Strategic Studies Quarterly, Summer 2011, Vol. 5, No. 2
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Carl Sagan's Groovy Cosmos
CARL SAGAN’S GROOVY COSMOS: PUBLIC SCIENCE AND AMERICAN COUNTERCULTURE IN THE 1970S By SEAN WARREN GILLERAN A thesis submitted in partial fulfillment of the requirements for the degree of MASTER OF ARTS IN HISTORY WASHINGTON STATE UNIVERSITY Department of History MAY 2017 © Copyright by SEAN WARREN GILLERAN, 2017 All Rights Reserved © Copyright by SEAN WARREN GILLERAN, 2017 All Rights Reserved To the Faculty of Washington State University: The members of the Committee appointed to examine the thesis of SEAN WARREN GILLERAN find it satisfactory and recommend that it be accepted. _________________________________ Matthew A. Sutton, Ph.D., Chair _________________________________ Jeffrey C. Sanders, Ph.D. _________________________________ Lawrence B. A. Hatter, Ph.D. ii ACKNOWLEDGEMENT This thesis has been years in the making and is the product of input from many, many different people. I am grateful for the support and suggestions of my committee—Matt Sutton, Jeff Sanders, and Lawrence Hatter—all of whom have been far too patient, kind, and helpful. I am also thankful for input I received from Michael Gordin at Princeton and Helen Anne Curry at Cambridge, both of whom read early drafts and proposals and both of whose suggestions I have been careful to incorporate. Catherine Connors and Carol Thomas at the University of Washington provided much early guidance, especially in terms of how and why such a curious topic could have real significance. Of course, none of this would have happened without the support of Bruce Hevly, who has been extraordinarily generous with his time and whose wonderful seminars and lectures have continued to inspire me, nor without Graham Haslam, who is the best teacher and the kindest man I have ever known. -

RICHARD RHODES Email: [email protected] Website
RICHARD RHODES email: [email protected] website: www.RichardRhodes.com HONORS Pulitzer Prize in General Nonfiction, 1988 (for The Making of the Atomic Bomb). National Book Award in Nonfiction, 1987 (for The Making of the Atomic Bomb). National Book Critics Circle Award in General Nonfiction, 1987 (for The Making of the Atomic Bomb). Pulitzer Prize Finalist in History, 1995 (for Dark Sun). History of Science Society Watson Davis and Helen Miles Davis Prize of 1997 (for Dark Sun). Los Angeles Times Book Prize Finalist, 2004 (for John James Audubon). Doctor of Humane Letters, Westminster College, Fulton, Missouri, 1988. Doctor of Letters, honoris causa, Colby College, Waterville, Maine, 2010. American Nuclear Society Special Award and honorary membership, 2001. Modern Library 100 Best Nonfiction Books of the 20th Century (for The Making of the Atomic Bomb). FELLOWSHIPS AND APPOINTMENTS Affiliate, Center for International Security and Cooperation (CISAC), Stanford University, 2004-. Adviser, Alfred P. Sloan Foundation, 1990-. Fellow, Program on Peace and International Cooperation, MacArthur Foundation, 1990-1991; 2007-2008 Visiting scholar, History of Science Department, Harvard University, 1989-1990. Visiting fellow, Defense and Arms Control Studies Program, Massachusetts Institute of Technology, 1988-1989. Fellow, Alfred P. Sloan Foundation, 1985, 1988, 1991-94, 2002-04, 2010-11. Fellow, Ford Foundation, 1981 - 1983. Fellow, National Endowment for the Arts, 1978. Fellow, John Simon Guggenheim Memorial Foundation, 1974 - 1975. PUBLICATIONS See bibliography attached. EDUCATION B.A. cum laude, interdivisional honors major in History, the Arts and Letters, Yale University, 1959. East High School, Kansas City MO, 1955. COMMUNITY SERVICE Board of trustees, Atomic Heritage Foundation, Washington, D.C. -

Saddam Hussein
Saddam Hussein ﺻﺪام ﺣﺴﻴﻦ :Saddam Hussein Abd al-Majid al-Tikriti (/hʊˈseɪn/;[5] Arabic Marshal Ṣaddām Ḥusayn ʿAbd al-Maǧīd al-Tikrītī;[a] 28 April ﻋﺒﺪ اﻟﻤﺠﻴﺪ اﻟﺘﻜﺮﻳﺘﻲ 1937[b] – 30 December 2006) was President of Iraq from 16 July 1979 until 9 Saddam Hussein ﺻﺪام ﺣﺴﻴﻦ April 2003.[10] A leading member of the revolutionary Arab Socialist Ba'ath Party, and later, the Baghdad-based Ba'ath Party and its regional organization the Iraqi Ba'ath Party—which espoused Ba'athism, a mix of Arab nationalism and socialism—Saddam played a key role in the 1968 coup (later referred to as the 17 July Revolution) that brought the party to power inIraq . As vice president under the ailing General Ahmed Hassan al-Bakr, and at a time when many groups were considered capable of overthrowing the government, Saddam created security forces through which he tightly controlled conflicts between the government and the armed forces. In the early 1970s, Saddam nationalized oil and foreign banks leaving the system eventually insolvent mostly due to the Iran–Iraq War, the Gulf War, and UN sanctions.[11] Through the 1970s, Saddam cemented his authority over the apparatus of government as oil money helped Iraq's economy to grow at a rapid pace. Positions of power in the country were mostly filled with Sunni Arabs, a minority that made up only a fifth of the population.[12] Official portrait of Saddam Hussein in Saddam formally rose to power in 1979, although he had already been the de 1979 facto head of Iraq for several years. -

Improving Counterterrorism and Law Enforcement Cooperation Between the United States and the Arab Gulf States
Improving Counterterrorism and Law Enforcement Cooperation between the United States and the Arab Gulf States Thomas Warrick and Joze Pelayo Scowcroft Middle East Security Initiative The Atlantic Council’s Scowcroft Middle East Security Initiative honors the legacy of Brent Scowcroft and his tireless efforts to build a new security architecture for the region. Our work in this area addresses the full range of security threats and challenges including the danger of interstate warfare, the role of terrorist groups and other nonstate actors, and the underlying security threats facing countries in the region. Through all of the Council’s Middle East programming, we work with allies and partners in Europe and the wider Middle East to protect US interests, build peace and security, and unlock the human potential of the region. You can read more about our programs at www.atlanticcouncil.org/ programs/middle-east-programs/. Task Force on Mideast Counterterrorism – Law Enforcement Cooperation ■ Javed Ali, Towsley Policymaker in Residence, Gerald R. Ford School of Public Policy, University of Michigan ■ Kirsten Fontenrose, Director, Scowcroft Middle East Security Initiative, Atlantic Council ■ Daniel L. Glaser, Principal, Financial Integrity Network ■ Bernard Hudson, Nonresident Fellow, Belfer Center for Science and International Affairs ■ Michael McGarrity, Vice President Global Risk Services, Global Guardian ■ Pamela G. Quanrud, Former Director, C-ISIL Coalition, US Department of State ■ Todd Rosenblum, Nonresident Senior Fellow, Scowcroft Center -

B Reactor's 60Th Anniversary, by Richard Rhodes
WashingtonHistory.org HISTORY COMMENTARY Hanford and History: B Reactor's 60th Anniversary By Richard Rhodes COLUMBIA The Magazine of Northwest History, Fall 2006: Vol. 20, No. 3 Many people know the history of the Hanford Engineer Works well; some have lived it. I know it as a historian. I wrote about it in my book, The Making of the Atomic Bomb, and would have written more, but I simply did not have room. I treated plutonium production as a black box, inadvertently contributing to the myth that the atomic bomb was the work of 30 theoretical physicists at Los Alamos. More recently I have reviewed volumes of primary sources to refresh my memory of the heroic work carried out there between 1943 and 1945, so I think I can speak with some authority about it. I may even be able to clear up a mystery or two. Scientists at the Metallurgical Laboratory of the University of Chicago selected the site where plutonium would be produced for the first atomic bombs. Thirty-three-year-old Army Corps of Engineers colonel Franklin T. Matthias, known to his friends as "Fritz," wrote them into his diary after a meeting at DuPont’s home offices in Wilmington, Delaware, on December 14, 1942. The site needed to be spacious enough to accommodate a manufacturing area of approximately 12 by 16 miles, with no public highway or railroad nearer than 10 miles, no town of greater than 1,000 population nearer than 20 miles, an available water supply of at least 25,000 gallons per minute and an electrical supply of at least 100,000 kilowatts. -

70Th Anniversary of the Manhattan Project Atomic Heritage Foundation
Atomic Heritage Foundation presents 70th Anniversary of the Manhattan Project June 2 and 3, 2015 Carnegie Institution for Science 1530 P Street, NW Washington, DC 20005 Visit our merchandise tables to purchase books, posters, and hats! Manhattan Project 70th Anniversary Manhattan Project veterans Lawrence S. O’Rourke (left) and William E. Tewes (right) with his future wife, Olive. The Atomic Heritage Foundation is proud to host events commemorating the 70th Anniversary of the Manhattan Project. It took more than half a million people to build the world’s first atomic bombs; we are honored to welcome more than a dozen men and women who participated in that astonishing effort. The 70th Anniversary Reunion on June 2 will be an opportunity for vet- erans and family members to share their memories and catch up with old friends. Veterans from Los Alamos, Oak Ridge, Hanford, Chicago and other locations will discuss how each site contributed to the Manhattan Project in its own unique way. The 70th Anniversary commemoration will continue on June 3 with a day- long symposium, which will feature a discussion of the new Manhattan Project National Historical Park. We have assembled a first-class roster of Manhattan Project veterans and experts who will discuss topics ranging from innovation to women in science to atomic spies and more. We hope you enjoy the events! Cynthia C. Kelly President, Atomic Heritage Foundation Atomic Heritage Foundation The Atomic Heritage Foundation (AHF), founded by Cynthia C. Kelly in 2002, is a nonprofit organization in Washington, DC, dedicated to the preservation and interpretation of the Manhattan Project and its legacy. -

Witness to Abuse Human Rights Abuses Under the Material Witness Law Since September 11
Human Rights Watch June 2005 Vol. 17, No. 2 (G) Witness to Abuse Human Rights Abuses under the Material Witness Law since September 11 Summary......................................................................................................................................... 1 Recommendations......................................................................................................................... 7 To the Justice Department ...................................................................................................... 7 To Congress............................................................................................................................... 8 To the Judiciary......................................................................................................................... 9 I. The Material Witness Law: Overview and Pre-September 11 Use.................................. 10 Overview of the Material Witness Law ............................................................................... 12 Arrest of Material Witnesses before September 11 ........................................................... 14 II. Post-September 11 Material Witness Detention Policy................................................... 15 III. Misuse of the Material Witness Law to Hold Suspects as Witnesses........................... 17 Suspects Held as Witnesses................................................................................................... 20 Prolonged Incarceration and Undue Delays in Presenting Witnesses -

For the District of Columbia 2012 Report 555 4Th Street, NW Washington, DC 20530 Judiciary Center Building U.S
U.S. Department of Justice U.S. Attorney’s Office for the District of Columbia The United States Attorney’s Office for the District of Columbia The United States Attorney’s Office for the District of Columbi a 2012 Report U.S. Attorney’s Office for the District of Columbia Judiciary Center Building 555 4th Street, NW Washington, DC 20530 2012 Report Front Row Left to Right: Michael Ambrosino, Renata Cooper, Vince Cohen, Ron Machen, Darlena Perry, Melanie Howard Second Row: Wendy Pohlhaus, Ashley Patterson, Shelia Miller, Benjamin Kagan-Guthrie, Jenny Mancino, Matt Jones Third Row: Denise Simmonds, Bill Miller, Denise Clark, Pat Riley, Ashley Fitzgerald 21,534 New Cases Opened Contents 16,762 1 Letter from the U.S. Attorney Number of Informations Filed 3 Executive Summary 10,042 6 Office Overview Number of Convictions 22 Accomplishments 72 Targeted Initiatives 4,500 80 In the Community Number of Enrolled Diversions 102 Our People 2,680 Number of Indictments Returned The United States Attorney’s Office 2012 RepoRt for the District of Columbia From October 1, 2011 Cover photo courtesy of The Washington Examiner Judiciary Center, 555 4th Street, NW, Washington, D.C. 20530 to December 31, 2012 Special thanks to interns Deona DeClue, Kira Hettinger, and Ashley Page for their editing contributions. Letter from the United States Attorney Dear Friends, 2012 was a year of great accomplishment and great change for the contracting. At the same time, we reached settlements exceeding $800 million with banks who United States Attorney’s Office for the District of Columbia. violated U.S. -

UP Police Constable Exam Paper – 28 January 2019 (First Shift)
www.examstocks.com https://t.me/sscplus UP Police Constable Exam Paper – 28 January 2019 (First Shift) The Handwritten Constitution Was Signed On 24th January, 1950, By 284 Members Of The Constituent Assembly, Which Included _________women. (A) 30 (B) 20 (C) 15 (D) 25 Answer -C The Kakori Train Robbery Was Conceived By Ram Prasad Bismil And ______ . (A) Khudiram Bose (B) Shivaram Rajguru (C) Ashfaqullah Khan (D) Jatindra Nath Das Answer -C “My Passage From India” Is A Book Written By _________. (A) Mulk Raj Anand (B) Edward Morgan Forster (C) Vidiadhar Surajprasad Naipaul (D) Ismail Mechant Answer -D _____is The O†Ȃcial Currency Of Finland. (A) Dollar (B) Pound (C) Rial (D) Euro Answer -D Who Invented The Jet Engine? (A) Roger Bacon (www.examstocks.comB) Sir Frank Whittle (C) James Watt fb.com/examstocksofficial https://t.me/examstocks www.examstocks.com https://t.me/sscplus (D) Lewis Edson Waterman Answer -B Name The Younger Son Of Shivaji Who Was Also The Third Chhatrapati. (A) Rajaram (B) Sambhaji (C) Shahu (D) Bajirao Answer -A Which Indian State Has Its Maximum Area Under Forest Cover? (A) Kerala (B) Maharashtra (C) Uttar Pradesh (D) Madhya Pradesh Answer -D Which Of The Following Is NOT A State Of The United States Of America? (A) New York (B) Minnesota (C) Louisiana (D) Atlanta Answer -D Which Line Demarcates The Boundary Between India And Pakistan? (A) McMahon Line (B) Redcliတāe Line (C) Madison Line (D) Durand Line Answer -B World Environment Day Is Held On Which Day? (www.examstocks.comA) 22nd April fb.com/examstocksofficial https://t.me/examstocks www.examstocks.com https://t.me/sscplus (B) 8th May (C) 5th June (D) 11th June Answer -C Which Of The Following Social Media Networks Is NOT A Publicly Listed Company? (A) Twitter (B) Facebook (C) Weibo (D) Quora Answer – Pyongyang Is The Capital Of Which Country? (A) Maldives (B) Mongolia (C) Malaysia (D) North Korea Answer -D _________ Is An Ancient Folk Dance Originating From Odisha. -

Ensemble T Ogether Concordes
UNION MONDIALE DES ANCIENS ELEVES - UNION MUNDIAL DE LOS ANTIGUOS ALUMNOS - WORLD UNION ALUMNI/OLD BOYS ENSEMBLE T OGETHER CONCORDES BOGOTÁ D.C. MARCH 2002 EDITORIAL INVITATION TO THE CONGRESS effective if we all prepare for it well. We, and the Indian Kolkata Congress' organizers will appreciate your suggestions of topics and speakers for the program. The idea is that we send you the topics and the final program soon, so you can Dear fellow Jesuit Alumni/ae: discuss them in your own associations and/or federations and bring your thoughts and input to Kolkata. We will all be eager to learn from one another. As the President of the World Union of Jesuit Alumni (WUJA) and according to our regulations, it gives me great pleasure to extend this invitation to you and the All members of the alumni/ae associations from the world are cordially invited members of your Jesuit Alumni(ae) Association to the VI Congress of the World to this Congress. But it may be possible that due to distance not all can come. In Union of Jesuit Alumni at Saint Xavier's College, Kolkata, India from January 21 light of the fact that this is, as the one in Sydney was, a strategic congress, it to January 24, 2003. will be important that your association send al least a core delegation as representativesrepresentatives. Probably the President, the Jesuit Counselor and at least one The Indian Federation and the organizing committee for the sixth Congress have or two other alumni, of whom one should be a young former student. -

India's Limited War Doctrine: the Structural Factor
IDSA Monograph Series No. 10 December 2012 INDIA'S LIMITED WAR DOCTRINE THE STRUCTURAL FACTOR ALI AHMED INDIA’S LIMITED WAR DOCTRINE: THE STRUCTURAL FACTOR | 1 IDSA Monograph Series No. 10 December 2012 INDIA’S LIMITED WAR DOCTRINE THE STRUCTURAL FACTOR ALI AHMED 2 | ALI AHMED Institute for Defence Studies and Analyses, New Delhi. All rights reserved. No part of this publication may be reproduced, sorted in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photo-copying, recording or otherwise, without the prior permission of the Institute for Defence Studies and Analyses (IDSA). ISBN: 978-93-82169-09-3 Disclaimer: The views expressed in this Monograph are those of the author and do not necessarily reflect those of the Institute or the Government of India. First Published: December 2012 Price: Rs. Published by: Institute for Defence Studies and Analyses No.1, Development Enclave, Rao Tula Ram Marg, Delhi Cantt., New Delhi - 110 010 Tel. (91-11) 2671-7983 Fax.(91-11) 2615 4191 E-mail: [email protected] Website: http://www.idsa.in Layout & Cover by: Vaijayanti Patankar Printed at: INDIA’S LIMITED WAR DOCTRINE: THE STRUCTURAL FACTOR | 3 To Late Maj Gen S. C. Sinha, PVSM 4 | ALI AHMED INDIA’S LIMITED WAR DOCTRINE: THE STRUCTURAL FACTOR | 5 CONTENTS ACKNOWLEDGEMENTS .......................... 7 1. INTRODUCTION .................................... 9 2. DOCTRINAL CHANGE ............................. 16 3. THE STRUCTURAL FACTOR .................. 42 4. CONCLUSION ....................................... 68 REFERENCES ......................................... 79 6 | ALI AHMED * INDIA’S LIMITED WAR DOCTRINE: THE STRUCTURAL FACTOR | 7 ACKNOWLEDGEMENTS This monograph is the outcome of my fellowship at IDSA in 2010- 12. -
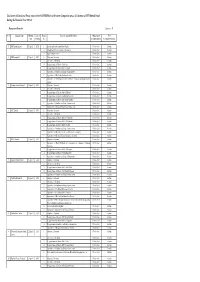
Voting Data for Website
Disclosure of Exercise of Proxy votes in the AGM/EGM,etc of Investee Companies across all schemes of UTI Mutual Fund during the Financial Year 2011-12 Management Proposals Annexure - B Sr. No. Company Name Meeting Type of Resln Proposal / Agenda/ Resolution Management Vote Date Meeting No. Recommendation (For/Against/Abstain) 1 KSB Pumps Limited 5-Apr-11 EGM 1 Increase in the Authorized Share Capital Not to object Abstain 2 Amendment to Memorandum of Association Not to object Abstain 3 Issue of Bonus Shares Not to object Abstain 2 KSB Pumps Ltd. 7-Apr-11 AGM 1 Adoption of Accounts Not to object Abstain 2 Declaration of Dividend Not to object Abstain 3 Re-appointment of Director: Dr. A. Lee Not to object Abstain 4 Re-appointment of Director: Mr. W. Spiegel Not to object Abstain 5 Appointment of Auditors and fixing of Remuneration Not to object Abstain 6 Appointment of Mr. Pradip Shah as a Director Not to object Abstain 7 Appointment of KSB Singapore (Asia Pacific) Pte Ltd as sole selling agent of the Not to object Abstain company 3 Ambuja Cements Limited 11-Apr-11 AGM 1 Adoption of Accounts Not to object Abstain 2 Declaration of Dividend Not to object Abstain 3 Re-appointment of Director: Mr. M.L.Bhakta Not to object Abstain 4 Re-appointment of Director: Dr. Omkar Goswami Not to object Abstain 5 Re-appointment of Director: Mr. Naresh Chandra Not to object Abstain 6 Appointment of Auditors and fixing of remuneration Not to object Abstain 7 Approval for variations in the previous ESOS scheme Not to object Abstain 4 ACC Limited 13-Apr-11 AGM 1 Adoption of Accounts Not to object Abstain 2 Declaration of Dividend Not to object Abstain 3 Re-appointment of Director: Mr.