Public-Key Infrastructure – the Verisign Difference
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Paypal's Security
PayPal’s Security Key PayPal is a great service for enabling both businesses and consumers to buy and sell goods and services online without exposing private financial information to the other parties in a transaction. As a consumer, you can safely purchase goods and services online without exposing your credit or debit card information to be recorded and possibly misused. As a business, you can be paid for your goods or services using the Web or email without the need of storing your customer’s private financial information. A big concern with PayPal is that anyone who knows the password of your PayPal account can access the financial services that you have authorized to be used with PayPal. For consumers, this means that unauthorized purchases or cash transfer may be performed from your credit cards and bank accounts. As a business, unauthorized PayPal access can be a source of fraudulent purchases. Password security is always the responsibility of the PayPal account holder; but now PayPal has a service to make the disclosure of your PayPal password an almost insignificant threat. In February 2007, PayPal introduced an optional security key system for users to access their PayPal accounts. The security key does not replace your PayPal password; instead, it adds an extra layer of security by requiring an additional security code be entered with your password when you log into your PayPal account. What makes this security code so different from a password is that it randomly generated by a small, electronic device called a security token, which is a key fob that easily fits in the palm of your hand. -

Zoom Go Boom!
Security Now! Transcript of Episode #761 Page 1 of 21 Transcript of Episode #761 Zoom Go Boom! Description: This week starts off with a bunch of web browser news including Firefox zero-days, Safari's recent scrape, more coronavirus-related feature rollbacks, the status of TLS v1.0 and 1.1, and some interesting developments on the Edge front. We revisit the lingering STIR and SHAKEN telco protocol mess, then look at a new DNS-filtering add-on service from Cloudflare and at the growing influence of an Internet group hoping to tighten up the mess with BGP. After a quick update on my SpinRite project, we take a look at what's been going on with the security of Zoom, the suddenly chosen tool for hosting Internet virtual classrooms and meetings of all kinds. High quality (64 kbps) mp3 audio file URL: http://media.GRC.com/sn/SN-761.mp3 Quarter size (16 kbps) mp3 audio file URL: http://media.GRC.com/sn/sn-761-lq.mp3 SHOW TEASE: It's time for Security Now!. Steve Gibson is here. Lots to talk about including a Mozilla Firefox zero-day. It's been fixed, but just barely. A problem with Safari. BGP gets some MANRS. And what's wrong with Zoom, and a pretty good alternative. It's all coming up next on Security Now!. Leo Laporte: This is Security Now! with Steve Gibson, Episode 761, recorded Tuesday, April 7th, 2020: Zoom Go Boom! It's time for Security Now!, the show where we cover your security and privacy and safety and quarantine online. -

Obstacles to the Adoption of Secure Communication Tools
Obstacles to the Adoption of Secure Communication Tools Ruba Abu-Salma M. Angela Sasse Joseph Bonneau University College London, UK University College London, UK Stanford University & EFF, USA Anastasia Danilova Alena Naiakshina Matthew Smith University of Bonn, Germany University of Bonn, Germany University of Bonn, Germany Abstract—The computer security community has advocated Recent mobile phone-based secure communication tools widespread adoption of secure communication tools to counter have often been designed to hide security from the user com- mass surveillance. Several popular personal communication tools pletely (albeit at some security cost [1]). WhatsApp famously (e.g., WhatsApp, iMessage) have adopted end-to-end encryption, and many new tools (e.g., Signal, Telegram) have been launched deployed E2E encryption to approximately a billion users with security as a key selling point. However it remains unclear through a code update to its application for messages, voice if users understand what protection these tools offer, and if they calls and video communications [18], with only negligible value that protection. In this study, we interviewed 60 partici- changes to the user experience. Some other communication pants about their experience with different communication tools tools (e.g., Signal, Threema) have launched with security and their perceptions of the tools’ security properties. We found that the adoption of secure communication tools is hindered by as an explicit selling point, but they also hide nearly all fragmented user bases and incompatible tools. Furthermore, the cryptographic details. vast majority of participants did not understand the essential There are key differences in the security model of dif- concept of end-to-end encryption, limiting their motivation to ferent E2E-encrypted tools, in addition to a large gap in adopt secure tools. -

Analysis and Implementation of the Messaging Layer Security Protocol
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by AMS Tesi di Laurea Alma Mater Studiorum · Universita` di Bologna CAMPUS DI CESENA Dipartimento di Informatica - Scienza e Ingegneria Corso di Laurea Magistrale in Ingegneria e Scienze Informatiche Analysis and Implementation of the Messaging Layer Security Protocol Tesi in Sicurezza delle Reti Relatore: Presentata da: Gabriele D'Angelo Nicola Giancecchi Anno Accademico 2018/2019 Parole chiave Network Security Messaging MLS Protocol Ratchet Trees \Oh me, oh vita! Domande come queste mi perseguitano. Infiniti cortei d'infedeli, citt`agremite di stolti, che v'`edi nuovo in tutto questo, oh me, oh vita! Risposta: Che tu sei qui, che la vita esiste e l’identit`a. Che il potente spettacolo continua, e che tu puoi contribuire con un verso." - Walt Whitman Alla mia famiglia. Introduzione L'utilizzo di servizi di messaggistica su smartphone `eincrementato in maniera considerevole negli ultimi anni, complice la sempre maggiore disponi- bilit`adi dispositivi mobile e l'evoluzione delle tecnologie di comunicazione via Internet, fattori che hanno di fatto soppiantato l'uso dei classici SMS. Tale incremento ha riguardato anche l'utilizzo in ambito business, un contesto dove `epi`ufrequente lo scambio di informazioni confidenziali e quindi la necessit`adi proteggere la comunicazione tra due o pi`upersone. Ci`onon solo per un punto di vista di sicurezza, ma anche di privacy personale. I maggiori player mondiali hanno risposto implementando misure di sicurezza all'interno dei propri servizi, quali ad esempio la crittografia end-to-end e regole sempre pi`ustringenti sul trattamento dei dati personali. -
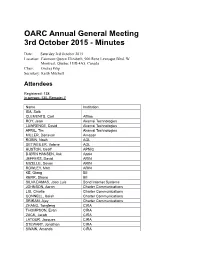
2015 AGM Minutes
OARC Annual General Meeting 3rd October 2015 - Minutes Date: Saturday 3rd October 2015 Location: Fairmont Queen Elizabeth, 900 Rene Levesque Blvd. W Montreal, Quebec H3B 4A5, Canada Chair: Ondrej Filip Secretary: Keith Mitchell Attendees Registered: 138 In person: 130, Remote: 7 Name Institution ISA, Saib CLEMENTS, Carl Afilias ROY, Jean Akamai Technologies LAWRENCE, David Akamai Technologies APRIL, Tim Akamai Technologies MILLER, Donavan Amazon ROBIN, Noah AOL DETWEILER, Valerie AOL HUSTON, Geoff APNIC BJØRN HANSEN, Ask Apple JEFFERS, David ARIN MIZELLE, Devon ARIN ROWLEY, Matt ARIN KE, Qiang BII KERR, Shane BII SILVA DAMAS, Joao Luis Bond Internet Systems JOHNSON, Aaron Charter Communications LIU, Charlie Charter Communications CONNELL, Isaiah Charter Communications SRIRAM, Ajay Charter Communications ZHANG, Tongfeng CIRA THOMPSON, Evan CIRA ZACK, Jacob CIRA LATOUR, Jacques CIRA STEWART, Jonathan CIRA SWAIN, Amanda CIRA MALENFANT, Eric CIRA CHANTIGNY, Rock CIRA BOOS, Roy Cisco Systems KWONG, David Cisco Systems VALSORDA, Filippo Cloudflare GUÐMUNDSSON, Ólafur CloudFlare ZHANG, Mingkai CNNIC XINYUE, Zhang CNNIC PAN, Lanlan CNNIC HAGOPIAN, Peter Comcast BARNITZ, John Comcast EBERSMAN, Paul Comcast HLAVACEK, Tomas CZ.NIC FILIP, Ondrej CZ.NIC SURÝ, Ondřej CZ.NIC PETRASCH, Christian DENIC BHABUTA, Denesh DNS-OARC KHEMLANI, Dalini DNS-OARC GRAVES, Susan DNS-OARC SOTOMAYOR, William DNS-OARC MITCHELL, Keith DNS-OARC DUARTE, Eduardo DNS.PT ROBERTS, Bruce DomainTools ALLEN, David Dyn GRAY, Robert Dyn COWIE, James Dyn HYNES, Liam Dyn KNIGHT, Dave -

Alpine Start Advising Response to Proposed Amendment 3 to the .COM Registry Agreement Greg Rafert, Ph.D. February 14, 2020
Alpine Start Advising Response to Proposed Amendment 3 to the .COM Registry Agreement Greg Rafert, Ph.D. February 14, 2020 I. Executive Summary 1. This comment provides an economic analysis of Verisign, Inc.’s (Verisign) proposed price increase for .COM registrations. Based on my training as an economist, review of the available evidence, and experience with ICANN and the TLD marketplace, I conclude that there is no economic rationale for Verisign to increase prices for .COM and that increased prices will very likely harm consumers: In the face of heightened competition, which has been provided as one reason for increasing .COM pricing, economic theory and empirical economic studies predict that a firm would typically lower, not increase, prices. To my knowledge, Verisign has not provided a rationale as to why increased competition would require it to increase prices for .COM. Verisign’s gross profit and operating margins have grown significantly over time and are currently high relative to other firms. While not demonstrative as to whether Verisign has market power in the TLD Alpine Start Advising 1 marketplace, they do suggest that changes in Verisign’s costs are not driving Verisign’s interest in increasing prices for .COM. An increase in the price of .COM registrations will harm consumers worldwide, as consumers are unlikely to switch to other, less expensive TLDs due to the high costs associated with switching from a .COM domain. While Verisign may argue that it will use increased revenues from .COM price increases to further improve the security and stability of the internet, thus benefiting consumers, this is unlikely. -
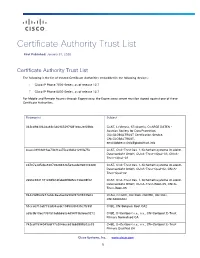
Certificate Authority Trust List
Certificate Authority Trust List First Published: January 31, 2020 Certificate Authority Trust List The following is the list of trusted Certificate Authorities embedded in the following devices: Cisco IP Phone 7800 Series, as of release 12.7 Cisco IP Phone 8800 Series, as of release 12.7 For Mobile and Remote Access through Expressway, the Expressway server must be signed against one of these Certificate Authorities. Fingerprint Subject 342cd9d3062da48c346965297f081ebc2ef68fdc C=AT, L=Vienna, ST=Austria, O=ARGE DATEN - Austrian Society for Data Protection, OU=GLOBALTRUST Certification Service, CN=GLOBALTRUST, [email protected] 4caee38931d19ae73b31aa75ca33d621290fa75e C=AT, O=A-Trust Ges. f. Sicherheitssysteme im elektr. Datenverkehr GmbH, OU=A-Trust-nQual-03, CN=A- Trust-nQual-03 cd787a3d5cba8207082848365e9acde9683364d8 C=AT, O=A-Trust Ges. f. Sicherheitssysteme im elektr. Datenverkehr GmbH, OU=A-Trust-Qual-02, CN=A- Trust-Qual-02 2e66c9841181c08fb1dfabd4ff8d5cc72be08f02 C=AT, O=A-Trust Ges. f. Sicherheitssysteme im elektr. Datenverkehr GmbH, OU=A-Trust-Root-05, CN=A- Trust-Root-05 84429d9fe2e73a0dc8aa0ae0a902f2749933fe02 C=AU, O=GOV, OU=DoD, OU=PKI, OU=CAs, CN=ADOCA02 51cca0710af7733d34acdc1945099f435c7fc59f C=BE, CN=Belgium Root CA2 a59c9b10ec7357515abb660c4d94f73b9e6e9272 C=BE, O=Certipost s.a., n.v., CN=Certipost E-Trust Primary Normalised CA 742cdf1594049cbf17a2046cc639bb3888e02e33 C=BE, O=Certipost s.a., n.v., CN=Certipost E-Trust Primary Qualified CA Cisco Systems, Inc. www.cisco.com 1 Certificate Authority -

Introduction to Public Key Technology and Federal PKI Infrastructure
Withdrawn NIST Technical Series Publication Warning Notice The attached publication has been withdrawn (archived), and is provided solely for historical purposes. It may have been superseded by another publication (indicated below). Withdrawn Publication Series/Number NIST Special Publication 800-32 Title Introduction to Public Key Technology and the Federal PKI Infrastructure Publication Date(s) February 26, 2001 Withdrawal Date September 13, 2021 Withdrawal Note SP 800-32 is withdrawn in its entirety. Superseding Publication(s) (if applicable) The attached publication has been superseded by the following publication(s): Series/Number Title Author(s) Publication Date(s) URL/DOI Additional Information (if applicable) Contact Computer Security Division (Information Technology Laboratory) Latest revision of the N/A attached publication Related Information https://csrc.nist.gov/projects/crypto-publication-review-project https://csrc.nist.gov/publications/detail/sp/800-32/archive/2001-02-26 Withdrawal https://csrc.nist.gov/news/2021/withdrawal-of-nist-special-pubs-800-15-25- Announcement Link and-32 Date updated: September 13, 2021 SP 800-32 IIInnntttrrroooddduuuccctttiiiooonnn tttooo PPPuuubbbllliiiccc KKKeeeyyy TTTeeeccchhhnnnooolllooogggyyy aaannnddd ttthhheee FFFeeedddeeerrraaalll PPPKKKIII IIInnnfffrrraaassstttrrruuuccctttuuurrreee D. Richard Kuhn Vincent C. Hu 26 February 2001 W. Timothy Polk Shu-Jen Chang 1 National Institute of Standards and Technology, 2001. U.S. Government publication. Not subject to copyright. Portions of this document have been abstracted from other U.S. Government publications, including: “Minimum Interoperability Specification for PKI Components (MISPC), Version 1” NIST SP 800-15, January 1998; “Certification Authority Systems”, OCC 99-20, Office of the Comptroller of the Currency, May 4, 1999; “Guideline for Implementing Cryptography in the Federal Government”, NIST SP800-21, November 1999; Advances and Remaining Challenges to Adoption of Public Key Infrastructure Technology, U.S. -

White Paper: a Proposal for DNAME Equivalence Mapping for TLD Strings
VeriSign® White Paper: A Proposal for DNAME Equivalence Mapping for TLD Strings COPYRIGHT NOTIFICATION ©2005 VeriSign, Inc. All rights reserved. VeriSign, the VeriSign logo “Where it all comes together,” and other trademarks, service marks, and designs are registered or unregistered trademarks of VeriSign and its subsidiaries in the United States and in foreign countries. 11/05. DISCLAIMER AND LIMITATION OF LIABILITY VeriSign, Inc. has made efforts to ensure the accuracy and completeness of the information in this document. However, VeriSign, Inc. makes no warranties of any kind (whether express, implied or statutory) with respect to the information contained herein. VeriSign, Inc. assumes no liability to any party for any loss or damage (whether direct or indirect) caused by any errors, omissions or statements of any kind contained in this document. Further, VeriSign, Inc. assumes no liability arising from the application or use of the product or service described herein and specifically disclaims any representation that the products or services described herein do not infringe upon any existing or future intellectual property rights. Nothing herein grants the reader any license to make, use, or sell equipment or products constructed in accordance with this document. Finally, all rights and privileges related to any intellectual property right described herein are vested in the patent, trademark, or service mark owner, and no other person may exercise such rights without express permission, authority, or license secured from the patent, trademark, or service mark owner. VeriSign Inc. reserves the right to make changes to any information herein without further notice. NOTICE AND CAUTION Concerning U.S. -

Efail: Breaking S/MIME and Openpgp Email Encryption Using Exfiltration Channels
Efail: Breaking S/MIME and OpenPGP Email Encryption using Exfiltration Channels Damian Poddebniak and Christian Dresen, Münster University of Applied Sciences; Jens Müller, Ruhr University Bochum; Fabian Ising and Sebastian Schinzel, Münster University of Applied Sciences; Simon Friedberger, NXP Semiconductors, Belgium; Juraj Somorovsky and Jörg Schwenk, Ruhr University Bochum https://www.usenix.org/conference/usenixsecurity18/presentation/poddebniak This paper is included in the Proceedings of the 27th USENIX Security Symposium. August 15–17, 2018 • Baltimore, MD, USA ISBN 978-1-939133-04-5 Open access to the Proceedings of the 27th USENIX Security Symposium is sponsored by USENIX. Efail: Breaking S/MIME and OpenPGP Email Encryption using Exfiltration Channels Damian Poddebniak1, Christian Dresen1, Jens Muller¨ 2, Fabian Ising1, Sebastian Schinzel1, Simon Friedberger3, Juraj Somorovsky2, and Jorg¨ Schwenk2 1Munster¨ University of Applied Sciences 2Ruhr University Bochum 3NXP Semiconductors, Belgium Abstract is designed to protect user data in such scenarios. With end-to-end encryption, the email infrastructure becomes OpenPGP and S/MIME are the two prime standards merely a transportation service for opaque email data and for providing end-to-end security for emails. We de- no compromise – aside from the endpoints of sender or scribe novel attacks built upon a technique we call mal- receiver – should affect the security of an end-to-end en- leability gadgets to reveal the plaintext of encrypted crypted email. emails. We use CBC/CFB gadgets to inject malicious plaintext snippets into encrypted emails. These snippets S/MIME and OpenPGP. The two most prominent stan- abuse existing and standard conforming backchannels to dards offering end-to-end encryption for email, S/MIME exfiltrate the full plaintext after decryption. -
![PHINMS Security White Paper Pdf Icon[230 KB, 8 Pages]](https://docslib.b-cdn.net/cover/5162/phinms-security-white-paper-pdf-icon-230-kb-8-pages-1915162.webp)
PHINMS Security White Paper Pdf Icon[230 KB, 8 Pages]
On Securing the Public Health Information Network Messaging System Barry Rhodes Rajashekar Kailar Associate Director For Public Health System Development Chief Technology Officer Information Resources Management Office Business Networks International, Inc. Centers for Disease Control and Prevention www.bnetal.com www.cdc.gov Abstract The Public Health Information Network PHINMS is operating system neutral since it is Messaging System (henceforth, PHINMS) is the implemented using Java and J2EE standards. Centers for Disease Control and Prevention’s (CDC) implementation of the ebXML 2.0 Further, it provides language neutral, queue based messaging standards [EbXML]. This system was interfaces for sending and receiving messages. The developed for the purpose of secure and reliable preferred queue implementation is an messaging over the Internet. This software has ODBC/JDBC compliant database table, but been widely deployed by CDC and its public support for queues based on XML file descriptors health partners, including state and local health also exists. PHINMS supports peer-to-peer departments, and healthcare providers. PHINMS is messaging, as well as messaging via a third party designed to leverage X.509 digital certificates using a send and poll model. issued by public key infrastructures, but does not require a single, universal PKI. In this paper we Message data security is accomplished using a discuss some of the security aspects of PHINMS. combination of encryption, end-point authentication, and access control techniques. Introduction Transport reliability is accomplished using message integrity verification, transmission retries and duplicate detection on message receipt. The Public Health Information Network Messaging System (PHINMS) is a CDC Since PHINMS is used to transport sensitive data developed implementation of existing standards over public un-trusted networks (e.g., Internet), it for the secure and reliable transmittal of messages is important to make sure that end-points trust across the Internet. -

WIPO Domain Name Dispute: Case No. LRO2013-0066
ARBITRATION AND MEDIATION CENTER EXPERT DETERMINATION LEGAL RIGHTS OBJECTION Regtime Ltd. and Legato Ltd. v. VeriSign Sarl Case No. LRO2013-0066 1. The Parties The Objectors are Regtime Ltd. and Legato Ltd., Russian Federation, represented by Winston & Strawn LLP, United States of America. The Respondent/Applicant is VeriSign Sarl, Switzerland, represented by Thomas C. Indelicarto, VeriSign Inc., United States of America. 2. The applied-for gTLD string The applied-for gTLD string is <.ком> [xn--j1aef]. 3. Procedural History The Objection was filed with the WIPO Arbitration and Mediation Center (the “WIPO Center”) on March 13, 2013 (UTC), pursuant to the New gTLD Dispute Resolution Procedure (the “Procedure”). In accordance with Article 9 of the Procedure, the WIPO Center completed the review of the Objection on March 22, 2013, and determined that the Objection complies with the requirements of the Procedure and the World Intellectual Property Organization Rules for New gTLD Dispute Resolution for Existing Legal Rights Objections (the “WIPO Rules for New gTLD Dispute Resolution”). In accordance with Article 11(a) of the Procedure, the WIPO Center formally notified the Respondent of the Objection, and the proceedings commenced on April 22, 2013. In accordance with Article 11(b) and relevant communication provisions of the Procedure, the Response was timely filed with the WIPO Center on May 22, 2013. The WIPO Center appointed Assen Alexiev as the Panel in this matter on June 13, 2013. The Panel finds that it was properly constituted. The Panel has submitted the Statement of Acceptance and Declaration of Impartiality and Independence, as required by the WIPO Center to ensure compliance with Article 13(c) of the Procedure and Paragraph 9 of WIPO Rules for New gTLD Dispute Resolution.