Cybersecurity Challenges for Canada and the United States
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

David Hume Kennerly Archive Creation Project
DAVID HUME KENNERLY ARCHIVE CREATION PROJECT 50 YEARS BEHIND THE SCENES OF HISTORY The David Hume Kennerly Archive is an extraordinary collection of images, objects and recollections created and collected by a great American photographer, journalist, artist and historian documenting 50 years of United States and world history. The goal of the DAVID HUME KENNERLY ARCHIVE CREATION PROJECT is to protect, organize and share its rare and historic objects – and to transform its half-century of images into a cutting-edge digital educational tool that is fully searchable and available to the public for research and artistic appreciation. 2 DAVID HUME KENNERLY Pulitzer Prize-winning photojournalist David Hume Kennerly has spent his career documenting the people and events that have defined the world. The last photographer hired by Life Magazine, he has also worked for Time, People, Newsweek, Paris Match, Der Spiegel, Politico, ABC, NBC, CNN and served as Chief White House Photographer for President Gerald R. Ford. Kennerly’s images convey a deep understanding of the forces shaping history and are a peerless repository of exclusive primary source records that will help educate future generations. His collection comprises a sweeping record of a half-century of history and culture – as if Margaret Bourke-White had continued her work through the present day. 3 HISTORICAL SIGNIFICANCE The David Hume Kennerly collection of photography, historic artifacts, letters and objects might be one of the largest and most historically significant private collections ever produced and collected by a single individual. Its 50-year span of images and objects tells the complete story of the baby boom generation. -

Exhibit a Case 3:16-Cr-00051-BR Document 545-2 Filed 05/11/16 Page 2 of 86
Case 3:16-cr-00051-BR Document 545-2 Filed 05/11/16 Page 1 of 86 Exhibit A Case 3:16-cr-00051-BR Document 545-2 Filed 05/11/16 Page 2 of 86 Executive Order 12333 United States Intelligence Activities (As amended by Executive Orders 13284 (2003), 13355 (2004) and 134 70 (2008)) PREAMBLE Timely, accurate, and insightful information about the activities, capabilities, plans, and intentions of foreign powers , organizations, and persons, and their agents, is essential to the national security of the United States. All reasonable and lawful means must be used to ensure that the United States will receive the best intelligence possible. For that purpose, by virtue of the authority vested in me by the Constitution and the laws of the United States of America, including the National Security Act of 1947, as amended, (Act) and as President of the United States of America, in order to provide for the effective conduct of United States intelligence activities and the protection of constitutional rights, it is hereby ordered as follows: PART 1 Goals, Directions, Duties, and Responsibilities with Respect to United States Intelligence Efforts 1.1 Goals. The United States intelligence effort shall provide the President, the National Security Council, and the Homeland Security Council with the necessary information on which to base decisions concerning the development and conduct of foreign, defense, and economic policies, and the protection of United States national interests from foreign security threats. All departments and agencies shall cooperate fully to fulfill this goal. (a} All means, consistent with applicable Federal law and this order, and with full consideration of the rights of United States persons, shall be used to obtain reliable intelligence information to protect the United States and its interests. -

Annual Report
COUNCIL ON FOREIGN RELATIONS ANNUAL REPORT July 1,1996-June 30,1997 Main Office Washington Office The Harold Pratt House 1779 Massachusetts Avenue, N.W. 58 East 68th Street, New York, NY 10021 Washington, DC 20036 Tel. (212) 434-9400; Fax (212) 861-1789 Tel. (202) 518-3400; Fax (202) 986-2984 Website www. foreignrela tions. org e-mail publicaffairs@email. cfr. org OFFICERS AND DIRECTORS, 1997-98 Officers Directors Charlayne Hunter-Gault Peter G. Peterson Term Expiring 1998 Frank Savage* Chairman of the Board Peggy Dulany Laura D'Andrea Tyson Maurice R. Greenberg Robert F Erburu Leslie H. Gelb Vice Chairman Karen Elliott House ex officio Leslie H. Gelb Joshua Lederberg President Vincent A. Mai Honorary Officers Michael P Peters Garrick Utley and Directors Emeriti Senior Vice President Term Expiring 1999 Douglas Dillon and Chief Operating Officer Carla A. Hills Caryl R Haskins Alton Frye Robert D. Hormats Grayson Kirk Senior Vice President William J. McDonough Charles McC. Mathias, Jr. Paula J. Dobriansky Theodore C. Sorensen James A. Perkins Vice President, Washington Program George Soros David Rockefeller Gary C. Hufbauer Paul A. Volcker Honorary Chairman Vice President, Director of Studies Robert A. Scalapino Term Expiring 2000 David Kellogg Cyrus R. Vance Jessica R Einhorn Vice President, Communications Glenn E. Watts and Corporate Affairs Louis V Gerstner, Jr. Abraham F. Lowenthal Hanna Holborn Gray Vice President and Maurice R. Greenberg Deputy National Director George J. Mitchell Janice L. Murray Warren B. Rudman Vice President and Treasurer Term Expiring 2001 Karen M. Sughrue Lee Cullum Vice President, Programs Mario L. Baeza and Media Projects Thomas R. -

The Sponsor Effect: Breaking Through the Last Glass Ceiling
DEcember 2010 The Sponsor Effect: Breaking Through the Last Glass Ceiling By Sylvia Ann Hewlett, with Kerrie Peraino, Laura Sherbin, and Karen Sumberg Center for Work-Life Policy Survey research sponsored by: American Express, Deloitte, Intel, and Morgan Stanley RESEARCH REPORT The Sponsor Effect: Breaking Through the Last Glass Ceiling EXECUTIVE SUMMARY Women just aren’t making it to the very top. Despite making gains in middle and senior management, they hold just 3 percent of Fortune 500 CEO positions. In the C-suite, they’re outnumbered four to one. They account for less than 16 percent of all corporate officers, and comprise only 7.6 percent of Fortune 500 top earner positions. What’s keeping them under this last glass ceiling? What we uncover in this report is not a male conspiracy, but rather, a surprising absence of male (and female) advocacy. Women who are qualified to lead simply don’t have the powerful backing necessary to inspire, propel, and protect them through the perilous straits of upper management. Women lack, in a word, sponsorship. Spearheaded by American Express, Deloitte, Intel, and Morgan Stanley, the Hidden Brain Drain Task Force launched a study in the fall of 2009 to determine the nature and impact of sponsorship and examine just why women fail to either access or make better use of it.1 We found that the majority of ambitious women underestimate the pivotal role sponsorship plays in their advancement—not just within their current firm, but throughout their career and across their industry. More surprisingly, however, we found that women who do grasp the importance of relationship capital fail to cultivate it effectively. -

Spartan Daily 1.000 Parking Spaces
New garage prepare may not add Spartans S.U.'s musical week for homecoming any spaces by Morgan Hampton page 3 page 4 SJSU students won't gain a single parking space when the new $5.85 million parking garage is completed in 1982 if city urban renewal plans are finalized. The new garage has been approved by California State University and Colleges board of trustees, but still awaits master plan revision before plans are finalized. SJSU President Gail Fullerton said last week she expects no problem in getting approval at the next meeting in November. The 1.200 space garage will displace about 200 existing parking spaces at its site on Fourth Street between San Carlos and San Salvador streets, leaving a net gain of Spartan Daily 1.000 parking spaces. But 1,000 by SJSU students parking spaces now used Volume 73. Number 23 Serving San Jose State University since 1934 Friday. October 5, 1979 will be lost when the city reclaims its property on Fourth Street between San Fernando and San Carlos streets. The city plans to build condominiums, apartments and retail stores on the Fourth Street property, according to Pat Forst, coordinator for the San Jose Redevelopment Agency. When construction will begin is "touch and go," ac- cording to Forst, because the city is waiting for financial Hannah's removal unclear clearance of the developer's plans. Forst would not estimate when construction would begin, but she said even if urban renewal plans for the Ombudsman Fourth Street property are delayed until 1982, the city may have plans to use the lots for its own parking before position filled that time. -

E-Mails from Inside the NSA Bureaucracy
7/28/2016 Electrospaces.net 6 More Next Blog» Create Blog Sign In June 24, 2016 Welcome to Electrospaces.net! Here you can read about: E-mails from inside the NSA bureaucracy - Signals Intelligence (SIGINT), - Communications Security (COMSEC), Earlier this month, the NSA declassified a huge set of internal e-mails, following FOIA- - Information Classification, requests about the issue of whether Edward Snowden had raised concerns about the and also about the equipment, from NSA's surveillance programs through proper channels inside the agency. past and present, which make that civilian and military leaders can > Download the declassified e-mails (very large pdf) communicate in order to fulfill their duties. Here, we will take a look at the administrative details these internal NSA e-mails The main focus will be on the United provide. Next time we will see what their content says about the concerns that States and its National Security Snowden claimed to have raised. Agency (NSA), but attention will also be paid to other countries and subjects. Any comments, additions, corrections, questions or suggestions will be very appreciated! There's no login or registration required for commenting. twitter.com/electrospaces info (at) electrospaces.net PGP Public Key ID: FD9FD4E6 The postings on this weblog are updated frequently as new information about the NSA is still being revealed. Therefore, revisit this weblog and check the articles for updates! Index of all postings Internal e-mail from NSA director Michael Rogers. In the signature block we see his NSANet and SIPRNet e-mail addresses and his non-secure phone number (all redacted) (Click to enlarge - See also: NSA director Alexander's phones) Recent Posts E-mails from inside the NSA bureaucracy E-mail addresses German journalists about working with the Snowden documents http://electrospaces.blogspot.dk/ 1/18 7/28/2016 Electrospaces.net Except from the classification markings, the NSA's internal e-mails aren't very different from those exchanged by most other people around the world. -

Fondamentaux & Domaines
Septembre 2020 Marie Lechner & Yves Citton Angles morts du numérique ubiquitaire Sélection de lectures, volume 2 Fondamentaux & Domaines Sommaire Fondamentaux Mike Ananny, Toward an Ethics of Algorithms: Convening, Observation, Probability, and Timeliness, Science, Technology, & Human Values, 2015, p. 1-25 . 1 Chris Anderson, The End of Theory: The Data Deluge Makes the Scientific Method Obsolete, Wired, June 23, 2008 . 26 Mark Andrejevic, The Droning of Experience, FibreCultureJournal, FCJ-187, n° 25, 2015 . 29 Franco ‘Bifo’ Berardi, Concatenation, Conjunction, and Connection, Introduction à AND. A Phenomenology of the End, New York, Semiotexte, 2015 . 45 Tega Brain, The Environment is not a system, Aprja, 2019, http://www.aprja.net /the-environment-is-not-a-system/ . 70 Lisa Gitelman and Virginia Jackson, Introduction to Raw Data is an Oxymoron, MIT Press, 2013 . 81 Orit Halpern, Robert Mitchell, And Bernard & Dionysius Geoghegan, The Smartness Mandate: Notes toward a Critique, Grey Room, n° 68, 2017, pp. 106–129 . 98 Safiya Umoja Noble, The Power of Algorithms, Introduction to Algorithms of Oppression. How Search Engines Reinforce Racism, NYU Press, 2018 . 123 Mimi Onuoha, Notes on Algorithmic Violence, February 2018 github.com/MimiOnuoha/On-Algorithmic-Violence . 139 Matteo Pasquinelli, Anomaly Detection: The Mathematization of the Abnormal in the Metadata Society, 2015, matteopasquinelli.com/anomaly-detection . 142 Iyad Rahwan et al., Machine behavior, Nature, n° 568, 25 April 2019, p. 477 sq. 152 Domaines Ingrid Burrington, The Location of Justice: Systems. Policing Is an Information Business, Urban Omnibus, Jun 20, 2018 . 162 Kate Crawford, Regulate facial-recognition technology, Nature, n° 572, 29 August 2019, p. 565 . 185 Sidney Fussell, How an Attempt at Correcting Bias in Tech Goes Wrong, The Atlantic, Oct 9, 2019 . -

Change Not Charity: Essays on Oxfam America's First 40 Years
Change not Charity: Essays on Oxfam America’s first 40 years Change not Charity: Essays on Oxfam America’s first 40 years Edited by Laura Roper Contents Acknowledgements 7 Author Bios 9 Introduction 15 The Early Years (1970-1977): Founding and Early Fruition 1. The Founding of Oxfam America, John W. Thomas 23 2. From Church Basement to the Board Room: Early Governance and Organizational Development, Robert C. Terry 28 3. Launching Oxfam’s Educational Mission, Nathan Gray 48 4. Humanitarian Response in Oxfam America’s Development: From Ambivalence to Full Commitment, Judith van Raalten and Laura Roper 57 5. Perspectives on Oxfam’s Partnership Model, Barbara Thomas-Slayter 74 The Short Years: Establishing an Institutional Identity and Ways of Working 6. Acting Strategically: Memories of Oxfam, 1977–1984, Joe Short 91 7. The Origins of Advocacy at Oxfam America, Laurence R. Simon 114 8. Humanitarian Aid Experiences at Home and Abroad: An Oxfam America Memoir, Michael Scott 140 9. Oxfam’s Cambodia Response and Effective Approaches to Humanitarian Action, Joel R. Charny 165 10. Women’s Empowerment in South Asia: Oxfam America’s First Gender Program, Martha Chen 175 11. Lessons from Lebanon, 1982–83, Dan Connell 186 The Hammock Years (1984–1995): Organizational Evolution in an Ever-Changing World 12. Walking the Talk: Development, Humanitarian Aid, and Organizational Development John Hammock 203 13. The 1984 Ethiopia Famine: A Turning Point for Oxfam America, Bernie Beaudreau 229 14. Finding My Feet: Reflections of a Program Officer on Her Work in Africa in the 1980s, Deborah Toler 236 15. Reflections on Working with Rebel Movements in the Horn of Africa, Rob Buchanan 251 16. -

Large Print Guide
Large Print Guide You can download this document from www.manchesterartgallery.org Sponsored by While principally a fashion magazine, Vogue has never been just that. Since its first issue in 1916, it has assumed a central role on the cultural stage with a history spanning the most inventive decades in fashion and taste, and in the arts and society. It has reflected events shaping the nation and Vogue 100: A Century of Style has been organised by the world, while setting the agenda for style and fashion. the National Portrait Gallery, London in collaboration with Tracing the work of era-defining photographers, models, British Vogue as part of the magazine’s centenary celebrations. writers and designers, this exhibition moves through time from the most recent versions of Vogue back to the beginning of it all... 24 June – 30 October Free entrance A free audio guide is available at: bit.ly/vogue100audio Entrance wall: The publication Vogue 100: A Century of Style and a selection ‘Mighty Aphrodite’ Kate Moss of Vogue inspired merchandise is available in the Gallery Shop by Mert Alas and Marcus Piggott, June 2012 on the ground floor. For Vogue’s Olympics issue, Versace’s body-sculpting superwoman suit demanded ‘an epic pose and a spotlight’. Archival C-type print Photography is not permitted in this exhibition Courtesy of Mert Alas and Marcus Piggott Introduction — 3 FILM ROOM THE FUTURE OF FASHION Alexa Chung Drawn from the following films: dir. Jim Demuth, September 2015 OUCH! THAT’S BIG Anna Ewers HEAT WAVE Damaris Goddrie and Frederikke Sofie dir. -

David Hume Kennerly Archive Project
DAVID HUME KENNERLY ARCHIVE PROJECT 50 YEARS BEHIND THE SCENES OF HISTORY The David Hume Kennerly Archive is an extraordinary collection of images, objects and recollections created and collected by a great American photographer, journalist, artist and historian documenting 50 years of United States and world history. The goal of the DAVID HUME KENNERLY ARCHIVE PROJECT is to protect, organize and share its rare and historic objects – and to transform its half-century of images into a cutting- edge digital educational tool that is fully searchable and available to the public for research and artistic appreciation. 2 DAVID HUME KENNERLY Pulitzer Prize-winning photojournalist David Hume Kennerly has spent his career documenting the people and events that have defined the world. The last photographer hired by Life Magazine, he has also worked for Time, People, Newsweek, Paris Match, Der Spiegel, Politico, ABC, NBC, CNN and served as Chief White House Photographer for President Gerald R. Ford. Kennerly’s images convey a deep understanding of the forces shaping history and are a peerless repository of exclusive primary source records that will help educate future generations. His collection comprises a sweeping record of a half-century of history and culture – as if Margaret Bourke-White had continued her work through the present day. 3 HISTORICAL SIGNIFICANCE The David Hume Kennerly collection of photography, historic artifacts, letters and objects might be one of the largest and most historically significant private collections ever produced and collected by a single individual. Its 50-year span of images and objects tells the complete story of the baby boom generation. -

Fiff-Kommunikation 4/2015
Britta Schinzel NGOs – wir klagen an und fordern auf Das Projekt 11 TAGE berührt die Intentionen des FIfF und anderer gegen Überwachung, Cyberwar und Drohnenkrieg agitierender NGOs auf vielfältige Weise. Der virtuelle Angriff auf die Ratte aus dem Internet simuliert die Drohnen-Zielfindung; das von Florian Mehnert verwendete Mittel von Egoshootern aus der Spielewelt verweist auf die Vermischung der Gamification mit dem Training an modernen Waffensystemen; die Überwachung ist essentieller Teil von Cyberwar und Drohnenkrieg. Nicht zuletzt sind auch die gegen Mehnert instanziierten Shitstorms und Morddrohungen wichtige Themen für NGOs, die sich mit dem IT-Bereich beschäftigen. Hier werden einige dieser Punkte aufgegriffen. Einleitung kontrollstation in Nähe zum Einsatzgebiet, von wo aus er mit- tels Sichtdatenlink kontrolliert wird, und einer Satelliten-Kom- Es scheint zunehmend nötig, gegen Krieg, Waffenproduktion, munikationsverbindung für Operationen ausser Sichtweite. In und Überwachung zu agitieren, gesellschaftliches Bewusstsein der Bodenkontrollstation sitzt ein Pilot, der das System fern- schwerpunkt herzustellen bzw. zu schärfen, mehr noch, Einfluss auf Parla- steuert und auf der Militärbasis in Nevada oder Ramstein im mentarier und die Regierung zu nehmen und sogar Verfassungs- Pfälzerwald2 vor ihren Bildschirmen 2 Sensoroperatoren zur klagen anzustrengen. Bedienung der Kameras, Sensoren und Radare, und für die Datenanalyse und Kommunikation. Das Fluggerät besitzt ein Wer kann in einer Demokratie außerparlamentarisch Einfluss auf Multispektral-Zielsystem, eine TV-Kamera und eine thermo- die Politik nehmen? graphische Kamera, die volle Bewegungsvideos produzieren. Es kann bis zu 14 Stunden in der Luft bleiben, bis zu 15 km hoch Solche Akteure sind einmal die Medien, zum anderen die Wis- fliegen, in einem Einsatzradius von 750 km und zurück zur Ba- senschaften mit Veröffentlichungen, und wie im vorliegenden sis. -
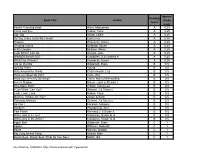
Book Title Author Reading Level Approx. Grade Level
Approx. Reading Book Title Author Grade Level Level Anno's Counting Book Anno, Mitsumasa A 0.25 Count and See Hoban, Tana A 0.25 Dig, Dig Wood, Leslie A 0.25 Do You Want To Be My Friend? Carle, Eric A 0.25 Flowers Hoenecke, Karen A 0.25 Growing Colors McMillan, Bruce A 0.25 In My Garden McLean, Moria A 0.25 Look What I Can Do Aruego, Jose A 0.25 What Do Insects Do? Canizares, S.& Chanko,P A 0.25 What Has Wheels? Hoenecke, Karen A 0.25 Cat on the Mat Wildsmith, Brain B 0.5 Getting There Young B 0.5 Hats Around the World Charlesworth, Liza B 0.5 Have you Seen My Cat? Carle, Eric B 0.5 Have you seen my Duckling? Tafuri, Nancy/Greenwillow B 0.5 Here's Skipper Salem, Llynn & Stewart,J B 0.5 How Many Fish? Cohen, Caron Lee B 0.5 I Can Write, Can You? Stewart, J & Salem,L B 0.5 Look, Look, Look Hoban, Tana B 0.5 Mommy, Where are You? Ziefert & Boon B 0.5 Runaway Monkey Stewart, J & Salem,L B 0.5 So Can I Facklam, Margery B 0.5 Sunburn Prokopchak, Ann B 0.5 Two Points Kennedy,J. & Eaton,A B 0.5 Who Lives in a Tree? Canizares, Susan et al B 0.5 Who Lives in the Arctic? Canizares, Susan et al B 0.5 Apple Bird Wildsmith, Brain C 1 Apples Williams, Deborah C 1 Bears Kalman, Bobbie C 1 Big Long Animal Song Artwell, Mike C 1 Brown Bear, Brown Bear What Do You See? Martin, Bill C 1 Found online, 7/20/2012, http://home.comcast.net/~ngiansante/ Approx.