Linux VDS User's Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Linux Administrators Security Guide LASG - 0.1.1
Linux Administrators Security Guide LASG - 0.1.1 By Kurt Seifried ([email protected]) copyright 1999, All rights reserved. Available at: https://www.seifried.org/lasg/. This document is free for most non commercial uses, the license follows the table of contents, please read it if you have any concerns. If you have any questions email [email protected]. A mailing list is available, send an email to [email protected], with "subscribe lasg-announce" in the body (no quotes) and you will be automatically added. 1 Table of contents License Preface Forward by the author Contributing What this guide is and isn't How to determine what to secure and how to secure it Safe installation of Linux Choosing your install media It ain't over 'til... General concepts, server verses workstations, etc Physical / Boot security Physical access The computer BIOS LILO The Linux kernel Upgrading and compiling the kernel Kernel versions Administrative tools Access Telnet SSH LSH REXEC NSH Slush SSL Telnet Fsh secsh Local YaST sudo Super Remote Webmin Linuxconf COAS 2 System Files /etc/passwd /etc/shadow /etc/groups /etc/gshadow /etc/login.defs /etc/shells /etc/securetty Log files and other forms of monitoring General log security sysklogd / klogd secure-syslog next generation syslog Log monitoring logcheck colorlogs WOTS swatch Kernel logging auditd Shell logging bash Shadow passwords Cracking passwords John the ripper Crack Saltine cracker VCU PAM Software Management RPM dpkg tarballs / tgz Checking file integrity RPM dpkg PGP MD5 Automatic -
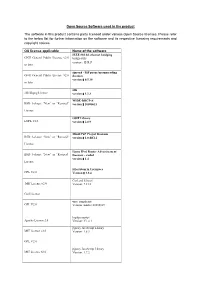
Open Source Software Used in the Product the Software in This Product Contains Parts Licensed Under Various Open Source Licenses
Open Source Software used in the product The software in this product contains parts licensed under various Open Source licenses. Please refer to the below list for further information on the software and its respective licensing requirements and copyright notices. OS license applicable Name of the software IEEE 802.1d ethernet bridging GNU General Public License v2.0 bridge-utils version:0.9.7 or later siproxd - SIP proxy/masquerading GNU General Public License v2.0 daemon version:0.5.10 or later zlib zlib/libpng License version:1.2.3 WIDE-DHCPv6 BSD 3-clause “New” or “Revised” version:20080615 License OSIP Library LGPL V2.1 version:2.0.9 MiniUPnP Project Daemon BSD 3-clause “New” or “Revised” version:1.0-RC12 License Linux IPv6 Router Advertisement BSD 3-clause “New” or “Revised” Daemon – radvd version:1.4 License Filesystem in Userspace GPL V2.0 Version:2.8.4 Curl and Libcurl MIT License v2.0 Version: 7.21.3 Curl License wpa_supplicant GPL V2.0 Version: master-20110109 log4javascript Apache License 2.0 Version: V1.4.1 jQuery JavaScript Library MIT License v2.0 Version: 1.8.3 GPL V2.0 jQuery JavaScript Library MIT License v2.0 Version: 1.7.2 GPL V2.0 Jqueryjs MIT License v2.0 Version: 1.4.4 theWall - pc_pppoe BSD 3-clause license Version: 0.2 Endian Firewall Community GPL V2.0 Version: EFW-2.3 Struts EJB LGPL V2.1 Version: 1.3 Linux Kernel GPL V2.0 version:2.6.35 Free BSD BSD 2-clause license Version: 5.0 ssltunnel BSD 2-clause license Version: 1.16.0.3 ZMailer BSD 2-clause license Version: 2.99.57 kakaxi-project trunk-20120909-svn: Apache License 2.0 Android - platform - bootable - BSD 2-clause license bootloader – legacy 2.2_r1 Android – platform – bionic BSD 2-clause license Version: 2.3_r1 Android - platform - system - core Apache License 2.0 2.3_r1 Android – platform – external – GPL V2.0 wpa_supplicant Version: 2.2_r1 You may obtain the most recent version of the source for free by downloading it from the supplier`s website http://download- c.huawei.com/download/downloadCenter?downloadId=20841&version=35510&siteCode=worldwide . -

Linux Administrators Security Guide LASG - 0.1.0
Linux Administrators Security Guide LASG - 0.1.0 By Kurt Seifried ([email protected]) copyright 1999, All rights reserved. Available at: https://www.seifried.org/lasg/ This document is free for most non commercial uses, the license follows the table of contents, please read it if you have any concerns. If you have any questions email [email protected]. If you want to receive announcements of new versions of the LASG please send a blank email with the subject line “subscribe” (no quotes) to [email protected]. 1 Table of contents License Preface Forward by the author Contributing What this guide is and isn't How to determine what to secure and how to secure it Safe installation of Linux Choosing your install media It ain't over 'til... General concepts, server verses workstations, etc Physical / Boot security Physical access The computer BIOS LILO The Linux kernel Upgrading and compiling the kernel Kernel versions Administrative tools Access Telnet SSH LSH REXEC NSH Slush SSL Telnet Fsh secsh Local YaST sudo Super Remote Webmin Linuxconf COAS 2 System Files /etc/passwd /etc/shadow /etc/groups /etc/gshadow /etc/login.defs /etc/shells /etc/securetty Log files and other forms of monitoring sysklogd / klogd secure-syslog next generation syslog Log monitoring logcheck colorlogs WOTS swatch Kernel logging auditd Shell logging bash Shadow passwords Cracking passwords Jack the ripper Crack Saltine cracker VCU PAM Software Management RPM dpkg tarballs / tgz Checking file integrity RPM dpkg PGP MD5 Automatic updates RPM AutoRPM -

Name Synopsis Description
SMTPSERVER(8zm) SMTPSERVER(8zm) NAME smtpserver − zmailer SMTP server SYNOPSIS smtpserver [-46aBhigntVvw][-p port][-l SYSLOG][-l logfile][-s[ftveRSDh]] [-s strict] [-s sloppy][-I pidfile][-L maxloadaver][-M SMTPmaxsize][-P postoffice][-R router] [-C cfgfile][-Z zenvfile][-T '[1.2.3.4]'] DESCRIPTION This program implements the server side of the SMTP protocol as defined in RFC-2821, and knows about the common extensions to the protocol expected by sendmail and BSMTP clients. By default the program will kill the previous smtpserver (8zm) daemon, if any, then detach and lis- ten for SMTP connections. Incoming messages will be submitted for processing using the zmailer (3zm) interface to ZMailer. Non-trivial address checking is done asynchronously, although this behaviour can be changed by a command line option if you cannot afford to transfer data just to bounce it back. Complex routing analysis checking is done by executing the router (8zm) program in interactive mode, and executing a well-known shell function with well-known parameters for each request. Traditionally this task has needed starting router process (and some other processes) underneath each incoming SMTP session, which is not a very lightweight thing. Current version has prestarted farm of auxiliary server processes that can be used to handle com- plex things, and they can amortize e.g. router startup cost among lots of actual users making the use of routing in reception time very cheap in terms of resources. Presently system starts a master process that starts a set of auxiliary processes, and keeps inter- nal nameless rendezvous sockets for each of them. -

The Qmail Handbook by Dave Sill ISBN:1893115402 Apress 2002 (492 Pages)
< Free Open Study > The qmail Handbook by Dave Sill ISBN:1893115402 Apress 2002 (492 pages) This guide begins with a discussion of qmail s history, architecture and features, and then goes into a thorough investigation of the installation and configuration process. Table of Contents The qmail Handbook Introduction Ch apt - Introducing qmail er 1 Ch apt - Installing qmail er 2 Ch apt - Configuring qmail: The Basics er 3 Ch apt - Using qmail er 4 Ch apt - Managing qmail er 5 Ch apt - Troubleshooting qmail er 6 Ch apt - Configuring qmail: Advanced Options er 7 Ch apt - Controlling Junk Mail er 8 Ch apt - Managing Mailing Lists er 9 Ch apt - Serving Mailboxes er 10 Ch apt - Hosting Virtual Domain and Users er 11 Ch apt - Understanding Advanced Topics er 12 Ap pe ndi - How qmail Works x A Ap pe ndi - Related Packages x B Ap pe ndi - How Internet Mail Works x C Ap pe ndi - qmail Features x D Ap pe - Error Messages ndi x E Ap pe - Gotchas ndi x F Index List of Figures List of Tables List of Listings < Free Open Study > < Free Open Study > Back Cover • Provides thorough instruction for installing, configuring, and optimizing qmail • Includes coverage of secure networking, troubleshooting issues, and mailing list administration • Covers what system administrators want to know by concentrating on qmail issues relevant to daily operation • Includes instructions on how to filter spam before it reaches the client The qmail Handbook will guide system and mail administrators of all skill levels through installing, configuring, and maintaining the qmail server. -

Guide to Unix/ Commands 1
Guide_on_Unix [email protected] PDF generated using the open source mwlib toolkit. See http://code.pediapress.com/ for more information. PDF generated at: Wed, 11 Nov 2009 14:39:13 UTC Contents Articles Guide to Unix/ Commands 1 Guide to Unix/ Commands/ Summary 2 Guide to Unix/ Commands/ Getting Help 9 Guide to Unix/ Commands/ File System Utilities 11 Guide to Unix/ Commands/ Finding Files 23 Guide to Unix/ Commands/ File Viewing 25 Guide to Unix/ Commands/ File Editing 29 Guide to Unix/ Commands/ File Compression 30 Guide to Unix/ Commands/ File Analysing 34 Guide to Unix/ Commands/ Multiuser Commands 35 Guide to Unix/ Commands/ Self Information 37 Guide to Unix/ Commands/ System Information 38 Guide to Unix/ Commands/ Networking 42 Guide to Unix/ Commands/ Process Management 47 Guide to Unix/ Commands/ Devices 49 Guide to Unix/ Commands/ Kernel Commands 50 Guide to Unix/ Commands/ compress Commands 51 Guide to Unix/ Commands/ Miscellaneous 51 Guide to Unix/ Environment Variables 55 Guide to Unix/ Files 58 Guide to Unix/ BSD/ Introduction 65 Guide to Unix/ BSD/ OpenBSD 67 Guide to Unix/ Explanations/ Shell Prompt 69 Guide to Unix/ Explanations/ Quoting and Filename Expansion 73 Guide to Unix/ Explanations/ Pipes and Job Control 76 Guide to Unix/ Explanations/ Signals 77 Bourne Shell Scripting/ Quick Reference 80 Guide to Unix/ Explanations/ Introduction to Editors 85 Learning the vi editor/ vi Reference 88 Guide to Unix/ GNU Free Documentation License 98 References Article Sources and Contributors 104 Article Licenses License 105 Guide to Unix/Commands 1 Guide to Unix/ Commands The Unix command line is often considered difficult to learn. -

Installation Manual for LISTSERV for Unix 16.0-2017A
L-Soft international, Inc. Installation Manual for LISTSERV® for UNIX(R) Version 16.0 2017a Level Set Release This document describes the installation of LISTSERV 16.0-2017a for UNIX with a build date of February 28, 2017 or later. Information in this document is subject to change without notice. Companies, names, and data used in examples herein are fictitious unless otherwise noted. L-Soft international, Inc. does not endorse or approve the use of any of the product names or trademarks appearing in this document. Permission is granted to copy this document, at no charge and in its entirety, provided that the copies are not used for commercial advantage, that the source is cited, and that the present copyright notice is included in all copies so that the recipients of such copies are equally bound to abide by the present conditions. Prior written permission is required for any commercial use of this document, in whole or in part, and for any partial reproduction of the contents of this document exceeding 50 lines of up to 80 characters, or equivalent. The title page, table of contents and index, if any, are not considered part of the document for the purposes of this copyright notice, and can be freely removed if present. Copyright 2009-2017, L-Soft international, Inc. All Rights Reserved Worldwide. LISTSERV is a registered trademark licensed to L-Soft international, Inc. ListPlex, CataList, and EASE are service marks of L-Soft international, Inc. All other trademarks, both marked and not marked, are the property of their respective owners. -

OPENSOURCES Voices from the Open Source Revolution Michael Tiemann Future of Cygnus Solutions: an Entrepreneur’S Account
Eric S. Raymond A Brief History of Hackerdom Marshall Kirk McKusick Twenty Years of Berkeley Unix: From AT&T-Owned to Freely Redistributable Scott Bradner The Internet Engineering Task Force Richard Stallman The GNU Operating System and the Free Software Movement OPENSOURCES Voices from the Open Source Revolution Michael Tiemann Future of Cygnus Solutions: An Entrepreneur’s Account Paul Vixie Software Engineering Linus Torvalds The Linux Edge Robert Young Giving It Away: How Red Hat Software Stumbled Across a New Economic Model and Helped Improve an Industry Larry Wall Diligence, Patience, and Humility Bruce Perens The Open Source Definition Tim O'Reilly Hardware, Software, and Infoware Jim Hamerly and Tom Paquin with Susan Walton Freeing the Source: The Story of Mozilla Eric S. Raymond Edited by The Revenge of the Hackers Chris DiBona, Sam Ockman and Mark Stone OPENSOURCES Voices from the Open Source Revolution Edited by Chris DiBona, Sam Ockman and Mark Stone Copyright “Free Software” is Copyright c ; 1998 Richard M. Stallman Verbatim copying and duplication is permitted in any medium provided this notice is preserved. “A Brief History of Hackerdom” and “Revenge of the Hackers” are Copyright c ; 1998 Eric S. Raymond. These essays are free; you can redistribute them and/or modify them under the terms of the GNU General Public License as published by the Free Software Foundation; either version 2 of the License, or (at your option) any later version. These essays are distributed in the hope that they will be useful, but WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. -

GNU General Public License Version 2
Notice regarding Open Source software The product contains Open Source software that has been released by programmers under specific licensing requirements such as the „General Public License“ (GPL) Version 2 or 3, the „Lesser General Public License“ (LGPL), the „Apache License“ or similar licenses. To the extent that any accompanying material such as instruction manuals, handbooks etc. contain copyright notices, conditions of use or licensing requirements that contradict any applicable Open Source license, these conditions are inapplicable. The use and distribution of any Open Source software contained in the product is exclusively governed by the respective Open Source license. The software is provided by its programmers without ANY WARRANTY, whether implied or expressed, of any fitness for a particular purpose, and the programmers DECLINE ALL LIABILITY for damages, direct or indirect, that result from the use of this software. This disclaimer does in no way affect the responsibility of Vodafone. AVAILABILITY OF SOURCE CODE: Where the applicable license entitles you to the source code of such software and/or other additional data, you may obtain it for a period of three years after purchasing this product, and, if required by the license conditions, for as long as we offer customer support for the product. Vodafone provides two options for obtaining the source code: (1) You may obtain the most recent version of the source for free by downloading as below mentioned after the table of used Open source modules (2) You may obtain any version of the source code that has been distributed by Vodafone for the cost of reproduction of the physical copy with a cost of USD 10 by sending a request directly to: [email protected] or Huawei Industrial Base, Bantian, Longgang 518129, Shenzhen, P.R.C. -

Open Source Software Notice
文档名称 文档密级 OPEN SOURCE SOFTWARE NOTICE This document contains an open source software notice for this product. The open source software licenses are granted by the respective right holders. And the open source licenses prevails all other license information with regard to the respective open source software contained in the product. Warranty Disclaimer THE OPEN SOURCE SOFTWARE IN THIS PRODUCT IS DISTRIBUTED IN THE HOPE THAT IT WILL BE USEFUL, BUT WITHOUT ANY WARRANTY, WITHOUT EVEN THE IMPLIED WARRANTY OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. SEE THE APPLICABLE LICENSES FOR MORE DETAILS. Copyright Notice and License Texts Software: amrnb-5.1.0 Copyright notice: Copyright© 2003, 3GPP Organizational Partners (ARIB, CWTS, ETSI, T1, TTA, TTC). License: Use the BSD License Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met: 1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer. 2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution. THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, 2015-10-9 华为保密信息,未经授权禁止扩散 第 1 页, 共 173 页 文档名称 文档密级 SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. -

ESET Mail Security Installation Manual and User Guide Table of Contents
we protect digital worlds ESET Mail Security Installation Manual and User Guide Table of contents 1. Introduction .........................................................................................3 2. Terminology and abbreviations..........................................................5 3. Installation .............................................................................................9 4. Architecture Overview ......................................................................11 5. Integration with Email Messaging System.....................................15 5.1. Bi-directional email messages scanning in MTA...............................17 5.2. Scanning of inbound email messages. ................................................ 17 5.3. Scanning of outbound email messages...............................................18 5.4. Scanning of email messages being downloaded from POP3/ IMAP server.............................................................................................................18 5.5. Alternative methods of content filtering.............................................19 5.5.1. Scanning email messages using AMaViS.........................................19 6. Important ESET Mail Security mechanisms...................................21 6.1. Handle Object Policy .................................................................................. 22 6.2. User Specific Configuration ..................................................................... 23 6.3. Blacklist and Whitelist.................................................................................24 -

Designing and Writing Secure Application Code Outline General
Outline Designing and Writing General principles Secure Application Code • Least privilege, defense in depth, … Example • Sendmail vs qmail John Mitchell Tools for secure coding • Type-safe programming languages • Purify • Perl tainting • Code analysis algorithms • Run-time monitoring (another lecture) General topics in this course Before you start building … Vulnerabilities What are the security requirements? • How hackers break into systems • Confidentiality (secrets remain secret) – Circumvent security mechanisms (e.g., dictionary attack) • Integrity (meaning preserved) – Use code for purpose it was not intended (buffer overflow) • Availability Defensive programming • Accountability • Build all software with security in mind This What threats are possible? • Make sure video game is not a boot loader lecture Who do you trust / not trust? Security Mechanisms • Authentication • Access control Security = preserve properties against attack • Network protocols General advice Compartmentalization Compartmentalization Divide system into modules • Principle of least privilege • Each module serves a specific purpose • Minimize trust relationships • Assign different access rights to different modules Defense in depth – Read/write access to files • Use more than one security mechanism – Read user or network input • Secure the weakest link – Execute privileged instructions (e.g., Unix root) • Fail securely Principle of least privilege Keep it simple • Give each module only the rights it needs Consult experts • Don’t build what you can easily borrow/steal