018 1 / 19 The Retroshare project The GXS system Decentralize your app! Outline I Overview of Retroshare I The GXS system I Decentralize your app! C.Soler The GXS System 03 Feb. 2018 2 / 19 The Retroshare project The GXS system Decentralize your app! The Retroshare Project I Mesh computers using signed TLS over TCP/UDP/Tor/I2P; I anonymous end-to-end encrypted FT with swarming; I mail, IRC chat, forums, channels; I available on Mac OS, Linux, Windows, (+ Android). C.Soler The GXS System 03 Feb. 2018 3 / 19 The Retroshare project The GXS system Decentralize your app! The Retroshare Project I Mesh computers using signed TLS over TCP/UDP/Tor/I2P; I anonymous end-to-end encrypted FT with swarming; I mail, IRC chat, forums, channels; I available on Mac OS, Linux, Windows. C.Soler The GXS System 03 Feb. 2018 3 / 19 The Retroshare project The GXS system Decentralize your app! The Retroshare Project I Mesh computers using signed TLS over TCP/UDP/Tor/I2P; I anonymous end-to-end encrypted FT with swarming; I mail, IRC chat, forums, channels; I available on Mac OS, Linux, Windows. C.Soler The GXS System 03 Feb. 2018 3 / 19 The Retroshare project The GXS system Decentralize your app! The Retroshare Project I Mesh computers using signed TLS over TCP/UDP/Tor/I2P; I anonymous end-to-end encrypted FT with swarming; I mail, IRC chat, forums, channels; I available on Mac OS, Linux, Windows. -

Anonymous Rate Limiting with Direct Anonymous Attestation
Anonymous rate limiting with Direct Anonymous Attestation Alex Catarineu Philipp Claßen Cliqz GmbH, Munich Konark Modi Josep M. Pujol 25.09.18 Crypto and Privacy Village 2018 Data is essential to build services 25.09.18 Crypto and Privacy Village 2018 Problems with Data Collection IP UA Timestamp Message Payload Cookie Type 195.202.XX.XX FF.. 2018-07-09 QueryLog [face, facebook.com] Cookie=966347bfd 14:01 1e550 195.202.XX.XX Chrome.. 2018-07-09 Page https://analytics.twitter.com/user/konark Cookie=966347bfd 14:06 modi 1e55040434abe… 195.202.XX.XX Chrome.. 2018-07-09 QueryLog [face, facebook.com] Cookie=966347bfd 14:10 1e55040434abe… 195.202.XX.XX Chrome.. 2018-07-09 Page https://booking.com/hotels/barcelona Cookie=966347bfd 16:15 1e55040434abe… 195.202.XX.XX Chrome.. 2018-07-09 QueryLog [face, facebook.com] Cookie=966347bfd 14:10 1e55040434abe… 195.202.XX.XX FF.. 2018-07-09 Page https://shop.flixbus.de/user/resetting/res Cookie=966347bfd 18:40 et/hi7KTb1Pxa4lXqKMcwLXC0XzN- 1e55040434abe… 47Tt0Q 25.09.18 Crypto and Privacy Village 2018 Anonymous data collection Timestamp Message Type Payload 2018-07-09 14 Querylog [face, facebook.com] 2018-07-09 14 Querylog [boo, booking.com] 2018-07-09 14 Page https://booking.com/hotels/barcelona 2018-07-09 14 Telemetry [‘engagement’: 0 page loads last week, 5023 page loads last month] More details: https://gist.github.com/solso/423a1104a9e3c1e3b8d7c9ca14e885e5 http://josepmpujol.net/public/papers/big_green_tracker.pdf 25.09.18 Crypto and Privacy Village 2018 Motivation: Preventing attacks on anonymous data collection Timestamp Message Type Payload 2018-07-09 14 querylog [book, booking.com] 2018-07-09 14 querylog [fac, facebook.com] … …. -

DARK WEB INVESTIGATION GUIDE Contents 1
DARK WEB INVESTIGATION GUIDE Contents 1. Introduction 3 2. Setting up Chrome for Dark Web Access 5 3. Setting up Virtual Machines for Dark Web Access 9 4. Starting Points for Tor Investigations 20 5. Technical Clues for De-Anonymizing Hidden Services 22 5.1 Censys.io SSL Certificates 23 5.2 Searching Shodan for Hidden Services 24 5.3 Checking an IP Address for Tor Usage 24 5.4 Additional Resources 25 6. Conclusion 26 2 Dark Web Investigation Guide 1 1. Introduction 3 Introduction 1 There is a lot of confusion about what the dark web is vs. the deep web. The dark web is part of the Internet that is not accessible through traditional means. It requires that you use a technology like Tor (The Onion Router) or I2P (Invisible Internet Project) in order to access websites, email or other services. The deep web is slightly different. The deep web is made of all the webpages or entire websites that have not been crawled by a search engine. This could be because they are hidden behind paywalls or require a username and password to access. We are going to be setting up access to the dark web with a focus on the Tor network. We are going to accomplish this in two different ways. The first way is to use the Tor Browser to get Google Chrome connected to the the Tor network. This is the less private and secure option, but it is the easiest to set up and use and is sufficient for accessing material on the dark web. -

HTML5 Websocket Protocol and Its Application to Distributed Computing
CRANFIELD UNIVERSITY Gabriel L. Muller HTML5 WebSocket protocol and its application to distributed computing SCHOOL OF ENGINEERING Computational Software Techniques in Engineering MSc arXiv:1409.3367v1 [cs.DC] 11 Sep 2014 Academic Year: 2013 - 2014 Supervisor: Mark Stillwell September 2014 CRANFIELD UNIVERSITY SCHOOL OF ENGINEERING Computational Software Techniques in Engineering MSc Academic Year: 2013 - 2014 Gabriel L. Muller HTML5 WebSocket protocol and its application to distributed computing Supervisor: Mark Stillwell September 2014 This thesis is submitted in partial fulfilment of the requirements for the degree of Master of Science © Cranfield University, 2014. All rights reserved. No part of this publication may be reproduced without the written permission of the copyright owner. Declaration of Authorship I, Gabriel L. Muller, declare that this thesis titled, HTML5 WebSocket protocol and its application to distributed computing and the work presented in it are my own. I confirm that: This work was done wholly or mainly while in candidature for a research degree at this University. Where any part of this thesis has previously been submitted for a degree or any other qualification at this University or any other institution, this has been clearly stated. Where I have consulted the published work of others, this is always clearly attributed. Where I have quoted from the work of others, the source is always given. With the exception of such quotations, this thesis is entirely my own work. I have acknowledged all main sources of help. Where the thesis is based on work done by myself jointly with others, I have made clear exactly what was done by others and what I have contributed myself. -

Whotracks. Me: Shedding Light on the Opaque World of Online Tracking
WhoTracks.Me: Shedding light on the opaque world of online tracking Arjaldo Karaj Sam Macbeth Rémi Berson [email protected] [email protected] [email protected] Josep M. Pujol [email protected] Cliqz GmbH Arabellastraße 23 Munich, Germany ABSTRACT print users and their devices [25], and the extent to Online tracking has become of increasing concern in recent which these methods are being used across the web [5], years, however our understanding of its extent to date has and quantifying the value exchanges taking place in on- been limited to snapshots from web crawls. Previous at- line advertising [7, 27]. There is a lack of transparency tempts to measure the tracking ecosystem, have been done around which third-party services are present on pages, using instrumented measurement platforms, which are not and what happens to the data they collect is a common able to accurately capture how people interact with the web. concern. By monitoring this ecosystem we can drive In this work we present a method for the measurement of awareness of the practices of these services, helping to tracking in the web through a browser extension, as well as inform users whether they are being tracked, and for a method for the aggregation and collection of this informa- what purpose. More transparency and consumer aware- tion which protects the privacy of participants. We deployed ness of these practices can help drive both consumer this extension to more than 5 million users, enabling mea- and regulatory pressure to change, and help researchers surement across multiple countries, ISPs and browser con- to better quantify the privacy and security implications figurations, to give an accurate picture of real-world track- caused by these services. -

Tracking Users Across the Web Via TLS Session Resumption
Tracking Users across the Web via TLS Session Resumption Erik Sy Christian Burkert University of Hamburg University of Hamburg Hannes Federrath Mathias Fischer University of Hamburg University of Hamburg ABSTRACT modes, and browser extensions to restrict tracking practices such as User tracking on the Internet can come in various forms, e.g., via HTTP cookies. Browser fingerprinting got more difficult, as trackers cookies or by fingerprinting web browsers. A technique that got can hardly distinguish the fingerprints of mobile browsers. They are less attention so far is user tracking based on TLS and specifically often not as unique as their counterparts on desktop systems [4, 12]. based on the TLS session resumption mechanism. To the best of Tracking based on IP addresses is restricted because of NAT that our knowledge, we are the first that investigate the applicability of causes users to share public IP addresses and it cannot track devices TLS session resumption for user tracking. For that, we evaluated across different networks. As a result, trackers have an increased the configuration of 48 popular browsers and one million of the interest in additional methods for regaining the visibility on the most popular websites. Moreover, we present a so-called prolon- browsing habits of users. The result is a race of arms between gation attack, which allows extending the tracking period beyond trackers as well as privacy-aware users and browser vendors. the lifetime of the session resumption mechanism. To show that One novel tracking technique could be based on TLS session re- under the observed browser configurations tracking via TLS session sumption, which allows abbreviating TLS handshakes by leveraging resumptions is feasible, we also looked into DNS data to understand key material exchanged in an earlier TLS session. -

An Analysis of Private Browsing Modes in Modern Browsers
An Analysis of Private Browsing Modes in Modern Browsers Gaurav Aggarwal Elie Bursztein Collin Jackson Dan Boneh Stanford University CMU Stanford University Abstract Even within a single browser there are inconsistencies. We study the security and privacy of private browsing For example, in Firefox 3.6, cookies set in public mode modes recently added to all major browsers. We first pro- are not available to the web site while the browser is in pose a clean definition of the goals of private browsing private mode. However, passwords and SSL client cer- and survey its implementation in different browsers. We tificates stored in public mode are available while in pri- conduct a measurement study to determine how often it is vate mode. Since web sites can use the password man- used and on what categories of sites. Our results suggest ager as a crude cookie mechanism, the password policy that private browsing is used differently from how it is is inconsistent with the cookie policy. marketed. We then describe an automated technique for Browser plug-ins and extensions add considerable testing the security of private browsing modes and report complexity to private browsing. Even if a browser ad- on a few weaknesses found in the Firefox browser. Fi- equately implements private browsing, an extension can nally, we show that many popular browser extensions and completely undermine its privacy guarantees. In Sec- plugins undermine the security of private browsing. We tion 6.1 we show that many widely used extensions un- propose and experiment with a workable policy that lets dermine the goals of private browsing. -
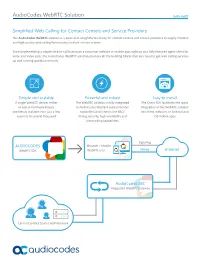
Audiocodes Webrtc Solution DATA SHEET
AudioCodes WebRTC Solution DATA SHEET Simplified Web Calling for Contact Centers and Service Providers The AudioCodes WebRTC solution is a quick and straightforward way for contact centers and service providers to supply intuitive and high-quality web calling functionality to their service centers. From implementing a simple click-to-call button on a consumer website or mobile app, right up to a fully featured agent client for voice and video calls, the AudioCodes WebRTC solution provides all the building blocks that you need to get web calling services up and running quickly and easily. Simple and scalable Powerful and robust Easy to install A single WebRTC device, either The WebRTC solution is fully integrated The Client SDK facilitates the quick virtual or hardware-based, in AudioCodes Mediant session border integration of the WebRTC solution seamlessly scalable from just a few controllers and inherits the SBCs’ into client websites or Android and sessions to several thousand strong security, high availability and iOS mobile apps transcoding capabilities Signaling AUDIOCODES Browser / Mobile WebRTC SDK WebRTC user Media Internet AudioCodes SBC Integrated WebRTC Gateway Carrier/Contact Center VoIP Network AudioCodes WebRTC Solution DATA SHEET Specifications WebRTC Gateway About AudioCodes AudioCodes Ltd. (NasdaqGS: AUDC) is a Deployment leading vendor of advanced voice networking VMWare KVM AWS Mediant 9000 Mediant 4000 method and media processing solutions for the digital workplace. With a commitment to the human 3,000 voice deeply embedded in its DNA, AudioCodes 5,000 WebRTC sessions 2,700 3,500 (20,000 on 1,000 enables enterprises and service providers (20K on roadmap) roadmap) to build and operate all-IP voice networks for unified communications, contact centers 3,000 1,050 integrated and hosted business services. -

A Deep Dive Into the Technology of Corporate Surveillance
Behind the One-Way Mirror: A Deep Dive Into the Technology of Corporate Surveillance Author: Bennett Cyphers and Gennie Gebhart A publication of the Electronic Frontier Foundation, 2019. “Behind the One-Way Mirror: A Deep Dive Into the Technology of Corporate Surveillance” is released under a Creative Commons Attribution 4.0 International License (CC BY 4.0). View this report online: https://www.eff.org/wp/behind-the-one-way-mirror ELECTRONIC FRONTIER FOUNDATION 1 Behind the One-Way Mirror: A Deep Dive Into the Technology of Corporate Surveillance Behind the One-Way Mirror A Deep Dive Into the Technology of Corporate Surveillance BENNETT CYPHERS AND GENNIE GEBHART December 2, 2019 ELECTRONIC FRONTIER FOUNDATION 2 Behind the One-Way Mirror: A Deep Dive Into the Technology of Corporate Surveillance Introduction 4 First-party vs. third-party tracking 4 What do they know? 5 Part 1: Whose Data is it Anyway: How Do Trackers Tie Data to People? 6 Identifiers on the Web 8 Identifiers on mobile devices 17 Real-world identifiers 20 Linking identifiers over time 22 Part 2: From bits to Big Data: What do tracking networks look like? 22 Tracking in software: Websites and Apps 23 Passive, real-world tracking 27 Tracking and corporate power 31 Part 3: Data sharing: Targeting, brokers, and real-time bidding 33 Real-time bidding 34 Group targeting and look-alike audiences 39 Data brokers 39 Data consumers 41 Part 4: Fighting back 43 On the web 43 On mobile phones 45 IRL 46 In the legislature 46 ELECTRONIC FRONTIER FOUNDATION 3 Behind the One-Way Mirror: A Deep Dive Into the Technology of Corporate Surveillance Introduction Trackers are hiding in nearly every corner of today’s Internet, which is to say nearly every corner of modern life. -

A Websocket-Based Approach to Transporting Web Application Data
A WebSocket-based Approach to Transporting Web Application Data March 26, 2015 A thesis submitted to the Division of Graduate Studies and Research of the University of Cincinnati in partial fulfillment of the requirements for the degree of MASTER OF SCIENCE in the Department of Computer Science of the College of Engineering and Applied Science by Ross Andrew Hadden B.S., University of Cincinnati, Cincinnati, Ohio (2014) Thesis Adviser and Committee Chair: Dr. Paul Talaga Committee members: Dr. Fred Annexstein, Professor, and Dr. John Franco, Professor Abstract Most web applications serve dynamic data by either deferring an initial page response until the data has been retrieved, or by returning the initial response immediately and loading additional content through AJAX. We investigate another option, which is to return the initial response immediately and send additional content through a WebSocket connection as the data becomes available. We intend to illustrate the performance of this proposition, as compared to popular conventions of both a server- only and an AJAX approach for achieving the same outcome. This dissertation both explains and demonstrates the implementation of the proposed model, and discusses an analysis of the findings. We use a Node.js web application built with the Cornerstone web framework to serve both the content being tested and the endpoints used for data requests. An analysis of the results shows that in situations when minimal data is retrieved after a timeout, the WebSocket method is marginally faster than the server and AJAX methods, and when retrieving populated files or database records it is marginally slower. The WebSocket method considerably outperforms the AJAX method when making multiple requests in series, and when making requests in parallel the WebSocket and server approaches both outperform AJAX by a tremendous amount. -

Proxysg Log Fields and Substitutions
ProxySG Log Fields and Substitutions Version 6.5.x through 7.3.x Guide Revision: 12/10/2020 Symantec Corporation - SGOS 6.x and 7.x Legal Notice Broadcom, the pulse logo, Connecting everything, and Symantec are among the trademarks of Broadcom. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries. Copyright © 2020 Broadcom. All Rights Reserved. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries. For more information, please visit www.broadcom.com. Broadcom reserves the right to make changes without further notice to any products or data herein to improve reliability, function, or design. Information furnished by Broadcom is believed to be accurate and reliable. However, Broadcom does not assume any liability arising out of the application or use of this information, nor the application or use of any product or circuit described herein, neither does it convey any license under its patent rights nor the rights of others. Thursday, December 10, 2020 2 of 182 sample-title Table of Contents "About this Document" on the next page Commonly Used Fields: n "Client/Server Bytes" on page 6 n "Connection Details" on page 9 n "DNS" on page 26 n "HTTP" on page 28 n "Request Headers" on page 29 n "Response Headers" on page 63 n "Request/Response Status" on page 102 n "SSL " on page 116 n "Time" on page 123 n "URL" on page 134 n "User Authentication" on page 145 n "WAF" on page 152 Additional Fields: n "CIFS " on page 155 n "MAPI and Office 365" on page 160 n "P2P Connections" on page 163 n "Special Characters" on page 164 n "Streaming Media" on page 167 n "WebEx Proxy" on page 175 "Substitution Modifiers" on page 176 n "Timestamp Modifiers" on page 177 n "String Modifiers " on page 179 n "Host Modifiers" on page 182 3 of 182 Symantec Corporation - SGOS 6.x and 7.x About this Document This document lists all valid ELFF and CPL substitutions for ELFF log formats, and some custom values for custom log formats. -

BG95&BG77 HTTP(S) Application Note
BG95&BG77 HTTP(S) Application Note LPWA Module Series Rev. BG95&BG77_HTTP(S)_Application_Note_V1.0 Date: 2019-08-12 Status: Released www.quectel.com LPWA Module Series BG95&BG77 HTTP(S) Application Note Our aim is to provide customers with timely and comprehensive service. For any assistance, please contact our company headquarters: Quectel Wireless Solutions Co., Ltd. Building 5, Shanghai Business Park Phase III (Area B), No.1016 Tianlin Road, Minhang District, Shanghai, China 200233 Tel: +86 21 5108 6236 Email: [email protected] Or our local office. For more information, please visit: http://www.quectel.com/support/sales.htm For technical support, or to report documentation errors, please visit: http://www.quectel.com/support/technical.htm Or email to: [email protected] GENERAL NOTES QUECTEL OFFERS THE INFORMATION AS A SERVICE TO ITS CUSTOMERS. THE INFORMATION PROVIDED IS BASED UPON CUSTOMERS’ REQUIREMENTS. QUECTEL MAKES EVERY EFFORT TO ENSURE THE QUALITY OF THE INFORMATION IT MAKES AVAILABLE. QUECTEL DOES NOT MAKE ANY WARRANTY AS TO THE INFORMATION CONTAINED HEREIN, AND DOES NOT ACCEPT ANY LIABILITY FOR ANY INJURY, LOSS OR DAMAGE OF ANY KIND INCURRED BY USE OF OR RELIANCE UPON THE INFORMATION. ALL INFORMATION SUPPLIED HEREIN IS SUBJECT TO CHANGE WITHOUT PRIOR NOTICE. COPYRIGHT THE INFORMATION CONTAINED HERE IS PROPRIETARY TECHNICAL INFORMATION OF QUECTEL WIRELESS SOLUTIONS CO., LTD. TRANSMITTING, REPRODUCTION, DISSEMINATION AND EDITING OF THIS DOCUMENT AS WELL AS UTILIZATION OF THE CONTENT ARE FORBIDDEN WITHOUT PERMISSION. OFFENDERS WILL BE HELD LIABLE FOR PAYMENT OF DAMAGES. ALL RIGHTS ARE RESERVED IN THE EVENT OF A PATENT GRANT OR REGISTRATION OF A UTILITY MODEL OR DESIGN.