THEME: MAN and the NATURAL WORLD
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Gods and Heroes: the Influence of the Classical World on Art in the 17Th & 18Th Centuries
12/09/2017 Cycladic Figure c 2500 BC Minoan Bull Leaper c 1500 BC Gods and Heroes: the Influence of the Classical World on Art in the 17th & 18th centuries Sophia Schliemann wearing “Helen’s Jewellery” Dr William Sterling Dr William Sterling www.williamsterling.co.uk www.williamsterling.co.uk Heracles from the Parthenon Paris and Helen krater c 700 BC Roman copy of Hellenistic bust of Homer Small bronze statue of Alexander the Great c 100 BC Dr William Sterling Dr William Sterling www.williamsterling.co.uk www.williamsterling.co.uk Judgement of Paris from Etruria c 550 BC Tiberius sword hilt showing Augustus as Jupiter Arrival of Aeneas in Italy Blacas Cameo showing Augustus with aegis breastplate Augustus of Prima Porta c 25 AD Dr William Sterling (discovered 1863) Dr William Sterling www.williamsterling.co.uk www.williamsterling.co.uk 1 12/09/2017 Romulus and Remus on the Franks Casket c 700 AD Siege of Jerusalem from the Franks Casket Mantegna Triumph of Caesar Mantua c 1490 Très Riches Heures du Duc de Berry c 1410 – tapestry of Trojan War Dr William Sterling Dr William Sterling www.williamsterling.co.uk www.williamsterling.co.uk The Colosseum Rome The Parthenon Athens The Pantheon Rome Artist’s Impression of the Mausoleum of Halicarnassus showing surviving sculpture Dr William Sterling Dr William Sterling www.williamsterling.co.uk www.williamsterling.co.uk Hera and Zeus on the Parthenon Frieze in the British Museum Hermes, Dionysus, Demeter and Ares on the Parthenon Frieze Dr William Sterling Dr William Sterling www.williamsterling.co.uk -

Art 258: Ancient and Medieval Art Spring 2016 Sched#20203
Art 258: Ancient and Medieval Art Spring 2016 Sched#20203 Dr. Woods: Office: Art 559; e-mail: [email protected] Office Hours: Monday and Friday 8:00-8:50 am Course Time and Location: MWF 10:00 – 10:50 HH221 Course Overview Art 258 is an introduction to western art from the earliest cave paintings through the age of Gothic Cathedrals. Sculpture, painting, architecture and crafts will be analyzed from an interdisciplinary perspective, for what they reveal about the religion, mythology, history, politics and social context of the periods in which they were created. Student Learning Outcomes Students will learn to recognize and identify all monuments on the syllabus, and to contextualize and interpret art as the product of specific historical, political, social and economic circumstances. Students will understand the general characteristics of each historical or stylistic period, and the differences and similarities between cultures and periods. The paper assignment will develop students’ skills in visual analysis, critical thinking and written communication. This is an Explorations course in the Humanities and Fine Arts. Completing this course will help you to do the following in greater depth: 1) analyze written, visual, or performed texts in the humanities and fine arts with sensitivity to their diverse cultural contexts and historical moments; 2) describe various aesthetic and other value systems and the ways they are communicated across time and cultures; 3) identify issues in the humanities that have personal and global relevance; 4) demonstrate the ability to approach complex problems and ask complex questions drawing upon knowledge of the humanities. Course Materials Text: F. -
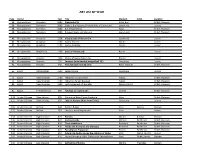
Art List by Year
ART LIST BY YEAR Page Period Year Title Medium Artist Location 36 Mesopotamia Sumerian 2600 Standard of Ur Inlaid Box British Museum 36 Mesopotamia Sumerian 2600 Stele of the Vultures (Victory Stele of Eannatum) Limestone Louvre 38 Mesopotamia Sumerian 2600 Bull Headed Harp Harp British Museum 39 Mesopotamia Sumerian 2600 Banquet Scene cylinder seal Lapis Lazoli British Museum 40 Mesopotamia Akkadian 2254 Victory Stele of Narum-Sin Sandstone Louvre 42 Mesopotamia Akkadian 2100 Gudea Seated Diorite Louvre 43 Mesopotamia Akkadian 2100 Gudea Standing Calcite Louvre 44 Mesopotamia Babylonian 1780 Stele of Hammurabi Basalt Louvre 45 Mesopotamia Assyrian 1350 Statue of Queen Napir-Asu Bronze Louvre 46 Mesopotamia Assyrian 750 Lamassu (man headed winged bull 13') Limestone Louvre 48 Mesopotamia Assyrian 640 Ashurbanipal hunting lions Relief Gypsum British Museum 65 Egypt Old Kingdom 2500 Seated Scribe Limestone Louvre 75 Egypt New Kingdom 1400 Nebamun hunting fowl Fresco British Museum 75 Egypt New Kingdom 1400 Nebamun funery banquet Fresco British Museum 80 Egypt New Kingdom 1300 Last Judgement of Hunefer Papyrus Scroll British Museum 81 Egypt First Millenium 680 Taharqo as a sphinx (2') Granite British Museum 110 Ancient Greece Orientalizing 625 Corinthian Black Figure Amphora Vase British Museum 111 Ancient Greece Orientalizing 625 Lady of Auxerre (Kore from Crete) Limestone Louvre 121 Ancient Greece Archaic 540 Achilles & Ajax Vase Execias Vatican 122 Ancient Greece Archaic 510 Herakles wrestling Antaios Vase Louvre 133 Ancient Greece High -

Writing As Material Practice Substance, Surface and Medium
Writing as Material Practice Substance, surface and medium Edited by Kathryn E. Piquette and Ruth D. Whitehouse Writing as Material Practice: Substance, surface and medium Edited by Kathryn E. Piquette and Ruth D. Whitehouse ]u[ ubiquity press London Published by Ubiquity Press Ltd. Gordon House 29 Gordon Square London WC1H 0PP www.ubiquitypress.com Text © The Authors 2013 First published 2013 Front Cover Illustrations: Top row (from left to right): Flouda (Chapter 8): Mavrospelio ring made of gold. Courtesy Heraklion Archaelogical Museum; Pye (Chapter 16): A Greek and Latin lexicon (1738). Photograph Nick Balaam; Pye (Chapter 16): A silver decadrachm of Syracuse (5th century BC). © Trustees of the British Museum. Middle row (from left to right): Piquette (Chapter 11): A wooden label. Photograph Kathryn E. Piquette, courtesy Ashmolean Museum; Flouda (Chapter 8): Ceramic conical cup. Courtesy Heraklion Archaelogical Museum; Salomon (Chapter 2): Wrapped sticks, Peabody Museum, Harvard. Photograph courtesy of William Conklin. Bottom row (from left to right): Flouda (Chapter 8): Linear A clay tablet. Courtesy Heraklion Archaelogical Museum; Johnston (Chapter 10): Inscribed clay ball. Courtesy of Persepolis Fortification Archive Project, Oriental Institute, University of Chicago; Kidd (Chapter 12): P.Cairo 30961 recto. Photograph Ahmed Amin, Egyptian Museum, Cairo. Back Cover Illustration: Salomon (Chapter 2): 1590 de Murúa manuscript (de Murúa 2004: 124 verso) Printed in the UK by Lightning Source Ltd. ISBN (hardback): 978-1-909188-24-2 ISBN (EPUB): 978-1-909188-25-9 ISBN (PDF): 978-1-909188-26-6 DOI: http://dx.doi.org/10.5334/bai This work is licensed under the Creative Commons Attribution 3.0 Unported License. -
![Arxiv:1911.09312V2 [Cs.CR] 12 Dec 2019](https://docslib.b-cdn.net/cover/5245/arxiv-1911-09312v2-cs-cr-12-dec-2019-485245.webp)
Arxiv:1911.09312V2 [Cs.CR] 12 Dec 2019
Revisiting and Evaluating Software Side-channel Vulnerabilities and Countermeasures in Cryptographic Applications Tianwei Zhang Jun Jiang Yinqian Zhang Nanyang Technological University Two Sigma Investments, LP The Ohio State University [email protected] [email protected] [email protected] Abstract—We systematize software side-channel attacks with three questions: (1) What are the common and distinct a focus on vulnerabilities and countermeasures in the cryp- features of various vulnerabilities? (2) What are common tographic implementations. Particularly, we survey past re- mitigation strategies? (3) What is the status quo of cryp- search literature to categorize vulnerable implementations, tographic applications regarding side-channel vulnerabili- and identify common strategies to eliminate them. We then ties? Past work only surveyed attack techniques and media evaluate popular libraries and applications, quantitatively [20–31], without offering unified summaries for software measuring and comparing the vulnerability severity, re- vulnerabilities and countermeasures that are more useful. sponse time and coverage. Based on these characterizations This paper provides a comprehensive characterization and evaluations, we offer some insights for side-channel of side-channel vulnerabilities and countermeasures, as researchers, cryptographic software developers and users. well as evaluations of cryptographic applications related We hope our study can inspire the side-channel research to side-channel attacks. We present this study in three di- community to discover new vulnerabilities, and more im- rections. (1) Systematization of literature: we characterize portantly, to fortify applications against them. the vulnerabilities from past work with regard to the im- plementations; for each vulnerability, we describe the root cause and the technique required to launch a successful 1. -

Proceedings of the Nimbus Program Review
X-650-62-226 J, / N63 18601--N 63 18622 _,_-/ PROCEEDINGS OF THE NIMBUS PROGRAM REVIEW OTS PRICE XEROX S _9, ,_-_ MICROFILM $ Jg/ _-"/_j . J"- O NOVEMBER 14-16, 1962 PROCEEDINGS OF THE NIMBUS PROGRAM REVIEW \ November 14-16, 1962 GODDARD SPACE FLIGHT CENTER Greenbelt, Md. NATIONAL AERONAUTICS AND SPACE ADMINISTRATION GODDARD SPACE FLIGHT CENTER PROCEEDINGS OF THE NIMBUS PROGRAM REVIEW FOREWORD The Nimbus program review was conducted at the George Washington Motor Lodge and at General Electric Missiles and Space Division, Valley Forge, Pennsylvania, on November 14, 15, and 16, 1962. The purpose of the review was twofold: first, to present to top management of the Goddard Space Flight Center (GSFC), National Aeronautics and Space Administration (NASA) Headquarters, other NASA elements, Joint Meteorological Satellite Advisory Committee (_MSAC), Weather Bureau, subsystem contractors, and others, a clear picture of the Nimbus program, its organization, its past accomplishments, current status, and remaining work, emphasizing the continuing need and opportunity for major contributions by the industrial community; second, to bring together project and contractor technical personnel responsible for the planning, execution, and support of the integration and test of the spacecraft to be initiated at General Electric shortly. This book is a compilation of the papers presented during the review and also contains a list of those attending. Harry P_ress Nimbus Project Manager CONTENTS FOREWORD lo INTRODUCTION TO NIMBUS by W. G. Stroud, GSFC _o THE NIMBUS PROJECT-- ORGANIZATION, PLAN, AND STATUS by H. Press, GSFC o METEOROLOGICAL APPLICATIONS OF NIMBUS DATA by E.G. Albert, U.S. -

Market Values in Eighteenth-Century Rome
Market values in eighteenth-century Rome Review of: The Art Market in Rome in the Eighteenth Century: A Study in the Social History of Art, edited by Paolo Coen, Leiden and Boston: Brill, 2018 [Studies in the History of Collecting and Art Markets, vol. 5], xii + 234 pp., 80 colour illus., €116/$134 hdbk, ISBN 978-90-04-33699-5. Jeffrey Collins Anyone who doubts that a society’s art market reveals its underlying values need only consider the case of Inigo Philbrick, the high-flying young dealer who sold investors overlapping shares of the same blue-chip contemporary works and who was recently apprehended in Vanuatu. The present volume boasts no one quite so colourful, though it too concerns a moment in which the business side of art acquired new prominence. Based on an international congress held at Rome’s Palazzo Barberini, the anthology’s ten chapters consider diverse facets of art’s production, circulation, and recirculation in early modern Rome, unfortunately not all centred on the time and place announced in the title. This is a limitation in a study of art markets, which are typically localized and responsive to shifting conditions. While less focused than one would wish, the collection nonetheless illuminates a key phase in the market’s development while contextualizing our own age of glossy magazines, glamorous fairs, ‘specullectors’, and illicit trafficking of cultural property. Both symposium and anthology reflect the efforts of Paolo Coen, professor of the history of art at the Università degli Studi di Teramo, to bring to Rome something of the economic perspective long established in studies of the seventeenth-century Netherlands. -

Terms and Facts- Hierarchical Scale
Terms and facts- Hierarchical scale From the Prehistoric and Neolithic- Post and Lintel, Megalith, tumulus, henge From Mesopotamia- The Code of Hammurabi, Shamash, Lamassu, Ziggurat, load bearing architecture, The Sumerians, the Akkadians, the Assyrians, the Babylonians, Stele or Stela From Minoa- Labrys, The myth of King Minos and the Minotaur From Mycenae- Corbelled vaults and domes, repousse, Tholos, Megaron, krater From Ancient Egypt- Ben-ben, mastaba, Imhotep, Ma’at, Canon (of artistic laws), cartouche, Canopic jars, Shabti or ushabti, the imagery of nine in connection to the pharaoh, the Amarna Period From Ancient Greece- Polykleitos, Humanism, contrapposto, Exekias, kouros and Kore, archaic smile, Praxiteles, some Greek mythology-especially the main gods and goddesses, meander (key design) Know the seven steps to lost wax casting Know the basic architecture of a Greek Temple-peristyle, the three column orders, (Doric, Ionic, Corinthian), stylobate, cella, shaft, caryatids, pediment, capital The two styles of Greek vase painting-black figure and red figure-the basic differences in look You should look up exam one of these myths and know the basic story or the main story about the character listed: Prometheus and Fire Apollo and Daphne Pygmalion and Galatea Niobe Persephone and Hades Pandora Tantalus-Son of Zeus The Danaides Alcyone and Ceyx Idas and Marpessa The Fall of Icarus Theseus and the Minotaur Perseus and the Medusa Jason and Medea Hercules and the Stymphalian Birds Chapter 2.9 Sculpture PART 2 MEDIA AND PROCESSES Seven steps in the lost-wax casting process Build and armature, sculpt the piece (clay), cover with ½ “ layer of wax, cover the entire piece with debris mixture, heat the entire work to melt out the wax through pre-drilled hole, pour the molten metal into the work through pre-drilled holes, break away the debris layer, clean and polishGateways to Art: Understanding the Visual Arts, Debra J. -

Catalogue of Paintings, Sculptures and Other Objects Exhibited During The
ART ' INSTITUTE OF CHICAGO CATALOGUE • OF PAINTINGS, ScuLPTURES AND OTHER OBJECTS EXHIBITED DURING THE WoRLD'S CoNGREssEs MAY 15 TO OCT. 31, 1893. THE ART INSTITUTE, Lake Front, opposite Adams Street, Chicago. THE ART INSTITUTE OF CHICAGO. CATALOGUE -OF- PAINTINGS, SCULPTURES AND OTHER OBJECTS EXHIBITED DURING THE WORLD'S CON- GRESSES. · SEPTEMBER, I893. CHICAGO, LAKE FRONT, HEAD OF ADAMS STREET. TRUSTEES OF THE ART INSTITUTE OF CHICAGO, !892-J. CHARLES L. HUTCHINSON, SAMUEL M. NICKERSON, DAVID W. IRWIN, MARTIN A. RYERSON, EDWARD E. A YER, WILLIAM . T. BAKER, ELIPHALET W. BLATCHFORD, NATHANIEL K. FAIRBANK, JAMES H. DOLE, ALBERT A. SPRAGUE, JOHN C. BLACK, ADOI;PHUS C. BARTLETT, . JOHN J. GLESSNER, CHARLES D. HAMILL, EDSON KEITH, TURLINGTON W. HARVEY. ALLISON V. ARM01J.R, HOMER N. HIBBARD, MARSHALL FIELD, GEORGE N . CULVER, PHILANDER C. HANFORD. OFFICERS CHARLES L. HUTCHINSON, JAMES H. DOLE, President. V{ce-President. LYMAN J . GAGE, N.H. CARPENTER, Treasurer. Secretary. W . M. R. FRENCH, ALFRED EMERSON, Director. Curator of Classical Antiquities. EXECUTIVE COMMITTEE <;HARLES L. HUTCHINSON, CHARLES D. HAMILL, JA)iES H. DOLE, JOHN C. BLACK, ALBERT A. SPRAGUE, MARTIN A. RYERSON, WILLIAM T . BAKER. THE ART INSTITUTE OF CHICAGO was incorporated May 24, 1879, for the purpose of maintaining a Museum and School of Art. The present building is built by the Art Institute and the World's Columbian Exposition jointly, at a cost of ~625,000, upon land granted by the city. At the end of the Fair the building will become the permanent and exclusive possession of· the Art Institute . During the Fair it is occupied by the World's Congresses. -

Greek Sculpture Archaic Kore 660 BC to 590 BC • Archaic Period • All Female Youth Sculptures Were Called Kore
Greek Sculpture Archaic Kore 660 BC to 590 BC • Archaic Period • All female youth sculptures were called Kore. • Made of marble • Would have been painted with bright colors and decorated. • Archaic smile-corners of her mouth slightly lifted. • Hair is carved down the back showing Egyptian influence. • Would have been found in and around temples holding an offering in her outstretched hand. • The Kore were always clothed. • Not meant to house the soul or KA at death but may have been used as graver markers. • Represented the ideal female youth. • Flesh would have been painted lighter than the male kouros. Kouros 660 BC to 590 BC • 1st appearance coincides with trade with Egypt. • Usually a votive statue (representing a hero or athlete) or a grave marker. • Represented the god Apollo. • All male statues were called kouros and were nude. • Represented the ideal male youth. • Flesh would have been painted brown or red. classical The Discus Thrower by Myron • 480-440 BC • Roman copy of a Greek sculpture. • Shows an athlete in motion performing the Olympic event discus throwing. • Athletes performed nude • Romans copied all the Greek sculptures. Venus de Milo 150 BC • Classical Period • Sculpted by Alexandros of Antioch • Statue of Aphrodite (Venus) • Located at the Louvre museum in Paris • Found on the island of Milos in 1820 • Milos means “apple” in Greek • Would have been painted and adorned with jewelry • Made of marble • 6’8 feet tall • The arms were lost in transport. • Her face is neutral and drapery is realistic • Known for perfect graceful proportions Doryphorus (the spear bearer) 450 BC-415 BC • Polykleitos of Argos • Bronze • Known for his sculptures of young athletes • Known only through Roman copies • Perfect proportions • Idealized • Classical period • Contrapposto stance Hellenistic The Seated Boxer 225 BC • Votive statue- commemorated a known boxer. -

Who's Who in Ancient Egypt
Who’s Who IN ANCIENT EGYPT Available from Routledge worldwide: Who’s Who in Ancient Egypt Michael Rice Who’s Who in the Ancient Near East Gwendolyn Leick Who’s Who in Classical Mythology Michael Grant and John Hazel Who’s Who in World Politics Alan Palmer Who’s Who in Dickens Donald Hawes Who’s Who in Jewish History Joan Comay, new edition revised by Lavinia Cohn-Sherbok Who’s Who in Military History John Keegan and Andrew Wheatcroft Who’s Who in Nazi Germany Robert S.Wistrich Who’s Who in the New Testament Ronald Brownrigg Who’s Who in Non-Classical Mythology Egerton Sykes, new edition revised by Alan Kendall Who’s Who in the Old Testament Joan Comay Who’s Who in Russia since 1900 Martin McCauley Who’s Who in Shakespeare Peter Quennell and Hamish Johnson Who’s Who in World War Two Edited by John Keegan Who’s Who IN ANCIENT EGYPT Michael Rice 0 London and New York First published 1999 by Routledge 11 New Fetter Lane, London EC4P 4EE Simultaneously published in the USA and Canada by Routledge 29 West 35th Street, New York, NY 10001 Routledge is an imprint of the Taylor & Francis Group This edition published in the Taylor & Francis e-Library, 2004. © 1999 Michael Rice The right of Michael Rice to be identified as the Author of this Work has been asserted by him in accordance with the Copyright, Designs and Patents Act 1988 All rights reserved. No part of this book may be reprinted or reproduced or utilised in any form or by any electronic, mechanical, or other means, now known or hereafter invented, including photocopying and recording, or in any information storage or retrieval system, without permission in writing from the publishers. -

Identifying Open Research Problems in Cryptography by Surveying Cryptographic Functions and Operations 1
International Journal of Grid and Distributed Computing Vol. 10, No. 11 (2017), pp.79-98 http://dx.doi.org/10.14257/ijgdc.2017.10.11.08 Identifying Open Research Problems in Cryptography by Surveying Cryptographic Functions and Operations 1 Rahul Saha1, G. Geetha2, Gulshan Kumar3 and Hye-Jim Kim4 1,3School of Computer Science and Engineering, Lovely Professional University, Punjab, India 2Division of Research and Development, Lovely Professional University, Punjab, India 4Business Administration Research Institute, Sungshin W. University, 2 Bomun-ro 34da gil, Seongbuk-gu, Seoul, Republic of Korea Abstract Cryptography has always been a core component of security domain. Different security services such as confidentiality, integrity, availability, authentication, non-repudiation and access control, are provided by a number of cryptographic algorithms including block ciphers, stream ciphers and hash functions. Though the algorithms are public and cryptographic strength depends on the usage of the keys, the ciphertext analysis using different functions and operations used in the algorithms can lead to the path of revealing a key completely or partially. It is hard to find any survey till date which identifies different operations and functions used in cryptography. In this paper, we have categorized our survey of cryptographic functions and operations in the algorithms in three categories: block ciphers, stream ciphers and cryptanalysis attacks which are executable in different parts of the algorithms. This survey will help the budding researchers in the society of crypto for identifying different operations and functions in cryptographic algorithms. Keywords: cryptography; block; stream; cipher; plaintext; ciphertext; functions; research problems 1. Introduction Cryptography [1] in the previous time was analogous to encryption where the main task was to convert the readable message to an unreadable format.