MAY 2016 Part C.Pdf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Cisco SCA BB Protocol Reference Guide
Cisco Service Control Application for Broadband Protocol Reference Guide Protocol Pack #60 August 02, 2018 Cisco Systems, Inc. www.cisco.com Cisco has more than 200 offices worldwide. Addresses, phone numbers, and fax numbers are listed on the Cisco website at www.cisco.com/go/offices. THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS. THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY. The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB’s public domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California. NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS” WITH ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE. IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. -

Security System for Mobile Messaging Applications Pejman Dashtinejad
Security System for Mobile Messaging Applications Pejman Dashtinejad Master of Science Thesis Stockholm, Sweden TRITA–ICT–EX-2015:2 Introduction | 1 Security System for Mobile Messaging Applications Pejman Dashtinejad 8 January 2015 Master of Science Thesis Examiner Professor Sead Muftic Department of ICT KTH University SE-100 44 Stockholm, Sweden TRITA–ICT–EX-2015:2 Abstract | iii Abstract Instant messaging (IM) applications are one of the most popular applications for smartphones. The IMs have the capability of sending messages or initiating voice calls via Internet which makes it almost cost free for the users to communicate with each other. Unfortunately, like any other type of applications, majority of these applications are vulnerable to malicious attacks and have privacy issues. The motivation for this thesis is the need to identifying security services of an IM application and to design a secure system for any mobile messaging application. This research proposes an E2EE (End-to-End Encryption) approach which provides a secure IM application design which protects its users with better integrity, confidentiality and privacy. To achieve this goal a research is conducted to investigate current security features of popular messaging applications in the mobile market. A list of requirements for good security is generated and based on those requirements an architecture is designed. A demo is also implemented and evaluated. Keywords: Mobile, Application, messaging, Chat, Encryption, Security Acknowledgments | v Acknowledgments First and foremost, thank you God to give me another chance to complete my higher education and to learn enormous skills and knowledge through all these years of study at the university. -

Enterprise Edition
Secure Communication. Simplified. SAFECHATS Problem Most companies use popular insecure email and ⛔ messaging services to communicate confidential information P The information flow within the Company is ⛔ disorganized Metadata is exposed and available to third-party ⛔ services SAFECHATS Introducing SAFECHATS Ultra-secure communication solution P Designed with security in mind SAFECHATS Why SAFECHATS? ✔ Information is always end-to-end encrypted by default P ✔ All-in-one communication suite: • Text messaging (one-on-one and group chats) • Voice calls • File transfers (no size and file type limits) SAFECHATS How does SAFECHATS solve the problem? ✔ Customizable white label solution ✔ Integrates with existing softwareP infrastructure ✔ Enterprise-wide account and contact list management, supervised audited chats for compliance SAFECHATS What makes SAFECHATS different? ✔ Your own isolated cloud environment or on-premise deployment P ✔ Customizable solution allows to be compliant with internal corporate security policies ✔ No access to your phone number and contact list SAFECHATS Screenshot Protection ✔ Notifications on iOS P ✔ DRM protection on Android SAFECHATS Identity Verification ✔ Protection from man-in-the-middle attacksP ✔ SMP Protocol SAFECHATS Privacy Features ✔ Show / hide messages and files P ✔ Recall messages and files ✔ Self-destructing messages and files SAFECHATS Additional Protection ✔ History retention control P ✔ Application lock: • PIN-code • Pattern-lock on Android devices • Touch ID on iOS devices SAFECHATS How does SAFECHATS -

A Better Death in a Digital Age: Post
Publishing Office Aims and scope Abramis Academic ASK House Communication ethics is a discipline that supports communication Northgate Avenue practitioners by offering tools and analyses for the understanding of Bury St. Edmunds ethical issues. Moreover, the speed of change in the dynamic information Suffolk environment presents new challenges, especially for communication IP32 6BB practitioners. UK Tel: +44 (0)1284 700321 Ethics used to be a specialist subject situated within schools of philosophy. Fax: +44 (0)1284 717889 Today it is viewed as a language and systematic thought process available Email: [email protected] to everyone. It encompasses issues of care and trust, social responsibility and Web: www.abramis.co.uk environmental concern and identifies the values necessary to balance the demands of performance today with responsibilities tomorrow. Copyright All rights reserved. No part For busy professionals, CE is a powerful learning and teaching approach that of this publication may be reproduced in any mate- encourages analysis and engagement with many constituencies, enhancing rial form (including pho- relationships through open-thinking. It can be used to improve organization tocopying or storing it in performance as well as to protect individual well-being. any medium by electronic means, and whether or not transiently or incidentally Submissions to some other use of this Papers should be submitted to the Editor via email. Full details on submission – publication) without the along with detailed notes for authors – are available online in PDF format: written permission of the www.communication-ethics.net copyright owner, except in accordance with the provisions of the Copyright, Subscription Information Designs and Patents Act Each volume contains 4 issues, issued quarterly. -
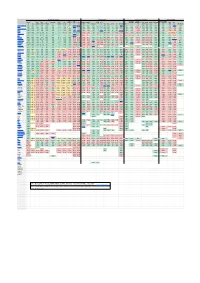
Digital Communications Protocols
Security & Privacy Compatibility Features & Usability Sustainability E2E E2E Offline Local Decentralized Active Open Open On Anonymous E2E E2E Default Audit FIDO1 Desktop Mobile Apple AOSP Messages messaging File Audio Video Phoneless or Federated Open IETF [1] TLS Client Server Premise [2] Private Group [3] [4] / U2F Web Web Android iOS [5] Win macOS Linux *BSD Terminal MDM [6] [7] [8] Share Call Call [9] [10] Spec [11] Introduced Element/Matrix TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE PARTIAL TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE FALSE 2014 XMPP TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE PARTIAL [12]TRUE FALSE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE FALSE [13] TRUE TRUE TRUE TRUE TRUE TRUE TRUE 1999 NextCloud Talk TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE FALSE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE FALSE TRUE TRUE FALSE TRUE TRUE TRUE TRUE TRUE FALSE FALSE 2018 Wire TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE TRUE FALSE TRUE FALSE TRUE TRUE FALSE TRUE TRUE TRUE TRUE PARTIAL TRUE TRUE FALSE TRUE TRUE TRUE TRUE FALSE FALSE FALSE 2014 Jami TRUE TRUE TRUE N/A [14] N/A TRUE TRUE FALSE [15] TRUE FALSE N/A [16] FALSE FALSE TRUE TRUE TRUE TRUE TRUE TRUE TRUE FALSE TRUE FALSE FALSE TRUE TRUE TRUE TRUE TRUE PARTIAL PARTIAL[17] [18] 2016 Briar [19] TRUE TRUE TRUE N/A [20] N/A TRUE TRUE TRUE TRUE TRUE N/A [21] FALSE FALSE TRUE FALSE TRUE FALSE FALSE FALSE FALSE FALSE FALSE TRUE TRUE FALSE FALSE FALSE FALSE TRUE FALSE FALSE 2016 Tox TRUE TRUE TRUE -

The History of the Development of British Satellite Broadcasting Policy, 1977-1992
THE HISTORY OF THE DEVELOPMENT OF BRITISH SATELLITE BROADCASTING POLICY, 1977-1992 Windsor John Holden —......., Submitted in accordance with the requirements for the degree of PhD University of Leeds, Institute of Communications Studies July, 1998 The candidate confirms that the work submitted is his own and that appropriate credit has been given where reference has been made to the work of others ABSTRACT This thesis traces the development of British satellite broadcasting policy, from the early proposals drawn up by the Home Office following the UK's allocation of five direct broadcast by satellite (DBS) frequencies at the 1977 World Administrative Radio Conference (WARC), through the successive, abortive DBS initiatives of the BBC and the "Club of 21", to the short-lived service provided by British Satellite Broadcasting (BSB). It also details at length the history of Sky Television, an organisation that operated beyond the parameters of existing legislation, which successfully competed (and merged) with BSB, and which shaped the way in which policy was developed. It contends that throughout the 1980s satellite broadcasting policy ceased to drive and became driven, and that the failure of policy-making in this time can be ascribed to conflict on ideological, governmental and organisational levels. Finally, it considers the impact that satellite broadcasting has had upon the British broadcasting structure as a whole. 1 TABLE OF CONTENTS Abstract i Contents ii Acknowledgements 1 INTRODUCTION 3 British broadcasting policy - a brief history -

'Precise' Strikes: Fractured Bodies, Fractured Lives
Israel’s drone wars: An update ‘Precise’ strikes: Fractured Bodies, Fractured Lives Front Cover image: Israel’s Heron TP drone at Tel Nof Air Force base, February 2010. Credit: UPI/Debbie Hill. Note: The term ‘drone’ is used interchangeably with ‘Unmanned Aerial Vehicle (UAV)’ Drone Wars UK is a small British NGO established in 2010 to undertake research and advocacy around the use of armed drones. We believe that the growing use of remotely-controlled, armed unmanned systems is encouraging and enabling a lowering of the threshold for the use of lethal force as well as eroding well established human rights norms. While some argue that the technology itself is neutral, we believe that drones are a danger to global peace and security. We have seen over the past decade that once these systems are in the armoury, the temptation to use them becomes great, even beyond the constraints of international law. As more countries develop or acquire this technology, the danger to global peace and security grows. Published by Drone Wars UK Drone Wars UK Written by Chloe Skinner Peace House, 19 Paradise Street November 2019 Oxford, OX1 1LD Designed: Chris Woodward www.dronewars.net www.chriswoodwarddesign.co.uk [email protected] ‘Precise Strikes’, Fractured Bodies, Fractured Lives | Israel’s drone wars: An update | 1 Contents 1 INTRODUCTION 3 2 “A RAPIDLY-GROWING DIVISION”: Israel’s drones and their operators 5 3 “ACCESS, PERSISTENCE, ACCURACY.” The humanitarian claims made for drone technology 8 4 “IN A MATTER OF SECONDS, THEY WERE CUT TO PIECES.” Life -

Protec3ng Messaging Other Than Email, Plus Network Link Protec3on
Protec'ng Messaging Other Than Email, plus Network Link Protec'on Joe St Sauver, Ph.D. [email protected] or [email protected] M3AAWG Senior Technical Advisor Scien@st, Farsight Security, Inc. Gold Ballroom, 1st Floor M3AAWG 36, San Francisco, California Wednesday Feb 17th, 2016, 15:30-16:30 hPps://www.stsauver.com/joe/crypto-other-than-email/ 1 Introduc'on • Today's session has two parts: – The first part will consider cryptographic privacy protecon for messaging other than email. – The second part will focus on cryptographic protecon of high speed internal links. • The common link between the two topics is that in each case, your op@ons are constrained by what the market offers. Today's goal is to help you understand why you want protec@on for these points of exposure, and how to select a solu@on. • Both of these topics are the subject of pending dra documents in the Pervasive Monitoring SIG. 2 I. Messaging Other Than Email 3 Messaging Other Than Email • M3AAWG has been working hard on protec@ng email against pervasive monitoring. • That's very important work, and protec@ng email privacy is a totally appropriate goal for M3AAWG. • Although M3AAWG has always had a strong focus on email, our charter, as the an@-Pervasive Monitoring SIG of the Messaging, Malware, and Mobile An-Abuse Working Group, includes, or should include, protec@ng mobile voice telephony and mobile applicaons (such as tex@ng/chat), too. • Arguably, for many users, secure mobile voice and secure text/ chat is as important, or even more important than email. -

National Security Agency | Cybersecurity Information Selecting
National Security Agency | Cybersecurity Information Selecting and Safely Using Collaboration Services for Telework - UPDATE Summary During a global pandemic or other crisis contingency scenarios, many United States Government (USG) personnel must operate from home while continuing to perform critical national functions and support continuity of government services. With limited access to government furnished equipment (GFE) such as laptops and secure smartphones, the use of (not typically approved) commercial collaboration services on personal devices for limited government official use becomes necessary and unavoidable. We define collaboration services as those capabilities that allow the workforce to communicate via internet-enabled text, voice, and video, and can include the sharing of files and other mission content. Collaboration can occur between two people or widened to include a large group to support mission needs. This document provides a snapshot of best practices and criteria based on capabilities available at the time of publication and was coordinated with the Department of Homeland Security (DHS), which has released similar guidance: “Cybersecurity Recommendations for Federal Agencies Using Video Conferencing” [1] and “Guidance for Securing Video Conferencing” [2]. This NSA publication is designed to provide simple and actionable considerations for individual government users. The intent of this document is not meant to be exhaustive or based on formal testing, but rather be responsive to a growing demand amongst the federal government to allow its workforce to operate remotely using personal devices when deemed to be in the best interests of the health and welfare of its workforce and the nation. Recommendations in this document are likely to change as collaboration services evolve and also address known vulnerabilities and threats. -

Warning Civilians Prior to Attack Under International Law: Theory and Practice
Color profile: Disabled Composite Default screen XIV Warning Civilians Prior to Attack under International Law: Theory and Practice Pnina Sharvit Baruch and Noam Neuman* primary goal of the modern law of armed conflict (also known as interna- Ational humanitarian law) is to protect civiliansasmuchaspossiblefromthe violent consequences of hostilities. Accordingly, the law of armed conflict requires that the parties to a conflict apply certain precautionary measures in order to mini- mize incidental injury to civilians resulting from military attacks. One of these pre- cautionary measures is the provision of warnings to civilians prior to an attack. This article will deal with this measure, and examine both theoretical and practical aspects of providing advance warnings of attacks. During World War II there were instances when civilians were warned prior to an attack. Advance warnings were also provided during other armed conflicts throughout the second half of the twentieth century; however, the amount, scope and specificity of warnings issued to civilians have dramatically increased in the conflicts fought since the beginning of this century. Probably the most elaborate and systematic warnings were issued by Israel in its conflict in Lebanon in 2006 and * Professor (Colonel, Israel Defense Forces (Ret.)) Pnina Sharvit Baruch, Tel Aviv University School of Law, Israel, and Lieutenant Colonel Noam Neuman, Israel Defense Forces. The opin- ions and conclusions expressed in this article are those of the authors and do not necessarily re- flect the views of the Israel Defense Forces or the government of Israel. We would like to thank Galit Rajuan, Nimrod Karin and David Benjamin for their valuable comments and suggestions. -

Issue 385 of Ofcom's Broadcast and on Demand Bulletin
Issue 385 of Ofcom’s Broadcast and On Demand Bulletin 27 August 2019 Issue number 385 27 August 2019 Issue 385 of Ofcom’s Broadcast and On Demand Bulletin 27 August 2019 Contents Introduction 3 Notice of Sanction Autonomous Non-profit Organisation TV-Novosti 5 Broadcast Standards cases In Breach The No Repeat 9 to 5 on Sam FM Sam FM Bristol, 20 May 2019, 12:34 7 Journey for Iqra Iqra Bangla, 28 March 2019, 20:00 9 Resolved The Music Marathon Gold, 27 May 2019, 12:45 15 Advertising Scheduling cases In Breach Advertising minutage ATN Bangla UK, various dates between 27 January 2019 and 10 March 2019 19 Advertising minutage Sony Entertainment Television, various dates between 24 February 2019 and 14 April 2019 20 Broadcast Licence Conditions cases In Breach Providing a service in accordance with ‘Key Commitments’ EAVA FM, St Mathews Community Solution Centre Ltd, 6 to 12 May 2019 22 Retention and production of recordings ATN Bangla UK, ATN Bangla UK Limited 25 Tables of cases Complaints assessed, not investigated 27 Complaints outside of remit 38 BBC First 40 Investigations List 42 Issue 385 of Ofcom’s Broadcast and On Demand Bulletin 27 August 2019 Introduction Under the Communications Act 2003 (“the Act”), Ofcom has a duty to set standards for broadcast content to secure the standards objectives1. Ofcom also has a duty to ensure that On Demand Programme Services (“ODPS”) comply with certain standards requirements set out in the Act2. Ofcom reflects these requirements in its codes and rules. The Broadcast and On Demand Bulletin reports on the outcome of Ofcom’s investigations into alleged breaches of its codes and rules, as well as conditions with which broadcasters licensed by Ofcom are required to comply. -

The Occupation of Palestinian Art: Maps, Land, Destruction and Concealment
The Occupation of Palestinian Art: Maps, Land, Destruction and Concealment Garrett Bailey A New Middle East?: Diagrams, Diagnosis and Power June 2016 1 Abstract Violence in the Middle East has been the focal point in news media. My paper has shifted the focus to forms of non-violent resistance as it pertains to Israel- Palestine. Palestinians have used art as a means of resistance before Israel declared itself a state in 1948. By focusing on Palestinian artists, I am able to show the ways in which art can reveal and counter Israeli Zionists rhetoric. Artists tear down the fallacies of Zionist propaganda through non-violent means. Resistance art is expressed in different forms, from maps, architecture and sculpture to film and graffiti. By examining Palestinian artists' work throughout the history of the Israeli-Palestine conflict, I am able to find out more about Israel's settlement building, border technology, pro-Israel lobbies, the tactics of the Israel Defense Force, and the censorship of Palestinian art. 2 Palestinians have engaged in non-violent resistance from the beginning of Israel's military occupation. Through an examination of maps, architecture, graffiti and film, I explore Israel's military tactics and their mechanisms of control. How does art shape the perceptions and realities of Israel/Palestine? Palestinian art is a necessary tool in exposing the oppression of the Israeli government and countering Zionist rhetoric. Zionism's purpose in the early 20th century was to find a homeland for the Jewish people living in the diaspora, proving the fall of the Ottoman Empire after World War One disastrous for the Palestinians.