Guide to Unix/ Commands 1
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Patrolling Fall 2008 75 Th Ranger Regiment Association, Inc
PATROLLING FALL 2008 75 TH RANGER REGIMENT ASSOCIATION, INC. VOLUME 23 ISSUE II Vietnamese Rangers (37 th Biet Dong Quan), and their US advisors inspect a captured NVA recoilless rifle during the battle at Khe Sanh, Tet, 1968. Trench lines were necessary due to sniper fire and constant incoming enemy rounds. Senior Advisor CPT Walter Gunn is in the forefront, Officers’ Messages ................................1-10 kneeling; SFC Willard Langdon, 4 th from right, with BDQ General ..................................11-24 & 72-80 patch. Unit Reports ........................................25-71 CHINA - BURMA - INDIA VIETNAM IRAN GRENADA PANAMA IRAQ SOMALIA AFGHANISTAN PATROLLING – FALL 2008 PATROLLING – FALL 2008 WHO WE ARE: The 75th Ranger Regiment Association, Inc., is a We have funded trips for families to visit their wounded sons and registered 501 (c) corporation, registered in the State of Georgia. We were husbands while they were in the hospital. We have purchased a learning founded in 1986 by a group of veterans of F/58, (LRP) and L/75 (Ranger). program soft ware for the son of one young Ranger who had a brain The first meeting was held on June 7, 1986, at Ft. Campbell, KY. tumor removed. The Army took care of the surgery, but no means existed OUR MISSION: to purchase the learning program. We fund the purchase of several awards 1. To identify and offer membership to all eligible 75th Infantry Rangers, for graduates of RIP and Ranger School. We have contributed to each of and members of the Long Range Reconnaissance Patrol the three Battalion’s Memorial Funds and Ranger Balls, Companies, Long Range Patrol Companies, Ranger and to the Airborne Memorial at Ft. -

Oracle Database Licensing Information, 11G Release 2 (11.2) E10594-26
Oracle® Database Licensing Information 11g Release 2 (11.2) E10594-26 July 2012 Oracle Database Licensing Information, 11g Release 2 (11.2) E10594-26 Copyright © 2004, 2012, Oracle and/or its affiliates. All rights reserved. Contributor: Manmeet Ahluwalia, Penny Avril, Charlie Berger, Michelle Bird, Carolyn Bruse, Rich Buchheim, Sandra Cheevers, Leo Cloutier, Bud Endress, Prabhaker Gongloor, Kevin Jernigan, Anil Khilani, Mughees Minhas, Trish McGonigle, Dennis MacNeil, Paul Narth, Anu Natarajan, Paul Needham, Martin Pena, Jill Robinson, Mark Townsend This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, delivered to U.S. Government end users are "commercial computer software" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. -

101 Useful Linux Commands - Haydenjames.Io
101 Useful Linux Commands - haydenjames.io Some of these commands require elevated permissions (sudo) to run. Enjoy! 1. Execute the previous command used: !! 2. Execute a previous command starting with a specific letter. Example: !s 3. Short way to copy or backup a file before you edit it. For example, copy nginx.conf cp nginx.conf{,.bak} 4. Toggle between current directory and last directory cd - 5. Move to parent (higher level) directory. Note the space! cd .. 6. Go to home directory cd ~ 7. Go to home directory cd $HOME 8. Go to home directory (when used alone) cd 9. Set permissions to 755. Corresponds to these permissions: (-rwx-r-x-r-x), arranged in this sequence: (owner-group-other) chmod 755 <filename> 10. Add execute permission to all users. chmod a+x <filename> 11. Changes ownership of a file or directory to . chown <username> 12. Make a backup copy of a file (named file.backup) cp <file> <file>.backup 13. Copy file1, use it to create file2 cp <file1> <file2> 14. Copy directory1 and all its contents (recursively) into directory2 cp -r <directory1> <directory2>/ 15. Display date date 16. Zero the sdb drive. You may want to use GParted to format the drive afterward. You need elevated permissions to run this (sudo). dd if=/dev/zero of=/dev/sdb 17. Display disk space usage df -h 18. Take detailed messages from OS and input to text file dmesg>dmesg.txt 19. Display a LOT of system information. I usually pipe output to less. You need elevated permissions to run this (sudo). -

The Oldest Rivalry in Computing Forget Apple Vs
Follow us on Twitter for more great Slate stories! Follow @slate BITWISE DECODING THE TECH WORLD. MAY 9 2014 9:57 AM The Oldest Rivalry in Computing Forget Apple vs. Google. Emacs and Vi have been battling for text-editor supremacy among programmers for 40 years. By David Auerbach An early Emacs manual cover from 1981. Courtesy of GNU Emacs n a world where both software and hardware frequently become obsolete right I on release, two rival programs can stake a claim to being among the longest-lived applications of all time. Both programs are about to enter their fifth decades. Both programs are text editors, for inputting and editing code, data files, raw HTML Web pages, and anything else. And they are mortal enemies. Their names are Emacs and Vi (styled by programmers as “vi”). These editors are legendary and ancient, no exaggeration. Both date back to at least 1976, making them older than the vast majority of people currently using them. Both programs are text editors, which means they are not WYSIWYG (what you see is what you get)—unlike, say, word processors like Microsoft Word, they do not format your words onscreen. Programming is very different from word processing, and the basic goal of Emacs and Vi—fast editing of source code (and any other text files)—has yet to become obsolete. Both have been in ongoing development for almost 40 years. These two wizened programs are as close to equally matched enemies as any two programs have ever been. If you know a programmer who uses one of them, there’s a good chance that she hates the other. -

Linux Administrators Security Guide LASG - 0.1.1
Linux Administrators Security Guide LASG - 0.1.1 By Kurt Seifried ([email protected]) copyright 1999, All rights reserved. Available at: https://www.seifried.org/lasg/. This document is free for most non commercial uses, the license follows the table of contents, please read it if you have any concerns. If you have any questions email [email protected]. A mailing list is available, send an email to [email protected], with "subscribe lasg-announce" in the body (no quotes) and you will be automatically added. 1 Table of contents License Preface Forward by the author Contributing What this guide is and isn't How to determine what to secure and how to secure it Safe installation of Linux Choosing your install media It ain't over 'til... General concepts, server verses workstations, etc Physical / Boot security Physical access The computer BIOS LILO The Linux kernel Upgrading and compiling the kernel Kernel versions Administrative tools Access Telnet SSH LSH REXEC NSH Slush SSL Telnet Fsh secsh Local YaST sudo Super Remote Webmin Linuxconf COAS 2 System Files /etc/passwd /etc/shadow /etc/groups /etc/gshadow /etc/login.defs /etc/shells /etc/securetty Log files and other forms of monitoring General log security sysklogd / klogd secure-syslog next generation syslog Log monitoring logcheck colorlogs WOTS swatch Kernel logging auditd Shell logging bash Shadow passwords Cracking passwords John the ripper Crack Saltine cracker VCU PAM Software Management RPM dpkg tarballs / tgz Checking file integrity RPM dpkg PGP MD5 Automatic -

Spyware • Automa�Cally Install Updates • Subscrip�Ons Must Be Renewed and Kept up to Date • Must They Always Be Ac�Ve?
9/25/13 The Frugal Firm Abra C. Siegel Siegel Law Offices, Ltd. 875 N Michigan Ave , 31st Floor Chicago, IL 60611 (312) 869-4279 Email: siegellawoffi[email protected] www.linkedin.com/in/abrasiegel Marc W. Matheny 244 N. College Avenue Indianapolis, IN 46202 (317) 639-3315 Email: [email protected] hp://www.marcmathenylaw.com 1 9/25/13 The Frugal Law Firm FRUGAL DOES NOT MEAN “CHEAP” Don’t break the bank. 2 9/25/13 Essenal Law Firm Technology • Core System: Mac or PC • Communicaons: Telephone, Email • Finances: AccounWng / Time & Billing • Workflow: Document Management • Systems: Pracce Management • Mobility: Smartphones and Tablets The Next Level • Document Assembly / Document Automaon • Strategy, Taccs and Execuon: Ligaon Soware • Specialty Soware • Advocacy Presentaon Tools • No Hands: Voice Recognion an Digital Dictaon Soware 3 9/25/13 TIME TO UPGRADE? • PC / Mac – average lifespan 3-5 years • Server – 5-7 years • Operang Systems and Soware – Support / No Support – “Goa Have it Syndrome” Copiers Scanners Fax • All in One • Separate Components • CoPiers / Printers – Inkjet v. Laser – Costs of Use 4 9/25/13 Desktop Scanners • Fujitsu ScanSnap – One Touch Scanning – Adobe Acrobat Pro – OCR Soware • Hitachi Magic Wand Can scan bound pages Smartphones • iPhone • Android • Windows • Apps 5 9/25/13 Alternave Telephone Systems • Cell Phones: Who needs a landline? • VOIP • Online Hosted Services Tablets and Apps • iPad • Android • Windows Surface Inexpensive Apps Mobile and Easy to Use 6 9/25/13 Email and Email Systems Ø Mozilla Thunderbird Ø Gmail Ø Case Management Soware • Word Processing • Presentaon • Spreadsheets 7 9/25/13 Case Management Tools Time & Billing 8 9/25/13 Pdf’ing Alternaves to Tradional Case Management Soware • Telephone text messaging • Google Calendar texts 9 9/25/13 Credit Card$ Credit Card$ • Advantages • Disadvantages • Ethical Issues 10 9/25/13 VIRTUAL RECEPTIONIST • NO employee costs. -

Learning the Vi Editor
Learning the vi Editor en.wikibooks.org December 29, 2013 On the 28th of April 2012 the contents of the English as well as German Wikibooks and Wikipedia projects were licensed under Creative Commons Attribution-ShareAlike 3.0 Unported license. A URI to this license is given in the list of figures on page 103. If this document is a derived work from the contents of one of these projects and the content was still licensed by the project under this license at the time of derivation this document has to be licensed under the same, a similar or a compatible license, as stated in section 4b of the license. The list of contributors is included in chapter Contributors on page 101. The licenses GPL, LGPL and GFDL are included in chapter Licenses on page 107, since this book and/or parts of it may or may not be licensed under one or more of these licenses, and thus require inclusion of these licenses. The licenses of the figures are given in the list of figures on page 103. This PDF was generated by the LATEX typesetting software. The LATEX source code is included as an attachment (source.7z.txt) in this PDF file. To extract the source from the PDF file, you can use the pdfdetach tool including in the poppler suite, or the http://www. pdflabs.com/tools/pdftk-the-pdf-toolkit/ utility. Some PDF viewers may also let you save the attachment to a file. After extracting it from the PDF file you have to rename it to source.7z. -

Freebsd and Netbsd on Small X86 Based Systems
FreeBSD and NetBSD on Small x86 Based Systems Dr. Adrian Steinmann <[email protected]> Asia BSD Conference in Tokyo, Japan March 17th, 2011 1 Introduction Who am I? • Ph.D. in Mathematical Physics (long time ago) • Webgroup Consulting AG (now) • IT Consulting Open Source, Security, Perl • FreeBSD since version 1.0 (1993) • NetBSD since version 3.0 (2005) • Traveling, Sculpting, Go AsiaBSDCon Tutorial March 17, 2011 in Tokyo, Japan “Installing and Running FreeBSD and NetBSD on Small x86 Based Systems” Dr. Adrian Steinmann <[email protected]> 2 Focus on Installing and Running FreeBSD and NetBSD on Compact Flash Systems (1) Overview of suitable SW for small x86 based systems with compact flash (CF) (2) Live CD / USB dists to try out and bootstrap onto a CF (3) Overview of HW for small x86 systems (4) Installation strategies: what needs special attention when doing installations to CF (5) Building your own custom Install/Maintenance RAMdisk AsiaBSDCon Tutorial March 17, 2011 in Tokyo, Japan “Installing and Running FreeBSD and NetBSD on Small x86 Based Systems” Dr. Adrian Steinmann <[email protected]> 3 FreeBSD for Small HW Many choices! – Too many? • PicoBSD / TinyBSD • miniBSD & m0n0wall • pfSense • FreeBSD livefs, memstick • NanoBSD • STYX. Others: druidbsd, Beastiebox, Cauldron Project, ... AsiaBSDCon Tutorial March 17, 2011 in Tokyo, Japan “Installing and Running FreeBSD and NetBSD on Small x86 Based Systems” Dr. Adrian Steinmann <[email protected]> 4 PicoBSD & miniBSD • PicoBSD (1998): Initial import into src/release/picobsd/ by Andrzej Bialecki <[email protected] -

Wildlife Management Activities and Practices
WILDLIFE MANAGEMENT ACTIVITIES AND PRACTICES COMPREHENSIVE WILDLIFE MANAGEMENT PLANNING GUIDELINES for the Edwards Plateau and Cross Timbers & Prairies Ecological Regions Revised April 2010 The following Texas Parks & Wildlife Department staff have contributed to this document: Mike Krueger, Technical Guidance Biologist – Lampasas Mike Reagan, Technical Guidance Biologist -- Wimberley Jim Dillard, Technical Guidance Biologist -- Mineral Wells (Retired) Kirby Brown, Private Lands and Habitat Program Director (Retired) Linda Campbell, Program Director, Private Lands & Public Hunting Program--Austin Linda McMurry, Private Lands and Public Hunting Program Assistant -- Austin With Additional Contributions From: Kevin Schwausch, Private Lands Biologist -- Burnet Terry Turney, Rare Species Biologist--San Marcos Trey Carpenter, Manager, Granger Wildlife Management Area Dale Prochaska, Private Lands Biologist – Kerr Wildlife Management Area Nathan Rains, Private Lands Biologist – Cleburne TABLE OF CONTENTS Comprehensive Wildlife Management Planning Guidelines Edwards Plateau and Cross Timbers & Prairies Ecological Regions Introduction Specific Habitat Management Practices HABITAT CONTROL EROSION CONTROL PREDATOR CONTROL PROVIDING SUPPLEMENTAL WATER PROVIDING SUPPLEMENTAL FOOD PROVIDING SUPPLEMENTAL SHELTER CENSUS APPENDICES APPENDIX A: General Habitat Management Considerations, Recommendations, and Intensity Levels APPENDIX B: Determining Qualification for Wildlife Management Use APPENDIX C: Wildlife Management Plan Overview APPENDIX D: Livestock -

Configuring and Using Mutt
Configuring and Using Mutt Ryan Curtin LUG@GT Ryan Curtin Configuring and Using Mutt - p. 1/21 Goals » Goals By the end of this presentation, hopefully, you should be able Introduction to: Basic Usage Know the differences between Mutt, Pine, and other CLI Making a muttrc mailreaders Questions and Comments? Know the capabilities of Mutt Configure Mutt to connect to GT PRISM accounts (IMAP) Configure Mutt to make parsing through mail easy Know basic Mutt commands Write a basic, working .muttrc Know where to find further reference on Mutt Ryan Curtin Configuring and Using Mutt - p. 2/21 What is Mutt? » Goals Mutt is a “small, but very powerful text-based mail client for Introduction Unix operating systems” » What is Mutt? » Why should I use mutt? » Comparison with Pine Based largely on the elm mail client » What else is out there? Highly customizable; keybindings, macros Basic Usage Features to support mailing-lists (list-reply) Making a muttrc Questions and Comments? IMAP, POP3 support MIME, DSN, PGP support Ryan Curtin Configuring and Using Mutt - p. 3/21 Why should I use mutt? » Goals Lightweight, fast, and simple Introduction » What is Mutt? » Why should I use mutt? Can run inside a screen session » Comparison with Pine » What else is out there? No need for an annoying mouse Basic Usage Making a muttrc It looks cool Questions and Comments? Ryan Curtin Configuring and Using Mutt - p. 4/21 Comparison with Pine » Goals Mutt is lighter (and presumably faster) Introduction » What is Mutt? » Why should I use mutt? Mutt supports more authentication methods » Comparison with Pine » What else is out there? Mutt has better encryption (PGP/MIME/OpenPGP) Basic Usage Making a muttrc Mutt is still in active development (Pine stopped at 4.64; Questions and Comments? development moved to Alpine) Ryan Curtin Configuring and Using Mutt - p. -

Pipenightdreams Osgcal-Doc Mumudvb Mpg123-Alsa Tbb
pipenightdreams osgcal-doc mumudvb mpg123-alsa tbb-examples libgammu4-dbg gcc-4.1-doc snort-rules-default davical cutmp3 libevolution5.0-cil aspell-am python-gobject-doc openoffice.org-l10n-mn libc6-xen xserver-xorg trophy-data t38modem pioneers-console libnb-platform10-java libgtkglext1-ruby libboost-wave1.39-dev drgenius bfbtester libchromexvmcpro1 isdnutils-xtools ubuntuone-client openoffice.org2-math openoffice.org-l10n-lt lsb-cxx-ia32 kdeartwork-emoticons-kde4 wmpuzzle trafshow python-plplot lx-gdb link-monitor-applet libscm-dev liblog-agent-logger-perl libccrtp-doc libclass-throwable-perl kde-i18n-csb jack-jconv hamradio-menus coinor-libvol-doc msx-emulator bitbake nabi language-pack-gnome-zh libpaperg popularity-contest xracer-tools xfont-nexus opendrim-lmp-baseserver libvorbisfile-ruby liblinebreak-doc libgfcui-2.0-0c2a-dbg libblacs-mpi-dev dict-freedict-spa-eng blender-ogrexml aspell-da x11-apps openoffice.org-l10n-lv openoffice.org-l10n-nl pnmtopng libodbcinstq1 libhsqldb-java-doc libmono-addins-gui0.2-cil sg3-utils linux-backports-modules-alsa-2.6.31-19-generic yorick-yeti-gsl python-pymssql plasma-widget-cpuload mcpp gpsim-lcd cl-csv libhtml-clean-perl asterisk-dbg apt-dater-dbg libgnome-mag1-dev language-pack-gnome-yo python-crypto svn-autoreleasedeb sugar-terminal-activity mii-diag maria-doc libplexus-component-api-java-doc libhugs-hgl-bundled libchipcard-libgwenhywfar47-plugins libghc6-random-dev freefem3d ezmlm cakephp-scripts aspell-ar ara-byte not+sparc openoffice.org-l10n-nn linux-backports-modules-karmic-generic-pae -
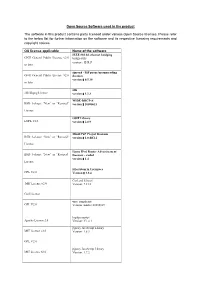
Open Source Software Used in the Product the Software in This Product Contains Parts Licensed Under Various Open Source Licenses
Open Source Software used in the product The software in this product contains parts licensed under various Open Source licenses. Please refer to the below list for further information on the software and its respective licensing requirements and copyright notices. OS license applicable Name of the software IEEE 802.1d ethernet bridging GNU General Public License v2.0 bridge-utils version:0.9.7 or later siproxd - SIP proxy/masquerading GNU General Public License v2.0 daemon version:0.5.10 or later zlib zlib/libpng License version:1.2.3 WIDE-DHCPv6 BSD 3-clause “New” or “Revised” version:20080615 License OSIP Library LGPL V2.1 version:2.0.9 MiniUPnP Project Daemon BSD 3-clause “New” or “Revised” version:1.0-RC12 License Linux IPv6 Router Advertisement BSD 3-clause “New” or “Revised” Daemon – radvd version:1.4 License Filesystem in Userspace GPL V2.0 Version:2.8.4 Curl and Libcurl MIT License v2.0 Version: 7.21.3 Curl License wpa_supplicant GPL V2.0 Version: master-20110109 log4javascript Apache License 2.0 Version: V1.4.1 jQuery JavaScript Library MIT License v2.0 Version: 1.8.3 GPL V2.0 jQuery JavaScript Library MIT License v2.0 Version: 1.7.2 GPL V2.0 Jqueryjs MIT License v2.0 Version: 1.4.4 theWall - pc_pppoe BSD 3-clause license Version: 0.2 Endian Firewall Community GPL V2.0 Version: EFW-2.3 Struts EJB LGPL V2.1 Version: 1.3 Linux Kernel GPL V2.0 version:2.6.35 Free BSD BSD 2-clause license Version: 5.0 ssltunnel BSD 2-clause license Version: 1.16.0.3 ZMailer BSD 2-clause license Version: 2.99.57 kakaxi-project trunk-20120909-svn: Apache License 2.0 Android - platform - bootable - BSD 2-clause license bootloader – legacy 2.2_r1 Android – platform – bionic BSD 2-clause license Version: 2.3_r1 Android - platform - system - core Apache License 2.0 2.3_r1 Android – platform – external – GPL V2.0 wpa_supplicant Version: 2.2_r1 You may obtain the most recent version of the source for free by downloading it from the supplier`s website http://download- c.huawei.com/download/downloadCenter?downloadId=20841&version=35510&siteCode=worldwide .