Theft Deterrent Deployment Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Designed to Engage Students and Empower Educators
PRODUCT BRIEF Intel® classmate PC – Convertible Intel® Celeron® Processors 847/NM70 (dual-core) Part of Intel® Education Solutions Designed to Engage Students and Empower Educators Designed to make learning more fun, creative, and engaging, the Intel® classmate PC – convertible brings together the best of Windows* 8 touch and keyboard experiences, the amazing performance of Intel® Celeron® processors, and Intel® Education Software. The new Intel classmate PC – convertible keeps students excited about learning. With the flip of the display, it quickly transforms from a full-featured PC to convenient tablet—with pen— making it easy to adapt the device to the teaching method and learning task at hand. Whether gathering field data with the HD camera and notating it with the pen, or analyzing, interpreting, and reporting results using collaborative Intel Education Software, the convertible classmate “The Intel classmate PC – convertible PC is designed for education and engineered for students to develop the 21st century skills needed to succeed in today’s global economy. creates an ecosystem of digital learning which encompasses 1:1 Highlights: technologies, independent learning, • Two devices in one: tablet and full-feature PC digital creativity, device management, • Supports both Windows 8 desktop and touch modes and learning beyond school. It is truly • Together with Intel Education Software, the convertible classmate PC is part of Intel Education Solutions versatile, easily catering for the • High Definition LCD display produces vivid -
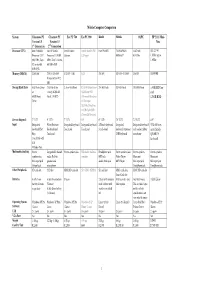
Mobile Computer Comparison
Mobile Computer Comparison System Classmate PC Classmate PC Eee PC 700 Eee PC 900 Kindle Mobilis OLPC HP 2133 Mini- Version 1.5 Version 1.5 Note 1st Generation 2nd Generation Processor (CPU) Intel ® Mobile Intel ® Mobile Intel® Mobile Intel® Mobile CPU Intel PXA255 TI OMAP2431 AMD x86 VIA C7-M Processor ULV Processor ULV 900 Celeron & Chipset 400MHz** 433 MHz 1.0Ghz up to 900 MHz, Zero MHz, Zero L2 cache, 1.6Ghz L2 cache, 400 400 MHz FSB MHz FSB Memory (DRAM) 256 RAM DDR ‐II 256 MB 512 MB ‐ 1GB 1GB 256 MB 128 MB – 512 MB 256 MB 1024 MB (Linux only)or 512 MB Storage/Hard Drive 4GB Flash Drive 1 GB Flash (for 2, 4, or 8GB Flash 12GB (4GB built‐in + 256 MB Flash 128 MB Flash 1024 MB Flash a 4GB SSD low or Linux), 2GB/4GB 8GB flash) SSD end 40GB Hard Flash, 1.8 HDD (Microsoft Windows 120GB HDD Drive OS Version) 20GB (4GB built‐in +16GB flash) SSD (Linux OS Version) Screen (diagonal) 7” LCD 9ʺ LCD 7ʺ LCD 8.9ʺ 6” LCD 7.0ʺ LCD 7.5ʺ LCD 8.9" Input Integrated Water Resistent Integrated keyboard Integrated keyboard 2‐Thumb keyboard Integrated Integrated keyboard 92% full-size, keyboard Hot Keyboard and Touch pad Touch pad Scroll wheel keyboard/ Optional with sealed rubber user-friendly Keys Touchpad USB Keyboard membrane QWERTY Touch Pad with keyboard L/R Wireless Pen Multimedia (built in) Stereo Integrated 2 channel Stereo speakers/mic HD audio / built‐in Headphone jack Stereo speakers/mic Stereo speakers Stereo speakers speakers/mic audio, Built‐in speakers MP3 jack Video Player Mono mic Mono mic Mic input jack speaker and Audio book jack MP3 -

2008 Corporate Responsibility Report
2008 Corporate Responsibility Report What can we make possible? A world of possibilities. LETTER FROM OUR CEO Throughout our 40-year history, Intel has pushed the boundaries of innovation, creating products that have fundamentally changed the way people live and work. But what we make possible goes well beyond our product roadmap. By working with others, we are finding opportunities to apply our technology and expertise to help tackle some of the world’s greatest challenges—from climate change and water conservation to education quality and the digital divide. Our commitment to corporate responsibility is unwavering, even during economic downturns. In education, we surpassed the milestone of training 6 million teachers worldwide through the Taking a proactive, integrated approach to managing our impact on local communities and the Intel® Teach Program. In addition, we partnered with governments to support the advancement environment not only benefits people and our planet, but is good for our business. Making of their education programs, and helped put affordable, portable, Intel-powered classmate PCs corporate responsibility an integral part of Intel’s strategy helps us mitigate risk, build strong into the hands of students in close to 40 countries. We announced a joint business venture with relationships with our stakeholders, and expand our market opportunities. Grameen Trust, using a “social business” model aimed at applying tech nology to address issues related to education, poverty, and healthcare in developing countries. While I am proud of the many recognitions that we have received—including our number one spot on Corporate Responsibility Officer magazine’s 100 Best Corporate Citizens list for At the heart of our commitment to corporate responsibility are Intel’s more than 80,000 2008—we continue to push ourselves to do more. -

E09EI6 English Manual 1
Technology Companion PC i Technology Companion PC Preface Copyright 2008 All Rights Reserved. The information in this document is subject to change without prior notice in order to improve reliability, design and function and does not represent a commitment on the part of the manufacturer. In no event will the manufacturer be liable for direct, indirect, special, incidental, or consequential damages arising out of the use or inability to use the product or documentation, even if advised of the possibility of such damages. This document contains proprietary information protected by copyright. All rights are reserved. No part of this manual may be form without prior written permission of the manufacturer. Limitation of Liability While reasonable efforts have been made to ensure the accuracy of this manual, the manufacturer and distributor assume no liability resulting from errors or omissions in this manual, or from the use of the information contained herein. i Technology Companion PC Table of Content ATTENTION: TEACHERS, PARENTS AND ADULT SUPERVISORS .................1 AGENCY REGULATORY NOTICES ...................................................3 MODIFICATIONS...................................................................................4 CONNECTIONS TO PERIPHERAL DEVICES..............................................4 SAR EXPOSURE .................................................................................4 DECLARATION OF CONFORMITY............................................................4 EUROPEAN NOTICE .............................................................................4 -

Affordable Computing for Schools in Developing Countries a Total Cost of Ownership (TCO) Model for Education Officials
Affordable Computing for Schools in Developing Countries A Total Cost of Ownership (TCO) Model for Education Officials Executive Summary Education decision-makers face the challenge of equipping young people with the skills necessary to compete in the global economy and need information and tools for formulating effective policy. This white paper discusses key issues related to technology in education and presents several major findings, including: • Academic research and private-sector investment decisions indicate that computers in schools contribute to improved academic outcomes, boost a nation’s economic competitiveness, and attract job-creating economic investments. • Governments need to consider the entire cost of school computing solutions, rather than merely the initial expenses. A total cost of ownership model takes into account recurrent and hidden costs such as teacher training, support and maintenance, and the cost of replacing hardware over a five-year period. • Support and training are recurrent costs that constitute two of the three largest costs in the total cost of ownership model. They are greater than hardware costs and much higher than software fees. • Ultra-low cost computers and Linux-based solutions are relatively equal in cost to traditional hardware and proprietary software solutions because they require higher labor and replacement costs over a five- year period. • The total cost of ownership for different computer types and software platforms is relatively consistent. Critical success factors, such as IT ecosystems and platform stability and longevity therefore need to be considered in affordable computing decisions. Introduction Developing-country education budgets are increasingly strained by greater numbers of young people and rising expectations among students and global markets. -

Performance That Makes Learning Take Flight
PRODUCT BRIEF Intel® classmate PC − clamshell Intel® Celeron® Processors 807/847 (single- and dual-core options) Part of the Intel® Learning Series Performance That Makes Learning Take Flight The Fast, Engaging Classroom PC The Intel® classmate PC – clamshell meets the requirements of educators, administrators, and school IT staff for rugged, powerful, student-friendly 1:1 eLearning. It features responsive performance for engaging educational experiences and a stunning visual interface with the Windows* 8 operating system. • Amazing performance. This Intel classmate PC is based on the Intel® Celeron® processor, which delivers responsive performance and a rich visual experience. Whether watching educational videos, playing learning games, or jumping to the web for research, students will find that the Intel classmate PC moves as fast as their minds. “Digital inclusion brings about a • Windows* 8 experience. The Intel classmate PC – clamshell is the perfect platform for level playing field. It means that running the new Windows 8 operating system, which provides a graphical, easy-to-use interface and improved performance. When combined with the Intel Celeron processor, the little girl in a village in Nigeria Windows 8 provides blazing performance for boot-up, hibernation wakeup, web browsing, can get the same information for audio and video file encoding, and everything else your students do. The stunning combina- tion of Windows 8 and Intel Learning Series design enhances education and enlivens learning her research project as a little while preserving your existing technology investments. girl in Washington or China.” Clamshell classmate PCs come equipped with pre-loaded content, are fully interoperable with school networks and infrastructures, and are excellent vehicles for 1:1 eLearning and 21st Turner Isoun, Minister of Science and Technology, Nigeria century skill development. -

Dell Vs. Competitors: Netbook Abrasion and Solvent Resistance a Principled Technologies Test Report 2
DELL VS. COMPETITORS: NETBOOK ABRASION AND SOLVENT RESISTANCE RESISTANCE OUR FINDINGS OUR PROCESS In today’s educational environment, institutions are To gauge the durability of each netbook system, we eager to get the most for their computing dollar, performed a custom abrasion resistance test, in which which means buying systems that last. In Principled we measured the physical damage that resulted when Technologies’ tests in our labs, as the above graphic we dragged each netbook across a ceramic tile floor. shows, the Dell Latitude 2110 netbook is more We also conducted a solvent spill test to determine resistant to abrasion and solvents than its closest how well the systems could withstand exposure to competitors are. The ability of the Dell Latitude 2110 various solvents that we spilled on a closed lid. to withstand abrasion and solvent spills make it an excellent choice for an educational institution, where netbooks need to last. JUNE 2010 A PRINCIPLED TECHNOLOGIES TEST REPORT Commissioned by Dell Inc. PROJECT OVERVIEW We tested the abrasion and solvent resistance of the following 10 netbook systems: Acer® Aspire® One 532h Apple® iPad™ ASUS® Eee PC 1001P ASUS Eee PC 1201T Dell™ Latitude™ 2110 Equus® NOBi Convertible HP Mini 2102 Lenovo® IdeaPad® S10-3 Lenovo IdeaPad S10-3t Lenovo ThinkPad® X100e To test the exterior scratch resistance of the netbooks, we dragged each across a commercial-grade ceramic tile floor. We completed three runs, and had a panel of three judges make their assessments after each run. Judges assigned a score of 1 to 5 for least to most scratches, which we then averaged for each test run. -

The OLPC XO, Intel Classmate PC and Asus Eee PC User Study
The OLPC XO, Intel Classmate PC and Asus Eee PC user study Submitted in partial fulfilment Of the requirements of the degree of Bachelor of Science (Honours) Of Rhodes University Constance Sibanda Grahamstown, South Africa November 2009 i Abstract Information communication technologies (ICTs) are increasingly considered valuable tools in education, promoting higher cognitive processes and allowing teachers and learners access to a wealth of information. However, these technologies are not easily accessible in developing countries such as South Africa, where a large percentage of the population are poor and are said to live below the breadline. The recent creation of small, low cost and low powered laptops called netbooks, are seen as possible solutions to allow or promote the use and integration of ICTs in education in these disadvantaged communities. This project evaluates the intuitiveness of the OLPC XO, the Intel Classmate and the Asus Eee PC in the context of secondary school education through the use of a user study. The user study involved three teachers and three learners from local secondary schools in Grahamstown. The results of the user study revealed that the teachers and learners (on the whole) felt that the Intel Classmate is the most intuitive netbook for secondary school learners involved in the user study. The presence of the VGA port and the portable nature of the Asus Eee were noted by participants as advantageous. The Asus Eee was also found to be appropriate for secondary school education although it was criticised for its small screen, small keyboard and absence of a webcam. Participants felt that the OLPC XO is less intuitive for secondary school educational purposes and is better suited for small children. -

2010 Corporate Responsibility Report at Intel, We Never Stop Looking for Bold Ideas in Technology, Business, Manufacturing, and Corporate Responsibility
2010 Corporate Responsibility Report At Intel, we never stop looking for bold ideas in technology, business, manufacturing, and corporate responsibility. Amazing things happen with Intel Inside.® In this report, we discuss our corporate responsibility performance during 2010, including our strategic approach to key environmental, social, and governance indicators. We prepared this report using the Global Reporting Initiative* (GRI) G3.1 guidelines, and we self-declare the report at the GRI Application Level A. On the cover: The “visibly smart” 2nd generation “ Corporate social responsibility is no longer optional for business leaders. I am very proud of Intel’s Intel® Core™ processor family features built-in long history of transparency and leadership in this area, and for the actions taken by employees graphics that enable a richer, higher in 2010 to push to higher levels of performance; we continue to extend our impact worldwide, performance computing with our education programs and driving energy efficiency in our products.” experience while efficiently managing Jane E. Shaw, Chairman of the Board power use. Letter from our C e o Throughout Intel’s history, we have pushed the boundaries of what’s possible to improve how people work, live, and play. Our vision for the next decade is even more ambitious: to create and extend computing technology to connect and enrich the lives of every person on earth. A key determinant of our success will be our ability to innovate and advance our leadership in corporate responsibility. At Intel, we don’t separate corporate responsibility from our business. One of the four $1 billion to improve education globally, partnering with educators, governments, and other objectives in our global strategy is, “Care for our people and our planet, and inspire the next companies to develop a range of transformative programs and technology solutions. -

Avaliação Experimental De Redes Mesh Com Os Classmate Pcs Da Intel Experimental Evaluation of Wireless Mesh Network with the Intel Classmate Pcs
Revista de Gestão da Tecnologia e Sistemas de Informação Journal of Information Systems and Technology Management Vol. 5, No. 2, 2008, p.235-250 ISSN online: 1807-1775 AVALIAÇÃO EXPERIMENTAL DE REDES MESH COM OS CLASSMATE PCS DA INTEL EXPERIMENTAL EVALUATION OF WIRELESS MESH NETWORK WITH THE INTEL CLASSMATE PCS Jorge R. Beingolea Garay Escola Politécnica da Universidade de São Paulo – USP Roberto K. Hiramatsu Escola Politécnica da Universidade de São Paulo – USP Sergio T. Kofuji Escola Politécnica da Universidade de São Paulo – USP Roseli de Deus Lopes Escola Politécnica da Universidade de São Paulo – USP _____________________________________________________________________________________ ABSTRACT This paper shows performance evaluation results of a wireless mesh network employing an 802.11s standard and low cost Intel Classmate PCs. The experiments consist of throughput and coverage range determination, in indoor and outdoor scenarios, in which net and communication multihop coverage tests were done. The results show maximum throughput of 14 Mbps for TCP _____________________________________________________________________________________ Recebido em/Manuscript first received: 24/01/2008 Aprovado em/Manuscript accepted: 18/07/2008 Endereço para correspondência/ Address for correspondence Jorge R. Beingolea Garay, Universidade de São Paulo, Escola Politécnica, Faculdade de Engenharia Elétrica Psi, Laboratório de Sistemas Integráveis Lsi. Av. Prof. Luciano Gualberto, travessa 3, 380 – Butantã – SP, Brasil – 05508-900. Telefone: (11) 3091-9741 Ramal: 9741 Fax (11) 3091-5665 E-mail: [email protected] Roberto K. Hiramatsu, Universidade de São Paulo, Escola Politécnica, Departamento de Engenharia de Sistema Eletrônicos. Av. Prof. Luciano Gualberto, travessa 3, 158 – Butantã – SP, Brasil – 05508-900. Telefone: (11) 3091-5674 Fax: (11) 3091-5665 E-mail: [email protected] Sergio T. -

Product Brief: Intel-Powered Clamshel Classmate PC
Product Brief Intel-powered clamshell Intel-powered clamshell classmate PC Part of the Intel® Learning Series classmate PCs: purpose-built netbooks for education With new features including a 10-inch screen and enhanced connectivity, the Intel-powered clamshell classmate PC makes it easier than ever to bring powerful, affordable computer technology into classrooms worldwide. The Intel-powered clamshell classmate PC was developed after years of classroom-based ethnographic research, resulting in a netbook that delivers an innovative learning methodology for students and offers new ways for teachers to engage their students. The latest clamshell model is based on Intel® architecture and Intel® Atom™ processors, and provides a premium suite of 1:1 eLearning software applications such as classroom collaboration, access management, a child-friendly desktop, and a robust webcam. Child-friendly, ultra-compact, and easy-to-carry, the netbook doubles storage capacity and offers a larger display and keyboard, as well as a more rugged design to ensure a better and longer-lasting user experience. Teachers, students, and administrators can also enjoy faster and more reliable Internet connections thanks to 802.11b/g/n WiFi and an expansion slot for 3G connectivity. The Intel-powered clamshell classmate PC is part of the Intel® Learning Series, a family of hardware and software products, reference designs, and services created to meet the educational needs of young students. Local technology companies that customize products and services for their markets are an important part of this program. These local, sustainable, and scalable solutions are now being deployed around the globe. The power of eLearning Governments and educational leaders worldwide are seeking smart, sustainable ways to increase educational quality. -

2Go Convertible Classmate PC User Manual
IInntteell--PPoowweerreedd CCoonnvveerrttiibbllee CCllaassssmmaattee PPCC UUsseerr’’ss MMaannuuaall © Copyright 2008 All Rights Reserved. The information in this document is subject to change without prior notice in order to improve reliability, design and function and does not represent a commitment on the part of the manufacturer. In no event will the manufacturer be liable for direct, indirect, special, incidental, or consequential damages arising out of the use or inability to use the product or documentation, even if advised of the possibility of such damages. This document contains proprietary information protected by copyright. All rights are reserved. No part of this manual may be reproduced by any mechanical, electronic, or other means in any form without prior written permission of the manufacturer. Limitation of Liability While reasonable efforts have been made to ensure the accuracy of this manual, the manufacturer and distributor assume no liability resulting from errors or omissions in this manual, or from the use of the information contained herein. Contents Before You Start .........................................................................................1 Attention: Teachers and Parents.............................................................................1 For Your Safety ...........................................................................................................2 Caring for Your Netbook.........................................................................................2 Regulatory Information..............................................................................3