Pico in the Wild: Replacing Passwords, One Site at a Time
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Lösenordshantering
LÖSENORDSHANTERING www.2secure.se Lösenordshantering Våra liv utspelar sig numera i stor utsträckning online. Vi handlar kläder, böcker och prylar, streamar filmer och musik, skickar e-post, delar bilder och meddelanden i sociala medier, betalar räkningar, ansöker om föräldrapenning, och mycket mer. För allt detta finns onlinetjänster i någon form, och för alla dessa tjänster behöver vi kunna identifiera oss. För att identifiera oss på en webbsida behöver vi vanligtvis ange ett användarnamn och ett lösenord. I vissa fall har vi en fysisk enhet (t ex en mobiltelefon eller ett bankkort) som kräver en PIN-kod. I mobilen har vi ett BankID där vi måste mata in en verifieringskod. Och så vidare. Hur många koder, lösenord, säkerhetsfrågor och andra inloggningsuppgifter har du? Några exempel som du kanske känner igen: Användarkonton och lösenord AppleID och iCloud Aktiedepå Gmail/Google Apps Spotify Hotmail Netflix Facebook Mataffären/Matkassen Twitter Flygbolag Instagram Taxibolag Snapchat Bokhandel Internetbanken Kläder och skor Försäkringskassan Apoteket Hem-/bil-/sjuk- Online-dating /olycksfallsförsäkringen Spel och dobbel Pensionsbolag Routern till hemmanätverket Livsförsäkring Koder Mobiltelefon - lösenkod till enhet, PIN och PUK till SIM-kort Surfplatta - lösenkod till enhet, eventuell PIN och PUK till SIM-kort Kod till hemlarmet WiFi-lösenordet hemma Bank- och kreditkort - PIN, CVV-kod, SecureCode/3DSecure för online BankID Och då har vi inte ens pratat om alla användarkonton, lösenord och koder på jobbet. VPN, intranät, HR-portalen, CRM-systemet, andra affärssystem... Information Vi har numera dussintals olika konton för tjänsterna vi använder för allehanda syften. "Nyckeln" till varje tjänst är ett användarnamn och ett lösenord. Redan här behöver vi alltså hålla reda på väldigt känslig information. -

Analyse D'un Logiciel De Gestion Des Mots De Passe
Analyse d’un logiciel de gestion des mots de passe Version TRIQUET Guillaume Création 06/01/2015 TRIQUET Guillaume MàJ part.3, Ajout part.4 07/01/2015 TRIQUET Guillaume MàJ part.3, Ajout part.5 08/01/2015 TRIQUET Guillaume MAJ part.4, Ajout Annexe 2 12/01/2015 TRIQUET Guillaume Conclusion 19/02/2015 TRIQUET Guillaume Printed 20/04/2015 Page 1 of 30 IT Service e-doceo © Confidential Sommaire 1. Introduction ............................................................................................................... 4 2. Objectifs .................................................................................................................... 4 3. Analyse des différentes solutions .............................................................................. 5 Critères ......................................................................................................................... 5 Analyse ........................................................................................................................ 5 1. Keepass ............................................................................................................. 5 2. Enpass Password Manager : .............................................................................. 5 3. Lastpass : ........................................................................................................... 6 4. Dashlane : .......................................................................................................... 6 5. 1password : ....................................................................................................... -
Ratgeber Zum Datenschutz Umgang Mit Passwörtern
Umgang mit Passwörtern Ratgeber zum Datenschutz Umgang mit Passwörtern Ratgeber zum Datenschutz Herausgeberin: Berliner Beauftragte für Datenschutz und Informationsfreiheit Friedrichstr. 219 Besuchereingang: Puttkamerstr. 16-18 10969 Berlin Telefon: 030 13889-0 Telefax: 030 2155050 E-Mail: [email protected] Gestaltung: april agentur GbR Druck: ARNOLD group. Stand: Juni 2020 Einleitung Um die Vertraulichkeit, Integrität und Authentizität per- sonenbezogener Daten bei der Nutzung von (Online-) Diensten gewährleisten zu können, muss die Identität der Nutzenden überprüft werden. Diese Identifizierung und Authentifizierung geschieht in der Regel durch die Eingabe einer Kombination aus persönlicher Kennung (Benutzer- name) und geheimem Passwort. Wer Kennung und Pass- wort kennt, kann sich authentifizieren. Bei Verfahren mit normalem Schutzbedarf kann eine sol- che Authentifizierung derzeit gerade noch als hinreichend angesehen werden. Von normalem Schutzbedarf ist dann auszugehen, wenn weder große Datenmengen noch sen- sible oder sensitive Daten verarbeitet werden. Um sensiti- ve Daten handelt es sich, wenn sie nach der Datenschutz- Grundverordnung zu besonderen Kategorien mit erhöhtem Schutzbedarf zählen, also etwa Gesundheitsdaten oder Daten über Herkunft, Religion oder sexuelle Orientierung der Betroffenen. 1 Sobald Anwendungen und Dienste Zugriff auf sensible, sensitive oder eine große Anzahl von personenbezogenen Daten ermöglichen, besteht ein erhöhter Schutzbedarf, der eine stärkere Absicherung der Daten mit einem oder meh- reren weiteren Faktoren erforderlich macht. Möglichkei- ten für eine solche Mehrfaktor-Authentifizierung sind z. B.: • Abfragen über den Besitz physischer Geräte, die mit dem Dienst verknüpft sind (Hardware-Token, der zeitabhängig eine TAN ausgibt oder über den USB- Port mit dem Dienst kommuniziert, Chipkarte, SMS- TAN, mTAN) oder • Abgleich von biometrischen Daten (also von Körper- merkmalen, etwa durch einen Iris-Scan, Fingerab- druck oder Gesichtserkennung). -

A Security Analysis of Autofill on Ios and Android
The Emperor’s New Autofill Framework: A Security Analysis of Autofill on iOS and Android Sean Oesch, Anuj Gautam, Scott Ruoti The University of Tennessee [email protected], [email protected], [email protected] Abstract—Password managers help users more effectively (P3) the filled credential will only be accessible to the manage their passwords, encouraging them to adopt stronger mapped app or web domain. [23]. passwords across their many accounts. In contrast to desktop On desktop environments, password managers are primarily systems where password managers receive no system-level support, mobile operating systems provide autofill frameworks implemented as ad-hoc browser extensions—i.e., the extension that are designed to integrate with password managers to individually implements all aspects of the autofill process provide secure and usable autofill for browsers and other apps without support from OS or browser autofill frameworks. installed on mobile devices. In this paper, we conduct the first While some desktop password managers correctly achieve P1 holistic security evaluation of such frameworks on iOS and and P2 [19], many have incorrect implementations that allow Android, examining whether they achieve substantive benefits over the ad-hoc desktop environment or become a problematic attackers to steal or phish users’ credentials [14], [22], [23], single point of failure. Our results find that while the [19], and none can fully implement P3 due to technical frameworks address several common issues (e.g., requiring user limitations of browser extension APIs [23], [19]. interaction before autofill), they also enforce insecure behavior In contrast to the situation on desktop, mobile operating and fail to provide the password managers implemented using systems provide system-wide autofill frameworks that attempt the frameworks with sufficient information to override this incorrect behavior. -
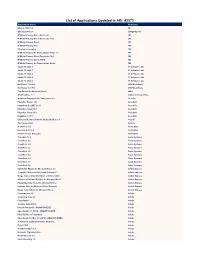
List of Applications Updated in ARL #2573
List of Applications Updated in ARL #2573 Application Name Publisher BIOS to UEFI 1.4 1E SyncBackPro 9.3 2BrightSparks M*Modal Fluency Direct Connector 3M M*Modal Fluency Direct Connector 7.85 3M M*Modal Fluency Direct 3M M*Modal Fluency Flex 3M Fluency for Imaging 3M M*Modal Fluency for Transcription Editor 7.6 3M M*Modal Fluency Direct Connector 10.0 3M M*Modal Fluency Direct CAPD 3M M*Modal Fluency for Transcription Editor 3M Studio 3T 2020.5 3T Software Labs Studio 3T 2020.7 3T Software Labs Studio 3T 2020.2 3T Software Labs Studio 3T 2020.8 3T Software Labs Studio 3T 2020.3 3T Software Labs MailRaider 3.69 Pro 45RPM software MailRaider 3.67 Pro 45RPM software Text Toolkit for Microsoft Excel 4Bits ASAP Utilities 7.7 A Must in Every Office Graphical Development Environment 3.2 Ab Initio PrizmDoc Server 13.8 AccuSoft ImageGear for .NET 24.11 AccuSoft PrizmDoc Client 13.8 AccuSoft PrizmDoc Client 13.9 AccuSoft ImagXpress 13.5 AccuSoft Universal Restore Bootable Media Builder 11.5 Acronis True Image 2020 Acronis ActivePerl 5.12 ActiveState Komodo Edit 12.0 ActiveState ActivePerl 5.26 Enterprise ActiveState TransMac 12.6 Acute Systems CrossFont 6.5 Acute Systems CrossFont 6.6 Acute Systems CrossFont 6.2 Acute Systems CrossFont 5.5 Acute Systems CrossFont 5.6 Acute Systems CrossFont 6.3 Acute Systems CrossFont 5.7 Acute Systems CrossFont 6.0 Acute Systems Split Table Wizard for Microsoft Excel 2.3 Add-in Express Template Phrases for Microsoft Outlook 4.7 Add-in Express Merge Tables Wizard for Microsoft Excel 2018 Add-in Express Advanced -
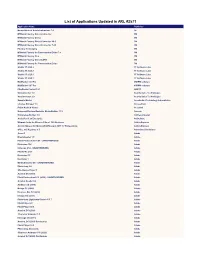
List of Applications Updated in ARL #2571
List of Applications Updated in ARL #2571 Application Name Publisher Nomad Branch Admin Extensions 7.0 1E M*Modal Fluency Direct Connector 3M M*Modal Fluency Direct 3M M*Modal Fluency Direct Connector 10.0 3M M*Modal Fluency Direct Connector 7.85 3M Fluency for Imaging 3M M*Modal Fluency for Transcription Editor 7.6 3M M*Modal Fluency Flex 3M M*Modal Fluency Direct CAPD 3M M*Modal Fluency for Transcription Editor 3M Studio 3T 2020.2 3T Software Labs Studio 3T 2020.8 3T Software Labs Studio 3T 2020.3 3T Software Labs Studio 3T 2020.7 3T Software Labs MailRaider 3.69 Pro 45RPM software MailRaider 3.67 Pro 45RPM software FineReader Server 14.1 ABBYY VoxConverter 3.0 Acarda Sales Technologies VoxConverter 2.0 Acarda Sales Technologies Sample Master Accelerated Technology Laboratories License Manager 3.5 AccessData Prizm ActiveX Viewer AccuSoft Universal Restore Bootable Media Builder 11.5 Acronis Knowledge Builder 4.0 ActiveCampaign ActivePerl 5.26 Enterprise ActiveState Ultimate Suite for Microsoft Excel 18.5 Business Add-in Express Add-in Express for Microsoft Office and .NET 7.7 Professional Add-in Express Office 365 Reporter 3.5 AdminDroid Solutions Scout 1 Adobe Dreamweaver 1.0 Adobe Flash Professional CS6 - UNAUTHORIZED Adobe Illustrator CS6 Adobe InDesign CS6 - UNAUTHORIZED Adobe Fireworks CS6 Adobe Illustrator CC Adobe Illustrator 1 Adobe Media Encoder CC - UNAUTHORIZED Adobe Photoshop 1.0 Adobe Shockwave Player 1 Adobe Acrobat DC (2015) Adobe Flash Professional CC (2015) - UNAUTHORIZED Adobe Acrobat Reader DC Adobe Audition CC (2018) -

The Case of Interaction Problems Between Password Managers and Websites
They Would do Better if They Worked Together: The Case of Interaction Problems Between Password Managers and Websites Nicolas HuamanC ∗ Sabrina Amft∗ Marten OltroggeC Yasemin Acary ∗ Sascha FahlC ∗ CCISPA Helmholtz Center for Information Security ∗Leibniz University Hannover yMax Planck Institute for Security and Privacy Abstract—Password managers are tools to support users with previous research on PWMs mostly focuses on PWM security the secure generation and storage of credentials and logins issues and usability and adoption challenges. Multiple studies used in online accounts. Previous work illustrated that building researched the security of different PWM types, finding that password managers means facing various security and usability challenges. For strong security and good usability, the interaction both browser-based and locally installed PWMs are vulner- between password managers and websites needs to be smooth and able to problems such as key theft or secret recovery from effortless. However, user reviews for popular password managers temporary files, as well as weaknesses within typical features suggest interaction problems for some websites. Therefore, to the such as autofill [64]. Other research focused on the usability best of our knowledge, this work is the first to systematically iden- of PWMs and were able to show that user adoption of PWMs tify these interaction problems and investigate how 15 desktop password managers, including the ten most popular ones, are is motivated by convenience of usage and usability [59]. affected. We use a qualitative analysis approach to identify 39 While security benefits can also be a driving factor for PWM interaction problems from 2,947 user reviews and 372 GitHub adoption, in the majority of cases these where only mentioned issues for 30 password managers. -

List of New Applications Added in ARL #2571
List of New Applications Added in ARL #2571 Application Name Publisher M*Modal Fluency Direct 3M M*Modal Fluency Direct Connector 10.0 3M M*Modal Fluency Direct Connector 3M M*Modal Fluency for Transcription Editor 3M M*Modal Fluency for Transcription Editor 7.6 3M M*Modal Fluency Flex 3M M*Modal Fluency Direct Connector 7.85 3M Fluency for Imaging 3M M*Modal Fluency Direct CAPD 3M Studio 3T 2020.7 3T Software Labs Studio 3T 2020.3 3T Software Labs Studio 3T 2020.8 3T Software Labs Studio 3T 2020.2 3T Software Labs MailRaider 3.69 Pro 45RPM software MailRaider 3.67 Pro 45RPM software Universal Restore Bootable Media Builder 11.5 Acronis ActivePerl 5.26 Enterprise ActiveState Photoshop Lightroom Classic [CRACKED!] CC (2018) Adobe Fresco CC (2020) Adobe Reader MUI Adobe Outlook Spy 4.0 Advanced Messaging Systems AE Broadcast+ Agencia Estado AE Broadcast Agencia Estado Airtame 3.4 Airtame ARGUS Enterprise 12.1 Altus Group Amethyst 0.15 Amethyst Game Engine BetterTouchTool 3.402 Andreas Hegenberg BetterTouchTool 2.428 Andreas Hegenberg BetterTouchTool 3.401 Andreas Hegenberg Password Manager SafeInCloud 20.2 Andrey Shcherbakov SynciOS Data Transfer 3.0 Anvsoft Video Download Capture 6.4 Apowersoft HEIC Converter Apowersoft AirServer 2020.7 App Dynamic Clipboard Viewer 3.0 Apple BIMx 2018 Apple Safari for Mac 14.0 Apple ARCserve Backup Agent for Microsoft Exchange 17.0 ARCserve ARCserve Backup Global Dashboard 17.5 ARCserve Arcserve Universal Agent 17.5 ARCserve ARCserve Backup NDMP NAS Option 17.0 ARCserve ARCserve Backup NDMP NAS Option -

Wachtwoorden Presentatie
Wachtwoorden themaochtend 31 januari 2017 1 Het programma • Algemene informatie • Aanmelden c.q. registreren • Over wachtwoorden aanmaken • Wachtwoorden bewaren • Wachtwoorden (software) kluizen • Software “SafeInCloud” & “KeePass” & “1Password” 2 Aanmelden c.q. Registreren Gebruikersnaam is meestal het emailadres Wachtwoord is …………….. 3 Het wachtwoord Hoe meer tekens, des te veiliger . 8 tekens is aan de korte kant. Een wachtwoord met 12 tekens of meer is veel sterker. Een wachtwoord van 12 in plaats van 8 tekens maakt het wachtwoord tot 80 miljoen keer zo sterk. Cijfers, hoofdletters en speciale tekens (&, ?, #, !, %, enz.) versterken het wachtwoord. Pas een Shift-ritme toe Om het extra ingewikkeld te maken kun je bijvoorbeeld ook gebruik maken van een zogenaamd Shift-ritme. Dat betekent dat je bijvoorbeeld bij het intikken van de eerste vier karakters van je wachtwoord de Shift- toets ingedrukt houdt en bij de tweede vier niet. Mew1sp1k? wordt dan MEW!sp1k? Gebruik verschillende wachtwoorden voor elke website en dienst. 4 Het wachtwoord Gebruik een wachtzin , die onthoud je makkelijker. Voorbeeld: IkHeb100Fietspompen. Het wachtwoord mag geen makkelijk te raden persoonlijke informatie bevatten, zoals een naam, geboortedatum of adres. 5 Check de sterkte van jouw wachtwoord Check hier of je wachtwoord veilig is 6 Wachtwoorden bewaren • Alles op papier ???? • In een (oud) schrift • Of een persoonlijk wachtwoorden logboek • Of een wachtwoordenkluis (lees software programma) • Drie voorbeelden “SafeInCloud” “KeePass” “1Password” 7 Wachtwoordkluis -

Deploying Authentication in the Wild: Towards Greater Ecological Validity
Journal of Cybersecurity, 2020, 1–15 doi: 10.1093/cybsec/tyaa010 Research Paper Research Paper Deploying authentication in the wild: towards greater ecological validity in security usability Downloaded from https://academic.oup.com/cybersecurity/article/6/1/tyaa010/5989371 by guest on 23 September 2021 studies Seb Aebischer,1 Claudio Dettoni,1 Graeme Jenkinson,1 Kat Krol,1 David Llewellyn-Jones,1 Toshiyuki Masui2,3 and Frank Stajano1,*,† 1Computer Laboratory, University of Cambridge, Cambridge, UK, 2Faculty of Science and Technology, Keio University Shonan Fujisawa Campus, Fujisawa, Kanagawa, Japan and 3Nota Inc., Japan *Correspondence address: Department of Computer Science and Technology, University of Cambridge, 15 JJ Thomson Avenue, Cambridge, CB3 0FD, UK. Tel: þ44-1223-763-500; E-mail: [email protected] †Authors listed in alphabetical order. All authors contributed in some form to the Gyazo study while only authors S.A., C.D., K.K., D.L.-J. and F.S. contributed to the Innovate UK study. Author G.J. designed and coded the reverse proxy used in the Gyazo study but left the Pico project before the study started. Author T.M., inventor and CTO of Gyazo, visited the other authors in Cambridge several times for a total of 6 months in connection with the Gyazo study. Authors S.A., C.D., K.K. and D.L.-J. were at Cambridge while they carried out the research described in this article. The Principal Investigator was F.S. Received 8 March 2019; revised 24 January 2020; accepted 19 May 2020 Abstract Pico is a token-based login method that claims to be simultaneously more usable and more secure than passwords. -

Digitaalgids 2 Maart 2020 Dossier Wachtwoordmanagers
dossier WACHTWOORDMANAGERS Nog steeds gebruiken 5 op de 6 Nederlanders geen wachtwoordmanager. Terwijl die zo veilig én makkelijk is. Met dit dossier krijgt u alles in handen om de sprong te wagen. 30 Wacht niet langer 32 Test 36 Workshop Dit artikel trekt je over de Welke wachtwoordmanager Aan de slag met het gratis streep (hopen we) is de beste? Bitwarden Illustraties Erik Flokstra maart/april 2020 DigitaalGids 29 INLEIDING WACHTWOORDMANAGERS Behoor je ook tot de 85% die nog steeds geen wachtwoordmanager gebruikt? Wacht niet langer. Het is minder gedoe dan je denkt. WACHT NIET LANGER Gebruik een wachtwoordmanager k zal er niet omheen draaien. Dit artikel is bedoeld om weifelaars over Ide streep te trekken. Mensen die zeg- gen: overstappen op een wachtwoord- manager lijkt me een enorm gedoe. Ik ken de gedachte maar al te goed. Ik dacht namelijk precies hetzelfde. Het heeft bij mij dan ook lang geduurd voordat ik ‘om’ was. Nu ben ik blij dat ik de stap heb gezet en wil ik nooit meer terug naar de oude situatie. De truc van een soepele overstap is om het in stappen te doen. Als je 'm een- maal gebruikt, is het ontzettend prak- tisch dat je nooit meer een wachtwoord hoeft te onthouden. En inloggen gaat veel sneller, alles wordt voor je ingevuld. In dit artikel ontzenuwen we twee ande- re argumenten om geen wachtwoord- manager te gebruiken: ‘wachtwoorden in de cloud zijn niet veilig’ en ‘niet nodig, mijn browser slaat ze al op’. Ook daar valt het nodige op af te dingen. 30 DigitaalGids maart/april 2020 Tekst Vincent van Amerongen DOSSIER WACHTWOORDMANAGERS Het is niet zo veel waar ik nog geen account had, dan bood een stuk veiliger dan als alternatief 1. -

An Analysis of Modern Password Manager Security and Usage on Desktop and Mobile Devices
University of Tennessee, Knoxville TRACE: Tennessee Research and Creative Exchange Doctoral Dissertations Graduate School 5-2021 An Analysis of Modern Password Manager Security and Usage on Desktop and Mobile Devices Timothy Oesch [email protected] Follow this and additional works at: https://trace.tennessee.edu/utk_graddiss Part of the Information Security Commons, Other Computer Engineering Commons, and the Other Computer Sciences Commons Recommended Citation Oesch, Timothy, "An Analysis of Modern Password Manager Security and Usage on Desktop and Mobile Devices. " PhD diss., University of Tennessee, 2021. https://trace.tennessee.edu/utk_graddiss/6670 This Dissertation is brought to you for free and open access by the Graduate School at TRACE: Tennessee Research and Creative Exchange. It has been accepted for inclusion in Doctoral Dissertations by an authorized administrator of TRACE: Tennessee Research and Creative Exchange. For more information, please contact [email protected]. To the Graduate Council: I am submitting herewith a dissertation written by Timothy Oesch entitled "An Analysis of Modern Password Manager Security and Usage on Desktop and Mobile Devices." I have examined the final electronic copy of this dissertation for form and content and recommend that it be accepted in partial fulfillment of the equirr ements for the degree of Doctor of Philosophy, with a major in Computer Engineering. Scott I. Ruoti, Major Professor We have read this dissertation and recommend its acceptance: Kent Seamons, Jinyuan Sun, Doowon Kim, Scott I. Ruoti Accepted for the Council: Dixie L. Thompson Vice Provost and Dean of the Graduate School (Original signatures are on file with official studentecor r ds.) An Analysis of Password Manager Security and Usage on Desktop and Mobile Devices A Dissertation Presented for the Doctor of Philosophy Degree The University of Tennessee, Knoxville Timothy Sean Oesch May 2021 © by Timothy Sean Oesch, 2021 All Rights Reserved.