Complete Hard Disk Encryption with Freebsd
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Portace Na Jin´E Os
VYSOKEU´ CENˇ ´I TECHNICKE´ V BRNEˇ BRNO UNIVERSITY OF TECHNOLOGY FAKULTA INFORMACNˇ ´ICH TECHNOLOGI´I USTAV´ INFORMACNˇ ´ICH SYSTEM´ U˚ FACULTY OF INFORMATION TECHNOLOGY DEPARTMENT OF INFORMATION SYSTEMS REDIRFS - PORTACE NA JINE´ OS PORTING OF REDIRFS ON OTHER OS DIPLOMOVA´ PRACE´ MASTER’S THESIS AUTOR PRACE´ Bc. LUKA´ Sˇ CZERNER AUTHOR VEDOUC´I PRACE´ Ing. TOMA´ Sˇ KASPˇ AREK´ SUPERVISOR BRNO 2010 Abstrakt Tato pr´acepopisuje jak pˇr´ıpravu na portaci, tak samotnou portaci Linuxov´ehomodulu RedirFS na operaˇcn´ısyst´emFreeBSD. Jsou zde pops´any z´akladn´ırozd´ılypˇr´ıstupuk Lin- uxov´emu a FreeBSD j´adru,d´alerozd´ılyv implementaci, pro RedirFS z´asadn´ı,ˇc´astij´adra a sice VFS vrstvy. D´alezkoum´amoˇznostia r˚uzn´epˇr´ıstupy k implementaci funkcionality linuxov´ehoRedirFS na operaˇcn´ımsyst´emu FreeBSD. N´aslednˇejsou zhodnoceny moˇznostia navrˇzenide´aln´ıpostup portace. N´asleduj´ıc´ıkapitoly pak popisuj´ıpoˇzadovanou funkcional- itu spolu s navrhovanou architekturou nov´ehomodulu. D´aleje detailnˇepops´ann´avrha implementace nov´ehomodulu tak, aby mˇelˇcten´aˇrjasnou pˇredstavu jak´ymzp˚usobem modul implementuje poˇzadovanou funkcionalitu. Abstract This thesis describes preparation for porting as well aw porting itself of RedirFS Linux kernel module to FreeBSD. Basic differences between Linux and FreeBSD kernels are de- scribed as well as differences in implementation of the Virtual Filesystem, crucial part for RedirFS. Further there are described possibilities and different approaches to implemen- tation RedirFS functionality to FreeBSD. Then, the possibilities are evaluated and ideal approach is proposed. Next chapters introduces erquired functionality of the new module as well as its solutions. Then the implementation details are describet so the reader can very well understand how the new module works and how the required functionality is implemented into the module. -

Introduzione Al Mondo Freebsd
Introduzione al mondo FreeBSD Corso avanzato Netstudent Netstudent http://netstudent.polito.it E.Richiardone [email protected] maggio 2009 CC-by http://creativecommons.org/licenses/by/2.5/it/ The FreeBSD project - 1 ·EÁ un progetto software open in parte finanziato ·Lo scopo eÁ mantenere e sviluppare il sistema operativo FreeBSD ·Nasce su CDROM come FreeBSD 1.0 nel 1993 ·Deriva da un patchkit per 386BSD, eredita codice da UNIX versione Berkeley 1977 ·Per problemi legali subisce un rallentamento, release 2.0 nel 1995 con codice royalty-free ·Dalla release 5.0 (2003) assume la struttura che ha oggi ·Disponibile per x86 32 e 64bit, ia64, MIPS, ppc, sparc... ·La mascotte (Beastie) nasce nel 1984 The FreeBSD project - 2 ·Erede di 4.4BSD (eÁ la stessa gente...) ·Sistema stabile; sviluppo uniforme; codice molto chiaro, ordinato e ben commentato ·Documentazione ufficiale ben curata ·Licenza molto permissiva, spesso attrae aziende per progetti commerciali: ·saltuariamente esterni collaborano con implementazioni ex-novo (i.e. Intel, GEOM, atheros, NDISwrapper, ZFS) ·a volte no (i.e. Windows NT) ·Semplificazione di molte caratteristiche tradizionali UNIX Di cosa si tratta Il progetto FreeBSD include: ·Un sistema base ·Bootloader, kernel, moduli, librerie di base, comandi e utility di base, servizi tradizionali ·Sorgenti completi in /usr/src (~500MB) ·EÁ giaÁ abbastanza completo (i.e. ipfw, ppp, bind, ...) ·Un sistema di gestione per software aggiuntivo ·Ports e packages ·Documentazione, canali di assistenza, strumenti di sviluppo ·i.e. Handbook, -

BSD UNIX Toolbox 1000+ Commands for Freebsd, Openbsd
76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page iii BSD UNIX® TOOLBOX 1000+ Commands for FreeBSD®, OpenBSD, and NetBSD®Power Users Christopher Negus François Caen 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page ii 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page i BSD UNIX® TOOLBOX 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page ii 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page iii BSD UNIX® TOOLBOX 1000+ Commands for FreeBSD®, OpenBSD, and NetBSD®Power Users Christopher Negus François Caen 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page iv BSD UNIX® Toolbox: 1000+ Commands for FreeBSD®, OpenBSD, and NetBSD® Power Users Published by Wiley Publishing, Inc. 10475 Crosspoint Boulevard Indianapolis, IN 46256 www.wiley.com Copyright © 2008 by Wiley Publishing, Inc., Indianapolis, Indiana Published simultaneously in Canada ISBN: 978-0-470-37603-4 Manufactured in the United States of America 10 9 8 7 6 5 4 3 2 1 Library of Congress Cataloging-in-Publication Data is available from the publisher. No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. Requests to the Publisher for permis- sion should be addressed to the Legal Department, Wiley Publishing, Inc., 10475 Crosspoint Blvd., Indianapolis, IN 46256, (317) 572-3447, fax (317) 572-4355, or online at http://www.wiley.com/go/permissions. -

Freesbie - Français
FreeBSD FreeSBIE - Français Surfer anonymement sur la toile avec Tor et Liste de choses à faire (TODO list) pour la Privoxy prochaine édition de FreeSBIE La vie privée n'est pas seulement importante, c'est une né- Les point suivants sont ceux qui n'ont pas été réalisés FreeBSD cessité. Vous ne voulez pas que d'autres personnes ap- dans la présente version. Si une version possédait toutes prennent les adresses des sites que vous allez visiter, d'où les caractéristiques nécessaires aux utilisateurs et celles FreeSBIE LiveCD vous venez, et ainsi de suite. Les mêmes principes s'appli- souhaitées par les programmeurs alors il n'y aurait plus de quent pour les autres services internet : SSH, IRC, etc. nouvelle version. FreeSBIE fournit deux puissants outils pour rendre la 1. Relecture du code - Bien que la boîte à outils de FreeS- Qu'est ce que FreeSBIE ? navigation anonyme et plus sûre: Tor et Privoxy. Vous BIE ait été complètement réécrite au cours de l'été 2004, FreeSBIE est un système d'exploitation complet utilisable pouvez rediriger vos connexions à travers différents il subsiste bon nombre de parties modifiées qui requièrent à partir d'un CD ou d'un DVD. Il est capable de détecter routeurs et obtenir un anonymat presque parfait. Parce un examen minutieux. automatiquement les composants de votre ordinateur et il qu'une telle configuration est loin d'être simple, FreeSBIE 2. Réécriture de BSDinstaller. Cette tâche progresse rap- reconnaît quantité de cartes graphiques, de périphériques vous assiste avec un script : /usr/local/bin/freesbie_tor. En idement. USB et autres matériels. -
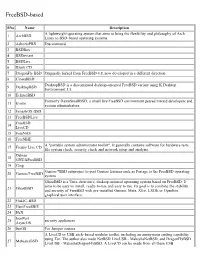
List of BSD Operating Systems
FreeBSD-based SNo Name Description A lightweight operating system that aims to bring the flexibility and philosophy of Arch 1 ArchBSD Linux to BSD-based operating systems. 2 AskoziaPBX Discontinued 3 BSDBox 4 BSDeviant 5 BSDLive 6 Bzerk CD 7 DragonFly BSD Originally forked from FreeBSD 4.8, now developed in a different direction 8 ClosedBSD DesktopBSD is a discontinued desktop-oriented FreeBSD variant using K Desktop 9 DesktopBSD Environment 3.5. 10 EclipseBSD Formerly DamnSmallBSD; a small live FreeBSD environment geared toward developers and 11 Evoke system administrators. 12 FenestrOS BSD 13 FreeBSDLive FreeBSD 14 LiveCD 15 FreeNAS 16 FreeSBIE A "portable system administrator toolkit". It generally contains software for hardware tests, 17 Frenzy Live CD file system check, security check and network setup and analysis. Debian 18 GNU/kFreeBSD 19 Ging Gentoo/*BSD subproject to port Gentoo features such as Portage to the FreeBSD operating 20 Gentoo/FreeBSD system GhostBSD is a Unix-derivative, desktop-oriented operating system based on FreeBSD. It aims to be easy to install, ready-to-use and easy to use. Its goal is to combine the stability 21 GhostBSD and security of FreeBSD with pre-installed Gnome, Mate, Xfce, LXDE or Openbox graphical user interface. 22 GuLIC-BSD 23 HamFreeSBIE 24 HeX IronPort 25 security appliances AsyncOS 26 JunOS For Juniper routers A LiveCD or USB stick-based modular toolkit, including an anonymous surfing capability using Tor. The author also made NetBSD LiveUSB - MaheshaNetBSD, and DragonFlyBSD 27 MaheshaBSD LiveUSB - MaheshaDragonFlyBSD. A LiveCD can be made from all these USB distributions by running the /makeiso script in the root directory. -

Introduzione Al Mondo Freebsd Corso Avanzato
Introduzione al mondo FreeBSD corso Avanzato •Struttura •Installazione •Configurazione •I ports •Gestione •Netstudent http://netstudent.polito.it •E.Richiardone [email protected] •Novembre 2012 •CC-by http://creativecommons.org/licenses/by/3.0/it/ The FreeBSD project - 1 • E` un progetto software open • Lo scopo e` mantenere e sviluppare il sistema operativo FreeBSD • Nasce su CDROM come FreeBSD 1.0 nel 1993 • Deriva da un patchkit per 386BSD, eredita codice da UNIX versione Berkeley 1977 • Per problemi legali subisce un rallentamento, release 2.0 nel 1995 con codice royalty-free • Dalla release 4.0 (2000) assume la struttura che ha oggi • Disponibile per x86 32 e 64bit, ia64, MIPS, ppc, sparc... • La mascotte (Beastie) nasce nel 1984 The FreeBSD project - 2 • Erede di 4.4BSD (e` la stessa gente...) • Sistema stabile; sviluppo uniforme; codice molto chiaro, ordinato e ben commentato • Documentazione ufficiale ben curata • Licenza molto permissiva, spesso attrae aziende per progetti commerciali: • saltuariamente progetti collaborano con implementazioni ex-novo (i.e. Intel, GEOM, NDISwrapper, ZFS, GNU/Linux emulation) • Semplificazione di molte caratteristiche tradizionali UNIX Di cosa si tratta Il progetto FreeBSD include: • Un sistema base • Bootloader, kernel, moduli, librerie di base, comandi e utility di base, servizi tradizionali • Sorgenti completi in /usr/src (~500MB) • E` gia` completo (i.e. ipfw, ppp, bind, ...) • Un sistema di gestione per software aggiuntivo • Ports e packages • Documentazione, canali di assistenza, strumenti -

Freebsd-Based Live Disks (Deel 2)
SoftwareBus 2008 6 ----------- FreeBSD-based live disks (deel 2) ------------ Jan Stedehouder In dit tweede deel staan wel stil bij drie GIMP, Inkscape en GQView vullen de live cd’s die op FreeBSD zijn gebaseerd. grafische afdeling in e n Beep Media In het eerste deel bekeken we l i v e cd’s Player, BMPx en MPlayer zorgen v o o r het voor O p e n B S D , NetBSD en Dragonfly. multimediale gebeuren. Dewerkblad- Mooie projecten, maar we misten bij de achtergrond verandert bij iedere vol- meeste de mogelijkheid om de cd op gende start. een harde schijf te installeren. Zullen de drie kandidaten voor dit deel het be- Deze live cd heeft geen mogelijkheid tot ter doen? We bekijken FreeSBIE, Desk- installatie op de harde schijf. In e e n in- topBSD and RoFreeSBIE Zoals we zullen terview met Distrowatch Weekly (num- zien, kan RoFreeSBIE beschouwd worden mer 186, 22 januari 2007) verklaarde als een samensmelting van de andere ontwikkelaar Matteo R o n d a t o dat dit ook twee cd’s. geen hoge prioriteit had. Hij geeft er de voorkeur aan dat gebruikers in dat geval FreeSBIE direct FreeBSD gebruiken. FreeSBIE kan worden gezien als een voort- zetting van het FreeBSD live-project en werd voor het eerst vrijgegeven in 2003. De meest recente vrij- gave (2.0.1) is al weer anderhalf jaar oud en was gebaseerd op FreeBSD 6.2. FreeSBIE presenteert een grafi- sche desktop, geba- seerd op Xfce (met Fluxbox als alternatie- ve mogelijkheid). Het aantal program- Fig. 6:FreeSBIE maakt gebruik van de Xfce gr a fi - ma ’ s is beperkt, maar voor eindgebrui- sche omgeving kers in eerste instantie afdoende. -

Copyrighted Material
76034c01.qxd:Toolbox 3/29/08 10:40 AM Page 1 Starting with BSD Systems Whether you use BSD systems every day or just tweak one once in a while, a book that presents effi- IN THIS CHAPTER cient ways to use, check, fix, secure, and enhance Find BSD resources your system can be an invaluable resource. Learn quick and BSD UNIX Toolbox is that resource. powerful commands Have a handy refer- BSD UNIX Toolbox is aimed primarily at BSD ence to many useful power users and systems administrators. To give utilities you what you need, we tell you how to quickly locate and get software, monitor the health and Work as BSD gurus do security of your systems, and access network resources. In short, we cut to the most efficient ways of using BSD systems. Our goal with BSD UNIX Toolbox is to pack a lot of useful information for using BSD systems into a small package that you can carry around with you. To that end, we describe: ❑ Commands — Tons of command line examples to use BSD systems in helpful and clever ways ❑ GUI Tools — Quick pointers to graphical administration tools to configure your system ❑ Software packages — Short procedures to find and download tons of applications ❑ OnlineCOPYRIGHTED resources — Listings of the best MATERIAL locations to find BSD forums, mailing lists, IRC channels, and other online resources ❑ Local documentation — Tools for gathering more information from man pages, doc directories, help commands, and other resources on your BSD system Because you’re not a beginner with BSD systems, you won’t see a lot of screenshots of windows, icons, and menus. -

The Freebsd Project
Το FreeBSD Project Γιώργος Κεραμίδας [email protected] Τι Είναι το FreeBSD; (1) • BSD UNIX, Ελεύθερο Λογισμικό • Ιστορικές ρίζες στο αρχικό BSD • Πλατφόρμα Δικτύων ISP (Yahoo!, Verio, ISC) • Embedded περιβάλλον (Juniper JunOS, Nokia, Timing Solutions, VXWorks) • Ένα από τα πιο επιτυχημένα projects ελεύθερου λογισμικού • Έμφαση σε storage, δικτυακές εφαρμογές & ασφάλεια Patras LUG Το FreeBSD Project 1 Τι Είναι το FreeBSD; (2) • Ολοκληρωμένο, integrated UNIX σύστημα • Πολυ-επεξεργαστικός, πολυ-νηματικός πυρήνας • Intel/AMD 32/64 bit, Itanium, sparc64, ARM, PPC • MIPS! Δωρεά της Juniper Networks • Εργαλεία & API προγραμματισμού: UNIX, POSIX, BSD • Network stack με υποστήριξη για πολλά πρωτόκολα • IPv4, IPv6, IPX/SPX, AppleTalk, IPSEC, ATM, Bluetooth, 802.11, SCTP, … • Ενσωματωμένη και σταθερή υποστήριξη για embedded targets & cross building, ως μέρος της επίσημης διαδικα- σίας ανάπτυξης Patras LUG Το FreeBSD Project 2 Τι Είναι το FreeBSD; (3) • Ολοκληρωμένο, integrated UNIX σύστημα • Εκτενής τεκμηρίωση, τόσο ως μέρος του συστήματος όσο και online • Ενημερωμένα manpages & τεκμηρίωση info • Πλήρες «βασικό σύστημα», με όλα τα εργαλεία που πε- ριμένει να βρει κανείς σε ένα UNIX • 18.148 πακέτα λογισμικού (2 Μάρτη 2008), ως μέρος του συστήματος των «Ports» • Πάνω από 50 κατηγορίες λογισμικού • Πολλά κοινά προγράμματα με Linux • Π.χ. Gnome, KDE, XFCE4, Mozilla apps Patras LUG Το FreeBSD Project 3 Το FreeBSD Project • Η Κοινότητα του FreeBSD • Κεντρικό repository και source code control • Μεγάλη δικτυακή κοινότητα • 340 committers, χιλιάδες ενεργά -

BSD Based Systems
Pregled BSD sistema I projekata Glavne BSD grane FreeBSD Homepage: http://www.freebsd.org/ FreeBSD je Unix-like slobodni operativni sistem koji vodi poreklo iz AT&T UNIX-a preko Berkeley Software Distribution (BSD) grane kroz 386BSD i 4.4BSD. Radi na procesorima kompatibilnim sa Intel x86 familijom procesora, kao I na DEC Alpha, UltraSPARC procesorima od Sun Microsystems, Itanium (IA-64), AMD64 i PowerPC procesorima. Radi I na PC-98 arhitekturi. Podrska za ARM i MIPS arhitekture je trenutno u razvoju. Početkom 1993. godine Jordan K. Hubbard, Rod Grimes i Nate Williams su pokrenuli projekat čiji je cilj bio rešavanje problema koji su postojali u principima razvoja Jolitzovog 386BSD-a. Posle konsultovanja sa tadašnjim korisnicima sistema, uspostavljeni su principi i smišljeno je ime - FreeBSD. Pre nego što je konkretan razvoj i počeo, Jordan Hubbard je predložio je firmi Walnut Creek CDROM (danas BSDi) da pripreme distribuiranje FreeBSD-a na CD-ROM-ovima. Walnut Creek CDROM su prihvatili ideju, ali i obezbedili (tada potpuno nepoznatom) projektu mašinu na kojoj će biti razvijan i brzu Internet konekciju. Bez ove pomoći teško da bi FreeBSD bio razvijen u ovolikoj meri i ovolikom brzinom kao što jeste. Prva distribucija FreeBSD-a na CD-ROM-ovima (i naravno na netu) bila je FreeBSD 1.0, objavljena u decembru 1993. godine. Bila je zasnovana na Berkeley-evoj 4.3BSD-Lite ("Net/2") traci, a naravno sadržala je i komponente 386BSD-a i mnoge programe Free Software Foundation (fondacija besplatnog- slobodnog softvera). Nakon što je Novell otkupio UNIX od AT&T-a, Berkeley je morao da prizna da Net/2 traka sadrži velike delove UNIX koda. -

Freesbie - a Code Walkthrough and a Case Study
FreeSBIE - A code walkthrough and a case study Matteo Riondato <rionda@gufi.org>, Massimiliano Stucchi <max@gufi.org> October 11, 2004 1 Introduction FreeSBIE is a LiveCD based on the FreeBSD operating system developed by an Italian group of people, and supported mainly by the Italian FreeBSD Users Group, known as GUFI. The first release (1.0) was released on April 15th, 2004, and has already been downloaded almost 20.000 times. But FreeSBIE is not only an ISO file you can download from one of our mirrors, it is also a way to create your very own, fully customized, LiveCD. In this paper, we’re going to depict how the FreeSBIE provided by the team can accomplish the task of letting everybody become a Release Engineer on his own. 2 The GUFI The Italian FreeBSD Users Group is a small group of people whose aim is to spread the word about FreeBSD in Italy. It is composed of 15 people making up the staff, working together to keep the mailing lists and the IRC channel in good state. The main event for the group is GUFICon, having place every year around the end of September. This time it was in Milan on October 2 and 3. 3 The beginning The project was started by Davide "dave" D’amico, in order to fulfill the need for a LiveCD based on FreeBSD. There already was a solution around, created by a Brazilian group, but it wasn’t as flexible as dave needed. He brought the project on and found help form Dario "SaturNero" Freni initially, and from the whole GUFI, in a couple of months. -

Recent and Forthcoming Freebsd Releases
Recent and Forthcoming FreeBSD Releases David Malone <[email protected]> 14 February 2009 W3 Servers IRELAND (November 1993) CURIA Irish Literature archive IEunet Networking Information regarding Ireland, and Links to the rest of Europe. Trinity College Dublin Dept of Mathematics IONA Technologies Ltd. info about their Object Request Broker software product and some bits and pieces of Irish news The University of Limerick Information on Natural Language Processing and some research projects in the Department of Computer Science and Information Systems. (Not using http yet) Plan • How the FreeBSD project runs. • How our releases are structured. • How we got to FreeBSD 7. • FreeBSD 7.1 and 7.X. • What’s to come next. A bit about me • Work in Hamilton Institute NUI Maynooth. • Background in maths and sysadmin. • About 1995 wanted to build xterms. • Looked at cheap ways of doing it. • Found FreeBSD. • Got involved in bugfixing. • In 2000 became a committer. The Blurb FreeBSD is an advanced operating system for modern server, desktop, and embedded computer platforms. FreeBSD’s code base has undergone over thirty years of continuous development, improvement, and optimization. It is developed and maintained by a large team of individuals. FreeBSD provides advanced networking, impressive security features, and world class performance and is used by some of the world’s busiest web sites and most pervasive embedded networking and storage devices. FreeBSD Project Structure • Users (unknown number). • Contributors (thousands?). • Committers • doc: 54, • ports: 157, • src: 204. • Elect or coopt various special groups • bug busters, • core, • security team, • ... FreeBSD Releases • The most recent version of FreeBSD is -current.