Open Source Software Notice
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Linux Platform 3.0.5
Open Source Used In Linux Platform 3.0.5 Cisco Systems, Inc. www.cisco.com Cisco has more than 200 offices worldwide. Addresses, phone numbers, and fax numbers are listed on the Cisco website at www.cisco.com/go/offices. Text Part Number: 78EE117C99-140544257 Open Source Used In Linux Platform 3.0.5 1 This document contains licenses and notices for open source software used in this product. With respect to the free/open source software listed in this document, if you have any questions or wish to receive a copy of any source code to which you may be entitled under the applicable free/open source license(s) (such as the GNU Lesser/General Public License), please contact us at [email protected]. In your requests please include the following reference number 78EE117C99-140544257 The product also uses the Linux operating system, Centos Full 6.8. Information on this distribution is available at http://vault.centos.org/6.8/os/Source/SPackages/. The full source code for this distribution, including copyright and license information, is available on request from [email protected]. Mention that you would like the Linux distribution source archive, and quote the following reference number for this distribution: 132404382-140544257. Contents 1.1 acl - libraries 2.2.49 :6.el6 1.1.1 Available under license 1.2 atop 1.27 :2.el6 1.2.1 Available under license 1.3 attr_libattr 2.4.44 :7.el6 1.3.1 Available under license 1.4 avahi 0.6.25 :15.el6_8.1 1.4.1 Available under license 1.5 bind 9.8.2 :0.47.rc1.el6_8.3 -

Linux Administrators Security Guide LASG - 0.1.1
Linux Administrators Security Guide LASG - 0.1.1 By Kurt Seifried ([email protected]) copyright 1999, All rights reserved. Available at: https://www.seifried.org/lasg/. This document is free for most non commercial uses, the license follows the table of contents, please read it if you have any concerns. If you have any questions email [email protected]. A mailing list is available, send an email to [email protected], with "subscribe lasg-announce" in the body (no quotes) and you will be automatically added. 1 Table of contents License Preface Forward by the author Contributing What this guide is and isn't How to determine what to secure and how to secure it Safe installation of Linux Choosing your install media It ain't over 'til... General concepts, server verses workstations, etc Physical / Boot security Physical access The computer BIOS LILO The Linux kernel Upgrading and compiling the kernel Kernel versions Administrative tools Access Telnet SSH LSH REXEC NSH Slush SSL Telnet Fsh secsh Local YaST sudo Super Remote Webmin Linuxconf COAS 2 System Files /etc/passwd /etc/shadow /etc/groups /etc/gshadow /etc/login.defs /etc/shells /etc/securetty Log files and other forms of monitoring General log security sysklogd / klogd secure-syslog next generation syslog Log monitoring logcheck colorlogs WOTS swatch Kernel logging auditd Shell logging bash Shadow passwords Cracking passwords John the ripper Crack Saltine cracker VCU PAM Software Management RPM dpkg tarballs / tgz Checking file integrity RPM dpkg PGP MD5 Automatic -

Third Party Terms for Modular Messaging 3.0 (July 2005)
Third Party Terms for Modular Messaging 3.0 (July 2005) Certain portions of the product ("Open Source Components") are licensed under open source license agreements that require Avaya to make the source code for such Open Source Components available in source code format to its licensees, or that require Avaya to disclose the license terms for such Open Source Components. If you are a licensee of this Product, and wish to receive information on how to access the source code for such Open Source Components, or the details of such licenses, you may contact Avaya at (408) 577-7666 for further information. The Open Source Components are provided “AS IS”. ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDERS OR THE CONTRIBUTORS OF THE OPEN SOURCE COMPONENTS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THE PRODUCT, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. Avaya provides a limited warranty on the Product that incorporates the Open Source Components. Refer to your customer sales agreement to establish the terms of the limited warranty. In addition, Avaya’s standard warranty language as well as information regarding support for the Product, while under warranty, is available through the following web site: http://www.avaya.com/support. -

Filesystems HOWTO Filesystems HOWTO Table of Contents Filesystems HOWTO
Filesystems HOWTO Filesystems HOWTO Table of Contents Filesystems HOWTO..........................................................................................................................................1 Martin Hinner < [email protected]>, http://martin.hinner.info............................................................1 1. Introduction..........................................................................................................................................1 2. Volumes...............................................................................................................................................1 3. DOS FAT 12/16/32, VFAT.................................................................................................................2 4. High Performance FileSystem (HPFS)................................................................................................2 5. New Technology FileSystem (NTFS).................................................................................................2 6. Extended filesystems (Ext, Ext2, Ext3)...............................................................................................2 7. Macintosh Hierarchical Filesystem − HFS..........................................................................................3 8. ISO 9660 − CD−ROM filesystem.......................................................................................................3 9. Other filesystems.................................................................................................................................3 -

State of the Art: Where We Are with the Ext3 Filesystem
State of the Art: Where we are with the Ext3 filesystem Mingming Cao, Theodore Y. Ts’o, Badari Pulavarty, Suparna Bhattacharya IBM Linux Technology Center {cmm, theotso, pbadari}@us.ibm.com, [email protected] Andreas Dilger, Alex Tomas, Cluster Filesystem Inc. [email protected], [email protected] Abstract 1 Introduction Although the ext2 filesystem[4] was not the first filesystem used by Linux and while other filesystems have attempted to lay claim to be- ing the native Linux filesystem (for example, The ext2 and ext3 filesystems on Linux R are when Frank Xia attempted to rename xiafs to used by a very large number of users. This linuxfs), nevertheless most would consider the is due to its reputation of dependability, ro- ext2/3 filesystem as most deserving of this dis- bustness, backwards and forwards compatibil- tinction. Why is this? Why have so many sys- ity, rather than that of being the state of the tem administrations and users put their trust in art in filesystem technology. Over the last few the ext2/3 filesystem? years, however, there has been a significant amount of development effort towards making There are many possible explanations, includ- ext3 an outstanding filesystem, while retaining ing the fact that the filesystem has a large and these crucial advantages. In this paper, we dis- diverse developer community. However, in cuss those features that have been accepted in our opinion, robustness (even in the face of the mainline Linux 2.6 kernel, including direc- hardware-induced corruption) and backwards tory indexing, block reservation, and online re- compatibility are among the most important sizing. -
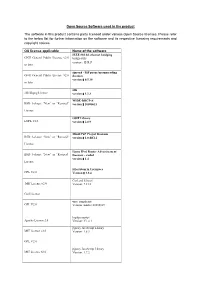
Open Source Software Used in the Product the Software in This Product Contains Parts Licensed Under Various Open Source Licenses
Open Source Software used in the product The software in this product contains parts licensed under various Open Source licenses. Please refer to the below list for further information on the software and its respective licensing requirements and copyright notices. OS license applicable Name of the software IEEE 802.1d ethernet bridging GNU General Public License v2.0 bridge-utils version:0.9.7 or later siproxd - SIP proxy/masquerading GNU General Public License v2.0 daemon version:0.5.10 or later zlib zlib/libpng License version:1.2.3 WIDE-DHCPv6 BSD 3-clause “New” or “Revised” version:20080615 License OSIP Library LGPL V2.1 version:2.0.9 MiniUPnP Project Daemon BSD 3-clause “New” or “Revised” version:1.0-RC12 License Linux IPv6 Router Advertisement BSD 3-clause “New” or “Revised” Daemon – radvd version:1.4 License Filesystem in Userspace GPL V2.0 Version:2.8.4 Curl and Libcurl MIT License v2.0 Version: 7.21.3 Curl License wpa_supplicant GPL V2.0 Version: master-20110109 log4javascript Apache License 2.0 Version: V1.4.1 jQuery JavaScript Library MIT License v2.0 Version: 1.8.3 GPL V2.0 jQuery JavaScript Library MIT License v2.0 Version: 1.7.2 GPL V2.0 Jqueryjs MIT License v2.0 Version: 1.4.4 theWall - pc_pppoe BSD 3-clause license Version: 0.2 Endian Firewall Community GPL V2.0 Version: EFW-2.3 Struts EJB LGPL V2.1 Version: 1.3 Linux Kernel GPL V2.0 version:2.6.35 Free BSD BSD 2-clause license Version: 5.0 ssltunnel BSD 2-clause license Version: 1.16.0.3 ZMailer BSD 2-clause license Version: 2.99.57 kakaxi-project trunk-20120909-svn: Apache License 2.0 Android - platform - bootable - BSD 2-clause license bootloader – legacy 2.2_r1 Android – platform – bionic BSD 2-clause license Version: 2.3_r1 Android - platform - system - core Apache License 2.0 2.3_r1 Android – platform – external – GPL V2.0 wpa_supplicant Version: 2.2_r1 You may obtain the most recent version of the source for free by downloading it from the supplier`s website http://download- c.huawei.com/download/downloadCenter?downloadId=20841&version=35510&siteCode=worldwide . -

Linux Administrators Security Guide LASG - 0.1.0
Linux Administrators Security Guide LASG - 0.1.0 By Kurt Seifried ([email protected]) copyright 1999, All rights reserved. Available at: https://www.seifried.org/lasg/ This document is free for most non commercial uses, the license follows the table of contents, please read it if you have any concerns. If you have any questions email [email protected]. If you want to receive announcements of new versions of the LASG please send a blank email with the subject line “subscribe” (no quotes) to [email protected]. 1 Table of contents License Preface Forward by the author Contributing What this guide is and isn't How to determine what to secure and how to secure it Safe installation of Linux Choosing your install media It ain't over 'til... General concepts, server verses workstations, etc Physical / Boot security Physical access The computer BIOS LILO The Linux kernel Upgrading and compiling the kernel Kernel versions Administrative tools Access Telnet SSH LSH REXEC NSH Slush SSL Telnet Fsh secsh Local YaST sudo Super Remote Webmin Linuxconf COAS 2 System Files /etc/passwd /etc/shadow /etc/groups /etc/gshadow /etc/login.defs /etc/shells /etc/securetty Log files and other forms of monitoring sysklogd / klogd secure-syslog next generation syslog Log monitoring logcheck colorlogs WOTS swatch Kernel logging auditd Shell logging bash Shadow passwords Cracking passwords Jack the ripper Crack Saltine cracker VCU PAM Software Management RPM dpkg tarballs / tgz Checking file integrity RPM dpkg PGP MD5 Automatic updates RPM AutoRPM -
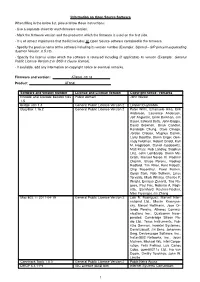
Information on Open Source Software When Filling in The
Information on Open Source Software When filling in the below list, please follow these instructions: - Use a separate sheet for each firmware version. - Mark the firmware version and the product in which the firmware is used on the first side. - It is of utmost importance that the list includes all Open Source software contained in the firmware. - Specify the precise name of the software including its version number (Example: Siproxd – SIP proxy/masquerading daemon Version: 0.5.10). - Specify the license under which the software is released including (if applicable) its version (Example: General Public License Version 2 or BSD-3 clause license). - If available, add any information on copyright notice or eventual remarks. Firmware and version: AT904L-03.18 Product: AT904L Software and version number License and License Version Copyright notice / remarks Encode and Decode base64 files Public domain John Walker 1.5 bridge-utils 1.4 General Public License Version 2 Lennert Buytenhek BusyBox 1.16.2 General Public License Version 2 Peter Willis, Emanuele Aina, Erik Andersen, Laurence Anderson, Jeff Angielski, Enrik Berkhan, Jim Bauer, Edward Betts, John Beppu, David Brownell, Brian Candler, Randolph Chung, Dave Cinege, Jordan Crouse, Magnus Damm, Larry Doolittle, Glenn Engel, Gen- nady Feldman, Robert Griebl, Karl M. Hegbloom, Daniel Jacobowitz, Matt Kraai, Rob Landley, Stephan Linz, John Lombardo, Glenn Mc- Grath, Manuel Novoa III, Vladimir Oleynik, Bruce Perens, Rodney Radford, Tim Riker, Kent Robotti, Chip Rosenthal, Pavel Roskin, Gyepi Sam, Rob Sullivan, Linus Torvalds, Mark Whitley, Charles P. Wright, Enrique Zanardi, Tito Ra- gusa, Paul Fox, Roberto A. Fogli- etta, Bernhard Reutner-Fischer, Mike Frysinger, Jie Zhang Mac 802.11 2011-04-19 General Public License Version 2 Luis R. -

Design and Implementation of the Spad Filesystem
Charles University in Prague Faculty of Mathematics and Physics DOCTORAL THESIS Mikul´aˇsPatoˇcka Design and Implementation of the Spad Filesystem Department of Software Engineering Advisor: RNDr. Filip Zavoral, Ph.D. Abstract Title: Design and Implementation of the Spad Filesystem Author: Mgr. Mikul´aˇsPatoˇcka email: [email protected]ff.cuni.cz Department: Department of Software Engineering Faculty of Mathematics and Physics Charles University in Prague, Czech Republic Advisor: RNDr. Filip Zavoral, Ph.D. email: Filip.Zavoral@mff.cuni.cz Mailing address (advisor): Dept. of Software Engineering Charles University in Prague Malostransk´en´am. 25 118 00 Prague, Czech Republic WWW: http://artax.karlin.mff.cuni.cz/~mikulas/spadfs/ Abstract: This thesis describes design and implementation of the Spad filesystem. I present my novel method for maintaining filesystem consistency — crash counts. I describe architecture of other filesystems and present my own de- sign decisions in directory management, file allocation information, free space management, block allocation strategy and filesystem checking algorithm. I experimentally evaluate performance of the filesystem. I evaluate performance of the same filesystem on two different operating systems, enabling the reader to make a conclusion on how much the performance of various tasks is affected by operating system and how much by physical layout of data on disk. Keywords: filesystem, operating system, crash counts, extendible hashing, SpadFS Acknowledgments I would like to thank my advisor Filip Zavoral for supporting my work and for reading and making comments on this thesis. I would also like to thank to colleague Leo Galamboˇsfor testing my filesystem on his search engine with 1TB RAID array, which led to fixing some bugs and improving performance. -

Name Synopsis Description
SMTPSERVER(8zm) SMTPSERVER(8zm) NAME smtpserver − zmailer SMTP server SYNOPSIS smtpserver [-46aBhigntVvw][-p port][-l SYSLOG][-l logfile][-s[ftveRSDh]] [-s strict] [-s sloppy][-I pidfile][-L maxloadaver][-M SMTPmaxsize][-P postoffice][-R router] [-C cfgfile][-Z zenvfile][-T '[1.2.3.4]'] DESCRIPTION This program implements the server side of the SMTP protocol as defined in RFC-2821, and knows about the common extensions to the protocol expected by sendmail and BSMTP clients. By default the program will kill the previous smtpserver (8zm) daemon, if any, then detach and lis- ten for SMTP connections. Incoming messages will be submitted for processing using the zmailer (3zm) interface to ZMailer. Non-trivial address checking is done asynchronously, although this behaviour can be changed by a command line option if you cannot afford to transfer data just to bounce it back. Complex routing analysis checking is done by executing the router (8zm) program in interactive mode, and executing a well-known shell function with well-known parameters for each request. Traditionally this task has needed starting router process (and some other processes) underneath each incoming SMTP session, which is not a very lightweight thing. Current version has prestarted farm of auxiliary server processes that can be used to handle com- plex things, and they can amortize e.g. router startup cost among lots of actual users making the use of routing in reception time very cheap in terms of resources. Presently system starts a master process that starts a set of auxiliary processes, and keeps inter- nal nameless rendezvous sockets for each of them. -

LINUX: Rute User's Tutorial and Exposition
LINUX: Rute User’s Tutorial and Exposition Paul Sheer August 14, 2001 Pages up to and including this page are not included by Prentice Hall. 2 “The reason we don’t sell billions and billions of Guides,” continued Harl, after wiping his mouth, “is the expense. What we do is we sell one Guide billions and billions of times. We exploit the multidimensional nature of the Universe to cut down on manufacturing costs. And we don’t sell to penniless hitchhikers. What a stupid notion that was! Find the one section of the market that, more or less by definition, doesn’t have any money, and try to sell to it. No. We sell to the affluent business traveler and his vacationing wife in a billion, billion different futures. This is the most radical, dynamic and thrusting business venture in the entire multidimensional infinity of space-time-probability ever.” ... Ford was completely at a loss for what to do next. “Look,” he said in a stern voice. But he wasn’t certain how far saying things like “Look” in a stern voice was necessarily going to get him, and time was not on his side. What the hell, he thought, you’re only young once, and threw himself out of the window. That would at least keep the element of surprise on his side. ... In a spirit of scientific inquiry he hurled himself out of the window again. Douglas Adams Mostly Harmless Strangely, the thing that least intrigued me was how they’d managed to get it all done. I suppose I sort of knew. -

The Qmail Handbook by Dave Sill ISBN:1893115402 Apress 2002 (492 Pages)
< Free Open Study > The qmail Handbook by Dave Sill ISBN:1893115402 Apress 2002 (492 pages) This guide begins with a discussion of qmail s history, architecture and features, and then goes into a thorough investigation of the installation and configuration process. Table of Contents The qmail Handbook Introduction Ch apt - Introducing qmail er 1 Ch apt - Installing qmail er 2 Ch apt - Configuring qmail: The Basics er 3 Ch apt - Using qmail er 4 Ch apt - Managing qmail er 5 Ch apt - Troubleshooting qmail er 6 Ch apt - Configuring qmail: Advanced Options er 7 Ch apt - Controlling Junk Mail er 8 Ch apt - Managing Mailing Lists er 9 Ch apt - Serving Mailboxes er 10 Ch apt - Hosting Virtual Domain and Users er 11 Ch apt - Understanding Advanced Topics er 12 Ap pe ndi - How qmail Works x A Ap pe ndi - Related Packages x B Ap pe ndi - How Internet Mail Works x C Ap pe ndi - qmail Features x D Ap pe - Error Messages ndi x E Ap pe - Gotchas ndi x F Index List of Figures List of Tables List of Listings < Free Open Study > < Free Open Study > Back Cover • Provides thorough instruction for installing, configuring, and optimizing qmail • Includes coverage of secure networking, troubleshooting issues, and mailing list administration • Covers what system administrators want to know by concentrating on qmail issues relevant to daily operation • Includes instructions on how to filter spam before it reaches the client The qmail Handbook will guide system and mail administrators of all skill levels through installing, configuring, and maintaining the qmail server.