Survival Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Mcafee Labs Threats Report August 2014
McAfee Labs Threats Report August 2014 Heartbleed Heartbleed presents a new cybercrime opportunity. 600,000 To-do lists The Heartbleed vulnerability Lists of Heartbleed-vulnerable exposed an estimated 600,000 websites are helpful to users but websites to information theft. can also act as “to-do” lists for cyber thieves. Unpatched websites Black market Despite server upgrades, many Criminals continue to extract websites remain vulnerable. information from Heartbleed- vulnerable websites and are selling it on the black market. McAfee Phishing Quiz Phishing continues to be an effective tactic for infiltrating enterprise networks. Average Score by Department (percent of email samples correctly identified) Only 6% of all test takers correctly 65% identified all ten email samples as phishing or legitimate. 60% 80% 55% of all test takers fell for at least one of the seven phishing emails. 50% 88% of test takers in Accounting & 0 Finance and HR fell for at least one of the seven phishing emails. Accounting & Finance Human Resources Other Departments The McAfee Phishing Quiz tested business users’ ability to detect online scams. Operation Tovar During Operation Tovar—The Gameover Zeus and CryptoLocker takedown: For CryptoLocker For Gameover Zeus more than 125,000 more than 120,000 domains were blocked. domains were sinkholed. Since the announcement of Operation Tovar: 80,000 times Copycats ****** McAfee Stinger, a free ****** are on the rise, creating tool that detects and ****** new ransomware or removes malware financial-targeting (including Gameover Zeus malware using the leaked and CryptoLocker), was Zeus source code. downloaded more than 80,000 times. McAfee joined global law enforcement agencies and others to take down Gameover Zeus and CryptoLocker. -

The Internet Organised Crime Threat Assessment (IOCTA) 2015
The Internet Organised Crime Threat Assessment (IOCTA) 2015 2 THE INTERNET ORGANISED CRIME THREAT ASSESSMENT (IOCTA) 2015 THE INTERNET ORGANISED CRIME THREAT ASSESSMENT (IOCTA) 2015 3 TABLE OF FOREWORD 5 CONTENTS ABBREVIATIONS 6 EXECUTIVE SUMMARY 7 KEY FINDINGS 10 KEY RECOMMENDATIONS 12 SUGGESTED OPERATIONAL PRIORITIES 15 INTRODUCTION 16 MALWARE 18 ONLINE CHILD SEXUAL EXPLOITATION 29 PAYMENT FRAUD 33 SOCIAL ENGINEERING 37 DATA BREACHES AND NETWORK ATTACKS 40 ATTACKS ON CRITICAL INFRASTRUCTURE 44 CRIMINAL FINANCES ONLINE 46 CRIMINAL COMMUNICATIONS ONLINE 50 DARKNETS 52 BIG DATA, IOT AND THE CLOUD 54 THE GEOGRAPHICAL DISTRIBUTION OF CYBERCRIME 57 GENERAL OBSERVATIONS 62 APPENDICES 67 A1. THE ENCRYPTION DEBATE 67 A2. AN UPDATE ON CYBER LEGISLATION 70 A3. COMPUTER CRIME, FOLLOWED BY CYBERCRIME FOLLOWED BY …. ROBOT AND AI CRIME? 72 4 THE INTERNET ORGANISED CRIME THREAT ASSESSMENT (IOCTA) 2015 FOREWORD These include concrete actions under the three main mandated Threat Assessment (IOCTA), the annual presentation of the areas – child sexual exploitation, cyber attacks, and payment I am pleased to present the 2015 Internet Organised Crime fraud – such as targeting certain key services and products Centre (EC3). offered as part of the Crime-as-a-Service model, addressing the cybercrime threat landscape by Europol’s European Cybercrime growing phenomenon of live-streaming of on-demand abuse of children, or targeted actions with relevant private sector partners ofUsing cybercrime the 2014 for report the asperiod a baseline, under this consideration. assessment Itcovers offers the a cross-cutting crime enablers such as bulletproof hosting, illegal viewkey developments, predominantly changes from a lawand enforcement emerging threats perspective in the based field tradingagainst onlinesites on payment Darknets fraud. -

A Step Ahead Focus on Security
A STEP AHEAD FOCUS ON SECURITY IN THIS ISSUE: HOW MCAFEE UNCOVERED A CYBERCRIME GANG AND AIDED IN THEIR ARREST THE FUTURE OF CYBERSECURITY BIG THREATS, CRITICAL MOVES & ONGOING TRENDS WHAT WE SHOULD AND SHOULD NOT DO IN 2018 INSIGHTS AND TIPS FROM THE WORLD’S MOST FAMOUS FORMER HACKER Think you’re secure? ThinkWhy you you’re may secure? be surprised. Why you may be surprised. With more than 50,000 security threats emerging each day, IT managers like you have a challenging job. Even with carefully crafted policies, the biggest threat Over half of U.S. may come from inside your organization. Firewalls, antivirus software, rules and employees who regulations can only do so much. The final barrier is employee behavior and, when print, scan or you’re waging the war against laid-back attitudes, culprits can be everywhere. copy confidential information never, or rarely, worry that Did you know? those items will remain secure. Intellectual % property (IP) 98 theft has reached Why you should of compromises took “unprecedented” just minutes, or less, levels, costing the be worried: to perpetrate.1 U.S. an estimated $300B a year.2 54% of workers copy, scan or print Who’s ignoring the rules? confidential work. 87% of employees work 1 in 10 rarely or never 1.5 in 10 are not aware of at a company that has follow the policy. what the security policies are. an IT security policy. % However: 60 of workers are not prompted to enter a password before printing. What can you do? With the right balance of people, processes and technology, Make your IT security policy more than a written you can protect sensitive data wherever it resides. -
2016 ICIT Ransomware Report
Expert research contributed by the following ICIT Fellows: Danyetta Magana (ICIT Fellow – President, Covenant Security Solutions) Igor Baikolov (ICIT Fellow – Chief Scientist, Securonix) Brian Contos (ICIT Fellow – Vice President & Chief Security Strategist, Securonix) John Menkhart (ICIT Fellow – Vice President, Federal, Securonix) George Kamis, (ICIT Fellow – CTO, Forcepoint Federal) Stacey Winn (ICIT Fellow - Senior Product Marketing Manager, Public Sector, Forcepoint) Thomas Boyden (ICIT Fellow – Managing Director, GRA Quantum) Kevin Chalker (ICIT Fellow – Founder & CEO, GRA Quantum) John Sabin (ICIT Fellow – Director of Network Security & Architecture, GRA Quantum) 1 Contents Introduction: .............................................................................................................................................................. 3 Origins of Ransomware: ........................................................................................................................................ 6 Overview of Ransomware: ................................................................................................................................... 8 Types of Ransomware: .......................................................................................................................................... 9 Locker Ransomware: ........................................................................................................................................ 9 Crypto Ransomware: ..................................................................................................................................... -

Held for Ransom
HELD FOR RANSOM DEFENDING YOUR DATA AGAINST RANSOMWARE Topics • What is Ransomware? • Basic Ransomware Operation • A Little History • Ransomware Characteristics • Actual Compromises • Some Help With Recovery • A Plan for Protection www.bleepingcomputer.com 2 What is Ransomware? • Windows ransomware, such as Cryptolocker, Cryptowall, Locky, and Samas, does not bother to steal your critical files (Office documents, photos, videos) as it is much easier to just encrypt them in-place and give you a ransom note. • If the ransom is not paid by its due date, you do not get the decryption key needed to decrypt your files. • Depending on the variant of Ransomware you’ve been infected with, you may be able to recover your files. It’s not just Windows: •Linux.Encoder, which exploits a security vulnerability in the Magneto e-commerce platform. •OS X KeRanger, distributed through compromised www.wysiwygventures.com Transmission BitTorrent client. 3 Basic Ransomware Operation • Infect system via email attachment, Angler exploit kit (0- day Flash exploit), or GameOver Zeus Botnet. • Contact CnC server to generate / receive encryption key. • Perform a depth first search of all disk folders (including network drives), encrypting files with targeted extensions using with one of several algorithms, such as RSA, ECC, AES. • Place ransom notes in all folders where files were encrypted. • Delete malware when encryption is complete and display final ransom note. 4 Basic Ransomware Operation • Depending on which variant of Ransomware a system has been infected with, other activities shown here may also take place: • Deletion of Shadow Volume copies: – "C:\Windows\SYsWOW64\cmd.exe" /C "C:\Windows\Sysnative\vssadmin.exe" Delete Shadows /All /Quiet • Secure deletion of original files after they’ve been encrypted. -

Download Slides (PDF)
WORKING TOGETHER: LE AND PRIVATE SECTOR BOTNET TAKEDOWNS Thomas Grasso (FBI) Alan Neville (Symantec) Working Together: LE and private sector botnet takedowns 1 Agenda Working Together: LE and private sector botnet takedowns 2 What are botnets? Working Together: LE and private sector botnet takedowns 3 Growing resilience of cybercrime networks TRADITIONAL BOTNET PEER TO PEER BOTNET Single point of failure No single point of failure Only one or a few C&C servers Every peer acts as C&C server Vulnerable to takedown & sinkholing Difficult to take down or sinkhole Unsurprisingly, cybercriminals are increasingly moving to P2P infrastructure Working Together: LE and private sector botnet takedowns 4 How we took out half a million ZeroAccess bots ZeroAccess uses highly resilient P2P architecture Each bot acts as a C&C, sinkholing almost impossible Create sinkholes that act like bot peers Inject sinkhole address in peer list and let it propagate ZA Eventually bots only have our sinkhole peer address GAME OVER FOR ZEROACCESS! SYMC ZA Working Together: LE and private sector botnet takedowns 5 Operation Tovar: Takedown of GameOver & Zeus/Crytolocker COLLABORATION BETWEEN LAW ENFORCEMENT AND SECURITY INDUSTRY Flaw in C&C communication is exploited to redirect traffic to servers owned by law enforcement Security industry Infections show signs assists with cleanup of increasing again, providing removal need for ongoing tools action Working Together: LE and private sector botnet takedowns 6 Collaborative Approach to Botnet Takedowns Working Together: LE and private sector botnet takedowns 7 Botnet Threat Focus Cell • A collaborative effort involving government, private sector and academia to combat the botnet threat. -

A Study on Ransomware and Its Effect on India and Rest of the World
Special Issue - 2017 International Journal of Engineering Research & Technology (IJERT) ` ISSN: 2278-0181 NCICCNDA - 2017 Conference Proceedings A Study on Ransomware and its Effect on India and Rest of the World Naveen Kumar C.G Dr.Sanjay Pande M.B Research Scholar, Professor and Head of the Department Bharathiar University GMIT, Davanagere, Coimbatore, Tamilnadu, India Karnataka,India Abstract- - Increased growth of internet technology pave III. TYPES OF CYBER ATTACKS the way to every individual and organizations to access Cyber-attacks are mainly categorized into four types, they the information in touch of fingertip. Almost all the are: organizations are transacting their day to day activities using internet and they are completely depend upon the . Targeted attack internet. Internet is exposed to many type of threats and attacks, it is the responsibility of the stakeholders to Cyber-attacks that are geared at particular organizations, secure their information by these attacks. Right now, services, and individuals to obtain private, technical, and information security is one of the top priority of the institutional information, and other intellectual assets for the organizations and also the individuals. Cyberattack is an purpose of vandalism or monetary gain. offensive type that targets on information systems, infrastructures, and computer networks etc. by a means . APT (Advanced Persistent Threat) of malicious act and destroys or steals the information. This paper is aimed to study the recent attack of A kind of targeted attack geared at a particular entity and ransomware, history of ransomware, its impact on India carried out continuously and persistently using a variety of and rest of the world. -

Magnified Losses, Amplified Need for Cyber-Attack Preparedness
Magnified Losses, Amplified Need for Cyber-Attack Preparedness Distributed by: TrendLabsSM 2014 Annual Security Roundup Contents TREND MICRO LEGAL DISCLAIMER The information provided herein is for general information and educational purposes only. It is not intended and should not be construed to 6 constitute legal advice. The information contained herein may not be applicable to all situations Scale of Impact and Losses Due and may not reflect the most current situation. to Cyber Attacks Intensified Nothing contained herein should be relied on or acted upon without the benefit of legal advice based on the particular facts and circumstances presented and nothing herein should be construed 9 otherwise. Trend Micro reserves the right to modify the contents of this document at any time without 2014 Was the “Year of PoS RAM prior notice. Scrapers” Translations of any material into other languages are intended solely as a convenience. Translation accuracy is not guaranteed nor implied. If any questions arise related to the accuracy of a 13 translation, please refer to the original language official version of the document. Any discrepancies Heartbleed and Shellshock Proved or differences created in the translation are not binding and have no legal effect for compliance or That No Application Was Invulnerable enforcement purposes. Although Trend Micro uses reasonable efforts 15 to include accurate and up-to-date information herein, Trend Micro makes no warranties or representations of any kind as to its accuracy, Online and Mobile Banking Faced currency, or completeness. You agree that access Bigger Security Challenges to and use of and reliance on this document and the content thereof is at your own risk. -

Mcafee Labs Threats Report August 2014 Heartbleed Was the Most Significant Security Event Since the Target Data Breach in 2013
McAfee Labs Threats Report August 2014 Heartbleed was the most significant security event since the Target data breach in 2013. This quarter, our lead topic concerns the Heartbleed About McAfee Labs vulnerability. As most security professionals know, Heart- bleed was the most significant security event since the McAfee Labs is one of the world’s leading sources for threat Target data breach in 2013. McAfee Labs worked around research, threat intelligence, and cybersecurity thought the clock to understand this vulnerability and ensure that leadership. With data from millions of sensors across key relevant McAfee technologies could detect and prevent threats vectors—file, web, message, and network—McAfee Heartbleed-based theft from occurring. Unfortunately, the Labs delivers real-time threat intelligence, critical analysis, bad guys continue to reap rewards from this vulnerability and expert thinking to improve protection and reduce risks. because many websites remain unpatched. www.mcafee.com/us/mcafee-labs.aspx We also detail what we learned from our McAfee Phishing Quiz, which tested business users’ ability to correctly Follow McAfee Labs detect phishing emails. Finally, we document what has happened since international law enforcement agencies, jointly with IT security industry participants including Introduction McAfee, took down the Gameover Zeus and CryptoLocker infrastructure. It was a resounding success, but as we all For many of us, summertime is a chance to relax and expected, the relief was only temporary. enjoy the world’s bounties. But to the bad guys, summer is merely another season, presenting new opportunities Reporting on threats is an ever-changing art. For longtime to steal. -

Dissecting Ransomware to Defeat Threat Actors
Dissecting Ransomware to Defeat Threat Actors March 11, 2020 Dissecting Ransomware to Defeat Threat Actors Today’s web conference is generously sponsored by: https://www.domaintools.com/ Dissecting Ransomware to Defeat Threat Actors Moderator Tim Mackey, Security Strategist Tim Mackey is a principal security strategist within the Synopsys CyRC (Cybersecurity Research Center). He joined Synopsys as part of the Black Duck Software acquisition where he worked to bring integrated security scanning technology to Red Hat OpenShift and the Kubernetes container orchestration platforms. As a security strategist, Tim applies his skills in distributed systems engineering, mission critical engineering, performance monitoring, large-scale data center operations, and global data privacy regulations to customer problems. He takes the lessons learned from those activities and delivers talks globally at well-known events such as RSA, Black Hat, Open Source Summit, KubeCon, OSCON, DevSecCon, DevOpsCon, Red Hat Summit, and Interop. Tim is also an O'Reilly Media published author and has been covered in publications around the globe including USA Today, Fortune, NBC News, CNN, Forbes, Dark Reading, TEISS, InfoSecurity Magazine, and The Straits Times. Data and Ransomware Attackers define the rules Average total cost of data breach: $8.19 Million Customer impact: 3.6% abnormal turnover Average time to identify and contain a breach: 245 days Source: 2019 Cost of Data Breach Study (US Data) – Ponemon Institute TruismTruism #1 #1 You can’t secure data you don’t -
Malware Disruptions and More Information
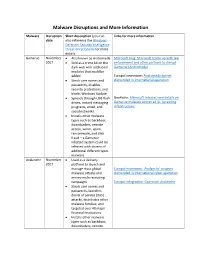
Malware Disruptions and More Information Malware Disruption Short description (you can Links for more information date also reference the Windows Defender Security Intelligence threat encyclopedia for more details Gamarue November • Also known as Andromeda Microsoft blog: Microsoft teams up with law 2017 • Sold as a crime kit on the enforcement and other partners to disrupt dark web with additional Gamarue (Andromeda) modules that could be added Europol newsroom: Andromeda botnet • Steals user names and dismantled in international operation passwords, disables security protections, and blocks Windows Update • Spreads through USB flash Geekwire: Microsoft releases new details on drives, instant messaging Gamarue malware botnet ad its 'sprawling programs, email, and infrastructure' social networks • Installs other malware types such as backdoor, downloaders, remote access, worm, spam, ransomware, and click fraud – a Gamarue infected system could be infected with dozens of additional different types malware Avalanche November • Used as a delivery 2017 platform to launch and manage mass global Europol newsroom: 'Avalanche' network malware attacks and dismantled in international cyber operation money mule recruiting campaigns Europol infographic: Operation Avalanche • Steals user names and passwords, launches denial of service (DoS) attacks, distributes other malware families, and targeted over 40 major financial institutions • Installs other malware types such as backdoor, downloaders, remote access, worm, spam, and click fraud Barium November -

Book and Is Not Responsible for the Web: Content of the External Sources, Including External Websites Referenced in This Publication
2020 12th International Conference on Cyber Conflict 20/20 Vision: The Next Decade T. Jančárková, L. Lindström, M. Signoretti, I. Tolga, G. Visky (Eds.) 2020 12TH INTERNATIONAL CONFERENCE ON CYBER CONFLicT 20/20 VISION: THE NEXT DECADE Copyright © 2020 by NATO CCDCOE Publications. All rights reserved. IEEE Catalog Number: CFP2026N-PRT ISBN (print): 978-9949-9904-6-7 ISBN (pdf): 978-9949-9904-7-4 COPYRIGHT AND REPRINT PERMissiONS No part of this publication may be reprinted, reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording or otherwise, without the prior written permission of the NATO Cooperative Cyber Defence Centre of Excellence ([email protected]). This restriction does not apply to making digital or hard copies of this publication for internal use within NATO, or for personal or educational use when for non-profit or non-commercial purposes, providing that copies bear this notice and a full citation on the first page as follows: [Article author(s)], [full article title] 2020 12th International Conference on Cyber Conflict 20/20 Vision: The Next Decade T. Jančárková, L. Lindström, M. Signoretti, I. Tolga, G. Visky (Eds.) 2020 © NATO CCDCOE Publications NATO CCDCOE Publications LEGAL NOTICE: This publication contains the opinions of the respective authors only. They do not Filtri tee 12, 10132 Tallinn, Estonia necessarily reflect the policy or the opinion of NATO Phone: +372 717 6800 CCDCOE, NATO, or any agency or any government. NATO CCDCOE may not be held responsible for Fax: +372 717 6308 any loss or harm arising from the use of information E-mail: [email protected] contained in this book and is not responsible for the Web: www.ccdcoe.org content of the external sources, including external websites referenced in this publication.