Elliptic Curve Cryptography on Smart Cards
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Laser-Marked Document Showing a Colour-Shift Effect
(19) & (11) EP 2 174 797 A1 (12) EUROPEAN PATENT APPLICATION (43) Date of publication: (51) Int Cl.: 14.04.2010 Bulletin 2010/15 B42D 15/00 (2006.01) B42D 15/10 (2006.01) B41M 5/24 (2006.01) B41M 3/14 (2006.01) (21) Application number: 08017527.6 (22) Date of filing: 07.10.2008 (84) Designated Contracting States: • Klein, Sylke AT BE BG CH CY CZ DE DK EE ES FI FR GB GR 64380 Rossdorf (DE) HR HU IE IS IT LI LT LU LV MC MT NL NO PL PT • Montag, Heidemarie RO SE SI SK TR 64289 Darmstadt (DE) Designated Extension States: AL BA MK RS (74) Representative: Luderschmidt, Schüler & Partner Patentanwälte (71) Applicant: European Central Bank John-F.-Kennedy-Strasse 4 60311 Frankfurt am Main (DE) 65189 Wiesbaden (DE) (72) Inventors: • Arrieta, Antonio Jesús 60311 Frankfurt am Main (DE) (54) Laser-marked document showing a colour-shift effect (57) Document comprising a coating containing at the coated area with a pulsed laser beam at a rate of least one sort of effect pigments, wherein said document greater than 500 mm/s and a laser mark having a colour also comprises at least one laser mark having a high shift effect is obtained. contrast and a strong colour shift effect The authenticity of the document can be easily Said document is obtainable by a process, wherein, checked by visual inspection from different viewing an- a document comprising a coating containing at least one gles. sort of effectpigments which show differentcolours under different viewing angles is treated on at least a part of EP 2 174 797 A1 Printed by Jouve, 75001 PARIS (FR) EP 2 174 797 A1 Description BACKGROUND OF THE INVENTION 5 1. -

Bitcoin: a Seemingly Rampant Elevator, Or Is Someone Pushing Its Buttons?
Södertörn University | Institution for Social Sciences Bachelor Thesis (15 hp) | Business Studies - Finance | Spring Semester 2014 Bitcoin: A Seemingly Rampant Elevator, or is Someone Pushing its Buttons? - A Case Study on Bitcoin’s Fluctuations in Price and Concept. Author: Oscar Wandery Supervisor: Maria Smolander Stockholm Södertörn University Business Studies Abstract This study looks at the price mechanism of the digital quasi-currency bitcoin. Through statistical analysis of secondary data a probable significant results regarding correlation and regression between price and different independent variables have been established. The final analysis is pointing towards network effects being a part of the determinants for the crypto-currency’s price. Complimentary to the quantitative study explained above, an implementation of hermeneutic analysis based on secondary theoretical sources, journalistic opinion and a professional qualified judgment has aided the author and study in conceptual understanding. This interpretation has semantic character, and takes a Socratic kickoff regarding the nature of bitcoin as a financial instrument. The analysis runs back and forth throughout the course of the study and finally intertwines with qualitative results in the discussion. It is the author’s impression that a significant dimorphism surrounds bitcoin, calling for a conceptual differentiation leading to practical rethinking. The study takes the shape of a case-study conducted over four months. The author’s location during the process of writing was Stockholm Sweden, but the gathered data is of transnational character. Keywords: Bitcoin, crypto-currency, money, digital money, price fluctuations, financial instruments, financial systems. 2 Stockholm Södertörn University Business Studies Sammanfattning Den här studien tittar på prismekanismen hos den digitala kvasi-valören bitcoin. -

AUTOMATED TELLER MACHINE (Athl) NETWORK EVOLUTION in AMERICAN RETAIL BANKING: WHAT DRIVES IT?
AUTOMATED TELLER MACHINE (AThl) NETWORK EVOLUTION IN AMERICAN RETAIL BANKING: WHAT DRIVES IT? Robert J. Kauffiiian Leollard N.Stern School of Busivless New 'r'osk Universit,y Re\\. %sk, Net.\' York 10003 Mary Beth Tlieisen J,eorr;~rd n'. Stcr~iSchool of B~~sincss New \'orl; University New York, NY 10006 C'e~~terfor Rcseai.clt 011 Irlfor~i~ntion Systclns lnfoornlation Systen~sI)epar%ment 1,eojrarcl K.Stelm Sclrool of' Busir~ess New York ITuiversity Working Paper Series STERN IS-91-2 Center for Digital Economy Research Stem School of Business Working Paper IS-91-02 Center for Digital Economy Research Stem School of Business IVorking Paper IS-91-02 AUTOMATED TELLER MACHINE (ATM) NETWORK EVOLUTION IN AMERICAN RETAIL BANKING: WHAT DRIVES IT? ABSTRACT The organization of automated teller machine (ATM) and electronic banking services in the United States has undergone significant structural changes in the past two or three years that raise questions about the long term prospects for the retail banking industry, the nature of network competition, ATM service pricing, and what role ATMs will play in the development of an interstate banking system. In this paper we investigate ways that banks use ATM services and membership in ATM networks as strategic marketing tools. We also examine how the changes in the size, number, and ownership of ATM networks (from banks or groups of banks to independent operators) have impacted the structure of ATM deployment in the retail banking industry. Finally, we consider how movement toward market saturation is changing how the public values electronic banking services, and what this means for bankers. -
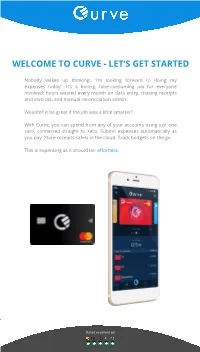
Curve - Let’S Get Started
WELCOME TO CURVE - LET’S GET STARTED Nobody wakes up thinking: “I’m looking forward to doing my expenses today”. It’s a boring, time-consuming job for everyone involved; hours wasted every month on data entry, chasing receipts and invoices, and manual reconciliation admin. Wouldn’t it be great if the job was a little smarter? With Curve, you can spend from any of your accounts using just one card, connected straight to Xero. Submit expenses automatically as you pay. Store receipts safely in the cloud. Track budgets on the go. This is expensing as it should be: effortless. Rated excellent on LIFE WITH CURVE + XERO No expense headaches Easier bookkeeping Smarter cashflow Curve: the card built with small businesses, freelancers, and entrepreneurs in mind. WHAT IS CURVE? With Curve, you can spend from anywhere from any of your bank accounts using just one smart Curve card, connected to an even smarter app. Curve works just like a normal bank card, and can be used anywhere in the world that accepts Mastercard. In addition, Curve cardholders collect Curve Rewards points whenever they spend at over 45 leading UK retailers, cut out foreign exchange fees on business trips, and can track their purchase history any time straight from the app. CONNECTING TO XERO WITH CURVE After getting set up with your You can find Xero inside the Tap “Connect to Xero” to new Curve card, securely Curve Connect tab. begin. add your existing debit and credit cards to the app. Log-in to your Xero account. Choose your company’s Get to know the basics. -

APPENDIX G-2.C Credit Card Defaults, Credit Card Profits, and Bankruptcy
APPENDIX G-2.c Credit Card Defaults, Credit Card Profits, and Bankruptcy (Prepared by Professor Lawrence M. Ausubel) Reprinted from The American Bankruptcy Law Journal, Vol. 71, Spring 1997, pp. 249-270. Copyright 1997 by Lawrence M. Ausubel. Credit Card Defaults, Credit Card Profits, and Bankruptcy by Lawrence M. Ausubel* Credit card defaults have become an increasingly conspicuous feature on the bankruptcy landscape. In 1996, bank credit card delinquencies exceeded 3.5 percent—the highest delinquency rate since 1973, when statistics were first collected.1 Bank credit card chargeoffs also veered upward to 4.5 percent per year, exceeding all but the levels recorded during the years 1991!1992.2 At the same time, personal bankruptcy filings reached a record high 290,111 in the quarter ending September 30, 1996—up thirty-one percent from the corresponding period one year earlier—and surpassed one million for the first year ever in 1996.3 Both credit card defaults and bankruptcies soared amid a generally healthy economy with relatively low unemployment4 and reasonable growth in gross domestic product.5 Wall Street analysts warned that the consumer balance sheet was heading toward a precipice which endangered the health of the banking system, if not the economic expansion generally.6 Bankruptcies and credit card debt have even achieved prominence in the national political debate. In the first 1996 presidential debate, Senator Robert Dole responded to his initial question on the economy by referring to the record bankruptcy rate: *Professor of Economics, University of Maryland at College Park. Copyright 1997. All rights reserved. This Article is based on a paper presented by the author at the Seventieth Annual Meeting of the National Conference of Bankruptcy Judges, San Diego, California, October 16-19, 1996. -

PIN Distribution by SMS a SPA’S White Paper
PIN distribution by SMS A SPA’s White paper November 2012 shaping the future of payment technology Table of Contents 1. Executive summary ................................................................... 4 2. Introduction .............................................................................. 5 2.1. Context ................................................................................................. 5 2.2. Scope .................................................................................................... 5 2.3. Definitions ............................................................................................. 6 2.4. Growing PIN and mobile phone usage ................................................... 6 3. Benefits ..................................................................................... 8 3.1. Generates additional revenues .............................................................. 8 3.1.1. Initial PIN with new payment card ...................................................................... 8 3.1.2. PIN reminder ................................................................................................... 9 3.2. Reduces cost of traditional PIN mailer ................................................ 10 3.3. Improves customer convenience ......................................................... 10 3.4. Enables differentiation ........................................................................ 11 3.5. Mitigates risks of traditional PIN mailer ............................................. -

Merchants Payment Coalition Meeting
Meeting Between Federal Reserve Staff and Merchants Payment Coalition November 2, 2010 Participants: Representatives of the Merchants Payment Coalition (MPC), Walmart, Sears Financial Services, Publix Super Markets, The Kroger Co., Best Buy, 7-11, Charming Shops, and Supervalu. Louise Roseman, David Mills, Robin Prager, Mark Manuszak, Edith Collis, Chris Clubb, Dena Milligan, Joshua Hart, Stephanie Martin, David Stein, and Ky Tran-Trong (Federal Reserve Board); Julia Cheney (Federal Reserve Bank of Philadelphia) Summary: Federal Reserve staff met with representatives of the MPC, merchants and other individuals representing merchants (collectively referred to as "merchants") to discuss the interchange fee provisions of the Dodd-Frank Wall Street Reform and Consumer Protection Act (the "Dodd-Frank Act"). MPC is a trade organization that represents about 2.7 million retail stores. Using prepared materials, representatives of the merchants outlined economic principles of regulation and expressed views as to their preferred approaches for implementing the interchange fee provisions of the Dodd-Frank Act. Specifically, representatives of the merchants expressed their preference for a presumptive at-par interchange fee, limiting the fraud adjustment to issuer-specific actions that demonstrably prevent fraud, imposing limits on fees charged to merchants, and requiring at least two networks per authorization method on a debit card. A copy of the prepared materials is attached. [note1 A revised version of the materials distributed at the meeting has been attached to this summary at the request of MPC. [end of note.] CONSTANTINE CANNON Jeffrey I. Shinder NEW YORK WASHINGTON Attorney at Law 212-350-2709 [email protected] October 27, 2010 BY E-MAIL Ms. -

American Express Company
UNITED STATES SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 Form 10-K ☑ ANNUAL REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the fiscal year ended December 31, 2020 OR ☐ TRANSITION REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the transition period from to Commission File No. 1-7657 American Express Company (Exact name of registrant as specified in its charter) New York 13-4922250 (State or other jurisdiction of incorporation or organization) (I.R.S. Employer Identification No.) 200 Vesey Street New York, New York 10285 (Address of principal executive offices) (Zip Code) Registrant’s telephone number, including area code: (212) 640-2000 Securities registered pursuant to Section 12(b) of the Act: Title of each class Trading Symbol(s) Name of each exchange on which registered Common Shares (par value $0.20 per Share) AXP New York Stock Exchange Securities registered pursuant to section 12(g) of the Act: None Indicate by check mark if the registrant is a well-known seasoned issuer, as defined in Rule 405 of the Securities Act. Yes þ No o Indicate by check mark if the registrant is not required to file reports pursuant to Section 13 or Section 15(d) of the Act. Yes o No þ Indicate by check mark whether the registrant (1) has filed all reports required to be filed by Section 13 or 15(d) of the Securities Exchange Act of 1934 during the preceding 12 months (or for such shorter period that the registrant was required to file such reports) and (2) has been subject to such filing requirements for the past 90 days. -

The Role of the Interchange Fee in Card Payment Systems
Éva Keszy-Harmath− Gergely Kóczán−Surd Kováts− Boris Martinovic−Kristóf Takács The role of the interchange fee in card payment systems MNB OCCASIONAL PAPERS 96. 2012 Éva Keszy-Harmath− Gergely Kóczán−Surd Kováts− Boris Martinovic−Kristóf Takács The role of the interchange fee in card payment systems MNB OCCASIONAL PAPERS 96. 2012 The views expressed here are those of the authors and do not necessarily reflect the official view of the central bank of Hungary (Magyar Nemzeti Bank). Occasional Papers 96. The role of the interchange fee in card payment systems (A bankközi jutalék szerepe a kártyás fizetési rendszerekben) Written by: Éva Keszy-Harmath, Gergely Kóczán, Surd Kováts*, Boris Martinovic*, Kristóf Takács (Magyar Nemzeti Bank, Payments and Securities Settlement) Budapest, January 2012 Published by the Magyar Nemzeti Bank Publisher in charge: dr. András Simon Szabadság tér 8−9., H−1850 Budapest www.mnb.hu ISSN 1585-5678 (online) * Hungarian Competition Authority (GVH). Contents Abstract 5 1 Introduction 6 2 Development and operation of the interchange fee 7 2.1 The four-party card system 7 2.2 Merchant and interchange fees 7 3 Economic background of the interchange fee 11 3.1 Two-sided markets and network externalities 11 3.2 Usage externalities and interchange fee models 13 4 Competitive assessment of the interchange fee 18 4.1 Competition related problems in connection with the interchange fee 18 4.2 Solutions other than the interchange fee 20 5 Competition proceedings related to the interchange fee 22 5.1 Competition proceedings -

A Guide to EMV Chip Technology November 2014
EMVCo, LLC Version 2.0 A Guide to EMV Chip Technology November 2014 A Guide to EMV Chip Technology Version 2.0 November 2014 - 1 - Copyright © 2014 EMVCo, LLC. All rights reserved. EMVCo, LLC Version 2.0 A Guide to EMV Chip Technology November 2014 Table of Contents TABLE OF CONTENTS .................................................................................................................. 2 LIST OF FIGURES .......................................................................................................................... 3 1 INTRODUCTION ................................................................................................................ 4 1.1 Purpose .......................................................................................................................... 4 1.2 References ..................................................................................................................... 4 2 BACKGROUND ................................................................................................................. 5 2.1 What are the EMV Chip Specifications? ........................................................................ 5 2.2 Why EMV Chip Technology? ......................................................................................... 6 3 THE HISTORY OF THE EMV CHIP SPECIFICATIONS ................................................... 8 3.1 Timeline .......................................................................................................................... 8 3.1.1 The Need -

Top 150 Merchant Acquirers Worldwide Companies from 45 Countries Generated 342.2 Billion Purchase Transactions
ISSUE 1183 SEPTEMBER 2020 ARTICLES IN THIS ISSUE p5 Top 150 Merchant Acquirers p12 Acquiring-as-a-Service Worldwide Platform from FSS p7 Top 100 U.S. Mastercard and p13 Point of Sale Terminal Visa Issuers at Midyear Manufacturers — Part 2 p10 Buy Now, Pay Later Funding p14 Top General Purpose Deals in 2020 Credit Card Issuers in the United States at Midyear p11 PayNearMe Payment Processing TRANSACTIONS (BIL.) IN 2019 Top 150 Merchant Acquirers Worldwide Companies from 45 countries generated 342.2 billion purchase transactions. The six companies listed below accounted for 41% or 141.8 billion of those transactions. Read full article on page 5 FIS (WORLDPAY) 36.72 JPMORGAN CHASE 29.41 SBERBANK 20.61 FISERV 20.36 (FIRST DATA) BANK OF 18.56 AMERICA 16.19 GLOBAL PAYMENTS FOR 50 YEARS, THE LEADING PUBLICATION COVERING PAYMENT SYSTEMS WORLDWIDE CONTENTS COVER STORY Top 150 Merchant Acquirers Outstandings for the top 10 Worldwide Acquirers headquartered in 45 countries included 32 in the U.S. issuers of Mastercard and U.S., 10 in Turkey, 7 in France, Russia, and Iran, and 5 in Brazil Visa credit cards totaled and Japan. p5 $569 bil. as of June 30, 2020, down 9.8% from June 30, 2019 Top 100 U.S. Issuers of Visa and Mastercard Credit Cards at Midyear Rankings are based on outstandings as of June 30, 2020 and on purchase volume for January 1 through June 30, 2020. Acquiring-as-a-Service Platform p7 from FSS Embark is a cloud-based managed service accessed through a single connection and integration. -

View Mini White Paper Sample
Understand the Business Impact of EMV Chip Cards 3 What About Mail/Telephone Order and eCommerce? 3 What Is EMV 3 How Chip Cards Work Upgrading Card 3 Contactless Technology 4 Background: Behind the Curve Security at 4 Liability Shift 5 Should You Adopt Chip Technology? the Point of Sale 5 Possible Reasons to Wait 6 Who’s Ready and Who’s Not? A revolution in credit and debit card technology is underway to make card-present transactions in the U.S. more secure. While companies of all sizes are making changes, many do not understand what is happening. U.S. companies are encouraged to update their technology for reading credit and EMV technology can debit cards from the swipe system to a more secure one that involves reading data on microchips embedded in payment cards. This EMV technology, named for the significantly reduce the risk companies that developed it – Europay, MasterCard and Visa – can significantly reduce of card-present counterfeit the risk of card-present counterfeit, as well as lost and stolen card fraud because chip and lost and stolen card cards are nearly impossible to counterfeit. There is unique information both in the chip and the magnetic stripe to indicate that it is a chip card. The card information if fraud. Chip cards have skimmed could only be used for card-not-present transactions. been widely used in other Chip cards have been widely used in other countries since 19861. U.S. companies have countries since 1986, but been reluctant to adopt them primarily because the new technology is expensive and U.S.