Privacy on the Internet in the Digital Era
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Since Sliced Bread?
Douglas A. Hamilton WINDOWS NT NT: The Greatest Thing Since Sliced Bread? T'S OFFICIAL. Windows unlike OS/2, is not the only product in the family. Right around the corner is the NT is finally out of the Chicago technology that Microsoft will be using in DOS 7.0 and Windows 4.0. Earli oven. The pricing has est betas for software developers are I scheduled for early fall and products been set and delivery dates based on it should be out in 1994. Chicago is a rewrite of the same Win32 have been promised. Those API (application programming interface) seen on NT. Compared with NT, it leaves promises (back in May) out the security (how many of us need government-certified C2 security on our were that the base system personal machines?), portability to RISC processors and the OS/2 character-mode would ship within 60 days and POSIX subsystems. And it wouldn't surprise me if Unicode support were trimmed out or if the networking were and the Advanced Server version would ship 30 days unbundled. What Chicago leaves in is 32- bit flat virtual memory, preemptive multi later. So there's every chance that by the time you read tasking, threads, pipes and semaphores all the really good stuff in Win32. That be this, there'll be piles of Windows NT packages at your comes Windows 4.0. Subtract the graphi cal user interface and you get DOS 7.0. local computer store. Is there anyone left who wonders why developers are so excited about NT? It's After a false rumor that Microsoft might price NT at not just because NT is expected to do ex tremely well. -

System Requirements for LWC Connect to Learning
System Requirements for LWC Connect to Learning Run the Adobe Connect Diagnostic to see if you meet the Flash, connection, and add-in minimum requirements https://na3cps.adobeconnect.com/common/help/en/support/meeting_test.htm MINIMUM COMPUTER SYSTEM REQUIREMENTS: Windows • 1.4GHz Intel® Pentium® 4 or faster processor (or equivalent) for Microsoft® Windows® XP, Windows 7 or Windows 8 • Windows 8.1 (32-bit/64-bit), Windows 8 (32-bit/64-bit), Windows 7 (32-bit/64-bit), Windows XP • 512MB of RAM (1GB recommended) for Windows XP, Windows 7 or Windows 8 • Microsoft Internet Explorer 8, 9, 10, 11; Mozilla Firefox; Google Chrome • Adobe® Flash® Player 11.2+ Mac OS • 1.83GHz Intel Core™ Duo or faster processor • 512MB of RAM (1GB recommended) • Mac OS X 10.7.4, 10.8, 10.9 • Mozilla Firefox; Apple Safari; Google Chrome • Adobe Flash Player 11.2+ Linux • Ubuntu 12.04; Red Hat Enterprise Linux 6; OpenSuSE 12.2 • No Add-in support for Linux. Users on Linux can attend meetings in the browser. • Mozilla Firefox • Adobe Flash Player 11.2+ Mobile • Apple supported devices: iPhone 5S, iPhone 5, iPhone 4S, iPad with Retina display, iPad 3, iPad 2, iPad mini, and iPod touch (4th & 5th generations) • Apple supported OS versions summary: iOS 6 and higher • Android supported devices: Motorola DROID RAZR MAXX, Motorola Atrix, Motorola Xoom, Samsung Galaxy Tab 2 10.1, Samsung Galaxy S3 & S4, Nexus 7 tablet • Android supported OS versions summary: 2.3.4 and higher 1 ADDITIONAL REQUIREMENTS • Latest version of Adobe Flash Player installed o Download latest version at http://get.adobe.com/flashplayer/ . -

Windows NT Architecture Previous Screen Gilbert Held Payoff Windows NT Is a Sophisticated Operating System for Workstations and Network Servers
50-30-19 Windows NT Architecture Previous screen Gilbert Held Payoff Windows NT is a sophisticated operating system for workstations and network servers. This article helps network managers to understand the communications capability of workstations and servers running on Windows NT, and data base administrators to determine the suitability of this platform for a structured query language (SQL) data base server. Introduction Windows NT is a 32-bit, preemptive multitasking operating system that includes comprehensive networking capabilities and several levels of security. Microsoft markets two version of Windows NT: one for workstations—appropriately named Windows NT Workstation—and a second for servers—Windows NT Server. This article, which describes the workings of the NT architecture, collectively references both versions as Windows NT when information is applicable to both versions of the operating system. Similarly, it references a specific version of the operating system when the information presented is specific to either Windows NT Workstation or Windows NT Server. Architecture Windows NT consists of nine basic modules. The relationship of those modules to one another, as well as to the hardware platform on which the operating system runs, is illustrated in Exhibit 1. Windows NT Core Modules Hardware Abstraction Layer The hardware abstraction layer (HAL) is located directly above the hardware on which Windows NT operates. HAL actually represents a software module developed by hardware manufacturers that is bundled into Windows NT to allow it to operate on a specific hardware platform, such as Intel X86, DEC Alpha, or IBM PowerPC. HAL hides the specifics of the hardware platform from the rest of the operating system and represents the lowest level of Windows NT. -

Sourcefire White Paper
And Its Role in the Security Model www.sourcefire.com June 2002 Sourcefire, Inc. 7095 Samuel Morse Drive Suite 100 Columbia, MD 21046 410.290.1616 | 410.290.0024 TABLE OF CONTENTS Table of Contents ............................................................................................................2 Open Source Software: OSS...........................................................................................3 What is OSS?..........................................................................................................................3 History.....................................................................................................................................4 Opinions on OSS.....................................................................................................................4 Arguments in favor of OSS ......................................................................................................5 Security, Stability, and Cost .......................................................................................................................5 Standards, Immediacy, and Lack of Restrictions......................................................................................7 Arguments Against OSS..........................................................................................................7 Status Quo and Security.............................................................................................................................8 Poor Packaging and Support .....................................................................................................................9 -

Supported Server-Side Configuration
Server and hosting requirements Supported server-side configuration Supported operating systems: Windows 7 Service Pack 1 (32bit or 64bit) Windows 8 or 8.1 (32bit or 64bit) Windows 10 (32bit or 64bit) Windows Server versions: 2008 R2 Service Pack 1, 2012, 2012 R2 We recommend that you install the following components on the computer where you want to run Kentico. If you do not install these components on your computer before installing Kentico, the Installer is capable of downloading and installing them or their suitable alternatives on its own (except for the Visual Studio built-in server). In such cases, your computer must be connected to the Internet. Microsoft .NET Framework 4.5 or 4.6. Microsoft Internet Information Services (see the table below) or Visual Studio 2012/2013/2015 built-in web server. Microsoft SQL Server 2008 R2, 2012, 2014 (including the free SQL Server Express Edition 2008 R2/2012/2014). The collation set for the SQL server must be case-insensitive. Internet Information Services overview The following table lists instructions on how to install different versions of IIS on different operating systems. Internet Information Services version Operating system Details and installation instructions IIS 7.0 Windows Vista not supported Windows Server 2008 IIS 7.5 Windows 7 SP1 IIS 7 Installation and Deployment Windows Server 2008 R2 SP1 IIS 8.0 Windows 8 Installing IIS on Windows Server 2012 Windows Server 2012 IIS 8.5 Windows 8.1 Installing IIS 8.5 Windows Server 2012 R2 IIS 10 Windows 10 Same process as IIS 8+ For the Kentico -

Models Step 1: Identify Which Version of the Windows Phone Operating
Nokia Lumia – All Models (Excluding models 710 and 800) Step 1: Identify which version of the Windows Phone operating system is installed on your phone: 1. Go to your App list. 2. From there, tap “Settings” > “About” > “More info”. 3. The “Software” section indicates which version of the Windows Phone operating system is in use. a. If your phone is currently running Windows Phone 7, proceed to page 2 for instructions on how to wipe your device. b. If your phone is currently running Windows Phone 8, 8.1, or 10, proceed to page 3 for instructions on how to wipe your device. ______________________________________________________________________________ Nokia Lumia - Tous les modèles (À l'exclusion des modèles 710 et 800) Étape 1: Déterminer la version du système d'exploitation Windows Phone installée sur votre téléphone: 1. Accédez à votre liste d’applications. 2. Presse « Paramètres » > « À propos » > « Plus d'info ». 3. La section « Logiciel » indique le nom de la version du système d'exploitation Windows Phone. a. Si votre téléphone utilise actuellement Windows Phone 7, aller à la page 2 pour obtenir des instructions sur la façon de réinitialiser votre téléphone. b. Si votre téléphone utilise actuellement Windows Phone 8, 8.1, ou 10, aller à la page 4 pour obtenir des instructions sur la façon de réinitialiser votre téléphone. Nokia Lumia (Windows 7.5) Model Numbers: 610, 900 The following instruction will give you all the information you need to remove your personal information from your phone. Before recycling your device please also remember to: The account for the device has been fully paid and service has been deactivated. -

Installing the IPM Client on Windows NT
CHAPTER 6 Installing the IPM Client on Windows NT IPM supports running only the IPM client software on a Windows NT system. However, you can run the IPM client on Windows NT with an IPM server that resides on a different operating system platform such as Sun Solaris. The IPM client software can be installed from the CD-ROM or it can be downloaded for installation using the IPM server’s web server. This chapter provides the following information about installing the IPM client software on Windows NT: • Requirements for the IPM Client on Windows NT on page 6-2 • Installing the IPM Client on Windows NT from the CD-ROM on page 6-3 • Installing the IPM Client on Windows NT Using the Web Server on page 6-4 • Verifying the IPM Client Installation on Windows NT on page 6-6 • Modifying the IPM Client Configuration on Windows NT on page 6-7 • Uninstalling the IPM Client on Windows NT on page 6-10 Installing the IPM Client on Windows NT 6-1 Requirements for the IPM Client on Windows NT Requirements for the IPM Client on Windows NT The following hardware and software is required to install the IPM client on a Windows NT system: • Windows NT version 4.0 with Service Pack 3 Note IPM software release 2.0 has not been tested with Windows NT Service Pack 4. • 64 MB RAM minimum (128 MB recommended) • 30 MB hard disk space Before you install the IPM client on a workstation running Windows NT, you should know the following information: • IPM server port number for the Naming server (the default is 44342) • Name of the host where the IPM server software is installed Tips The IPM server port number is obtained using the pkgparam -v CSCOcwbS | grep OSAGENT_PORT command on the Solaris server system. -

Flashboot User Manual
FlashBoot User Manual © 2015 Mikhail Kupchik Contents 3 Table of Contents Foreword 0 Part I Introduction 5 1 Product................................................................................................................................... Overview 5 2 Why USB................................................................................................................................... Flash Disks? 5 3 Why FlashBoot?................................................................................................................................... 6 4 System................................................................................................................................... Requirements 7 5 Limitations................................................................................................................................... of Demo Version 8 6 Demo Version................................................................................................................................... -> Full Version 8 7 Support................................................................................................................................... & Feedback 8 Part II CD/DVD to USB conversions 9 1 Install ...................................................................................................................................full Win8/8.1/10 -> USB [BIOS mode] 9 2 Install................................................................................................................................... full -

Level One Benchmark Windows NT 4.0 Operating Systems V1.0.5
Level One Benchmark Windows NT 4.0 Operating Systems V1.0.5 Copyright 2003, The Center for Internet Security www.cisecurity.org Page 2 of 32 Terms of Use Agreement Background. CIS provides benchmarks, scoring tools, software, data, information, suggestions, ideas, and other services and materials from the CIS website or elsewhere (“Products”) as a public service to Internet users worldwide. Recommendations contained in the Products (“Recommendations”) result from a consensus-building process that involves many security experts and are generally generic in nature. The Recommendations are intended to provide helpful information to organizations attempting to evaluate or improve the security of their networks, systems and devices. Proper use of the Recommendations requires careful analysis and adaptation to specific user requirements. The Recommendations are not in any way intended to be a “quick fix” for anyone’s information security needs. No representations, warranties and covenants. CIS makes no representations, warranties or covenants whatsoever as to (i) the positive or negative effect of the Products or the Recommendations on the operation or the security of any particular network, computer system, network device, software, hardware, or any component of any of the foregoing or (ii) the accuracy, reliability, timeliness or completeness of any Product or Recommendation. CIS is providing the Products and the Recommendations “as is” and “as available” without representations, warranties or covenants of any kind. User agreements. By using the Products and/or the Recommendations, I and/or my organization (“we”) agree and acknowledge that: 1. No network, system, device, hardware, software or component can be made fully secure; 2. -

Windows 95 & NT
Windows 95 & NT Configuration Help By Marc Goetschalckx Version 1.48, September 19, 1999 Copyright 1995-1999 Marc Goetschalckx. All rights reserved Version 1.48, September 19, 1999 Marc Goetschalckx 4031 Bradbury Drive Marietta, GA 30062-6165 tel. (770) 565-3370 fax. (770) 578-6148 Contents Chapter 1. System Files 1 MSDOS.SYS..............................................................................................................................1 WIN.COM..................................................................................................................................2 Chapter 2. Windows Installation 5 Setup (Windows 95 only)...........................................................................................................5 Internet Services Manager (Windows NT Only)........................................................................6 Dial-Up Networking and Scripting Tool....................................................................................6 Direct Cable Connection ..........................................................................................................16 Fax............................................................................................................................................17 Using Device Drivers of Previous Versions.............................................................................18 Identifying Windows Versions.................................................................................................18 User Manager (NT Only) .........................................................................................................19 -

Lumia with Windows 10 Mobile User Guide
User Guide Lumia with Windows 10 Mobile Issue 1.1 EN-US About this user guide This guide is the user guide for your software release. Important: For important information on the safe use of your device and battery, read “For your safety” and “Product and safety info” in the printed or in-device user guide, or at www.microsoft.com/mobile/support before you take the device into use. To find out how to get started with your new device, read the printed user guide. For the online user guidance, videos, even more information, and troubleshooting help, go to support.microsoft.com, and browse to the instructions for Windows phones. You can also check out the support videos at www.youtube.com/lumiasupport. Moreover, there's a user guide in your phone – it's always with you, available when needed. To find answers to your questions and to get helpful tips, tap Lumia Help+Tips. If you’re new to Lumia, check out the section for new users. For info on Microsoft Privacy Statement, go to aka.ms/privacy. © 2016 Microsoft Mobile. All rights reserved. 2 User Guide Lumia with Windows 10 Mobile Contents For your safety 5 People & messaging 64 Get started 6 Calls 64 Turn the phone on 6 Contacts 68 Lock the keys and screen 7 Social networks 73 Charge your phone 7 Messages 74 Your first Lumia? 10 Email 78 Learn more about your phone 10 Camera 83 Set up your phone 10 Open your camera quickly 83 Update your apps 11 Camera basics 83 Explore your tiles, apps, and settings 12 Advanced photography 86 Navigate inside an app 14 Photos and videos 88 Use the touch screen -
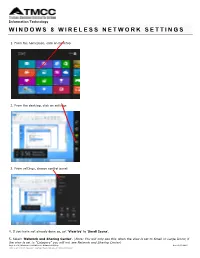
Windows 8 Wireless Network Settings
Information Technology WINDOWS 8 WIRELESS NETWORK SETTINGS 1. From the homepage, click on Desktop 2. From the desktop, click on settings 3. From settings, choose control panel 4. If you have not already done so, set ‘View by’ to ‘Small Icons’. 5. Select ‘Network and Sharing Center’. (Note: You will only see this when the view is set to Small or Large Icons; if the view is set to “Category” you will not see Network and Sharing Center) Page 1 of 6; Windows 8 OS Wireless Network Settings Rev.: 2/5/2013 TMCC is an EEO/AA institution. See http://eeo.tmcc.edu for more information. 6. Click ‘Set up a new connection or network’. 7. Click ‘Manually connect to a wireless network’. Then click ‘Next’. 8. Fill in the appropriate Network name: a. For Students: TMCC-Student b. For Staff: TMCC-Admin Security 9. Select ‘WPA2-Enterprise’ from the security type drop-down box. 10. Select ‘AES’ from the encryption type drop-down box. 11. Leave the Security key field blank. 12. Make sure ‘Connect even if the network is not broadcasting’ box is checked. 13. Below is an example of what is should look like for students: 14. Click ‘Next’. 15. Click ‘Change connection settings’ 16. Make sure both 'Connect automatically when this network is in range' and 'Connect even if the network is not broadcasting its name (SSID)' are selected. Page 2 of 6; Windows 8 OS Wireless Network Settings Rev.: 2/5/2013 TMCC is an EEO/AA institution. See http://eeo.tmcc.edu for more information.