Linux Administrator's Security Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Mining of Massive Datasets
Mining of Massive Datasets Anand Rajaraman Kosmix, Inc. Jeffrey D. Ullman Stanford Univ. Copyright c 2010, 2011 Anand Rajaraman and Jeffrey D. Ullman ii Preface This book evolved from material developed over several years by Anand Raja- raman and Jeff Ullman for a one-quarter course at Stanford. The course CS345A, titled “Web Mining,” was designed as an advanced graduate course, although it has become accessible and interesting to advanced undergraduates. What the Book Is About At the highest level of description, this book is about data mining. However, it focuses on data mining of very large amounts of data, that is, data so large it does not fit in main memory. Because of the emphasis on size, many of our examples are about the Web or data derived from the Web. Further, the book takes an algorithmic point of view: data mining is about applying algorithms to data, rather than using data to “train” a machine-learning engine of some sort. The principal topics covered are: 1. Distributed file systems and map-reduce as a tool for creating parallel algorithms that succeed on very large amounts of data. 2. Similarity search, including the key techniques of minhashing and locality- sensitive hashing. 3. Data-stream processing and specialized algorithms for dealing with data that arrives so fast it must be processed immediately or lost. 4. The technology of search engines, including Google’s PageRank, link-spam detection, and the hubs-and-authorities approach. 5. Frequent-itemset mining, including association rules, market-baskets, the A-Priori Algorithm and its improvements. 6. -

Linux Administrators Security Guide LASG - 0.1.1
Linux Administrators Security Guide LASG - 0.1.1 By Kurt Seifried ([email protected]) copyright 1999, All rights reserved. Available at: https://www.seifried.org/lasg/. This document is free for most non commercial uses, the license follows the table of contents, please read it if you have any concerns. If you have any questions email [email protected]. A mailing list is available, send an email to [email protected], with "subscribe lasg-announce" in the body (no quotes) and you will be automatically added. 1 Table of contents License Preface Forward by the author Contributing What this guide is and isn't How to determine what to secure and how to secure it Safe installation of Linux Choosing your install media It ain't over 'til... General concepts, server verses workstations, etc Physical / Boot security Physical access The computer BIOS LILO The Linux kernel Upgrading and compiling the kernel Kernel versions Administrative tools Access Telnet SSH LSH REXEC NSH Slush SSL Telnet Fsh secsh Local YaST sudo Super Remote Webmin Linuxconf COAS 2 System Files /etc/passwd /etc/shadow /etc/groups /etc/gshadow /etc/login.defs /etc/shells /etc/securetty Log files and other forms of monitoring General log security sysklogd / klogd secure-syslog next generation syslog Log monitoring logcheck colorlogs WOTS swatch Kernel logging auditd Shell logging bash Shadow passwords Cracking passwords John the ripper Crack Saltine cracker VCU PAM Software Management RPM dpkg tarballs / tgz Checking file integrity RPM dpkg PGP MD5 Automatic -

Iclab: a Global, Longitudinal Internet Censorship Measurement Platform
ICLab: A Global, Longitudinal Internet Censorship Measurement Platform Arian Akhavan Niaki∗y Shinyoung Cho∗yz Zachary Weinberg∗x Nguyen Phong Hoangz Abbas Razaghpanahz Nicolas Christinx Phillipa Gilly yUniversity of Massachusetts, Amherst zStony Brook University xCarnegie Mellon University {arian, shicho, phillipa}@cs.umass.edu {shicho, nghoang, arazaghpanah}@cs.stonybrook.edu {zackw, nicolasc}@cmu.edu Abstract—Researchers have studied Internet censorship for remains elusive. We highlight three key challenges that must nearly as long as attempts to censor contents have taken place. be addressed to make progress in this space: Most studies have however been limited to a short period of time and/or a few countries; the few exceptions have traded off detail Challenge 1: Access to Vantage Points. With few ex- for breadth of coverage. Collecting enough data for a compre- ceptions,1 measuring Internet censorship requires access to hensive, global, longitudinal perspective remains challenging. “vantage point” hosts within the region of interest. In this work, we present ICLab, an Internet measurement The simplest way to obtain vantage points is to recruit platform specialized for censorship research. It achieves a new balance between breadth of coverage and detail of measurements, volunteers [37], [43], [73], [80]. Volunteers can run software by using commercial VPNs as vantage points distributed around that performs arbitrary network measurements from each the world. ICLab has been operated continuously since late vantage point, but recruiting more than a few volunteers per 2016. It can currently detect DNS manipulation and TCP packet country and retaining them for long periods is difficult. Further, injection, and overt “block pages” however they are delivered. -

Introduction to Linux and Using CSC Environment Efficiently
Introduction to Linux and Using CSC Environment Efficiently Introduction UNIX A slow-pace course for absolute UNIX beginners February 10th, 2014 Lecturers (in alphabetical order): Tomasz Malkiewicz Atte Sillanpää Thomas Zwinger Program 09:45 – 10:00 Morning coffee + registration 10:00 – 10:15 Introduction to the course (whereabouts, etc.) 10:15 – 10:45 What is UNIX/Linux: history and basic concepts (multi-user, multi-tasking, multi-processor) 10:45 – 11:15 Linux on my own computer: native installation, dual-boot, virtual appliances 11:15 – 11:45 A first glimpse of the shell: simple navigation, listing, creating/removing files and directories 11:45 – 12:45 lunch 12:45 – 13:00 Text editors: vi and emacs 13:00 – 13:45 File permissions: concepts of users and groups, changing permissions/groups 13:45 – 14:15 Job management: scripts and executables, suspending/killing jobs, monitoring, foreground/background 14:15 – 14:30 coffee break 14:30 – 15:00 Setup of your system: environment variables, aliases, rc-files 15:00 – 15:30 A second look at the shell: finding files and contents, remote operations, text-utils, changing shells 15:30 – 17:00 Troubleshooter: Interactive session to deal with open questions and specific problems Program All topics are presented with interactive demonstrations Additionally, exercises to each of the sections will be provided The Troubleshooter section is meant for personal interaction and is (with a time- limit to 17:00) kept in an open end style Practicalities Keep the name tag visible Lunch is served in the same building. -

Analysis and Evaluation of Email Security
Al-Azhar University – Gaza Deanship of Postgraduate Studies Faculty of Engineering & Information Technology Master of Computing and Information System Analysis and Evaluation of Email Security Prepared by Mohammed Ahmed Maher Mahmoud Al-Nakhal Supervised by Dr. Ihab Salah Al-Dein Zaqout A Thesis submitted in partial fulfillment of the requirements for the degree of Master of Computing and Information Systems 2018 جامعةةةةةةةةةة ةةةةةةةةةة – غةةةةةةةةةة عمةةةةةةةةةاا لعل اةةةةةةةةةا لع ةةةةةةةةةا ك هلنعا وتكنولوج ا ملع وما ماجسةةةاحل بواةةةم وعلةةةت ملع ومةةةا حتليل وتقييم أمن الربيد اﻹلكرتوني إعداد الباحث حممد أمحد ماهر حممود النخال إشراف الدكتور/ إيهاب صﻻح الدين زقوت قدمت هذه الرسالة استكماﻻً لمتطلبات الحصول على درجة الماجستير في الحوسبة ونظم المعلومات من كلية الهندسة وتكنولوجيا المعلومات – جامعة اﻷزهر – غزة 2018 قَالُوا سُبْحَانَكَ لَا عِلْمَ لَنَا إِلَّا مَا عَلَّمْتَنَا إِنَّكَ أَنْتَ الْعَلِيمُ الْحَكِيمُ صدق اهلل العظيم سورة البقرة ) آية 32( i Dedication To my parents who take my hands and walk me among the ports of life, what is clear in their paths. Thanks to them and hope from Almighty Allah to keep them for me and extend in their age ... To my loving, forgiving and supportive wife who created the atmosphere for me to complete this work. To my brother Mahmoud and sisters Dema and Dania …... To the martyrs of Palestine who fought for the sake of Almighty Allah. ii Acknowledgment The prophet Mohammad (Peace Be Upon Him) says, “He who does not thank people, does not thank Allah “. Completing and issuing such dissertation would not have been possible without the help and support of the people who ably guided this dissertation through the whole process. -

Redesigning Src2pkg, a Linux Package Creation Toolkit
Redesigning src2pkg, a Linux package creation toolkit Timothy Goya December 4, 2009 Senior Project COMPUTER SCIENCE DEPARTMENT California Polytechnic State University San Luis Obispo 2009 1 Contents 1 Introduction 3 2 Background 4 2.1 GNU Coding Standards . 4 2.2 CheckInstall . 4 2.3 src2pkg 1.x . 4 3 Description 5 3.1 Flexibility and coupling . 5 3.2 A simple example script . 5 3.3 Other interesting functions . 6 3.4 Modules . 6 3.4.1 Build systems . 6 3.4.2 Sandboxing methods . 7 3.4.3 Package formats . 7 4 Evaluation 7 5 Really Cool Bash Features 8 5.1 /dev/tcp . 8 5.2 Manipulating Binary . 9 5.3 Localization . 9 6 Conclusions 9 2 Acknowledgments Many thanks to Dr. Phillip Nico for his saintly patience and understanding during his time as my senior project advisor. Special thanks to Gilbert Ashley, the author of src2pkg, for his approval and support throughout this redesign. Thanks to Piete Sartain for adminstrating the src2pkg wiki and Drew Ames for the writing much of the great documentation on the src2pkg wiki. I would also like to thank Dr. Alexander Dekhtyar for acting as my advisor for my rst senior project idea. Abstract Package managers ease installation and removal of applications. How- ever, as the name indicates, in order for a package manager to be useful, they need packages created from upstream sources to manage. This is the purpose of src2pkg, a toolkit written in Bash shell script which automates many package creation tasks. src2pkg, however, suers from major de- sign aws that cripple its ability to package some exotic upstream sources. -

Latexsample-Thesis
INTEGRAL ESTIMATION IN QUANTUM PHYSICS by Jane Doe A dissertation submitted to the faculty of The University of Utah in partial fulfillment of the requirements for the degree of Doctor of Philosophy Department of Mathematics The University of Utah May 2016 Copyright c Jane Doe 2016 All Rights Reserved The University of Utah Graduate School STATEMENT OF DISSERTATION APPROVAL The dissertation of Jane Doe has been approved by the following supervisory committee members: Cornelius L´anczos , Chair(s) 17 Feb 2016 Date Approved Hans Bethe , Member 17 Feb 2016 Date Approved Niels Bohr , Member 17 Feb 2016 Date Approved Max Born , Member 17 Feb 2016 Date Approved Paul A. M. Dirac , Member 17 Feb 2016 Date Approved by Petrus Marcus Aurelius Featherstone-Hough , Chair/Dean of the Department/College/School of Mathematics and by Alice B. Toklas , Dean of The Graduate School. ABSTRACT Blah blah blah blah blah blah blah blah blah blah blah blah blah blah blah. Blah blah blah blah blah blah blah blah blah blah blah blah blah blah blah. Blah blah blah blah blah blah blah blah blah blah blah blah blah blah blah. Blah blah blah blah blah blah blah blah blah blah blah blah blah blah blah. Blah blah blah blah blah blah blah blah blah blah blah blah blah blah blah. Blah blah blah blah blah blah blah blah blah blah blah blah blah blah blah. Blah blah blah blah blah blah blah blah blah blah blah blah blah blah blah. Blah blah blah blah blah blah blah blah blah blah blah blah blah blah blah. -

Checkinstall
LinuxFocus article number 360 http://linuxfocus.org CheckInstall by Mario M. Knopf (homepage) About the author: Mario enjoys working with Linux, networks Abstract: and security related topics. Checkinstall is utility to automatically build RPM/Debian or Slackware packages from tar.gz source pages. This makes it possible to do a "clean" installation and de−installation of almost any source code tar.gz package. Translated to English _________________ _________________ _________________ by: Mario M. Knopf (homepage) Introduction It often happens that the program which one certainly would like to test, is only available as tar.gz source code (no rpm or Debian package available). In such a case, you download the source package, unpack it and compile it manually. So far, so good. However, what happens if you like to delete the program? The Makefile contains only in very few cases an appropriate routine to uninstall the program. Of course there is the possibility of installing the program into a temporary directory and write down all of the files which were created or modified by the installation for a later removing. But this procedure is painful and very extensive, if programs are frequently compiled from the sources. The tool CheckInstall [1] written by Felipe Eduardo Sánchez Díaz Durán solves this problem. As a rule, you compile and install a GNU Autoconf compliant program under use of the widely known command sequence ./configure && make && make install. The configure shell script attempts to guess correct values for various system−dependent variables, which are used later during the compilation. It checks whether all requirements for compilation are fulfilled and uses those values to create a Makefile in each directory of the package. -

Pipenightdreams Osgcal-Doc Mumudvb Mpg123-Alsa Tbb
pipenightdreams osgcal-doc mumudvb mpg123-alsa tbb-examples libgammu4-dbg gcc-4.1-doc snort-rules-default davical cutmp3 libevolution5.0-cil aspell-am python-gobject-doc openoffice.org-l10n-mn libc6-xen xserver-xorg trophy-data t38modem pioneers-console libnb-platform10-java libgtkglext1-ruby libboost-wave1.39-dev drgenius bfbtester libchromexvmcpro1 isdnutils-xtools ubuntuone-client openoffice.org2-math openoffice.org-l10n-lt lsb-cxx-ia32 kdeartwork-emoticons-kde4 wmpuzzle trafshow python-plplot lx-gdb link-monitor-applet libscm-dev liblog-agent-logger-perl libccrtp-doc libclass-throwable-perl kde-i18n-csb jack-jconv hamradio-menus coinor-libvol-doc msx-emulator bitbake nabi language-pack-gnome-zh libpaperg popularity-contest xracer-tools xfont-nexus opendrim-lmp-baseserver libvorbisfile-ruby liblinebreak-doc libgfcui-2.0-0c2a-dbg libblacs-mpi-dev dict-freedict-spa-eng blender-ogrexml aspell-da x11-apps openoffice.org-l10n-lv openoffice.org-l10n-nl pnmtopng libodbcinstq1 libhsqldb-java-doc libmono-addins-gui0.2-cil sg3-utils linux-backports-modules-alsa-2.6.31-19-generic yorick-yeti-gsl python-pymssql plasma-widget-cpuload mcpp gpsim-lcd cl-csv libhtml-clean-perl asterisk-dbg apt-dater-dbg libgnome-mag1-dev language-pack-gnome-yo python-crypto svn-autoreleasedeb sugar-terminal-activity mii-diag maria-doc libplexus-component-api-java-doc libhugs-hgl-bundled libchipcard-libgwenhywfar47-plugins libghc6-random-dev freefem3d ezmlm cakephp-scripts aspell-ar ara-byte not+sparc openoffice.org-l10n-nn linux-backports-modules-karmic-generic-pae -
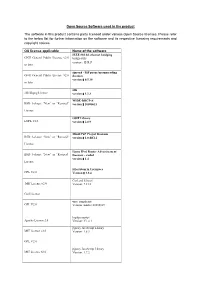
Open Source Software Used in the Product the Software in This Product Contains Parts Licensed Under Various Open Source Licenses
Open Source Software used in the product The software in this product contains parts licensed under various Open Source licenses. Please refer to the below list for further information on the software and its respective licensing requirements and copyright notices. OS license applicable Name of the software IEEE 802.1d ethernet bridging GNU General Public License v2.0 bridge-utils version:0.9.7 or later siproxd - SIP proxy/masquerading GNU General Public License v2.0 daemon version:0.5.10 or later zlib zlib/libpng License version:1.2.3 WIDE-DHCPv6 BSD 3-clause “New” or “Revised” version:20080615 License OSIP Library LGPL V2.1 version:2.0.9 MiniUPnP Project Daemon BSD 3-clause “New” or “Revised” version:1.0-RC12 License Linux IPv6 Router Advertisement BSD 3-clause “New” or “Revised” Daemon – radvd version:1.4 License Filesystem in Userspace GPL V2.0 Version:2.8.4 Curl and Libcurl MIT License v2.0 Version: 7.21.3 Curl License wpa_supplicant GPL V2.0 Version: master-20110109 log4javascript Apache License 2.0 Version: V1.4.1 jQuery JavaScript Library MIT License v2.0 Version: 1.8.3 GPL V2.0 jQuery JavaScript Library MIT License v2.0 Version: 1.7.2 GPL V2.0 Jqueryjs MIT License v2.0 Version: 1.4.4 theWall - pc_pppoe BSD 3-clause license Version: 0.2 Endian Firewall Community GPL V2.0 Version: EFW-2.3 Struts EJB LGPL V2.1 Version: 1.3 Linux Kernel GPL V2.0 version:2.6.35 Free BSD BSD 2-clause license Version: 5.0 ssltunnel BSD 2-clause license Version: 1.16.0.3 ZMailer BSD 2-clause license Version: 2.99.57 kakaxi-project trunk-20120909-svn: Apache License 2.0 Android - platform - bootable - BSD 2-clause license bootloader – legacy 2.2_r1 Android – platform – bionic BSD 2-clause license Version: 2.3_r1 Android - platform - system - core Apache License 2.0 2.3_r1 Android – platform – external – GPL V2.0 wpa_supplicant Version: 2.2_r1 You may obtain the most recent version of the source for free by downloading it from the supplier`s website http://download- c.huawei.com/download/downloadCenter?downloadId=20841&version=35510&siteCode=worldwide . -

Linux Administrators Security Guide LASG - 0.1.0
Linux Administrators Security Guide LASG - 0.1.0 By Kurt Seifried ([email protected]) copyright 1999, All rights reserved. Available at: https://www.seifried.org/lasg/ This document is free for most non commercial uses, the license follows the table of contents, please read it if you have any concerns. If you have any questions email [email protected]. If you want to receive announcements of new versions of the LASG please send a blank email with the subject line “subscribe” (no quotes) to [email protected]. 1 Table of contents License Preface Forward by the author Contributing What this guide is and isn't How to determine what to secure and how to secure it Safe installation of Linux Choosing your install media It ain't over 'til... General concepts, server verses workstations, etc Physical / Boot security Physical access The computer BIOS LILO The Linux kernel Upgrading and compiling the kernel Kernel versions Administrative tools Access Telnet SSH LSH REXEC NSH Slush SSL Telnet Fsh secsh Local YaST sudo Super Remote Webmin Linuxconf COAS 2 System Files /etc/passwd /etc/shadow /etc/groups /etc/gshadow /etc/login.defs /etc/shells /etc/securetty Log files and other forms of monitoring sysklogd / klogd secure-syslog next generation syslog Log monitoring logcheck colorlogs WOTS swatch Kernel logging auditd Shell logging bash Shadow passwords Cracking passwords Jack the ripper Crack Saltine cracker VCU PAM Software Management RPM dpkg tarballs / tgz Checking file integrity RPM dpkg PGP MD5 Automatic updates RPM AutoRPM -

Name Synopsis Description
SMTPSERVER(8zm) SMTPSERVER(8zm) NAME smtpserver − zmailer SMTP server SYNOPSIS smtpserver [-46aBhigntVvw][-p port][-l SYSLOG][-l logfile][-s[ftveRSDh]] [-s strict] [-s sloppy][-I pidfile][-L maxloadaver][-M SMTPmaxsize][-P postoffice][-R router] [-C cfgfile][-Z zenvfile][-T '[1.2.3.4]'] DESCRIPTION This program implements the server side of the SMTP protocol as defined in RFC-2821, and knows about the common extensions to the protocol expected by sendmail and BSMTP clients. By default the program will kill the previous smtpserver (8zm) daemon, if any, then detach and lis- ten for SMTP connections. Incoming messages will be submitted for processing using the zmailer (3zm) interface to ZMailer. Non-trivial address checking is done asynchronously, although this behaviour can be changed by a command line option if you cannot afford to transfer data just to bounce it back. Complex routing analysis checking is done by executing the router (8zm) program in interactive mode, and executing a well-known shell function with well-known parameters for each request. Traditionally this task has needed starting router process (and some other processes) underneath each incoming SMTP session, which is not a very lightweight thing. Current version has prestarted farm of auxiliary server processes that can be used to handle com- plex things, and they can amortize e.g. router startup cost among lots of actual users making the use of routing in reception time very cheap in terms of resources. Presently system starts a master process that starts a set of auxiliary processes, and keeps inter- nal nameless rendezvous sockets for each of them.