Fastlane: Test Minimization for Rapidly Deployed Large-Scale Online Services
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Enterprise Best Practices for Ios Devices On
White Paper Enterprise Best Practices for iOS devices and Mac computers on Cisco Wireless LAN Updated: January 2018 © 2018 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 51 Contents SCOPE .............................................................................................................................................. 4 BACKGROUND .................................................................................................................................. 4 WIRELESS LAN CONSIDERATIONS .................................................................................................... 5 RF Design Guidelines for iOS devices and Mac computers on Cisco WLAN ........................................................ 5 RF Design Recommendations for iOS devices and Mac computers on Cisco WLAN ........................................... 6 Wi-Fi Channel Coverage .................................................................................................................................. 7 ClientLink Beamforming ................................................................................................................................ 10 Wi-Fi Channel Bandwidth ............................................................................................................................. 10 Data Rates .................................................................................................................................................... 12 802.1X/EAP Authentication .......................................................................................................................... -

Emerging Frontiers in Research and Innovation 2018 (EFRI-2018) (Nsf 17-578) |
This document has been archived and replaced by NSF 19-502. Emerging Frontiers in Research and Innovation 2018 (EFRI-2018) 1. Chromatin and Epigenetic Engineering (CEE) 2. Continuum, Compliant, and Configurable Soft Robotics Engineering (C3 SoRo) PROGRAM SOLICITATION NSF 17-578 REPLACES DOCUMENT(S): NSF 16-612 National Science Foundation Directorate for Engineering Emerging Frontiers and Multidisciplinary Activities Directorate for Biological Sciences Directorate for Computer & Information Science & Engineering Air Force Office of Scientific Research Letter of Intent Due Date(s) (required) (due by 5 p.m. submitter's local time): September 29, 2017 Preliminary Proposal Due Date(s) (required) (due by 5 p.m. submitter's local time): October 25, 2017 Full Proposal Deadline(s) (due by 5 p.m. submitter's local time): February 23, 2018 IMPORTANT INFORMATION AND REVISION NOTES Any proposal submitted in response to this solicitation should be submitted in accordance with the revised NSF Proposal & Award Policies & Procedures Guide (PAPPG) (NSF 18-1), which is effective for proposals submitted, or due, on or after January 29, 2018. SUMMARY OF PROGRAM REQUIREMENTS General Information Program Title: EMERGING FRONTIERS IN RESEARCH AND INNOVATION (EFRI): Chromatin and Epigenetic Engineering (CEE) and Continuum, Compliant, and Configurable Soft Robotics Engineering (C3 SoRo) Synopsis of Program: The Emerging Frontiers in Research and Innovation (EFRI) program of the NSF Directorate for Engineering (ENG) serves a critical role in helping ENG focus on -

FASTLANE NEXT GENERATION User Guide
Developed by TEI Software Development for Louisiana Economic Development FASTLANE NEXT GENERATION User Guide Contents About FASTLANE Next Generation ............................................................................................................... 4 Available Incentive Programs.................................................................................................................... 4 FASTLANE Next Generation Features ....................................................................................................... 4 How to Use FASTLANE Next Generation ....................................................................................................... 5 Account Registration ................................................................................................................................. 5 Login after new Registration ..................................................................................................................... 7 Log in with an account created in Old FASTLANE ..................................................................................... 8 Forgot Password ..................................................................................................................................... 10 Search Advance Data .............................................................................................................................. 12 Search Project Data ................................................................................................................................ -
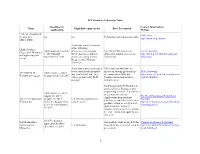
EPP Graduate Fellowship Table Name Deadline for Application
EPP Graduate Fellowship Table Deadline for Contact Information/ Name Eligibility requirements Brief Description Application Website CMU's Fellowship & CMU FSO Scholarship n/a n/a Fellowship and Scholarship Office http://www.cmu.edu/fso/ Office (FSO) Applicants must be from one of the following GEM: Graduate Application open on July underrepresented groups: For MS or PhD students in Gem Fellowship Degrees for Minorities 1, 2017 through Native American, African physical or natural sciences, or http://www.gemfellowship.org/gem- in Engineering and November 13, 2017. American, Latino, Puerto engineering. fellowship Science Rican, or other Hispanic American. Applicants must be nominated Ph.D. students who have an by doctoral faculty members interest in solving problems that IBM Fellowship The IBM Ph.D. Applications accepted and enrolled full-time in a are important to IBM and http://www.research.ibm.com/universi Fellowship Program through October 26,2017 college or university Ph.D. fundamental to innovation in ty/phdfellowship/ program. multiple areas. Students pursuing PhD studies in applied physics, biological and engineering sciences. US citizens Applications accepted or permanent residents. August 15, 2017 - The Hertz Foundation Fellowships Applications from students The Hertz Foundation October 27, 2017. U.S Citizens or permanent Brochure currently beyond their first year of Fellowships Reference Reports must resident aliens. http://hertzfoundation.org/fellowships/ graduate school are rarely acted be received by October, fellowshipaward upon favorably, and only 30, 2017. considered in cases of exceptional leverage. (Critical to apply to as a first year). 2018 Pre-doctoral Ford Foundation For graduate study in any field for National Academies Fellowship application deadline: Fellowship for U.S Minorities those planning a career in teaching http://sites.nationalacademies.org/pga/ December 14, 2017 Minorities or research. -

NSF Proposal and Award Policy Newsletter, Issue V, May 2018 (Nsf18078)
n ISSUE V n MAY n 2018 NATIONAL SCIENCE FOUNDATION Proposal & Award Policy Draft PAPPG Published in the What’s Federal Register for Public Comment Inside NSF recently published notice of the availability of the “For Comment” version of the Proposal and Award Policies and Procedures Guide (PAPPG) in the Draft PAPPG Published Federal Register. The draft PAPPG may be accessed on the NSF website. To in the Federal Register facilitate review, revised text has been highlighted in yellow throughout the Page 1 document and explanatory comments have been included in the margins, where appropriate. NSF greatly values the feedback that we receive from the research community Proposal Submission in and looks forward to receiving your comments. The 60-day comment period Research.gov is Here runs through July 13, 2018. n Page 1 Proposal Submission in Research.gov is Here NSF is pleased to announce that since April 30, 2018, proposers may now New Account Management System prepare and submit full, research non-collaborative proposals in Research. gov. The initial release of this new Research.gov capability runs in parallel with Page 2 existing FastLane proposal preparation and submission capabilities, so propos- ers can choose to prepare and submit full, research non-collaborative propos- als in Research.gov or in FastLane. Note that there will be no impact to Grants. Revision of NSF Award gov and Application Submission Web Services (ASWS), and NSF will continue Terms and Conditions to fully support these proposal submission methods. Currently there is not a Page 3 timeframe for full transition from FastLane to Research.gov, and both applica- tions will operate concurrently. -

National Science Foundation's Research.Gov Modernization
National Science Foundation's Research.gov Modernization Bill Daus Office of Information and Resource Management Division of Information Systems October 22, 2019 1 NSF Presenter Bill Daus Branch Chief Office of Information and Resource Management Division of Information Systems [email protected] 2 Upcoming NSF.gov, FastLane, and Research.gov Extended Outage • Systems unavailable Friday, November 8 at 8:00 PM EST until Tuesday, November 12 at 6:00 AM EST (Veteran’s Day weekend) • No access to NSF website, FastLane, and Research.gov • Proposals cannot be prepared or submitted in FastLane or Research.gov • Project reports and cash requests cannot be submitted in Research.gov • NSF is migrating its business applications to a modern and flexible platform, and making updates to correct text errors (e.g., special characters displaying as question marks in proposals and project reports) • Subscribe to our System Updates listserv to stay in the know! Sign up by sending a blank email to: system_updates- [email protected] to be automatically enrolled 3 Agenda • Why is NSF Modernizing Proposal Preparation and Submission? • Why Prepare Proposals in Research.gov? • What Features are Available Today and What’s Ahead? • Interactive Demo • Providing Feedback • Resources for More Information and FAQs • Q&A 4 Why is NSF Modernizing Proposal Preparation and Submission? *Results based on 16,736 responses from the June 2015 survey sent to 116,638 members of the research community The Problem Statement FastLane is… • Limited by outdated technology -

Federal Register/Vol. 82, No. 11/Wednesday, January 18, 2017
5970 Federal Register / Vol. 82, No. 11 / Wednesday, January 18, 2017 / Rules and Regulations § 490.411 Establishment of minimum level be classified as Structurally Deficient (c) For all bridges carrying the NHS, for condition for bridges. when one of its NBI Items, 58—Deck, which includes on- and off-ramps (a) State DOTs will maintain bridges 59—Superstructure, 60—Substructure, connected to the NHS and bridges so that the percentage of the deck area or 62—Culverts, is 4 or less, or when carrying the NHS that cross a State of bridges classified as Structurally one of its NBI Items, 67—Structural border, FHWA shall calculate a ratio of Deficient does not exceed 10.0 percent. Evaluation or 71—Waterway Adequacy, the total deck area of all bridges This minimum condition level is is 2 or less. Beginning with calendar classified as Structurally Deficient to the applicable to bridges carrying the NHS, year 2018 and thereafter, a bridge will total deck area of all applicable bridges which includes on- and off-ramps be classified as Structurally Deficient for each State. The percentage of deck connected to the NHS within a State, when one of its NBI Items, 58—Deck, area of bridges classified as Structurally and bridges carrying the NHS that cross a State border. 59—Superstructure, 60—Substructure, Deficient shall be computed by FHWA (b) For the purposes of carrying out or 62—Culverts, is 4 or less. to the one tenth of a percent as follows: this section and § 490.413, a bridge will Where: § 490.413 Penalties for not maintaining DEPARTMENT OF TRANSPORTATION Structurally Deficient = total number of the bridge condition. -

2021 SEASON SCHEDULE 16-18 Dodge Mile-High NHRA Nationals Presented by Pennzoil APRIL 21 CSP “Take It to the Track” Test Night 8 Kinsco/Code 3 Jr
2021 SEASON SCHEDULE 16-18 Dodge Mile-High NHRA Nationals presented by Pennzoil APRIL 21 CSP “Take it to the Track” Test Night 8 Kinsco/Code 3 Jr. Dragster Test 23 Kinsco Friday E.T. Series 9 Crossroads Trailer Jr. Drag Racing Series 24 US Recognition Saturday E.T. Series/Sunoco King Street 10 Test & Tune 25 Painter’s Grinding Colorado Bug-In/JR Race Car Titan 16 11 Test & Tune 26-28 Frank Hawley Drag Racing School 17 Test & Tune 28 CSP “Take it to the Track” Test Night 18 Test & Tune 30 PSCA Day Test (AM) Kinsco Friday E.T. Series/PSCA 21 CSP “Take it to the Track” Test Night Qualifying (PM) 23 Day Test (AM) Kinsco Friday E.T. Series (PM) 31 Madcap Racing Engines Fast 16/Get Biofuel Quick 16/ 24 US Recognition Saturday E.T. Series Fineline Series/MagnaFuel Super Series/Fastlane 25 US Recognition Saturday E.T. Series Automotive Stick Shift/PSCA/VDRA Qualifying 28 CSP “Take it to the Track” Test Night 30 Club Clash presented by Corvette Connection AUGUST 1 Fun Ford Series powered by your local Ford Stores/VDRA M AY Eliminations 1 Randy Coy & Son’s Denver Auto & Parts Swap Meet/ 4 CSP “Take it to the Track” Test Night Crossroads Trailer Jr. Drag Racing Series 6 Club Clash presented by Corvette Connection 2 Truck Invasion – Famouz Fadez & Tattz 7 Ultimate Call Out/Northwest Dyno Circuit 4 Race Car Test Night 8 Crossroads Trailer Jr. Drag Racing Series/Sunoco King Street 5 CSP “Take it to the Track” Test Night 11 CSP “Take it to the Track” Test Night 7 Kinsco Friday E.T. -

DEPARTMENT of TRANSPORTATION Office of the Secretary of Transportation Docket No. DOT-OST-2016-0022 Notice of Funding Opportunit
DEPARTMENT OF TRANSPORTATION Office of the Secretary of Transportation Docket No. DOT-OST-2016-0022 Notice of Funding Opportunity for the Department of Transportation’s Nationally Significant Freight and Highway Projects (FASTLANE Grants) for Fiscal Year 2016 AGENCY: Office of the Secretary of Transportation, DOT ACTION: Notice of Funding Opportunity SUMMARY: The Fixing America’s Surface Transportation Act (FAST Act) established the Nationally Significant Freight and Highway Projects (NSFHP) program to provide Federal financial assistance to projects of national or regional significance and authorized the program at $4.5 billion for fiscal years (FY) 2016 through 2020, including $800 million for FY 2016 to be awarded by the Secretary of Transportation. The Department will also refer to NSFHP grants as Fostering Advancements in Shipping and Transportation for the Long-term Achievement of National Efficiencies (FASTLANE) grants. The purpose of this notice is to solicit applications for FY 2016 grants for the NSFHP program. The Department also invites interested parties to submit comments about this notice’s contents to public docket DOT-OST-2016-0022 by June 1, 2016. DATES: Applications must be submitted by 8:00 p.m. EDT on April 14, 2016. The Grants.gov “Apply” function will open by March 15, 2016. ADDRESSES: Applications must be submitted through www.Grants.gov. Only applicants who comply with all submission requirements described in this notice and submit applications through www.Grants.gov will be eligible for award. FOR FURTHER INFORMATION CONTACT: For further information concerning this notice, please contact the Office of the Secretary via email at [email protected]. -

BRKEWN-2670.Pdf
#CLUS Wireless Best Practices for Next-gen Workspace Aparajita Sood, Technical Marketing Engineer BRKEWN-2670 #CLUS Cisco Webex Teams Questions? Use Cisco Webex Teams (formerly Cisco Spark) to chat with the speaker after the session How 1 Find this session in the Cisco Events App 2 Click “Join the Discussion” 3 Install Webex Teams or go directly to the team space 4 Enter messages/questions in the team space Webex Teams will be moderated cs.co/ciscolivebot#BRKEWN-2670 by the speaker until June 18, 2018. #CLUS © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public 3 #CLUS © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public The Enterprise Becomes Social Customer & Employee Collaboration Work Styles Have Evolved Work anytime from anywhere “Work is a thing you do, not a place you go to” Video Becomes Pervasive Across All Devices Any Time, Any Place What Do You Consider First? #CLUS BRKEWN-2670 © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public 6 Agenda Design Provision Optimize Assurance • Designing for Performance and Resiliency • Provisioning with Best Practices • Optimizing RF and Security • Assurance and Analytics #CLUS BRKEWN-2670 © 2018 Cisco and/or its affiliates. All rights reserved. Cisco Public 7 Deployment Lifecycle The Bigger Picture Design Provision Optimize Assurance Planning Easy Setup Operate Analytics • Mobility Design • Express Setup • Optimizing RF • Workspace Guides • Plug and Play • Prioritize Apps Analytics • Data Sheets • RF Planner • Best Practices • Segment and • Monitoring and • Site Survey Secure Real time Diagnostics #CLUS BRKEWN-2670 © 2018 Cisco and/or its affiliates. All rights reserved. -

2020 Topps WWE Wrestlemania Checklist
BASE BASE CARDS Lince Dorado™ & Gran Metalik™ def. Buddy 1 Murphy™ & Tony Nese™ 205 Live® 2 Buddy Murphy™ def. CedricKalisto™ Alexander™ for 205 Live® 3 WWE®the WWE® Cruiserweight Cruiserweight Champion Championship Buddy Super Show-Down® 4 WWE®Murphy™ Cruiserweight def. Mustafa Champion Ali™ Buddy Survivor Series® 2018 5 Murphy™ def. Cedric Alexander™ TLC: Tables, Ladders & Chairs® 2018 6 Noam Dar™ def. Tony Nese™ 205 Live® 7 Buddy Murphy™ Retainsdef. Humberto the WWE® Carrillo™ 205 Live® 8 TonyCruiserweight Nese™ def. Championship Noam Dar™ in in a aFatal No- 4-Way Royal Rumble® 2019 9 WWE®Disqualification Cruiserweight Match Champion Buddy 205 Live® 10 TonyMurphy™ Nese™ def. def. Akira Kalisto™ Tozawa™ in the First Round Elimination Chamber® 2019 11 Tonyof the Nese™ WWE® def. Cruiserweight Drew Gulak™ Championship in the WWE® 205 Live® 12 TonyCruiserweight Nese™ def. Championship Cedric Alexander™ No. 1 Contender in the 205 Live® 13 TonyWWE® Nese™ Cruiserweight def. Buddy Championship Murphy™ for No. the 1 205 Live® 14 UniversalWWE® Cruiserweight Champion Roman Championship Reigns™ def. Finn WrestleMania® 35 15 IntercontinentalBálor™ Champion Seth Rollins™ def. Raw® 16 DolphKevin Owens™Ziggler™ & Drew McIntyre™ Retain the Raw® 17 BrockRaw® Lesnar™ Tag Team Decimates Championship Roman Reigns™ Hell in a Cell® 2018 18 Raw®and Braun Tag Strowman™Team Champions Dolph Ziggler™ Hell in a Cell® 2018 19 Seattle& Drew HatesMcIntyre™ The Elias™ def. The & Kevin Revival™ Owens™ Raw® 20 Show Raw® 21 RomanTriple H® Reigns™ def. Undertaker® Must Relinquish the Universal Super Show-Down® 22 DolphChampionship Ziggler™ def. Kurt Angle™ in a WWE® Raw® 23 BrockWorld Lesnar™Cup Quarterfinals def. -

2018 WWE Women's Division Checklist V1
BASE ROSTER UPDATES Card Number Team 1 Alexa Bliss WWE 2 Alicia Fox WWE 3 Asuka WWE 4 Bayley WWE 5 Becky Lynch WWE 6 Brie Bella WWE 7 Carmella WWE 8 Cathy Kelley WWE 9 Charlotte Flair WWE 10 Charly Caruso WWE 11 Dana Brooke WWE 12 Dasha Fuentes WWE 13 JoJo WWE 14 Lana WWE 15 Liv Morgan WWE 16 Mandy Rose WWE 17 Maria Kanellis WWE 18 Maryse WWE 19 Mickie James WWE 20 Naomi WWE 21 Natalya WWE 22 Nia Jax WWE 23 Nikki Bella WWE 24 Renee Young WWE 25 Ronda Rousey WWE 26 RuBy Riott WWE 27 Sarah Logan WWE 28 Sasha Banks WWE 29 Sonya Deville WWE 30 Stephanie McMahon WWE 31 Tamina WWE 32 Aliyah NXT 33 Bianca Belair NXT 34 Billie Kay NXT 35 Candice LeRae NXT 36 Dakota Kai NXT 37 Ember Moon NXT 38 Kairi Sane NXT 39 Kayla Braxton NXT 40 Lacey Evans NXT 41 Nikki Cross NXT 42 Peyton Royce NXT 43 Shayna Baszler NXT 44 Taynara Conti NXT 45 Vanessa Borne NXT 46 Zelina Vega NXT 47 Alundra Blayze WWE Legends 48 Lita WWE Legends 49 Trish Stratus WWE Legends 50 Wendi Richter WWE Legends MEMORABLE MATCHES AND MOMENTS Card Number Team Card Title NXT-1 NXT® EmBer Moon™ Defeats Liv Morgan™ NXT-2 NXT TakeOver®: San Antonio Asuka™ Defeats Billie Kay™, Peyton Royce™ and Nikki Cross™ NXT-3 NXT® Asuka™ Defeats Peyton Royce™ to retain the NXT® Women's Championship NXT-4 NXT® RuBy Riott™ Makes her NXT® DeBut NXT-5 NXT TakeOver®: Orlando NXT® Women's Champion Asuka™ Defeats EmBer Moon™ NXT-6 NXT® Asuka™ Crashes the NXT® Women's Championship No.