Polyominoes, Permutominoes and Permutations Enrica Duchi
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Early Intercourse of the Franks and Danes. Part II Author(S): Henry H
The Early Intercourse of the Franks and Danes. Part II Author(s): Henry H. Howorth Reviewed work(s): Source: Transactions of the Royal Historical Society, Vol. 7 (1878), pp. 1-29 Published by: Royal Historical Society Stable URL: http://www.jstor.org/stable/3677882 . Accessed: 30/12/2012 11:59 Your use of the JSTOR archive indicates your acceptance of the Terms & Conditions of Use, available at . http://www.jstor.org/page/info/about/policies/terms.jsp . JSTOR is a not-for-profit service that helps scholars, researchers, and students discover, use, and build upon a wide range of content in a trusted digital archive. We use information technology and tools to increase productivity and facilitate new forms of scholarship. For more information about JSTOR, please contact [email protected]. Royal Historical Society is collaborating with JSTOR to digitize, preserve and extend access to Transactions of the Royal Historical Society. http://www.jstor.org This content downloaded on Sun, 30 Dec 2012 11:59:53 AM All use subject to JSTOR Terms and Conditions TRANSACTIONS OF THE ROYALHISTORICAL SOCIETY. THE EARLY INTERCOURSE OF THE FRANKS AND DANES. PART II. BY HENRY H. HOWORTH, ESQ., F.S.A., Fellow of the Royal HistoricalSociety. THERE is a passage in one of the Frankish annals which has not received the attentionwhich it deserves,and which I believe throws a great deal of light on the historyof the Danish revolutionsof the early part of the ninth century. This chronicle was writtenin verse by a Low Saxon monk some time during the reign of Arnulph, who died in 899. -

WOODRIDGE Providence Blaze D More Effort and .Sacrifice Are De World Situation at the Time the 26 Turee in Down Town Stantforgj Other Industries, It Was Said
The Wsathsr Average Daily Circnlation rO U B T E EN THURSDAY, DECEMBER 81,1942 Fore f t of C. a. Wratkor B aras iltm rhfBtrr iEii^nino Hpralb For the Montk wt Deeember. 1942 7,858 Moderate mow tonlgkt; little Ultutrhrfitrr Sarttlttg B rralb chango te temperataiow About Town Thomas Qiara MenriMr of tbo Audit and Prosperous Boreau of Clrculatlooa ^ Manchester——a, « Aa Cky.^s. oj. # Tr*flVillage____ Charm A daughter, Marilyn Elaine, wna To Get f 2,000 PRICE THREE CENTS THE TEA ROOM born Tuesday at the Hartford (TWELVE PAGES) hospital, to Captain and Mrs. Wal VOL. LXIL, NO. 78 Wi»he$ AU lit Friends ter Hooper of 751 Collins street. Well Known Local Real* East Hartford. Mrs. Hooper was dent Now in Army Re NEW YEAR the former Miss Beatrice Arnold A Very Happy of 300 Spruce street. membered in Will. High British Officers Given Soviet Army Drives Mrs. Elsie Wilhelm of 44 Wood- I Is Our Wish To You Allied Submarines bridge street has received word Mrs. M ary B reyer of 611 Cen ter street, who died December 10 i ------------------------- N E W YEAR from her son. Pvt. Walter C. Wil Honors by King George VI helm, U. S. M. C., to. the effect and waa buried In St. James's TONIGHT th a t he Is a t present som ewhere In cemetery on January 12, left to I Please Note— Store will be closed from Thurs- And Planes Score “No Wines — No Liquors — Just Good the Pacific. He enlisted in the Ma St. -

Bulletin 92 - Annual Catalogue 1925-1926 Eastern Illinois University
Eastern Illinois University The Keep Eastern Illinois University Bulletin University Publications 4-1-1926 Bulletin 92 - Annual Catalogue 1925-1926 Eastern Illinois University Follow this and additional works at: http://thekeep.eiu.edu/eiu_bulletin Recommended Citation Eastern Illinois University, "Bulletin 92 - Annual Catalogue 1925-1926" (1926). Eastern Illinois University Bulletin. 188. http://thekeep.eiu.edu/eiu_bulletin/188 This Article is brought to you for free and open access by the University Publications at The Keep. It has been accepted for inclusion in Eastern Illinois University Bulletin by an authorized administrator of The Keep. For more information, please contact [email protected]. 1: '3"CO."'C3 c na.- ~G c.or·~ The Teachers College Bulletin No. 92 April I, 1926 Eastern Illinois State Teachers College AT CHARLESTON .... ------.;.;==~= ::::: ·:: ... Twenty-seventh Ye~:r:=::::.::::: .=:· :':": ·:·:·· --------. .. ...... : :· .: .: .:.. ~ .:. ·: :. .. ... ······::.···::·.·.. ANNUAL CATALOGUE NUMBER 1925-1926 WITH ANNOUN~EMENTS FOR 1926-1927 The Teachers College Bulletin PGBLISHED QUARTERLY BY THE EASTERN ILLINOIS STATE TEACHERS COLLEGE AT CHARLESTON Entered March 5, 1902, as second-class matter, at the post office at Charleston, Illinois. Act of Congress, July 16, 1894 No. 92 CHARLESTON, ILLINOIS April 1, 1926 Eastern Illinois State Teachers College AT CHARLESTON ::::l"· .. ·.~ *"·' .,. .. .. • t • '9 " ... ~ •• : 't..... ~ :· :· Annual Catalogue Number i .. {:-~~f:: /~ :·:;. ... for the Twenty-seventh Year , 'I. ' ·.: • ~ -

Stockholm Diplomatic List
Stockholm Diplomatic List 9 September 2020 The Heads of Mission are requested to kindly communicate to the Chief of Protocol all changes related to personnel as they occur (arrivals, departures, promotions, new addresses etc.), so that they may be included in the next updated edition of the Diplomatic List. Ministry for Foreign Affairs Protocol Department Abbreviations: (S) = Swedish citizen (SB) = Permanent resident in Sweden (”stadigvarande bosatt”) Afghanistan August 19th - Independence Day Embassy of the Islamic Republic of Afghanistan Chancery: Skepparbacken 2B, Saltsjö-Duvnäs Tel: +46-(0)73-965 95 70 Postal Address: Fax: +46-(0)8-35 84 20 Källängstorget 10 Email: [email protected] 181 44 Lidingö Consular Section: Källängstorget 10 Tel: +46-(0)72-016 22 65 181 44 Lidingö Fax: +46-(0)8-35 84 18 Office hours: Mon-Fri 09.30-16.00 Email: [email protected] His Excellency Mr Ghulam Abbas NOYAN, Ambassador Extraordinary and Plenipotentiary (28.11.2019) Mrs Sidiqa NOYAN Mr Ahmad Zaher MAQSOODI, Counsellor (Deputy Head of Mission) Mrs Bnafsha MAQSOODI Ms Farima NAWABI, First Secretary Mr Ajmal AHMADZAI, Second Secretary Mrs Marwa AFZALZADA Mr Ahmad Saber ETEBAR, Second Secretary (Consular Section) Albania November 28th - Independence and Flag Day Embassy of the Republic of Albania Chancery: Capellavägen 7 Tel: +46-(0)8-731 09 20 Postal Address: Fax: +46-(0)8-767 65 57 Capellavägen 7 Email: [email protected] 181 32 Lidingö His Excellency Mr Virgjil KULE, Ambassador Extraordinary and Plenipotentiary (24.10.2018) Mr Albert JERASI, Minister-Counsellor Mrs Albana JERASI Ms Marsida KURTI, Second Secretary Colonel Arben DEMOLLARI, Defence Attaché (Berlin) Algeria November 1st - National Day Embassy of the People´s Democratic Republic of Algeria Chancery: Danderydsgatan 3-5 Tel: +46-(0)8-679 91 30 Postal Address: Tel: +46-(0)8-679 91 40 P.O. -

Papers of Surrealism, Issue 8, Spring 2010 1
© Lizzie Thynne, 2010 Indirect Action: Politics and the Subversion of Identity in Claude Cahun and Marcel Moore’s Resistance to the Occupation of Jersey Lizzie Thynne Abstract This article explores how Claude Cahun and Marcel Moore translated the strategies of their artistic practice and pre-war involvement with the Surrealists and revolutionary politics into an ingenious counter-propaganda campaign against the German Occupation. Unlike some of their contemporaries such as Tristan Tzara and Louis Aragon who embraced Communist orthodoxy, the women refused to relinquish the radical relativism of their approach to gender, meaning and identity in resisting totalitarianism. Their campaign built on Cahun’s theorization of the concept of ‘indirect action’ in her 1934 essay, Place your Bets (Les paris sont ouvert), which defended surrealism in opposition to both the instrumentalization of art and myths of transcendence. An examination of Cahun’s post-war letters and the extant leaflets the women distributed in Jersey reveal how they appropriated and inverted Nazi discourse to promote defeatism through carnivalesque montage, black humour and the ludic voice of their adopted persona, the ‘Soldier without a Name.’ It is far from my intention to reproach those who left France at the time of the Occupation. But one must point out that Surrealism was entirely absent from the preoccupations of those who remained because it was no help whatsoever on an emotional or practical level in their struggles against the Nazis.1 Former dadaist and surrealist and close collaborator of André Breton, Tristan Tzara thus dismisses the idea that surrealism had any value in opposing Nazi domination. -
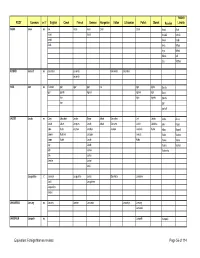
FOREIGN NAMES-Revised
Yiddish ROOT Common m / f English Czech French German Hungarian Italian Lithuanian Polish Slovak Russian / Jewish ISSAC Isaac m. Ike Isaac Isaac Izsak Izaak Isaak Aizik Isaac Isaak Issaaki Icchok Izaak Issak Isaak Zack Issia Itchok Isya Itzhak Itshak Izik Izia Yitzhak IUCUND Jocund m. Jocundas Juconde Giocondo Jukundas Joconde IVOR Ivor m. Evander Igor Igor Igor Ivo Igor Igino Gocha Igor Igorek Ingwar Igorek Igor Gora Ivar Igus Igorko Igocha Ivor Igor Igoriok JACOB Jacob m. Coby Jakoubek Jacob Diego Jakab Giacobbe Jak Jakub Iacha Akiva Jacob Jakub Jacques Jacob Jakob Giacomo Jakub Jokubko Iakiv Kapel Jake Kuba Jaymes Jacobus Jacopo Jakubek Kubo Iakov Koppel James Kubicek Jacques Jakusz Yakiv Yaakov Jamie Kubik Jacub Kuba Yakov Yakov Jay Jakob Yasha Yankel Jeb James Yashenka Jim Jasha Jimmie Jockel Jocki Jacqueline f. Jackalyn Jacqueline Jackie Giachetta Jakobina Jacki Jacquleine Jacqueline Jacqui JANUARIUS January m. January Janvier Januarius Januarijus January Januarek JAROPELK Jaropelk m. Jaropelk Yaropolk Equivalent Foreign Names-revised Page 56 of 114 Yiddish ROOT Common m / f English Czech French German Hungarian Italian Lithuanian Polish Slovak Russian / Jewish JAROMIR Jaromir m. Jarda Jaro Jarda Jaromir Jaromir Yaromir Jarek Jaromil Jaromiras Jaromir Jaromir Jarousek Mirek Mira Mirek JAROSLAW Jaroslaw m. Jerry Jarda Jaroslaw Jaroslavas Jarek Jarinko Iar Jarek Jaroslaw Jarino Iaroslav Jaroslav Jeske Jarko Slava Jarousek Jesko Jaro Yarik Slavek Jaroslav Yaroslav Jaroslawa f. Jarca Jaroslava Jaroslawa Jarka Iaroslava Jarka Jeroslawa Jaroslava Yaroslava Jaroslava Jarunka Jaruska Slavka JASPER Casper m. Caspar Gaspard Caspar Gaspar Gaspare Kasparas Gasparek Gaspar Jaspar Casper Gaspard Gazsi Gasparo Kacper Gaspar Jasper Kacper Jasper Jesper Kasper Kaspar Kasperek Equivalent Foreign Names-revised Page 57 of 114 Yiddish ROOT Common m / f English Czech French German Hungarian Italian Lithuanian Polish Slovak Russian / Jewish JOHANNES Ivan m. -

Arizona IASIS Preferred Physician Roster Updated 9/13/17
Arizona IASIS Preferred Physician Roster Updated 9/13/17 PRIMARY CARE PHYSICIANS Specialty Last Name First Name PCP ID Facility Name Address 1 Address 2 City St. Zip Phone FAMILY MEDICINE ALLEN GREGORY 1952380925 ALLEN FAMILY MEDICINE 7233 E BASELINE RD STE 126 MESA AZ 85209 (480) 699-2222 FAMILY MEDICINE BABARIA CHATUR 1568514404 QUEEN CREEK FAMILY MEDICINE 22707 S ELLSWORTH RD STE H103 QUEEN CREEK AZ 85142 (480) 677-3494 FAMILY MEDICINE BAILEY LINDA 1447658448 HEAVENS MEDICAL 105 S DELAWARE DR STE 1 &2 APACHE AZ 85120 (480) 646-1001 JUNCTION FAMILY MEDICINE BEACH JAMES 1053304808 43RD AVENUE MEDICAL 7725 N 43RD AVE STE 111 PHOENIX AZ 85051 (623) 931-9201 ASSOCIATES FAMILY MEDICINE BERRY BARBARA 1457411613 CENTRAL PHOENIX MEDICAL 7600 N 15TH ST STE 190 PHOENIX AZ 85020 (602) 200-3800 CLINIC LLC FAMILY MEDICINE BOTTNER MELVIN 1053304972 PHYSICIAN GROUP OF ARIZONA 1010 E UNIVERSITY DR MESA AZ 85203 (480) 844-1010 FAMILY MEDICINE BOTTNER MELVIN 1053304972 PHYSICIAN GROUP OF ARIZONA 1492 S MILL AVE STE 101 TEMPE AZ 85281 (480) 257-2727 FAMILY MEDICINE BOTTNER MELVIN 1053304972 PHYSICIAN GROUP OF ARIZONA 1495 E OSBORN RD PHOENIX AZ 85014 (602) 254-7554 FAMILY MEDICINE BOTTNER MELVIN 1053304972 PHYSICIAN GROUP OF ARIZONA 1968 E BASELINE RD STE F101 TEMPE AZ 85253 (480) 775-4110 FAMILY MEDICINE BOTTNER MELVIN 1053304972 PHYSICIAN GROUP OF ARIZONA 3330 N 2ND ST STE 502 PHOENIX AZ 85012 (602) 824-4400 FAMILY MEDICINE BOTTNER MELVIN 1053304972 PHYSICIAN GROUP OF ARIZONA 3340 W SOUTHERN AVE STE 131 PHOENIX AZ 85041 (623) 399-6214 FAMILY MEDICINE -

Non-Commutative Cryptography and Complexity of Group-Theoretic Problems
Mathematical Surveys and Monographs Volume 177 Non-commutative Cryptography and Complexity of Group-theoretic Problems Alexei Myasnikov Vladimir Shpilrain Alexander Ushakov With an appendix by Natalia Mosina American Mathematical Society http://dx.doi.org/10.1090/surv/177 Mathematical Surveys and Monographs Volume 177 Non-commutative Cryptography and Complexity of Group-theoretic Problems Alexei Myasnikov Vladimir Shpilrain Alexander Ushakov With an appendix by Natalia Mosina American Mathematical Society Providence, Rhode Island EDITORIAL COMMITTEE Ralph L. Cohen, Chair MichaelA.Singer Jordan S. Ellenberg Benjamin Sudakov MichaelI.Weinstein 2010 Mathematics Subject Classification. Primary 94A60, 20F10, 68Q25, 94A62, 11T71. For additional information and updates on this book, visit www.ams.org/bookpages/surv-177 Library of Congress Cataloging-in-Publication Data Myasnikov, Alexei G., 1955– Non-commutative cryptography and complexity of group-theoretic problems / Alexei Myas- nikov, Vladimir Shpilrain, Alexander Ushakov ; with an appendix by Natalia Mosina. p. cm. – (Mathematical surveys and monographs ; v. 177) Includes bibliographical references and index. ISBN 978-0-8218-5360-3 (alk. paper) 1. Combinatorial group theory. 2. Cryptography. 3. Computer algorithms. 4. Number theory. I. Shpilrain, Vladimir, 1960– II. Ushakov, Alexander. III. Title. QA182.5.M934 2011 005.82–dc23 2011020554 Copying and reprinting. Individual readers of this publication, and nonprofit libraries acting for them, are permitted to make fair use of the material, such as to copy a chapter for use in teaching or research. Permission is granted to quote brief passages from this publication in reviews, provided the customary acknowledgment of the source is given. Republication, systematic copying, or multiple reproduction of any material in this publication is permitted only under license from the American Mathematical Society. -

The Young King and the Old Count: Around the Flemish Succession Crisis of 965
This is a repository copy of The young king and the old count: Around the Flemish succession crisis of 965. White Rose Research Online URL for this paper: http://eprints.whiterose.ac.uk/140885/ Version: Accepted Version Article: McNair, FA (2018) The young king and the old count: Around the Flemish succession crisis of 965. Revue Belge de Philologie et de Histoire, 95 (2). pp. 145-162. ISSN 0035-0818 This article is protected by copyright. All rights reserved. This is an author produced version of a paper published in Revue Belge de Philologie et de Histoire. Uploaded with permission from the publisher. Reuse Items deposited in White Rose Research Online are protected by copyright, with all rights reserved unless indicated otherwise. They may be downloaded and/or printed for private study, or other acts as permitted by national copyright laws. The publisher or other rights holders may allow further reproduction and re-use of the full text version. This is indicated by the licence information on the White Rose Research Online record for the item. Takedown If you consider content in White Rose Research Online to be in breach of UK law, please notify us by emailing [email protected] including the URL of the record and the reason for the withdrawal request. [email protected] https://eprints.whiterose.ac.uk/ The Young King and the Old Count: Around the Flemish Succession Crisis of 965 Abstract: In 965, Count Arnulf the Great of Flanders died, leaving a small child as his only heir. In the wake of his death, the West Frankish King Lothar annexed his southern lands for the crown. -

CORRECTION HISTOIRE Charlemagne
CORRECTION HISTOIRE Charlemagne DOC 1 1.C’est la liste des règnes de tous les rois carolingiens (c’est-à-dire de Pépin Le Bref à Louis V) 2.Les rois ont été classés dans l’ordre chronologique de leur règne. 3.Le premier roi carolingien monte sur le trône en 752. Le règne du dernier roi carolingien se termine en 987. La dynastie carolingienne s’étend sur 235 ans. 4.C’est Charlemagne qui a régné le plus longtemps (43 ans) et le dernier roi carolingien est Louis V le Fainéant, il n’a régné qu’une année (986/987). 5.Les mots en italique désignent des particularités physiques, des traits de caractère ou des origines géographiques. Remarque : La règle de porter un nom de famille n’a été adoptée qu’au XIIe siècle. Elle s’est calquée sur l’habitude d’associer aux prénoms des particularités : - des traits de caractère : Lesage, Lebon, Gentil… - Des particularités physiques : Legros, Legrand, Leroux… - des lieux d’habitation : Deschamps, Desbois, Dupont… DOC 2 1.Charlemagne donne une impression d’autorité parce qu’il est très grand. 2.Il était en bonne santé parce qu’il se préoccupait de son hygiène de vie (bains, sport…) Ce qui était rare à cette époque. 3.Il a bâti son palais à Aix-La-Chapelle. 4.Cette ville se situe en Allemagne aujourd’hui. DOCS 3/4 1.Il s’agit d’un tableau (peinture) 2/3. Éléments importants à citer : - lourd manteau brodé, - tunique - couronne, - la longue épée à double tranchant (la puissance militaire) - la boule (emboitement de sphères concentriques : représentation symbolique de l’univers. -

Scalable Encryption Fingerprinting in Dynamic Malware Traces
KALI: Scalable Encryption Fingerprinting in Dynamic Malware Traces Lorenzo De Carli1 Ruben Torres2 Gaspar Modelo-Howard2 Alok Tongaonkar3 Somesh Jha4 1Colorado State University 2Symantec 3RedLock Inc. 4University of Wisconsin, Madison Abstract—Binary analysis of malware to determine uses of based on dynamic analysis of malware execution traces, which encryption is an important primitive with many critical applica- allows it to sidestep hurdles that are traditionally deployed tions, such as reverse-engineering of malware network commu- against static binary analysis, such as obfuscation and packing. nications and decryption of files encrypted by ransomware. The state of the art for encryption fingerprinting in dynamic execution Also, it works in a largely automated fashion, only requiring traces, the ALIGOT algorithm—while effective in identifying a access to a malware machine-level instruction trace, and can range of known ciphers—suffers from significant scalability limi- extract encryption keys and cleartexts. Internally, ALIGOT is tations: in certain cases, even analyzing traces of a few thousands based on the insight that loops are recurring structures in of machine instructions may require prohibitive time/space. In cipher implementations, therefore searching execution traces this work, we propose KALI, an enhanced algorithm based on ALIGOT which significantly reduces time/space complexity and for chains of dynamic loops. Once such chains have been increases scalability. Moreover, we propose a technique to focalize identified, each candidate chain is validated by comparing the analysis on encryption used for specific purposes, further its inputs and outputs against those of known ciphers. At improving efficiency. Results show that KALI achieves orders of the end of the process, each candidate is either discarded or magnitude reduction in execution time and memory utilization successfully matched to a known cipher. -

Ahnentafel of Guigues VI, Count D'albon
Ahnentafel of Guigues VI, Count d'Albon --- 1st Generation --- 1. Guigues VI, Count1 d'Albon (André Roux: Scrolls from his personal genealogicaL research. The Number refers to the family branch numbers on his many scrolls, 127.) (Roderick W. Stuart, Royalty for Commoners in ISBN: 0-8063-1344-7 (1001 North Calvert Street, Baltimore, MD 21202, USA: Genealogical Publishing Company, Inc., 1992), Page 146, Line 196-34.) (Paul Theroff, posts on the Genealogy Bulletin Board of the Prodigy Interactive Personal Service, was a member as of 5 April 1994, at which time he held the identification MPSE79A, until July, 1996. His main source was Europaseische Stammtafeln, 13 March 1995 at 18:58 Hours.). AKA: Guigues VI, Sire de Vion. Also Known As: Guigues "Le Vieux." AKA: Guigues VI, Count de Grenoble. AKA: Guigues I, Comte d'Albon Guigues abdicated in 1057 (P.D. Abbott, Provinces, Pays and Seigneuries of France in ISBN: 0- 9593773-0-1 (Author at 266 Myrtleford, 3737, Australia: Priries Printers Pty. Ltd, Canberra A.C.T., Australia, November, 1981), Page 581.). Born: circa 1001 at Albon, Dauphiné, France, son of Guigues V, Count de Vienne and Gotelenne de Clérieux, Some sources skip this generation. Married before 18 Oct 1013: Adélaïde=Alix de Beaujeu,, daughter of Guichard I, Seigneur de Beaujeu and Adelmodis N? Married before 1063: Adélaïde de Maurienne,, daughter of Odon dit Amé, Comte de Savoie and Adélaïde, Countess de Turin. Died: on 22 Apr 1063 at Cluny, Saône-et-Loire, Bourgogne, France, Guigues VI was a monk when he died (Stuart, Page 146, Line 196-34.).