End-To-End Authentication: a First Amendment Hook to the Encryption Debate
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Apple TV Overhauled for Games, Shows, Shopping 9 September 2015
Apple TV overhauled for games, shows, shopping 9 September 2015 focused service Zillow, according to Apple executive Eddie Cue. Siri virtual assistant software built in Apple TV allowed for natural language searches for shows, say by asking for something funny or a certain actor by name. The new Apple TV will launch in late October at a starting price of $149. Apple TV has lagged rivals with similar devices. According to the research firm Parks Associates, Roku leads the US market with a 37 percent market share, to 19 percent for Google Chromecast and 17 Apple Senior Vice President of Internet Software and percent for Apple TV. Amazon's Fire TV devices Services Eddy Cue speaks about the new Apple TV on have 14 percent. September 9, 2015 in San Francisco, California © 2015 AFP Apple on Wednesday unveiled a new streaming television device with voice search, touchscreen remote control and an app store in a challenge to Google, Amazon, and video game console titans. Apple TV was overhauled as people increasingly stream films and television shows on-demand online and turn to mobile applications for entertainment. "Our vision for TV is simple, and perhaps a little provocative," Apple chief executive Tim Cook said at a media event in San Francisco. "We believe the future of television is apps." Apple released a software kit for outside developers, and showed off early versions of Apple TV applications already being crafted by show streaming services Netflix, Hulu, and HBO. Game makers are already working on applications, as are home-sharing service Airbnb and real estate- 1 / 2 APA citation: Apple TV overhauled for games, shows, shopping (2015, September 9) retrieved 26 September 2021 from https://phys.org/news/2015-09-apple-tv-overhauled-games.html This document is subject to copyright. -

Online Platforms and Market Power Part 6: Examining the Dominance of Amazon, Apple, Facebook, and Google Questions for the Recor
Online Platforms and Market Power Part 6: Examining the Dominance of Amazon, Apple, Facebook, and Google Questions for the Record from the Honorable David N. Cicilline, Chairman, Subcommittee on Antitrust, Commercial and Administrative Law of the Committee on the Judiciary Questions for Mr. Tim Cook, CEO, Apple, Inc. 1. You testified that Apple’s apps “go through the same rules” that third-party apps are required to follow. The App Store Guidelines (“Guidelines”) are designed to ensure that the App Store remains a safe and trusted place for consumers to discover and download software for their Apple devices. The Guidelines apply to any app, Apple or third-party, that is available on the App Store in the first instance. a. How many Apple apps are pre-loaded on current iPhone models? The first iPhone included 13 integrated Apple apps. There were no third-party apps available for that iPhone. Apple’s subsequent decision to open the iPhone to third-party app development unleashed a wave of innovation and competition. Thirteen years later, there are more than 1.8 million third-party apps available through the App Store and only about 40 Apple apps integrated into the current iPhone models. Apple’s focus has always been to deliver a great consumer experience out of the box. That is why the iPhone comes with Apple apps like Phone, Notes, Settings, Files, Clock, Tips, Measure, and Reminders to provide basic functionality. In addition, apps like FaceTime, iMessage, Apple Music, TV, and others help differentiate the iPhone in a competitive smartphone market. The few apps that Apple has integrated into the iPhone are a drop in the bucket of the overall app ecosystem. -

Apple TV 4 Est Aussi Capable De Commander Des Fonctions De Base Sur Les Appareils Compatibles CEC
ACTUALITÉS INTERNATIONAL Mis à jour le 23.11.2015 à 15h29 | Publié le 23.11.2015 à 16h00 Test 5 choses à savoir sur l’Apple TV Lors de sa présentation à San Francisco en septembre, Apple avait déclaré que la quatrième génération de l’Apple TV représentait l’avenir de la télévision. Vraiment ? « Vanity Fair » a testé l’appareil pour se faire une idée. Voici ce qu’il faut retenir. Par Jérémy Patrelle. 1. L’APPLE TV N’EST PAS UNE TÉLÉVISION Cela paraîtra surperflu à certains d’entre vous mais précisons d’emblée que l’Apple TV n’est pas une télévision mais un petit boitier carré aux bords arrondis de 3,5 cm de haut et 9,8 cm de côté, pour 425 grammes. Il renferme un système permettant de profiter de services culture-loisirs (voir des film et séries, écouter de la musique, jouer aux jeux vidéo) et de connecter des objets high-tech type smartphones, tablettes, ou ordinateurs via l’Internet sans fil : le Wi-Fi. Il faut donc une télévision au sens « petite lucarne » du terme pour profiter de ses bienfaits. Une fois ceci intégré, cela roule tout seul. En moins de 20 minutes, l’installation se fait sans le moindre souci. Une prise secteur, une autre HDMI sur le téléviseur et le tour est joué. Celles et ceux qui ont un iPhone pourront le jumeler en dix secondes en l’approchant du boîtier, transférant ainsi toutes leurs données (comme les mots de passe notamment) sur le système. Pratique. Tout comme la nouvelle télécommande, redessinée, qui est dotée d’un trackpad en haut, ce qui offre une navigation très fluide à base de clics et de swipes délicats. -

Breaking Down Imessage's End-To-End Encryption, and How It
Breaking Down iMessage’s End-to-End Encryption, and How It Got Hacked in iOS 9.3 Xiaoyu Shi Mentor: Ming Chow Part I: Abstract iMessage, as an instant messaging service developed by Apple Inc., is the default messaging application on both iOS and OS X devices. Due to the fact that it is costless and that it is convenient for sending attachments, most users of Apple devices have been using iMessage instead of Short Message Service, or “text messages”. Earlier this year, Eddie Cue, Apple’s senior VP of Internet Software and Services, has disclosed that an many as 200,000 iMessages could be exchanged per second [1]. Besides that, although iMessage is not open source, Apple has published documents asserting that its end-to-end encryption has made iMessage one of the safest means of communication [2]. However, recent concerns of iMessage security have been raised following the discovery of an iMessage security flaw that allows third parties to decrypt attachments to iMessages, like images and videos, if the raw encrypted data has been intercepted. This paper will focus on Apple’s security specifications and its promises to the users, how the end-to-end encryption of iMessage is conducted, and dive into the topic concerning how this vulnerability of iMessage was found. [1] Apple says people send as many as 200,000 iMessages per second http://www.businessinsider.com/eddy-cue-200k-imessages-per-second-2016-2 [2] https://www.apple.com/business/docs/iOS_Security_Guide.pdf 1 Part II: Background 1. Statistics and status quo of Apple devices and iMessage a. -

Apple TV: Fast and Fun, but with Limits
FRIDAY Technology SEPTEMBER, 2015 11 Hands-on with the new Apple TV: Fast and fun, but with limits An Apple TV set-top box is seen in the demo area after a Apple special event. — AFP/AP photos By Janko Roettgers comes with a microphone button that initiates voice control, and two integrated microphones-one to actually fter announcing the new Apple TV at a press take voice commands, and one to monitor for and filter event in San Francisco Wednesday, Apple gave out background noise, like actors speaking on TV. Ajournalists some hands-on time. I had just a few Using voice to control Apple TV worked fairly well dur- minutes to actually try the device myself, and Apple ing my brief hands-on test, which says something: My deliberately didn’t show off some features, but I still got German accent tends to throw off voice recognition sys- some first impressions about Apple TV’s strengths, and tems, but Siri had no problems searching for foreign its potential weaknesses. comedies when asked to do so. Siri on Apple TV is also capable of handling multiple Here’s what using the new Apple TV is like: connected search queries, making it possible to search It’s all about Siri. Apple clearly has turned Siri into the for Adam Sandler movies, and then follow up with a sec- centerpiece of the new Apple TV. The remote control ond query for “just the good ones”-something Siri deter- Apple CEO Tim Cook discusses the Apple TV product advancements during the Apple Eddy Cue, senior vice president of Internet Software, discusses the Apple TV. -

Apple TV EST Agreement 03-21-07.Pdf
iTunes Store c/o Apple Inc. 1 Infinite Loop, M/S: 3-ITMS Cupertino, CA 95014 Senior Management: Royalties: Eddy Cue, VP, iTunes [email protected] [email protected] (512) 674-2456 (408) 974-3484 Legal/Business Affairs: Content Operations, Production & Kevin Saul, Associate General Design: Counsel Robert Kondrk, Director Design [email protected] and Production (408) 974-8849 direct dial [email protected] (408) 253-0186 fax (408) 974-6840 Matt Railo, Senior Counsel Music Programming, iTunes Radio, [email protected] Store Promotions: (408) 974-3504 direct dial Alex Luke, Director of Music (408) 974-9105 fax Programming & Label Relations [email protected] Matt Burrows, Senior Counsel (408) 974-0805 [email protected] (408) 974-1588 direct dial Marketing & Promotions: (408) 974-9105 fax Matt Fischer, Sr. Music Mktg. Mgr. Contract Administration: [email protected] Lorrie Bossie, Contract Administrator (408) 974-0828 [email protected] (408) 974-3675 direct dial Technical: (408) 974-9105 fax Brian Larson, [email protected], (408) 974-9016 Sony Pictures Television Inc. 2 Apple Inc. Rev. 3-20-07 CONFIDENTIAL DIGITAL VIDEO DOWNLOAD DISTRIBUTION AGREEMENT This Agreement (as hereinafter defined) is by and between Apple Inc. ("APPLE"), having its principal place of business at 1 Infinite Loop, Cupertino, California 95014, and Sony Pictures Television Inc. (“SPT”), having its principal place of business 10202 W. Washington Bl., Culver City, California 90232, and is entered into as of the date this Agreement set forth below and is effective once signed by both APPLE and SPT (the "Effective Date"). WHEREAS, APPLE desires to distribute downloads of certain Videos (as hereinafter defined) and other audio-visual content made available by SPT hereunder; and WHEREAS, SPT is willing to allow the distribution of Video downloads of certain such audio-visual content, as set forth herein. -
Should Eddy Cue Take Apple to Hollywood?” Student Case Discussion
“SHOULD EDDY CUE TAKE APPLE TO HOLLYWOOD?” STUDENT CASE DISCUSSION Eddy Cue, just back from a high-profile trip to the had not been particularly pleased with the candor 2018 South by Southwest conference in Austin, expressed while in Austin. Cook had asked Cue to Texas, was reflecting on a press conference he reconsider how Apple could strengthen its position had given while there. During the presser, he had in the content creation and distribution battle. They been asked if Apple had new plans to strengthen were scheduled to meet in 24 hours, and Cue did its position in the delivery and creation of original not have a clear strategy in mind. content. His blunt answer has been picked up by In media streaming, Apple had gone from first place many media outlets. in streaming device sales in 2015 to second place in 2018. Also, Apple’s position appeared weak in DISCUSSION CASE STUDENT terms of programming expenses; it ranked 11th with about $1B per year, with most of it for content acquired (but not created) by Apple. Just like the press had done in Austin, Cook had asked whether a bold move was needed. Cook was worried that Apple would fall behind Netflix and Amazon. What v should be done to ensure that content creation and content delivery could be better leveraged with Apple’s commercial successes in devices? In recent strategy meetings, Cook had said that although iPhones were the backbone of Apple’s innovations, the slowdown in iPhone sales was a concern. Although Apple had introduced successful products, including the Apple Watch and AirPods, the company’s attempt to compete with Amazon’s Alexa by introducing the HomePod had met only limited success. -

Apple Music Brings Change to Streaming, but Is It Enough? 9 June 2015, Byryan Nakashima
Apple Music brings change to streaming, but is it enough? 9 June 2015, byRyan Nakashima It could become one more thing that keeps current iPhone and iPad users inside the Apple ecosystem, while enticing others in. Here's a look at some of the major aspects of Apple Music. ___ INTEGRATION WITH SIRI Subscribers will be able to ask Siri, Apple's mobile digital assistant, all sorts of unusual questions about music, and have any of millions of tunes play back in response. Beats co-founder and Apple employee Jimmy Iovine speaks at the Apple Worldwide Developers Conference Executive Eddy Cue demonstrated a few of them in San Francisco, Monday, June 8, 2015. The maker of iPods and iPhones announced Apple Music, an app that Monday, including asking for a playlist of the top 10 combines Beats 1, a 24-hour, seven-day live radio hits in the alternative genre, asking for a song from station, with an on-demand music streaming service. the soundtrack of the movie "Selma," and even (AP Photo/Jeff Chiu) asking for the top song from May 1982. (It was Joan Jett & the Blackheart's "I Love Rock 'n' Roll.") Using Siri's artificial intelligence and one's voice When Apple launches its Apple Music streaming could come in handy when working out, going on a service at the end of June, it will affect things big jog or driving a car that comes with Apple's Car and small in the music industry. Play. Hundreds of millions of iPhone and iPad users in ___ more than 100 countries will get to try the $10-per- month service for free for the next three months REAL RADIO, OVER THE INTERNET when it is pushed to their devices with a free upgrade. -

Trial Exhibit PX-0613 : E-Mail from Eddy Cue to Carolyn Reidy Re "Thanks" : U.S. V. Apple, Et
Plaintiffs' Exhibit US v Apple 12- cv-02826 PX-0613 From: Eddy Cue <[email protected]> Sent: Tuesday, January 26, 20 10 l 1: 16 AM To: Reidy, Carolyn <[email protected]> Subject: Re: Thanks The PR contact is Katie Cotton [email protected] 408·974- eddy On Jan 26, 20 10 , at 11: 03 AM, Reidy, Carolyn wrote: >Eddy: l think I will go into withdrawal now that 1 don't have to discuss exhibit A or Clause G(f) anymore! > > I lake it from the Lime of this email that you didn't get out of New York last night-either that or you are an early riser in California 1f you didn't get out, I hope that's good news for our industry, and not because you ran into airport delays > > Ttoo believe this will be a great moment in book publishing. I'm hoping that Wednesday's event will erase any lingering feeling of failure at not having been able to move you further out of your "box'' (she said dryly) and will sustain us as we move through the next steps in this process of changing the industry. > > 1 dtd alert Stephen K ing yesterday afternoon that UNDER THE DOME might be featured from the stage tomorrow (we do like him lo be fully aware of anything happening involving him) and be was extremely pleased to hcru that. He will also be ready with a positive comment (nbout beinghoppy to sec books made even more available from such a good retailer--he's u huge iTunes fan) if the press goes to him for a comment (Lhc second reason I alerted bim)--thcy usually do try wld get comments from him on anything that is digital related when his book(s) arc even tangentially mentioned > >I lookforwarcl to seeing you on Wednesday, too > >You were going to send me a PR name I can pass on? > >Carolyn > > -·---0riginal Message----- > From. -

Apple Touts $1.8 Bn in Holiday Sales at App Store 6 January 2021
Apple touts $1.8 bn in holiday sales at App Store 6 January 2021 Videoconferencing app Zoom and the Disney+ app for the entertainment giant's streaming television service were listed among the most downloaded apps at the App Store last year, as the pandemic had people tending to work, play, and education from home. App Store revenue during the holiday week was driven strongly by games, with hot titles including "Among Us" and "Roblox," the Cupertino-based company said. App Store sales set a new single-day record of over $540 million on New Year's Day, according to Apple. Apple said spending for mobile apps surged in 2020, especially during the year-end holiday season "Apps have become more essential than ever," Apple said in the post. "Developers found new ways to keep people Apple on Wednesday said a dizzying $1.8 billion connected, help them learn and work from home, was spent on digital goods and services at its App stay fit and well, and provide much-needed Store between Christmas Eve and the end of entertainment." December. Developers have earned more than $200 billion at Word of the stellar holiday week at the exclusive the App Store since it launched 12 years ago, gateway onto Apple devices comes as the iPhone according to Apple. maker defends itself against concerns that its control over the App Store is monopolistic. But Apple's policies have been coming under increasing scrutiny. "Now more than ever before, customers around the world have found inspiration and value in the The news comes with Apple and the developer of breadth and quality of Apple's services, which have the blockbuster game Fortnite, Epic Games, impacted their lives in big and small ways every fighting in court over whether the California-based day," Apple senior vice president of internet company's tight control of its App Store. -
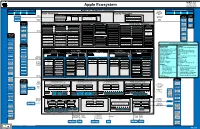
Apple Ecosystem Y
Apple Inc. One Apple Park Way Cupertino, CA 95014 Apple Ecosystem Phone: (408) 996-1010 www.apple.com Outside Relationships Apple Inc. (California Corporation) Securities Outside Relationships Regulation and Regulators Capital Suppliers Customers NASDAQ Listing Customers Suppliers Capital Regulators Debt Structure Equity Structure Rules Bond Debt ( $107B @ 9/28/19) Credit Ratings: Aa1 (Moody’s), AA+ (S&P) Equity Securities Public Debt Financing Common Stock Significant Regulators Common Stock (12.6 Billion Authorized; Holders Senior Floating Senior Fixed Rate Notes ($97.5B), Repurchases Shareholders 4.443 Million Shares Outstanding) US Securities Commercial Rate Notes bearing interest at 0.875% to 3.6% Vanguard Commercial Commercial Paper (9- Equity and Paper ($4.25B) and maturing 2022 to 2042 Group Banks months or less) ($6 billion) $175 Billion Share Repurchase Program Capital Exchange (7.36%) Commission Professional Berkshire Services Governance Human Resources Sales and Marketing Finance and Accounting Corporate Matters Hathaway The NASDAQ Board of Directors Research & (5.6%) Hiring / Training Legal Stock Market Ernst & Young Advertising Budget Support Development Arthur D. Levinson (C) Albert Gore Jr. (C, N) Susan L. Wagner (N, A) Real Estate IP Management BlackRock (Auditors) New Technologies Pension Plans Retail Accounts Internal Audit Fund TBWA/Media Tim Cook Andrea Jung (C, N) Ronald D. Sugar (A) Transactions Subsidiary Management Existing Product Advisors Professional Compensation E Commerce Accounting Arts Lab Enhancements -

Apple E-Mail Thread W/ Phillip Shoemaker, Philip Schiller, Eddy
Subject: Re: Reuters: Opera says to introduce faster browser for iPhone From: "Phillip Shoemaker" Confidential Received(Date): Wed, 10 Feb 2010 16:12:32 +0000 To: "Natalie Harrison" Confidential Cc: "Phil Schiller" I Confidential 1, "Greg Joswiak" Confidential ,"Eddy Cue" 1 1 "Ron Okamoto" Confidential 1,"Katie Cotton" Confidential I, "Natalie Kerris" Confidential 1,"Trudy Muller" Confidential Date: Wed, 10 Feb 2010 16:12:32+0000 It is unlikely that this Opera release is using our webkit, which is required for all browsers on our platform. Usually we give non-compliant browsers a quick rejection, but in this case I'll bring it to the ERB when the app gets submitted (and give PR a heads-up). On Feb 10, 2010, at 7: 11 AM, Natalie Harrison wrote: FYI Opera Mobile has issued a press release inviting media to see 'an exclusive preview of Opera Mini for iPhone' at Mobile World Congress. They claim the browser is up to six times faster than Safari and can cut data traffic by up to 90 percent. Opera co-founder Jon von Tetzchner says: "We have not submitted it yet to the Apple App Store. However, we hope that Apple will not deny their users a choice in Web browsing experience." Reuters Opera says to introduce faster browser for iPhone http://www.reuters.com/article/idUSLDE6190JO20100210 Wired Opera Mini on iPhone Next Week http://www.wired.com/gadgetlab/2010/02/overa-mini-on-iphone-next-week/ PC World Opera to Reveal Alternative IPhone Browser Next Week http://www.Dcworld.com/article/188990/overa to reveal alternative iphone browser next week.html Natalie Harrison iPhone PR HIGHLY CONFIDENTIAL -- SENSITIVE BUSINESS INFORMATION HJC-APPLE-011207 mobile: Confidential | Confidential www.apple.com HIGHLY CONFIDENTIAL -- SENSITIVE BUSINESS INFORMATION HJC-APPLE-011208.