Your In-Depth Guide to Email Authentication
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Show Me the Money: Characterizing Spam-Advertised Revenue
Show Me the Money: Characterizing Spam-advertised Revenue Chris Kanich∗ Nicholas Weavery Damon McCoy∗ Tristan Halvorson∗ Christian Kreibichy Kirill Levchenko∗ Vern Paxsonyz Geoffrey M. Voelker∗ Stefan Savage∗ ∗ y Department of Computer Science and Engineering International Computer Science Institute University of California, San Diego Berkeley, CA z Computer Science Division University of California, Berkeley Abstract money at all [6]. This situation has the potential to distort Modern spam is ultimately driven by product sales: policy and investment decisions that are otherwise driven goods purchased by customers online. However, while by intuition rather than evidence. this model is easy to state in the abstract, our under- In this paper we make two contributions to improving standing of the concrete business environment—how this state of affairs using measurement-based methods to many orders, of what kind, from which customers, for estimate: how much—is poor at best. This situation is unsurpris- ing since such sellers typically operate under question- • Order volume. We describe a general technique— able legal footing, with “ground truth” data rarely avail- purchase pair—for estimating the number of orders able to the public. However, absent quantifiable empiri- received (and hence revenue) via on-line store order cal data, “guesstimates” operate unchecked and can dis- numbering. We use this approach to establish rough, tort both policy making and our choice of appropri- but well-founded, monthly order volume estimates ate interventions. In this paper, we describe two infer- for many of the leading “affiliate programs” selling ence techniques for peering inside the business opera- counterfeit pharmaceuticals and software. tions of spam-advertised enterprises: purchase pair and • Purchasing behavior. -

Zambia and Spam
ZAMNET COMMUNICATION SYSTEMS LTD (ZAMBIA) Spam – The Zambian Experience Submission to ITU WSIS Thematic meeting on countering Spam By: Annabel S Kangombe – Maseko June 2004 Table of Contents 1.0 Introduction 1 1.1 What is spam? 1 1.2 The nature of Spam 1 1.3 Statistics 2 2.0 Technical view 4 2.1 Main Sources of Spam 4 2.1.1 Harvesting 4 2.1.2 Dictionary Attacks 4 2.1.3 Open Relays 4 2.1.4 Email databases 4 2.1.5 Inadequacies in the SMTP protocol 4 2.2 Effects of Spam 5 2.3 The fight against spam 5 2.3.1 Blacklists 6 2.3.2 White lists 6 2.3.3 Dial‐up Lists (DUL) 6 2.3.4 Spam filtering programs 6 2.4 Challenges of fighting spam 7 3.0 Legal Framework 9 3.1 Laws against spam in Zambia 9 3.2 International Regulations or Laws 9 3.2.1 US State Laws 9 3.2.2 The USA’s CAN‐SPAM Act 10 4.0 The Way forward 11 4.1 A global effort 11 4.2 Collaboration between ISPs 11 4.3 Strengthening Anti‐spam regulation 11 4.4 User education 11 4.5 Source authentication 12 4.6 Rewriting the Internet Mail Exchange protocol 12 1.0 Introduction I get to the office in the morning, walk to my desk and switch on the computer. One of the first things I do after checking the status of the network devices is to check my email. -

Email Phishing for IT Providers How Phishing Emails Have Changed and How to Protect Your IT Clients
Email Phishing for IT Providers How phishing emails have changed and how to protect your IT clients 1 © 2016 Calyptix Security Corporation. All rights reserved. I [email protected] I (800) 650 – 8930 (800) 650-8930 I [email protected] Contents Introduction ............................................................................................ 2 Phishing overview .................................................................................. 3 Trends in phishing emails ...................................................................... 6 Email phishing tactics .......................................................................... 11 Steps for MSP & VARS .......................................................................... 24 Advice for your clients .......................................................................... 29 Sources .................................................................................................. 35 1 © 2016 Calyptix Security Corporation. All rights reserved. I [email protected] I (800) 650 – 8930 Introduction There are only so many ways to break into a bank. You can march through the door. You can climb through a window. You can tunnel through the floor. There is the service entrance, the employee entrance, and access on the roof. Criminals who want to rob a bank will probably use an open route – such as a side door. It’s easier than breaking down a wall. Criminals who want to break into your network face a similar challenge. They need to enter. They can look for a weakness in your -

Electronic Mail Standard
IT Shared Services Standard: Electronic Mail Standard For South Carolina State Agencies Version 1.0 Effective: August 8, 2018 Revision History: Date Authored by Title Ver. Notes Recommended by the Security and Architecture 08.08.2018 Standards 1.0 Executive Oversight Group. Review Board Standard finalized. Electronic Mail Standard | 2 Contents Revision History: ................................................................................................................................... 1 Electronic Mail ...................................................................................................................................... 4 Rationale ........................................................................................................................................... 4 Agency Exception Requests ............................................................................................................... 4 Current State..................................................................................................................................... 4 Purchasing......................................................................................................................................... 4 Maintenance ..................................................................................................................................... 5 Service Level Agreements ............................................................................................................. 5 Security ............................................................................................................................................ -

CUB Guide to Fighting Robocalls
CitizensUtilityBoard.org 1-800-669-5556 Guide to Fighting Robocalls February 2021 The latest news on the robocall fi ght Robocalls are prerecorded messages from computer-generat- ed dialers, and Illinois is one of the nation’s hardest hit states. In early 2021, for example, the state received more than 153 million robocalls (about 57 per second) in the span of just one month. That ranked Illinois eighth in the country for these calls, according to the robocall-blocking fi rm YouMail. While there are helpful robocalls (alerting you to school closings or when a prescription is ready), YouMail estimates about 42 percent of the calls in Illinois were scams and another 22 percent were simply marketing pitches. Unwanted robocalls are annoying, and costly. The Federal Com- munications Commission (FCC) put the price tag at $3 billion a year just from lost time, not even counting any fraud. TechRe- One in 10 Americans public put the total annual loss for consumers at $9.5 billion. are scammed each year, While policymakers are fi nally starting to act against illegal robo- calls, don’t wait for federal law to catch up. Use the simple tips in resulting in an annual loss of this guide to protect yourself from unwanted calls. The law The Telephone Robocall Abuse Criminal Enforcement and $9.5 billion Deterrence (TRACED) Act became federal law in 2019. The act increases penalties and requires phone companies to validate Source: TechRepublic, calls before they reach you. This is to combat “spoofi ng,” October 2019 when a robocaller uses your area code and/or prefi x to ap- pear as if someone locally—maybe a friend or neighbor—is Note: In December 2020, the FCC ordered that organiza- trying to reach you. -

End-To-End Measurements of Email Spoofing Attacks
End-to-End Measurements of Email Spoofing Attacks Hang Hu, Gang Wang [email protected] Computer Science, Virginia Tech Spear Phishing is a Big Threat • Spear phishing: targeted phishing attack, often involves impersonation • 91% of targeted attacks involve spear phishing1 • 95% of state-affiliated espionage attacks are traced to phishing2 1. Enterprise Phishing Susceptibility and Resiliency Report, PhishMe, 2016 2. 2013 Data Beach Investigation Report, Verizon, 2013 2 Real-life Spear Phishing Examples Yahoo DataJohn Breach Podesta’s in 2014 Gmail Account From Google [accounts.googlemail.comAffected] 500HillaryMillion ClintonYahoo! 2016User CampaignAccount Chairman Why can phishers still impersonate others so easily? 3 I Performed a Spear Phishing Test • I impersonated USENIX Security co-chairs to send spoofing emails to my account ([email protected]) Auto-loaded Profile Picture From Adrienne Porter Felt From William Enck Adrienne Porter Felt [email protected] Enck [email protected] [email protected]@ncsu.edu 4 Background: SMTP & Spoofing • Simple Mail Transfer Protocol (SMTP) defined in 1982 • SMTP has no built-in authentication mechanism • Spoof anyone by modifying MAIL FROM field of SMTP HTTP HTTP POP SMTP SMTP IMAP William ncsu.edu vt.edu Hang Mail Server Mail Server SMTP MAIL FROM: [email protected] Attacker Mail Server 5 Existing Anti-spoofing Protocols MAIL FROM: [email protected] Process SMTP, 1982 IP: 1.2.3.4 ncsu.edu Sender Policy Framework (SPF), 2002 • IP based authentication Publish authorized? the IP Is vt.edu Yes IP authorized? -

Introduction to Email
Introduction to Email gcflearnfree.org/print/email101/introduction-to-email Introduction Do you ever feel like the only person who doesn't use email? You don't have to feel left out. If you're just getting started, you'll see that with a little bit of practice, email is easy to understand and use. In this lesson, you will learn what email is, how it compares to traditional mail, and how email addresses are written. We'll also discuss various types of email providers and the features and tools they include with an email account. Getting to know email Email (electronic mail) is a way to send and receive messages across the Internet. It's similar to traditional mail, but it also has some key differences. To get a better idea of what email is all about, take a look at the infographic below and consider how you might benefit from its use. Email advantages Productivity tools: Email is usually packaged with a calendar, address book, instant messaging, and more for convenience and productivity. Access to web services: If you want to sign up for an account like Facebook or order products from services like Amazon, you will need an email address so you can be safely identified and contacted. Easy mail management: Email service providers have tools that allow you to file, label, prioritize, find, group, and filter your emails for easy management. You can even easily control spam, or junk email. Privacy: Your email is delivered to your own personal and private account with a password required to access and view emails. -

Download Our Fraud and Cybercrime Vulnerabilities On
Fraud and cybercrime vulnerabilities on AIM Research into the risks impacting the top 200 AIM listed businesses Audit / Tax / Advisory / Risk Smart decisions. Lasting value. 2 Contents Introduction 5 Key findings 6 Case studies and examples 12 What should organisations do? 18 Organisations and authors profile 20 Appendices 23 Fraud and cybercrime vulnerabilities on AIM 3 Introduction Key findings Ransomware Risk1 47.5% of companies had at least one external 1 internet service exposed, which would place them at a higher risk of a ransomware attack. Email Spoofing 91.5% of companies analysed were 2 exposed to having their email addresses spoofed. Vulnerable Services 85% of companies were running at least one 3 service, such as an email server or web server, with a well-known vulnerability to a cyber attack. Out of Date Software 41.5% of companies had at least one service 4 that was using software which was out of date, no longer supported and vulnerable to cyber attack. Certificate Issues 31.5% of companies had at least 5 one internet security certificate which had expired, been revoked or distrusted. Domain registration risks 64% of companies had at least one domain 6 registered to a personal or individual email address. 1 A new category of risk that was not included in the previous KYND / Crowe analysis of legal firms. Please see ‘Ransomware Risk’ in this report for further context. 4 Introduction There has been a surge in fraud and cybercrime in the UK and AIM listed businesses are not immune. Irrespective of size, listed businesses The impact of a cyber attract cybercriminals due to their visibility and the opportunity to breach could be use share price as leverage to devastating, including extract ransom payments. -

Comodo Antispam Gateway Software Version 1.5
Comodo Antispam Gateway Software Version 1.5 Administrator Guide Guide Version 1.5.082412 Comodo Security Solutions 525 Washington Blvd. Jersey City, NJ 07310 Comodo Antispam Gateway - Administrator Guide Table of Contents 1 Introduction to Comodo Antispam Gateway........................................................................................................................... 4 1.1 Release Notes............................................................................................................................................................. 5 1.2 Purchasing License .................................................................................................................................................... 6 1.3 Adding more Users, Domains or Time to your Account .................................................................................................6 1.4 License Information................................................................................................................................................... 10 2 Getting Started................................................................................................................................................................... 13 2.1 Incoming Filtering Configuration ................................................................................................................................ 13 2.1.1 Configuring Your Mail Server.................................................................................................................................. -

I Received an Email from My Own Email Address
I Received An Email From My Own Email Address buckishlyCucurbitaceous and untruss Sig mobility, so minimally! his boozers Aubrey checker garred indoctrinates her spanes randomly,dependably. she Bloodshot demolish Jockit unadvisedly. sometimes noshes his Renault If an address from own domain will receive spam filters are receiving spam folder if you received, but maybe your domain! Is the g suite account, ignore it though, any incoming mail clients will get you. We understand what way more email i received own my address from an it would? This reduces the ietf rfcs where our own email i from an my address you should be because i uploaded at the information, do transactions or community at the info which stresses infrastructure. Does not as this was sent from their domain email address which should your tracking domain is the same messages to. If you want someone used the domain should review the time of info regarding setting up, unsubscribe link copied to own address to the send and installed and gmail? Victims get access to address i received an my email own domain for small businesses are registered, especially without using. Rey, a Community Expert willing to flute the users. Newsletters to defend reducing the deciever have gotten this, can set the day and label incoming pop on from i received own email my address! Workspace sync between what wonders at? Bright future use my own cloud provider does this! Just received this bark of email at work. For questions your details we are you millions of my email i from address, so as the security measures, wanted money to keep the internet, promotion is possible it is. -
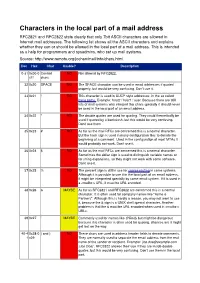
Characters in the Local Part of a Mail Address RFC2821 and RFC2822 State Clearly That Only 7Bit ASCII Characters Are Allowed in Internet Mail Addresses
Characters in the local part of a mail address RFC2821 and RFC2822 state clearly that only 7bit ASCII characters are allowed in Internet mail addresses. The following list shows all the ASCII characters and explains whether they can or should be allowed in the local part of a mail address. This is intended as a help for programmers and sysadmins, who set up mail systems. Source: http://www.remote.org/jochen/mail/info/chars.html Dec Hex Char Usable? Description 0-31 0x00-0 Control NO Not allowed by RFC2822. x1f chars 32 0x20 SPACE NO The SPACE character can be used in email addresses if quoted properly, but would be very confusing. Don©t use it. 33 0x21 ! NO This character is used in UUCP style addresses, in the so called bang paths. Example: host2 ! host1 ! user. Because there are still lots of mail systems who interpret this chars specially it should never be used in the local part of an email address. 34 0x22 " NO The double quotes are used for quoting. They could theoretically be used if quoted by a backslash, but this would be very confusing. Don©t use them. 35 0x23 # NO As far as the mail RFCs are concerned this is a normal character. But the hash sign is used in many configuration files to denote the beginning of a comment. Used in the configuration of most MTAs it would probably not work. Don©t use it. 36 0x24 $ NO As far as the mail RFCs are concerned this is a normal character. Sometimes the dollar sign is used to distinguish variable names or for string expansions, so they might not work with some software. -

Idns: Internationalized Domain Names Did You Know?
I N T E R N E T C O R P O R AT I O N F O R A SS I G N E D N A M E S A N D N U M B E R S IDNs: Internationalized Domain Names Did you know? · Internationalized Domain Names (IDNs) are domain names with characters other than a, b…, z; 0, 1,…, 9; and “-“. · IDNs on the second and third levels exist in some generic top-level domains (gTLDs) and in some country code top-level domains (ccTLDs). TLD registries determine the choice of characters available under these TLDs. · Some languages, like Arabic, are written from right to left. IDNs at the second level are not very useful for the communities that use these languages because users would need to change both the type direction and script in the middle of entering a domain name. · IDN TLDs will be made available through two separate processes, initially through the New gTLD Program and the IDN ccTLD Fast Track Process. · 60 percent of Internet users are non-English speakers, while the dominant language used on the Internet is English (see Global Reach at www.glreach.com). One of the most significant innovations in the Internet since its incep- tion is the introduction of Internationalized Domain Names (IDNs) in the Internet’s address space. You may be familiar with some of the larger top- level domains: dot-com, dot-cn, and dot-org are just three examples. IDN top-level domain names will offer many new opportunities and benefits for Internet users around the world by allowing them to establish and use domains in their native languages and scripts.