Volume IX, Issue 1 Logistics Solutions for Telecom Professionals
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Broadband Access Equipment
COMMUNICATIONS ENGINEERING JFM ‘07 BROADBAND ACCESS EQUIPMENT Foreword Convergence is becoming a reality in the heart of service provider networks, but in the access network it's more a case of divergence, as service providers seek to offer broadband services over an increasing variety of access technologies, so that customers can get connected wherever they are. That raises a number of challenges for carriers, which are beginning to rethink their network infrastructures to address the heightened bandwidth requirements of services like IPTV and HDTV. Not only do they need to ramp up bandwidth to run these services, but they need to control the quality of user experience. At the same time, they need to devise strategies for supporting legacy, circuit-based services over new packet-based access infrastructure. And all this needs to happen in a way that permits the technology to be deployed and changed easily, cheaply, and rapidly. The telecom operators and their suppliers are addressing these challenges by developing new technologies such IMS (IP Multimedia Subsystem), carrier-class Ethernet, and pseudowire encapsulation. They're also working together in associations such as the DSL Forum to establish new standards and architectures. And all of this is resulting in a plethora of new products hitting the market -- a market that represents a huge opportunity for vendors. It's sometimes said that for every dollar carriers spend in the core of their networks they spend $10 on metro equipment and $100 on access networking. Broadband access is evolving at a rapid rate as subscriber rates around the world continue to soar. -

Optimizing the Investment in New Metro/Backhaul Infrastructure to Support an Fttx Evolution Project
Optimizing the Investment in New Metro/Backhaul Infrastructure to Support an FTTx Evolution Project Carsten Rossenhoevel Managing Director 1 Agenda • MEF Mission and Scope • Membership and Status of the Forum • Carrier Ethernet Attributes – Standardized Services – Scalability – Manageability • Interoperability Status • Current Projects – User-Network and Network-Network Interface – Mobile Backhaul 2 The Metro Ethernet Forum’s Mission Accelerate the worldwide adoption of carrier-class Ethernet networks and services 1. Need and demand for a simple ubiquitous service 2. Requirement to scale network services to enable rapid deployment of applications 3. Availability of low cost, high bandwidth of Ethernet, beyond the LAN 4. Convergence of business, residential and mobile services 3 MEF Membership (Part 1 of 2) June 2008 Equipment Vendors, Test Companies, Lab Members • Accedian Networks • D-Link • Ixia • SMC Networks • Actelis Networks • Do Networks • JDSU • Soapstone Networks • Adtran • Dowslake Microsystems • Juniper Networks • Spirent Communications • Adva Optical Networking • DragonWave • Lightstorm Networks • Sunrise Telecom • Aethera Networks • EANTC • Maipu Communications • T | Pack • Agilent Technologies • ECI Telecom • Matisse Networks • Tejas Networks • Aktino • Ericsson • Maxim • Telco Systems • Alcatel- Lucent • Ethos Networks • Motorola • Telcordia Technologies • AMCC • EXFO • MRV Communications • Tellabs • ANDA Networks • Extreme Networks • Nakina Systems • Telrad Networks • ARRIS International • FibroLAN • NEC • Transition Networks -

Thirty Years & Going Strong
THE COMPETITIVE COMMUNICATIONS ASSOCIATION THIRTY YEARS & GOING STRONG 2011 ANNUAL REPORT1 FROM THE CEO’S DESK Our members – and the industry in general – also benefited from the busi- ness, networking and educational opportunities that COMPTEL presented. Our COMPTEL PLUS Convention & EXPOs brought together more than Throughout this annual report, you will see a timeline 4,300 industry leaders and decisionmakers, and exhibitors representing marking the milestones of COMPTEL and the industry 210 companies, in the Spring and Fall of 2011. In addition to the timely during the past three decades. COMPTEL was founded keynote addresses, panel discussions and workshops at our conventions, by upstarts in the long-distance market that were chal- we provided members with access to Webinars and white papers on the lenging the entrenched monopoly. We have grown and topics of importance to their business. evolved as competition expanded into other sectors – Over the years, COMPTEL has established a strong reputation for both our from local telephony and data to VoIP, video, broad- policy advocacy and business development opportunities, and we will con- band, managed services, cloud computing and data tinue this momentum going forward. We hope, in these pages, you enjoy centers – as a result of the innovation, entrepreneurial the look back at COMPTEL’s first 30 years, and get a glimpse of how we spirit and leadership of our member companies, who are setting the stage for continued growth and success of your business – rely on copper, fiber and wireless technologies to reach and the communications industry as a whole – for the years to come. -

Exploration Into
T O F O A R The Quintessential Meeting Place For The Ethernet Community In Asia/Pacific P T E T E R E E A N T D O F L R O A S R U N N New for 2013! H A Host Operator: Co-located with: T 6 OFFICIAL APAC CONGRESS 3 – 5 DECEMBER 2013, SUNTEC, SINGAPORE : The latest developments Delivering end to EXPLORATION INTO of Carrier Ethernet with end service The bright future of Carrier The latest case studies on Creating flexible Ethernet driven Cloud connectivity with Bringing 300 Ethernet Gurus From Across Asia Pacific Under One Roof Arvinder Gujral, Shahar Steiff, Head of Business Vice President of Business Development- India Operations, and South East Asia PCCW Hong Kong Twitter Lim Ming Kiat, Engineering Director, Muhammad Firdaus Abdul Monir, SingTel Assistant General Manager in Network Architecture and Planning group, , Telecom Malaysia Asad Naveed, Anuradha Udunuwara, General Manager of System Engineer, Engineering, Sri Lanka Telecom PLC Pakistan Telecommunications Company Trong Dat Ho, Telecom Expert, VNPT Munira Jannati Rangwala, Director of Ethernet Product Management, Tata Communications Paul Lai, Assistant Vice President of Carrier Data International Sai Ping Sung, Business Division, General Manager, Hutchison Telecom Telstra LEARNING-INTENSIVE PRE-CONFERENCE WORKSHOP www. .com Tuesday 3 December 2013 carrier ethernet apac Gold Sponsors Silver Sponsors L A U N N INTRODUCING YOUR H A T 6 2013 ADVISORY BOARD Jon Baldry, Technical Marketing Director, OFFICIAL APAC CONGRESS Transmode THE LEADING EVENT FOR THE CARRIER Asad Naveed, General Manager, System COMMUNITY WITHIN THE ASIAN PACIFIC MARKET. Engineering, Pakistan Carrier Ethernet APAC is the largest and most comprehensive event looking at the technologies behind Carrier Telecommunications Ethernet from the service provider perspective while addressing the distinctive regional framework. -

Before the Federal Communications Commission Washington, D.C. 20554 in the Matter of Ensuring Customer Premises Equipment Backup
Before the Federal Communications Commission Washington, D.C. 20554 In the Matter of ) ) Ensuring Customer Premises Equipment ) PS Docket No. 14-174 Backup Power for Continuity of ) Communications ) ) GN Docket No. 13-5 Technology Transitions ) ) RM-11358 Policies and Rules Governing Retirement Of ) Copper Loops by Incumbent Local Exchange ) Carriers ) ) WC Docket No. 05-25 Special Access for Price Cap Local Exchange ) Carriers ) ) RM-10593 AT&T Corporation Petition for Rulemaking ) to Reform Regulation of Incumbent Local ) Exchange Carrier Rates for Interstate Special ) Access Services ) ) Windstream Petition for Declaratory Ruling ) WC Docket No. 15-1 COMMENTS OF COMPTEL Karen Reidy COMPTEL 1200 G Street NW Suite 350 Washington, DC 20005 (202) 296-6650 February 5, 2015 TABLE OF CONTENTS Summary and Introduction ………………………………………………………………………2 I. The Commission Must Establish Clear Triggers for the Application of the Section 214 Discontinuance Process for Wholesale Input Services……………………….5 a. Carrier-Customers are a Part of the Community………………………………………….6 b. Discontinuance, Reduction, Impairment of Wholesale Input Services to Carrier Customers Presumptively – and in Some Cases Conclusively – Impacts Retail Customers ……………………………………………………………..…8 c. Section 214 Discontinuance Approval for a Tariffed Service is Needed Even Where There is a Comparable Non-Tariffed Service in the Market………………12 d. The Elimination of Special Access Term Discount Plans Requires a Section 214 Application………………………………………………………………….14 II. The Commission’s Adoption of its Tentative Conclusion Regarding Equivalent Wholesale Access is Needed to Ensure the Public Convenience and Necessity……………..16 a. Conditions – as Proposed by the Tentative Conclusion - on ILEC Discontinuance of Wholesale Input Services are Needed……………………………….17 b. The Commission Should Adopt the Standards for Meeting the Equivalency Standard for Wholesale Input Services……………………...…………21 c. -
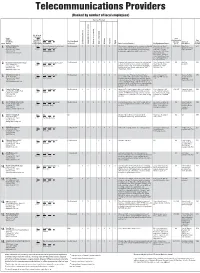
Telecommunications Providers (Ranked by Number of Local Employees)
Telecommunications Providers (Ranked by number of local employees) Services Provided No. of Local Employees Name 2009 Address Total No. of Parent Company Companywide Year Telephone Employees Facilities-Based revenues Top Local Locally 1 Rank Website Companywide Headquarters or Reseller Local voice service Long-distance voice service Cellular voice service Data transmission Wireless Internet Digital Other Services Provided Key Equipment Partners ($000) Executive(s) Founded Verizon Wireless Inc. 1,400 Verizon Communications Inc. and Facilities-based X X X X X X X Wireless voice and data services, consumer multimedia Alcatel-Lucent, Nortel 62,000,000 Russ Preite, 2000 1. 133 Calkins Road Vodafone Group PLC2 service, music on demand, location-based services, Networks Corp., Research Upstate New York Rochester, N.Y. 14623 81,000 wireless e-mail, text messaging, picture messaging, In Motion Ltd., Casio region president (585) 321-7000 Basking Ridge, N.J. downloadable applications, push-to-talk service America Inc., HTC Corp., www.verizonwireless.com LG Electronics Inc., Motorola Inc., Microsoft Corp., Nokia Corp., Palm Inc., Samsung America Inc., Kyocera Corp. Frontier Communications Corp.3 1,255 Frontier Communications Corp.4 Facilities-based X X X X X X X Integrated telecommunications services, switched and Cisco Systems Inc., Nortel, NA Ann Burr, 1899 2. dedicated network services, dedicated and dial-up Alcatel-Lucent, Sonus president 180 S. Clinton Ave. 5,671 Rochester, N.Y. 14646 Stamford, Conn. Internet access, e-mail, voice mail teleconferencing, Networks Inc., Mitel (585) 777-1000 digital network lines, domain name service, VOIP, Networks Corp. www.frontieronline.com virtual private network Time Warner Cable Inc. -

The SDN, NFV & Network Virtualization Bible
The SDN, NFV & Network Virtualization Bible: 2015 – 2020 Opportunities, Challenges, Strategies & Forecasts Table of Contents 1 Chapter 1: Introduction ................................................................................... 20 1.1 Executive Summary ....................................................................................................................................... 20 1.2 Topics Covered .............................................................................................................................................. 22 1.3 Forecast Segmentation ................................................................................................................................. 23 1.4 Key Questions Answered ............................................................................................................................... 25 1.5 Key Findings ................................................................................................................................................... 27 1.6 Methodology ................................................................................................................................................. 28 1.7 Target Audience ............................................................................................................................................ 29 1.8 Companies & Organizations Mentioned ....................................................................................................... 30 2 Chapter 2: An Overview of SDN, NFV -

Delivering on the Promise of Carrier Ethernet
corporate overview Delivering on the Promise of Carrier ethernet overture is harnessing the power of carrier ethernet “Integra selected Overture as a to provide an entrance to a smarter network. key partner based on the ease-of- We develop and manufacture high-speed Carrier Ethernet edge and aggregation solutions use, quality, and reliability of its that help our customers deliver high-capacity Ethernet services over any physical media leading edge EoC solutions, as well – fiber, copper or TDM. With Carrier Ethernet solutions that accelerate service, multiply as its demonstrated commitment revenue and streamline operational costs, Overture is the preferred edge and aggregation to superior service and support. partner to leading service providers and network operators worldwide. Overture is a natural fit for us and The flexibility of our award-winning products and solutions provides consistent customer we are very pleased to be working experiences from 1 Mbps to 10 Gbps over any network infrastructure. Our solutions support together to effectively serve our demanding applications that require greater bandwidth and more intelligent networks like swiftly growing customer base.” online collaboration, cloud computing, 10GE services, Ethernet transport infrastructure — Craig Heidgerken, Vice President, and mobile communications. Corporate Engineering, Integra Our success begins with our commitment to reliability. From our technology to our people who build and support it—Overture’s commitment to reliability is company wide. It’s at the heart of every product and engineered into everything we build. We also know that reliability is measured in more than nines: It’s measured in our ability to solve our customers’ problems and how fast we solve them. -

Delivering Ubiquitous Ethernet Services Using the World’S Access Technologies
MEF White Paper: Delivering Ubiquitous Ethernet Services using the World’s Access Technologies Delivering Ubiquitous Ethernet Services using an Array of Access Technologies Abstract This MEF white paper provides an overview of the various access technologies (also referred to as “first-mile” or “last-mile” technologies) that are used to deliver MEF-compliant Carrier Ethernet services. The goal of this white paper is to illustrate the fact that Service Providers who wish to deliver a ubiquitous Carrier Ethernet service can and should deploy a number of available access technologies to ensure they can reach all of their business customers’ locations. Carrier Ethernet and MEF Ethernet Services The MEF has defined Carrier Ethernet as a ubiquitous, standardized, carrier-class service and network with five attributes that distinguish it from familiar LAN-based Ethernet. These attributes are standardized services, scalability, reliability, management and quality of service. The basic Carrier Ethernet service building blocks are E-Line (Ethernet Private Line and Ethernet Virtual Private Line), E-LAN and E-Tree. This white paper discusses their deployment in the access network. Ethernet Virtual Private Line (EVPL) UNIUNI CECE Carrier Ethernet Network UNIUNI CECE UNIUNI Point-to-Point Ethernet Virtual Connections CECE Introduction Industry forums and standards bodies like the MEF, Corporate IT managers are exploring ways to add IEEE, ITU-T and IETF have developed the necessary network capacity while maintaining or reducing their extensions to the original Ethernet protocol, making it recurring operating expenses. Increasingly, suitable for service provider applications. For its part, businesses are moving away from traditional TDM, the MEF has documented numerous technical Frame Relay or ATM circuits and turning to Carrier requirements for building and managing feature-rich Ethernet Services to address these apparently business-class Ethernet services. -

Ka"Bk, Rl'~Ardkss of the Income Kvels of the Residents. AT&T Has
Moreover. AT&T's history orhroadband deployment sho\\'s that it has aggrcssl\Tly made l)SI SerVIl'l' available widely throughout its local service territory to the extent tcchnicalh' ka"bk, rl'~ardkss of the Income kvels of the residents. AT&T has upgraded its netwurks and no\\' offers DSI. service to nearly ~()o/u of households in its service areas"r:'7 Given this record, lherc is no baSIS for the Commission even to assume that AT&T \vill unlawfully discriminate in Its dcploylllellt of IPTV services. If and when evidence of discriminatory behavior in the roll OIlt of vIdeo services develops. appropriate relief may he sought at that time under applicable la\v.'·L'f> C The ACLU's Concems About Alleged Call Record Disclosures to the (,overIlment in Connection with Anti-Terrurist Intelligence Activities Cannot He (\)Il~i~!.~f~t in This Proceeding __ ._ Thl~ A('I JJ asserts t11,lt the Commission cannot approve the merger unless it first lll\c"tigatcs {jS'A Today's allegations that AT&T, Verizon, and BeilSouth violated provisions of the ('ommullications Act in allegedly providing assistance to the National Security Agency C'\JS!\") III connection with anti-terrorist intelligence activities instituted foll<nving the terrorist attacks of September II, 200 I. The AeLL! contends that this investi!!ation is necessary to determine if AT&T's has the requisite "character" to control BellSouth's licenses. The argument Footnote continued from previous page cable operators offering a bundle of voice, video and Internet services. In rc Implementation (~l Seclion 621 (aJ( I) ofthe Cahle Comme 'ns Policy Act or 1984, as Amended, MB Docket No. -
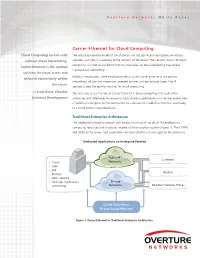
Carrier Ethernet for Cloud Computing
Overture Networks White Paper Carrier Ethernet for Cloud Computing Cloud Computing cannot exist The virtualized services model of cloud computing has significant implications on today’s without Cloud Networking. network, and how it is evolving to the network of tomorrow. The network impact of cloud computing is in fact so significant that any discussion on cloud computing should also Carrier Ethernet is the optimal include cloud networking. solution for cloud access and Without the network, there could be no cloud. Since Carrier Ethernet is the optimal network connectivity within networking solution for connection oriented services and the optimal Layer-2 for IP the cloud. services, is also the optimal solution for cloud computing. — Scott Knox, Director The best way to see the role of Carrier Ethernet in cloud computing is to look at the Solutions Development similarities and differences in network infrastructure as applications and services evolve from a traditional enterprise-centric architecture to a datacenter enabled architecture and finally to a cloud computing architecture. Traditional Enterprise Architecture The traditional enterprise network architecture has most, if not all, of the applications, computing resources and databases located at the enterprise location (Figure 1). The CAPEX and OPEX of the servers and applications are dedicated to and managed by the enterprise. Dedicated Applications on Enterprise Premise Public IP Customers - E-mail Networks - CRM - ERP Vendors - Storage - Web Presence - Desk-top Applications Private - Accounting Networks Remote Enterprise Offices Carrier Ethernet or IP over Carrier Ethernet Figure 1. Carrier Ethernet in Traditional Enterprise Architecture Network Connectivity to remote enterprise offices, customers, vendors and partners is via a combination of public and private networking. -
Annual Report 2016 Connecting, Extending and Assuring the Cloud Contents
Annual Report 2016 Connecting, Extending and Assuring the Cloud CONTENTS 1 WELCOME 3 SUPERVISORY BOARD Profile 5 Members 23 2016 Key Performance Indicators 5 Report of the Supervisory Board 23 Mission 5 ADVAntages 6 2016 Business Highlights 8 5 BUSINESS OVERVIEW 4 THE ADVA OPTICAL Mission 32 NETWORKING STOCK Technology 32 Market, Target Customers and Growth Drivers 33 2 MANAGEMENT BOARD Stock Information 27 Shareholder Structure 28 Products 36 Brian Protiva 17 Price Development 2016 in Comparison 29 Sales Regions and Marketing 39 Christoph Glingener 18 Investor Relations Review 29 DevOps 42 Ulrich Dopfer 19 Financial Analyst Coverage 30 Quality Management 44 Letter to the Shareholders 20 Investor Relations Contact 30 Compliance and Sustainability 45 2 ADVA ADVA Optical Optical Networking Networking - Annual – ReportAnnual 2016 Report 201 6 Risk Report 69 6 GROUP MANAGEMENT REPORT Outlook 78 Forward-Looking Statements 48 Basis of Preparation 48 Strategy and Control Design 49 7 IFRS CONSOLIDATED General Economic and Market Conditions 49 FINANCIAL STATEMENTS Business Development and Operational Performance 50 Net Assets and Financial Position 57 Consolidated Statement of Financial Position 82 Consolidated Income Statement 83 Events after the Balance Sheet Date 62 Consolidated Statement Restriction of Voting Rights of Comprehensive Income 84 and Share Transfers 62 Consolidated Cash Flow Statement 85 Appointment and Dismissal of Management Board Members 62 Consolidated Statement of Changes in Stockholders’ Equity 87 Changes to Articles of Association