Exploring the Monero Peer-To-Peer Network
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

On the Relationship of Cryptocurrency Price with US Stock and Gold Price Using Copula Models
mathematics Article On the Relationship of Cryptocurrency Price with US Stock and Gold Price Using Copula Models Jong-Min Kim 1 , Seong-Tae Kim 2 and Sangjin Kim 3,* 1 Statistics Discipline, University of Minnesota at Morris, Morris, MN 56267, USA; [email protected] 2 Department of Mathematics, North Carolina A&T State University, Greensboro, NC 27411, USA; [email protected] 3 Department of Management and Information Systems, Dong-A University, Busan 49236, Korea * Correspondence: [email protected] Received: 15 September 2020; Accepted: 20 October 2020; Published: 23 October 2020 Abstract: This paper examines the relationship of the leading financial assets, Bitcoin, Gold, and S&P 500 with GARCH-Dynamic Conditional Correlation (DCC), Nonlinear Asymmetric GARCH DCC (NA-DCC), Gaussian copula-based GARCH-DCC (GC-DCC), and Gaussian copula-based Nonlinear Asymmetric-DCC (GCNA-DCC). Under the high volatility financial situation such as the COVID-19 pandemic occurrence, there exist a computation difficulty to use the traditional DCC method to the selected cryptocurrencies. To solve this limitation, GC-DCC and GCNA-DCC are applied to investigate the time-varying relationship among Bitcoin, Gold, and S&P 500. In terms of log-likelihood, we show that GC-DCC and GCNA-DCC are better models than DCC and NA-DCC to show relationship of Bitcoin with Gold and S&P 500. We also consider the relationships among time-varying conditional correlation with Bitcoin volatility, and S&P 500 volatility by a Gaussian Copula Marginal Regression (GCMR) model. The empirical findings show that S&P 500 and Gold price are statistically significant to Bitcoin in terms of log-return and volatility. -

Vulnerability of Blockchain Technologies to Quantum Attacks
Vulnerability of Blockchain Technologies to Quantum Attacks Joseph J. Kearneya, Carlos A. Perez-Delgado a,∗ aSchool of Computing, University of Kent, Canterbury, Kent CT2 7NF United Kingdom Abstract Quantum computation represents a threat to many cryptographic protocols in operation today. It has been estimated that by 2035, there will exist a quantum computer capable of breaking the vital cryptographic scheme RSA2048. Blockchain technologies rely on cryptographic protocols for many of their essential sub- routines. Some of these protocols, but not all, are open to quantum attacks. Here we analyze the major blockchain-based cryptocurrencies deployed today—including Bitcoin, Ethereum, Litecoin and ZCash, and determine their risk exposure to quantum attacks. We finish with a comparative analysis of the studied cryptocurrencies and their underlying blockchain technologies and their relative levels of vulnerability to quantum attacks. Introduction exist to allow the legitimate owner to recover this account. Blockchain systems are unlike other cryptosys- tems in that they are not just meant to protect an By contrast, in a blockchain system, there is no information asset. A blockchain is a ledger, and as central authority to manage users’ access keys. The such it is the asset. owner of a resource is by definition the one hold- A blockchain is secured through the use of cryp- ing the private encryption keys. There are no of- tographic techniques. Notably, asymmetric encryp- fline backups. The blockchain, an always online tion schemes such as RSA or Elliptic Curve (EC) cryptographic system, is considered the resource— cryptography are used to generate private/public or at least the authoritative description of it. -
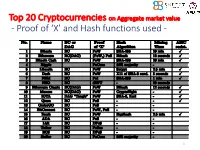
Proof of 'X' and Hash Functions Used
Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 1 ISI Kolkata BlockChain Workshop, Nov 30th, 2017 CRYPTOGRAPHY with BlockChain - Hash Functions, Signatures and Anonymization - Hiroaki ANADA*1, Kouichi SAKURAI*2 *1: University of Nagasaki, *2: Kyushu University Acknowledgements: This work is supported by: Grants-in-Aid for Scientific Research of Japan Society for the Promotion of Science; Research Project Number: JP15H02711 Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 3 Table of Contents 1. Cryptographic Primitives in Blockchains 2. Hash Functions a. Roles b. Various Hash functions used for Proof of ‘X’ 3. Signatures a. Standard Signatures (ECDSA) b. Ring Signatures c. One-Time Signatures (Winternitz) 4. Anonymization Techniques a. Mixing (CoinJoin) b. Zero-Knowledge proofs (zk-SNARK) 5. Conclusion 4 Brief History of Proof of ‘X’ 1992: “Pricing via Processing or Combatting Junk Mail” Dwork, C. and Naor, M., CRYPTO ’92 Pricing Functions 2003: “Moderately Hard Functions: From Complexity to Spam Fighting” Naor, M., Foundations of Soft. Tech. and Theoretical Comp. Sci. 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 5 Brief History of Proof of ‘X’ 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 2012: “Peercoin” Proof of Stake (& Proof of Work) ~ : Delegated Proof of Stake, Proof of Storage, Proof of Importance, Proof of Reserves, Proof of Consensus, ... 6 Proofs of ‘X’ 1. Proof of Work 2. Proof of Stake Hash-based Proof of ‘X’ 3. Delegated Proof of Stake 4. Proof of Importance 5. -

Cryptocurrency: the Economics of Money and Selected Policy Issues
Cryptocurrency: The Economics of Money and Selected Policy Issues Updated April 9, 2020 Congressional Research Service https://crsreports.congress.gov R45427 SUMMARY R45427 Cryptocurrency: The Economics of Money and April 9, 2020 Selected Policy Issues David W. Perkins Cryptocurrencies are digital money in electronic payment systems that generally do not require Specialist in government backing or the involvement of an intermediary, such as a bank. Instead, users of the Macroeconomic Policy system validate payments using certain protocols. Since the 2008 invention of the first cryptocurrency, Bitcoin, cryptocurrencies have proliferated. In recent years, they experienced a rapid increase and subsequent decrease in value. One estimate found that, as of March 2020, there were more than 5,100 different cryptocurrencies worth about $231 billion. Given this rapid growth and volatility, cryptocurrencies have drawn the attention of the public and policymakers. A particularly notable feature of cryptocurrencies is their potential to act as an alternative form of money. Historically, money has either had intrinsic value or derived value from government decree. Using money electronically generally has involved using the private ledgers and systems of at least one trusted intermediary. Cryptocurrencies, by contrast, generally employ user agreement, a network of users, and cryptographic protocols to achieve valid transfers of value. Cryptocurrency users typically use a pseudonymous address to identify each other and a passcode or private key to make changes to a public ledger in order to transfer value between accounts. Other computers in the network validate these transfers. Through this use of blockchain technology, cryptocurrency systems protect their public ledgers of accounts against manipulation, so that users can only send cryptocurrency to which they have access, thus allowing users to make valid transfers without a centralized, trusted intermediary. -

A Survey on Volatility Fluctuations in the Decentralized Cryptocurrency Financial Assets
Journal of Risk and Financial Management Review A Survey on Volatility Fluctuations in the Decentralized Cryptocurrency Financial Assets Nikolaos A. Kyriazis Department of Economics, University of Thessaly, 38333 Volos, Greece; [email protected] Abstract: This study is an integrated survey of GARCH methodologies applications on 67 empirical papers that focus on cryptocurrencies. More sophisticated GARCH models are found to better explain the fluctuations in the volatility of cryptocurrencies. The main characteristics and the optimal approaches for modeling returns and volatility of cryptocurrencies are under scrutiny. Moreover, emphasis is placed on interconnectedness and hedging and/or diversifying abilities, measurement of profit-making and risk, efficiency and herding behavior. This leads to fruitful results and sheds light on a broad spectrum of aspects. In-depth analysis is provided of the speculative character of digital currencies and the possibility of improvement of the risk–return trade-off in investors’ portfolios. Overall, it is found that the inclusion of Bitcoin in portfolios with conventional assets could significantly improve the risk–return trade-off of investors’ decisions. Results on whether Bitcoin resembles gold are split. The same is true about whether Bitcoins volatility presents larger reactions to positive or negative shocks. Cryptocurrency markets are found not to be efficient. This study provides a roadmap for researchers and investors as well as authorities. Keywords: decentralized cryptocurrency; Bitcoin; survey; volatility modelling Citation: Kyriazis, Nikolaos A. 2021. A Survey on Volatility Fluctuations in the Decentralized Cryptocurrency Financial Assets. Journal of Risk and 1. Introduction Financial Management 14: 293. The continuing evolution of cryptocurrency markets and exchanges during the last few https://doi.org/10.3390/jrfm years has aroused sparkling interest amid academic researchers, monetary policymakers, 14070293 regulators, investors and the financial press. -

Exploring the Interconnectedness of Cryptocurrencies Using Correlation Networks
Exploring the Interconnectedness of Cryptocurrencies using Correlation Networks Andrew Burnie UCL Computer Science Doctoral Student at The Alan Turing Institute [email protected] Conference Paper presented at The Cryptocurrency Research Conference 2018, 24 May 2018, Anglia Ruskin University Lord Ashcroft International Business School Centre for Financial Research, Cambridge, UK. Abstract Correlation networks were used to detect characteristics which, although fixed over time, have an important influence on the evolution of prices over time. Potentially important features were identified using the websites and whitepapers of cryptocurrencies with the largest userbases. These were assessed using two datasets to enhance robustness: one with fourteen cryptocurrencies beginning from 9 November 2017, and a subset with nine cryptocurrencies starting 9 September 2016, both ending 6 March 2018. Separately analysing the subset of cryptocurrencies raised the number of data points from 115 to 537, and improved robustness to changes in relationships over time. Excluding USD Tether, the results showed a positive association between different cryptocurrencies that was statistically significant. Robust, strong positive associations were observed for six cryptocurrencies where one was a fork of the other; Bitcoin / Bitcoin Cash was an exception. There was evidence for the existence of a group of cryptocurrencies particularly associated with Cardano, and a separate group correlated with Ethereum. The data was not consistent with a token’s functionality or creation mechanism being the dominant determinants of the evolution of prices over time but did suggest that factors other than speculation contributed to the price. Keywords: Correlation Networks; Interconnectedness; Contagion; Speculation 1 1. Introduction The year 2017 saw the start of a rapid diversification in cryptocurrencies. -

An Empirical Analysis of Smart Contracts: Platforms, Applications, and Design Patterns
An empirical analysis of smart contracts: platforms, applications, and design patterns Massimo Bartoletti and Livio Pompianu Universit`adegli Studi di Cagliari, Cagliari, Italy fbart,[email protected] Abstract. Smart contracts are computer programs that can be consis- tently executed by a network of mutually distrusting nodes, without the arbitration of a trusted authority. Because of their resilience to tamper- ing, smart contracts are appealing in many scenarios, especially in those which require transfers of money to respect certain agreed rules (like in financial services and in games). Over the last few years many plat- forms for smart contracts have been proposed, and some of them have been actually implemented and used. We study how the notion of smart contract is interpreted in some of these platforms. Focussing on the two most widespread ones, Bitcoin and Ethereum, we quantify the usage of smart contracts in relation to their application domain. We also analyse the most common programming patterns in Ethereum, where the source code of smart contracts is available. 1 Introduction Since the release of Bitcoin in 2009 [38], the idea of exploiting its enabling tech- nology to develop applications beyond currency has been receiving increasing attention [24]. In particular, the public and append-only ledger of transaction (the blockchain) and the decentralized consensus protocol that Bitcoin nodes use to extend it, have revived Nick Szabo's idea of smart contracts | i.e. pro- grams whose correct execution is automatically enforced without relying on a trusted authority [45]. The archetypal implementation of smart contracts is Ethereum [26], a platform where they are rendered in a Turing-complete lan- guage. -

Proof of Behavior Paul-Marie Grollemund, Pascal Lafourcade, Kevin Thiry-Atighehchi, Ariane Tichit
Proof of Behavior Paul-Marie Grollemund, Pascal Lafourcade, Kevin Thiry-Atighehchi, Ariane Tichit To cite this version: Paul-Marie Grollemund, Pascal Lafourcade, Kevin Thiry-Atighehchi, Ariane Tichit. Proof of Behav- ior. The 2nd Tokenomics Conference on Blockchain Economics, Security and Protocols, Oct 2020, Toulouse, France. hal-02559573 HAL Id: hal-02559573 https://hal.archives-ouvertes.fr/hal-02559573 Submitted on 30 Apr 2020 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Distributed under a Creative Commons Attribution| 4.0 International License 1 Proof of Behavior 2 Paul-Marie Grollemund 3 Université Clermont Auvergne, LMBP UMR 6620, Aubière, France 4 [email protected] 1 5 Pascal Lafourcade 6 Université Clermont Auvergne, LIMOS UMR 6158, Aubière, France 7 [email protected] 8 Kevin Thiry-Atighehchi 9 Université Clermont Auvergne, LIMOS UMR 6158, Aubière, France 10 [email protected] 11 Ariane Tichit 12 Université Clermont Auvergne, Cerdi UMR 6587, Clermont-Ferrand France 13 [email protected] 14 Abstract 15 Our aim is to change the Proof of Work paradigm. Instead of wasting energy in dummy computations 16 with hash computations, we propose a new approach based on the behavior of the users. -

A Comparison of Monero and Zcash
A Comparison of Monero and Zcash H˚avard Anda Estensen [email protected] June 13, 2018 Abstract There is a lot of excitement (and hype) around blockchain. Since most of the blockchains rely on a public ledger, transactions are pseudonymous and fully traceable. This paper will examine and compare how two popular cryp- tocurrencies, Monero and Zcash achieve privacy by obfuscating transactions. 1 Introduction Cryptocurrencies like Bitcoin (BTC) is revolutionizing the way digital payments are done. The systems are designed to work without an intermediary, directly between users. This is done by recording transactions on a public distributed ledger - a blockchain. Users that provide CPU power to the network are called miners and are rewarded with the network currency. But transactions are not as private as a lot of people think. Web merchants routinely leak data about purchases[1] and once one purchase is compromised the all purchases linked to an account is compromised since all transactions are recorded on the blockchain. In this paper, BTC will be used as a baseline comparison against Monero and Zcash. This makes a good comparison as both Monero and Zcash are hard forks of Bitcoin. 2 Why Privacy Is Important To understand why BTC doesn't provide desired privacy properties it is necessary to take a step back to look at how the core technology works. 2.1 Blockchain A blockchain is an append-only list of blocks that are linked and secured with cryptography[2]. Each block contains transaction data, a timestamp and the crypto- graphic hash of the previous block. -

Performance Analysis of Cryptographic Hash Functions Suitable for Use in Blockchain
I. J. Computer Network and Information Security, 2021, 2, 1-15 Published Online April 2021 in MECS (http://www.mecs-press.org/) DOI: 10.5815/ijcnis.2021.02.01 Performance Analysis of Cryptographic Hash Functions Suitable for Use in Blockchain Alexandr Kuznetsov1 , Inna Oleshko2, Vladyslav Tymchenko3, Konstantin Lisitsky4, Mariia Rodinko5 and Andrii Kolhatin6 1,3,4,5,6 V. N. Karazin Kharkiv National University, Svobody sq., 4, Kharkiv, 61022, Ukraine E-mail: [email protected], [email protected], [email protected], [email protected], [email protected] 2 Kharkiv National University of Radio Electronics, Nauky Ave. 14, Kharkiv, 61166, Ukraine E-mail: [email protected] Received: 30 June 2020; Accepted: 21 October 2020; Published: 08 April 2021 Abstract: A blockchain, or in other words a chain of transaction blocks, is a distributed database that maintains an ordered chain of blocks that reliably connect the information contained in them. Copies of chain blocks are usually stored on multiple computers and synchronized in accordance with the rules of building a chain of blocks, which provides secure and change-resistant storage of information. To build linked lists of blocks hashing is used. Hashing is a special cryptographic primitive that provides one-way, resistance to collisions and search for prototypes computation of hash value (hash or message digest). In this paper a comparative analysis of the performance of hashing algorithms that can be used in modern decentralized blockchain networks are conducted. Specifically, the hash performance on different desktop systems, the number of cycles per byte (Cycles/byte), the amount of hashed message per second (MB/s) and the hash rate (KHash/s) are investigated. -

Unpacking Blockchains
Unpacking Blockchains JOHN PRPIĆ - Faculty of Business Administration, Technology and Social Sciences, Lulea University of Technology -------------------------------------------------------------------------------------------------------------------------------------------------------------- 1: INTRODUCTION The Bitcoin digital currency appeared in 2009. Since this time, researchers and practitioners have looked “under the hood” of the open source Bitcoin currency, and discovered that Bitcoin’s “Blockchain” software architecture is useful for non-monetary purposes too. By coalescing the research and practice on Blockchains, this work begins to unpack Blockchains as a general phenomenon, therein, arguing that all Blockchain phenomena can be conceived as being comprised of transaction platforms and digital ledgers, and illustrating where public key encryption plays a differential role in facilitating these features of Blockchains 2: CRYPTOCURRENCY In 2008, Satoshi Nakamoto1 released a whitepaper detailing the principles behind a “peer-to-peer electronic cash system” (Nakamoto 2008) called Bitcoin. Early in 2009, Nakamoto followed up the whitepaper with a release of the very first source code for Bitcoin at Sourceforge2 (Swan 2015), thus ensuring that Bitcoin would be open source software (Lakhani & Von Hippel 2003). While outlining the principles of Bitcoin, Nakamoto notes that prior to Bitcoin, electronic payment systems were always dependent on trusted third parties (i.e. financial intermediaries such as Banks or PayPal) to verify that digital transactions were not duplicated, in what is characterized as the “double-spend” problem of electronic payment (Nakamoto 2008, Anceaume et al 2016, Teutsch, Jain & Saxena 2016, Yli-Huumo et al 2016). The Bitcoin system is then put forward as a solution to the double-spend problem, and in turn, to trusted third party intermediation, by offering a solution based on cryptographic signatures instead of trust (Nakamoto 2008, Luu et al 2016). -

Proof-Of-Work Sidechains
Proof-of-Work Sidechains Aggelos Kiayias1 and Dionysis Zindros2 1 University of Edinburgh and IOHK 2 National and Kapodistrian University of Athens and IOHK October 30, 2018 Abstract. During the last decade, the blockchain space has exploded with a plethora of new cryptocurrencies, covering a wide array of dif- ferent features, performance and security characteristics. Nevertheless, each of these coins functions in a stand-alone manner, independently. Sidechains have been envisioned as a mechanism to allow blockchains to communicate with one another and, among other applications, al- low the transfer of value from one chain to another, but so far there have been no decentralized constructions. In this paper, we put forth the first sidechains construction that allows communication between proof- of-work blockchains without trusted intermediaries. Our construction is generic in that it allows the passing of any information between block- chains. It gives rise to two illustrative examples: the “remote ICO,” in which an investor pays in currency on one blockchain to receive tokens in another, and the “two-way peg,” in which an asset can be trans- ferred from one chain to another and back. We pinpoint the features needed for two chains to communicate: On the source side, a proof-of- work blockchain that has been interlinked, potentially with a velvet fork; on the destination side, a blockchain with any consensus mechanism that has sufficient expressibility to implement verification. We model our con- struction mathematically and give a formal proof of security. In the heart of our construction, we use a recently introduced cryptographic primi- tive, Non-Interactive Proofs of Proof-of-Work (NIPoPoWs).