Non-Commutative Cryptography and Complexity of Group-Theoretic Problems
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Early Intercourse of the Franks and Danes. Part II Author(S): Henry H
The Early Intercourse of the Franks and Danes. Part II Author(s): Henry H. Howorth Reviewed work(s): Source: Transactions of the Royal Historical Society, Vol. 7 (1878), pp. 1-29 Published by: Royal Historical Society Stable URL: http://www.jstor.org/stable/3677882 . Accessed: 30/12/2012 11:59 Your use of the JSTOR archive indicates your acceptance of the Terms & Conditions of Use, available at . http://www.jstor.org/page/info/about/policies/terms.jsp . JSTOR is a not-for-profit service that helps scholars, researchers, and students discover, use, and build upon a wide range of content in a trusted digital archive. We use information technology and tools to increase productivity and facilitate new forms of scholarship. For more information about JSTOR, please contact [email protected]. Royal Historical Society is collaborating with JSTOR to digitize, preserve and extend access to Transactions of the Royal Historical Society. http://www.jstor.org This content downloaded on Sun, 30 Dec 2012 11:59:53 AM All use subject to JSTOR Terms and Conditions TRANSACTIONS OF THE ROYALHISTORICAL SOCIETY. THE EARLY INTERCOURSE OF THE FRANKS AND DANES. PART II. BY HENRY H. HOWORTH, ESQ., F.S.A., Fellow of the Royal HistoricalSociety. THERE is a passage in one of the Frankish annals which has not received the attentionwhich it deserves,and which I believe throws a great deal of light on the historyof the Danish revolutionsof the early part of the ninth century. This chronicle was writtenin verse by a Low Saxon monk some time during the reign of Arnulph, who died in 899. -

Generic Global Rigidity in Complex and Pseudo-Euclidean Spaces 3
GENERIC GLOBAL RIGIDITY IN COMPLEX AND PSEUDO-EUCLIDEAN SPACES STEVEN J. GORTLER AND DYLAN P. THURSTON Abstract. In this paper we study the property of generic global rigidity for frameworks of graphs embedded in d-dimensional complex space and in a d-dimensional pseudo- Euclidean space (Rd with a metric of indefinite signature). We show that a graph is generically globally rigid in Euclidean space iff it is generically globally rigid in a complex or pseudo-Euclidean space. We also establish that global rigidity is always a generic property of a graph in complex space, and give a sufficient condition for it to be a generic property in a pseudo-Euclidean space. Extensions to hyperbolic space are also discussed. 1. Introduction The property of generic global rigidity of a graph in d-dimensional Euclidean space has recently been fully characterized [4, 7]. It is quite natural to study this property in other spaces as well. For example, recent work of Owen and Jackson [8] has studied the number of equivalent realizations of frameworks in C2. In this paper we study the property of generic global rigidity of graphs embedded in Cd as well as graphs embedded in a pseudo Euclidean space (Rd equipped with an indefinite metric signature). We show that a graph Γ is generically globally rigid (GGR) in d-dimensional Euclidean space iff Γ is GGR in d-dimensional complex space. Moreover, for any metric signature, s, We show that a graph Γ is GGR in d-dimensional Euclidean space iff Γ is GGR in d- dimensional real space under the signature s. -

A Generic Property of the Bounded Syzygy Solutions Author(S): Florin N
A Generic Property of the Bounded Syzygy Solutions Author(s): Florin N. Diacu Source: Proceedings of the American Mathematical Society, Vol. 116, No. 3 (Nov., 1992), pp. 809-812 Published by: American Mathematical Society Stable URL: http://www.jstor.org/stable/2159450 Accessed: 16/11/2009 21:52 Your use of the JSTOR archive indicates your acceptance of JSTOR's Terms and Conditions of Use, available at http://www.jstor.org/page/info/about/policies/terms.jsp. JSTOR's Terms and Conditions of Use provides, in part, that unless you have obtained prior permission, you may not download an entire issue of a journal or multiple copies of articles, and you may use content in the JSTOR archive only for your personal, non-commercial use. Please contact the publisher regarding any further use of this work. Publisher contact information may be obtained at http://www.jstor.org/action/showPublisher?publisherCode=ams. Each copy of any part of a JSTOR transmission must contain the same copyright notice that appears on the screen or printed page of such transmission. JSTOR is a not-for-profit service that helps scholars, researchers, and students discover, use, and build upon a wide range of content in a trusted digital archive. We use information technology and tools to increase productivity and facilitate new forms of scholarship. For more information about JSTOR, please contact [email protected]. American Mathematical Society is collaborating with JSTOR to digitize, preserve and extend access to Proceedings of the American Mathematical Society. http://www.jstor.org PROCEEDINGS OF THE AMERICAN MATHEMATICAL SOCIETY Volume 116, Number 3, November 1992 A GENERIC PROPERTY OF THE BOUNDED SYZYGY SOLUTIONS FLORIN N. -

WOODRIDGE Providence Blaze D More Effort and .Sacrifice Are De World Situation at the Time the 26 Turee in Down Town Stantforgj Other Industries, It Was Said
The Wsathsr Average Daily Circnlation rO U B T E EN THURSDAY, DECEMBER 81,1942 Fore f t of C. a. Wratkor B aras iltm rhfBtrr iEii^nino Hpralb For the Montk wt Deeember. 1942 7,858 Moderate mow tonlgkt; little Ultutrhrfitrr Sarttlttg B rralb chango te temperataiow About Town Thomas Qiara MenriMr of tbo Audit and Prosperous Boreau of Clrculatlooa ^ Manchester——a, « Aa Cky.^s. oj. # Tr*flVillage____ Charm A daughter, Marilyn Elaine, wna To Get f 2,000 PRICE THREE CENTS THE TEA ROOM born Tuesday at the Hartford (TWELVE PAGES) hospital, to Captain and Mrs. Wal VOL. LXIL, NO. 78 Wi»he$ AU lit Friends ter Hooper of 751 Collins street. Well Known Local Real* East Hartford. Mrs. Hooper was dent Now in Army Re NEW YEAR the former Miss Beatrice Arnold A Very Happy of 300 Spruce street. membered in Will. High British Officers Given Soviet Army Drives Mrs. Elsie Wilhelm of 44 Wood- I Is Our Wish To You Allied Submarines bridge street has received word Mrs. M ary B reyer of 611 Cen ter street, who died December 10 i ------------------------- N E W YEAR from her son. Pvt. Walter C. Wil Honors by King George VI helm, U. S. M. C., to. the effect and waa buried In St. James's TONIGHT th a t he Is a t present som ewhere In cemetery on January 12, left to I Please Note— Store will be closed from Thurs- And Planes Score “No Wines — No Liquors — Just Good the Pacific. He enlisted in the Ma St. -

Lids-R-904 Robust Stability of Linear Systems
LIDS-R-904 ROBUST STABILITY OF LINEAR SYSTEMS - SOME COMPUTATIONAL CONSIDERATIONS* by Alan J. Laub** 1. INTRODUCTION In this paper we shall concentrate on some of the computational issues which arise in studying the robust stability of linear systems. Insofar as possible, we shall use notation consistent with Stein's paper [11 and we shall make frequent reference to that work. As we saw in [1] a basic stability question for a linear time-invariant system with transfer matrix G(s) is the following: given that a nominal closed-loop feedbadk system is stable, does the feedback system remain stable when subjected to perturbations and how large can those perturba- tions be? It turned out, through invocation of the Nyquist Criterion, that the size of the allowable perturbations was related to the "nearness to singularity" of the return difference matrix I + G(jW). Closed-loop stability was said to be "robust" if G could tolerate considerable perturbation before I + G became singular. Invited Paper presented at the Second Annual Workshop on the Informa- tion Linkage between Applied Mathematics and Industry held at Naval Postgraduate School, Monterey, California, Feb. 20-24, 1979; this research was partially supported by NASA under grant NGL-22-009-124 and the Department of Energy under grant ET-78-(01-3395). ** Laboratory for Information and Decision Systems, Pm. 35-331, M.I.T., Cambridge, MA 02139. -2- We shall now indulge in a modicum of abstraction and attempt to formalize the notion of robustness. The definition will employ some jargon from algebraic geometry and will be applicable to a variety of situations. -

Bulletin 92 - Annual Catalogue 1925-1926 Eastern Illinois University
Eastern Illinois University The Keep Eastern Illinois University Bulletin University Publications 4-1-1926 Bulletin 92 - Annual Catalogue 1925-1926 Eastern Illinois University Follow this and additional works at: http://thekeep.eiu.edu/eiu_bulletin Recommended Citation Eastern Illinois University, "Bulletin 92 - Annual Catalogue 1925-1926" (1926). Eastern Illinois University Bulletin. 188. http://thekeep.eiu.edu/eiu_bulletin/188 This Article is brought to you for free and open access by the University Publications at The Keep. It has been accepted for inclusion in Eastern Illinois University Bulletin by an authorized administrator of The Keep. For more information, please contact [email protected]. 1: '3"CO."'C3 c na.- ~G c.or·~ The Teachers College Bulletin No. 92 April I, 1926 Eastern Illinois State Teachers College AT CHARLESTON .... ------.;.;==~= ::::: ·:: ... Twenty-seventh Ye~:r:=::::.::::: .=:· :':": ·:·:·· --------. .. ...... : :· .: .: .:.. ~ .:. ·: :. .. ... ······::.···::·.·.. ANNUAL CATALOGUE NUMBER 1925-1926 WITH ANNOUN~EMENTS FOR 1926-1927 The Teachers College Bulletin PGBLISHED QUARTERLY BY THE EASTERN ILLINOIS STATE TEACHERS COLLEGE AT CHARLESTON Entered March 5, 1902, as second-class matter, at the post office at Charleston, Illinois. Act of Congress, July 16, 1894 No. 92 CHARLESTON, ILLINOIS April 1, 1926 Eastern Illinois State Teachers College AT CHARLESTON ::::l"· .. ·.~ *"·' .,. .. .. • t • '9 " ... ~ •• : 't..... ~ :· :· Annual Catalogue Number i .. {:-~~f:: /~ :·:;. ... for the Twenty-seventh Year , 'I. ' ·.: • ~ -

Stockholm Diplomatic List
Stockholm Diplomatic List 9 September 2020 The Heads of Mission are requested to kindly communicate to the Chief of Protocol all changes related to personnel as they occur (arrivals, departures, promotions, new addresses etc.), so that they may be included in the next updated edition of the Diplomatic List. Ministry for Foreign Affairs Protocol Department Abbreviations: (S) = Swedish citizen (SB) = Permanent resident in Sweden (”stadigvarande bosatt”) Afghanistan August 19th - Independence Day Embassy of the Islamic Republic of Afghanistan Chancery: Skepparbacken 2B, Saltsjö-Duvnäs Tel: +46-(0)73-965 95 70 Postal Address: Fax: +46-(0)8-35 84 20 Källängstorget 10 Email: [email protected] 181 44 Lidingö Consular Section: Källängstorget 10 Tel: +46-(0)72-016 22 65 181 44 Lidingö Fax: +46-(0)8-35 84 18 Office hours: Mon-Fri 09.30-16.00 Email: [email protected] His Excellency Mr Ghulam Abbas NOYAN, Ambassador Extraordinary and Plenipotentiary (28.11.2019) Mrs Sidiqa NOYAN Mr Ahmad Zaher MAQSOODI, Counsellor (Deputy Head of Mission) Mrs Bnafsha MAQSOODI Ms Farima NAWABI, First Secretary Mr Ajmal AHMADZAI, Second Secretary Mrs Marwa AFZALZADA Mr Ahmad Saber ETEBAR, Second Secretary (Consular Section) Albania November 28th - Independence and Flag Day Embassy of the Republic of Albania Chancery: Capellavägen 7 Tel: +46-(0)8-731 09 20 Postal Address: Fax: +46-(0)8-767 65 57 Capellavägen 7 Email: [email protected] 181 32 Lidingö His Excellency Mr Virgjil KULE, Ambassador Extraordinary and Plenipotentiary (24.10.2018) Mr Albert JERASI, Minister-Counsellor Mrs Albana JERASI Ms Marsida KURTI, Second Secretary Colonel Arben DEMOLLARI, Defence Attaché (Berlin) Algeria November 1st - National Day Embassy of the People´s Democratic Republic of Algeria Chancery: Danderydsgatan 3-5 Tel: +46-(0)8-679 91 30 Postal Address: Tel: +46-(0)8-679 91 40 P.O. -

Papers of Surrealism, Issue 8, Spring 2010 1
© Lizzie Thynne, 2010 Indirect Action: Politics and the Subversion of Identity in Claude Cahun and Marcel Moore’s Resistance to the Occupation of Jersey Lizzie Thynne Abstract This article explores how Claude Cahun and Marcel Moore translated the strategies of their artistic practice and pre-war involvement with the Surrealists and revolutionary politics into an ingenious counter-propaganda campaign against the German Occupation. Unlike some of their contemporaries such as Tristan Tzara and Louis Aragon who embraced Communist orthodoxy, the women refused to relinquish the radical relativism of their approach to gender, meaning and identity in resisting totalitarianism. Their campaign built on Cahun’s theorization of the concept of ‘indirect action’ in her 1934 essay, Place your Bets (Les paris sont ouvert), which defended surrealism in opposition to both the instrumentalization of art and myths of transcendence. An examination of Cahun’s post-war letters and the extant leaflets the women distributed in Jersey reveal how they appropriated and inverted Nazi discourse to promote defeatism through carnivalesque montage, black humour and the ludic voice of their adopted persona, the ‘Soldier without a Name.’ It is far from my intention to reproach those who left France at the time of the Occupation. But one must point out that Surrealism was entirely absent from the preoccupations of those who remained because it was no help whatsoever on an emotional or practical level in their struggles against the Nazis.1 Former dadaist and surrealist and close collaborator of André Breton, Tristan Tzara thus dismisses the idea that surrealism had any value in opposing Nazi domination. -

Generic Flatness for Strongly Noetherian Algebras
Journal of Algebra 221, 579–610 (1999) Article ID jabr.1999.7997, available online at http://www.idealibrary.com on Generic Flatness for Strongly Noetherian Algebras M. Artin* Department of Mathematics, Massachusetts Institute of Technology, Cambridge, Massachusetts 02139 View metadata, citation and similar papersE-mail: at core.ac.uk [email protected] brought to you by CORE provided by Elsevier - Publisher Connector L. W. Small Department of Mathematics, University of California at San Diego, La Jolla, California 92093 E-mail: [email protected] and J. J. Zhang Department of Mathematics, Box 354350, University of Washington, Seattle, Washington 98195 E-mail: [email protected] Communicated by J. T. Stafford Received November 18, 1999 Key Words: closed set; critically dense; generically flat; graded ring; Nullstellen- satz; strongly noetherian; universally noetherian. © 1999 Academic Press CONTENTS 0. Introduction. 1. Blowing up a critically dense sequence. 2. A characterization of closed sets. 3. Generic flatness. 4. Strongly noetherian and universally noetherian algebras. 5. A partial converse. *All three authors were supported in part by the NSF and the third author was also supported by a Sloan Research Fellowship. 579 0021-8693/99 $30.00 Copyright © 1999 by Academic Press All rights of reproduction in any form reserved. 580 artin, small, and zhang 0. INTRODUCTION In general, A will denote a right noetherian associative algebra over a commutative noetherian ring R.LetR0 be a commutative R-algebra. If R0 is finitely generated over R, then a version of the Hilbert basis theorem 0 asserts that A ⊗R R is right noetherian. We call an algebra A strongly right 0 0 noetherian if A ⊗R R is right noetherian whenever R is noetherian. -
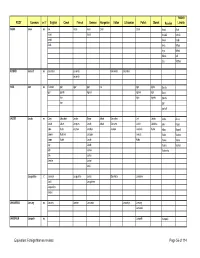
FOREIGN NAMES-Revised
Yiddish ROOT Common m / f English Czech French German Hungarian Italian Lithuanian Polish Slovak Russian / Jewish ISSAC Isaac m. Ike Isaac Isaac Izsak Izaak Isaak Aizik Isaac Isaak Issaaki Icchok Izaak Issak Isaak Zack Issia Itchok Isya Itzhak Itshak Izik Izia Yitzhak IUCUND Jocund m. Jocundas Juconde Giocondo Jukundas Joconde IVOR Ivor m. Evander Igor Igor Igor Ivo Igor Igino Gocha Igor Igorek Ingwar Igorek Igor Gora Ivar Igus Igorko Igocha Ivor Igor Igoriok JACOB Jacob m. Coby Jakoubek Jacob Diego Jakab Giacobbe Jak Jakub Iacha Akiva Jacob Jakub Jacques Jacob Jakob Giacomo Jakub Jokubko Iakiv Kapel Jake Kuba Jaymes Jacobus Jacopo Jakubek Kubo Iakov Koppel James Kubicek Jacques Jakusz Yakiv Yaakov Jamie Kubik Jacub Kuba Yakov Yakov Jay Jakob Yasha Yankel Jeb James Yashenka Jim Jasha Jimmie Jockel Jocki Jacqueline f. Jackalyn Jacqueline Jackie Giachetta Jakobina Jacki Jacquleine Jacqueline Jacqui JANUARIUS January m. January Janvier Januarius Januarijus January Januarek JAROPELK Jaropelk m. Jaropelk Yaropolk Equivalent Foreign Names-revised Page 56 of 114 Yiddish ROOT Common m / f English Czech French German Hungarian Italian Lithuanian Polish Slovak Russian / Jewish JAROMIR Jaromir m. Jarda Jaro Jarda Jaromir Jaromir Yaromir Jarek Jaromil Jaromiras Jaromir Jaromir Jarousek Mirek Mira Mirek JAROSLAW Jaroslaw m. Jerry Jarda Jaroslaw Jaroslavas Jarek Jarinko Iar Jarek Jaroslaw Jarino Iaroslav Jaroslav Jeske Jarko Slava Jarousek Jesko Jaro Yarik Slavek Jaroslav Yaroslav Jaroslawa f. Jarca Jaroslava Jaroslawa Jarka Iaroslava Jarka Jeroslawa Jaroslava Yaroslava Jaroslava Jarunka Jaruska Slavka JASPER Casper m. Caspar Gaspard Caspar Gaspar Gaspare Kasparas Gasparek Gaspar Jaspar Casper Gaspard Gazsi Gasparo Kacper Gaspar Jasper Kacper Jasper Jesper Kasper Kaspar Kasperek Equivalent Foreign Names-revised Page 57 of 114 Yiddish ROOT Common m / f English Czech French German Hungarian Italian Lithuanian Polish Slovak Russian / Jewish JOHANNES Ivan m. -

Arizona IASIS Preferred Physician Roster Updated 9/13/17
Arizona IASIS Preferred Physician Roster Updated 9/13/17 PRIMARY CARE PHYSICIANS Specialty Last Name First Name PCP ID Facility Name Address 1 Address 2 City St. Zip Phone FAMILY MEDICINE ALLEN GREGORY 1952380925 ALLEN FAMILY MEDICINE 7233 E BASELINE RD STE 126 MESA AZ 85209 (480) 699-2222 FAMILY MEDICINE BABARIA CHATUR 1568514404 QUEEN CREEK FAMILY MEDICINE 22707 S ELLSWORTH RD STE H103 QUEEN CREEK AZ 85142 (480) 677-3494 FAMILY MEDICINE BAILEY LINDA 1447658448 HEAVENS MEDICAL 105 S DELAWARE DR STE 1 &2 APACHE AZ 85120 (480) 646-1001 JUNCTION FAMILY MEDICINE BEACH JAMES 1053304808 43RD AVENUE MEDICAL 7725 N 43RD AVE STE 111 PHOENIX AZ 85051 (623) 931-9201 ASSOCIATES FAMILY MEDICINE BERRY BARBARA 1457411613 CENTRAL PHOENIX MEDICAL 7600 N 15TH ST STE 190 PHOENIX AZ 85020 (602) 200-3800 CLINIC LLC FAMILY MEDICINE BOTTNER MELVIN 1053304972 PHYSICIAN GROUP OF ARIZONA 1010 E UNIVERSITY DR MESA AZ 85203 (480) 844-1010 FAMILY MEDICINE BOTTNER MELVIN 1053304972 PHYSICIAN GROUP OF ARIZONA 1492 S MILL AVE STE 101 TEMPE AZ 85281 (480) 257-2727 FAMILY MEDICINE BOTTNER MELVIN 1053304972 PHYSICIAN GROUP OF ARIZONA 1495 E OSBORN RD PHOENIX AZ 85014 (602) 254-7554 FAMILY MEDICINE BOTTNER MELVIN 1053304972 PHYSICIAN GROUP OF ARIZONA 1968 E BASELINE RD STE F101 TEMPE AZ 85253 (480) 775-4110 FAMILY MEDICINE BOTTNER MELVIN 1053304972 PHYSICIAN GROUP OF ARIZONA 3330 N 2ND ST STE 502 PHOENIX AZ 85012 (602) 824-4400 FAMILY MEDICINE BOTTNER MELVIN 1053304972 PHYSICIAN GROUP OF ARIZONA 3340 W SOUTHERN AVE STE 131 PHOENIX AZ 85041 (623) 399-6214 FAMILY MEDICINE -

Generic Continuous Functions and Other Strange Functions in Classical Real Analysis
Georgia State University ScholarWorks @ Georgia State University Mathematics Theses Department of Mathematics and Statistics 4-17-2008 Generic Continuous Functions and other Strange Functions in Classical Real Analysis Douglas Albert Woolley Follow this and additional works at: https://scholarworks.gsu.edu/math_theses Part of the Mathematics Commons Recommended Citation Woolley, Douglas Albert, "Generic Continuous Functions and other Strange Functions in Classical Real Analysis." Thesis, Georgia State University, 2008. https://scholarworks.gsu.edu/math_theses/44 This Thesis is brought to you for free and open access by the Department of Mathematics and Statistics at ScholarWorks @ Georgia State University. It has been accepted for inclusion in Mathematics Theses by an authorized administrator of ScholarWorks @ Georgia State University. For more information, please contact [email protected]. GENERIC CONTINUOUS FUNCTIONS AND OTHER STRANGE FUNCTIONS IN CLASSICAL REAL ANALYSIS by Douglas A. Woolley Under the direction of Mihaly Bakonyi ABSTRACT In this paper we examine continuous functions which on the surface seem to defy well-known mathematical principles. Before describing these functions, we introduce the Baire Cate- gory theorem and the Cantor set, which are critical in describing some of the functions and counterexamples. We then describe generic continuous functions, which are nowhere differ- entiable and monotone on no interval, and we include an example of such a function. We then construct a more conceptually challenging function, one which is everywhere differen- tiable but monotone on no interval. We also examine the Cantor function, a nonconstant continuous function with a zero derivative almost everywhere. The final section deals with products of derivatives. INDEX WORDS: Baire, Cantor, Generic Functions, Nowhere Differentiable GENERIC CONTINUOUS FUNCTIONS AND OTHER STRANGE FUNCTIONS IN CLASSICAL REAL ANALYSIS by Douglas A.