Analyse D'un Logiciel De Gestion Des Mots De Passe
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Lösenordshantering
LÖSENORDSHANTERING www.2secure.se Lösenordshantering Våra liv utspelar sig numera i stor utsträckning online. Vi handlar kläder, böcker och prylar, streamar filmer och musik, skickar e-post, delar bilder och meddelanden i sociala medier, betalar räkningar, ansöker om föräldrapenning, och mycket mer. För allt detta finns onlinetjänster i någon form, och för alla dessa tjänster behöver vi kunna identifiera oss. För att identifiera oss på en webbsida behöver vi vanligtvis ange ett användarnamn och ett lösenord. I vissa fall har vi en fysisk enhet (t ex en mobiltelefon eller ett bankkort) som kräver en PIN-kod. I mobilen har vi ett BankID där vi måste mata in en verifieringskod. Och så vidare. Hur många koder, lösenord, säkerhetsfrågor och andra inloggningsuppgifter har du? Några exempel som du kanske känner igen: Användarkonton och lösenord AppleID och iCloud Aktiedepå Gmail/Google Apps Spotify Hotmail Netflix Facebook Mataffären/Matkassen Twitter Flygbolag Instagram Taxibolag Snapchat Bokhandel Internetbanken Kläder och skor Försäkringskassan Apoteket Hem-/bil-/sjuk- Online-dating /olycksfallsförsäkringen Spel och dobbel Pensionsbolag Routern till hemmanätverket Livsförsäkring Koder Mobiltelefon - lösenkod till enhet, PIN och PUK till SIM-kort Surfplatta - lösenkod till enhet, eventuell PIN och PUK till SIM-kort Kod till hemlarmet WiFi-lösenordet hemma Bank- och kreditkort - PIN, CVV-kod, SecureCode/3DSecure för online BankID Och då har vi inte ens pratat om alla användarkonton, lösenord och koder på jobbet. VPN, intranät, HR-portalen, CRM-systemet, andra affärssystem... Information Vi har numera dussintals olika konton för tjänsterna vi använder för allehanda syften. "Nyckeln" till varje tjänst är ett användarnamn och ett lösenord. Redan här behöver vi alltså hålla reda på väldigt känslig information. -

Password Managers an Overview
Peter Albin Lexington Computer and Technology Group March 13, 2019 Agenda One Solution 10 Worst Passwords of 2018 Time to Crack Password How Hackers Crack Passwords How Easy It Is To Crack Your Password How Do Password Managers Work What is a Password Manager Why use a Password Manager? Cloud Based Password Managers Paid Password Managers Free Password Managers How to Use LastPass How to Use Dashlane How to Use Keepass Final Reminder References March 13, 2019 2 One Solution March 13, 2019 3 10 Worst Passwords of 2018 1. 123456 2. password 3. 123456789 4. 12345678 5. 12345 6. 111111 7. 1234567 8. sunshine 9. qwerty 10. iloveyou March 13, 2019 4 Time to Crack Password March 13, 2019 5 Time to Crack Password March 13, 2019 6 Time to Crack Password March 13, 2019 7 Time to Crack Password Time to crack password "security1" 1600 1400 1200 1000 Days 800 Days 600 400 200 0 2000 2001 2002 2003 2004 2005 2006 2007 2008 2009 2010 2011 2012 2013 2014 2015 2016 Year March 13, 2019 8 How Hackers Crack Passwords https://youtu.be/YiRPt4vrSSw March 13, 2019 9 How Easy It Is To Crack Your Password https://youtu.be/YiRPt4vrSSw March 13, 2019 10 How Do Password Managers Work https://youtu.be/DI72oBhMgWs March 13, 2019 11 What is a Password Manager A password manager will generate, retrieve, and keep track of super-long, crazy-random passwords across countless accounts for you, while also protecting all your vital online info—not only passwords but PINs, credit-card numbers and their three-digit CVV codes, answers to security questions, and more … And to get all that security, you’ll only need to remember a single password March 13, 2019 12 Why use a Password Manager? We are terrible at passwords We suck at creating them the top two most popular remain “123456” and “password” We share them way too freely We forget them all the time We forget them all the time A password manager relieves the burden of thinking up and memorizing unique, complex logins—the hallmark of a secure password. -

Password Managers
Studying the Impact of Managers on Password Strength and Reuse Sanam Ghorbani Lyastani∗, Michael Schilling†, Sascha Fahl‡, Sven Bugiel∗, Michael Backes§ ∗CISPA, Saarland University, †Saarland University, ‡Leibniz University Hannover, §CISPA Helmholtz Center i.G. Abstract—Despite their well-known security problems, pass- applications. Password managers are being recommended as a words are still the incumbent authentication method for virtually solution because they fulfill important usability and security all online services. To remedy the situation, end-users are very aspects at the same time: They store all the users’ passwords often referred to password managers as a solution to the pass- word reuse and password weakness problems. However, to date so the users do not have to memorize them; they can also help the actual impact of password managers on password security users entering their passwords by automatically filling them into and reuse has not been studied systematically. log-in forms; and they can also offer help in creating unique, In this paper, we provide the first large-scale study of the random passwords. By today, there are several examples for password managers’ influence on users’ real-life passwords. From third party password managers that fit this description, such 476 participants of an online survey on users’ password creation and management strategies, we recruit 170 participants that as Lastpass [5], 1Password [1], and even seemingly unrelated allowed us to monitor their passwords in-situ through a browser security software, such as anti-virus [4] solutions. plugin. In contrast to prior work, we collect the passwords’ entry Unfortunately, it has not been sufficiently studied in the past methods (e.g., human or password manager) in addition to the whether password managers fulfill their promise and indeed passwords and their metrics. -

Enpass User Manual - Android Version 6.7
Enpass User Manual - Android version 6.7 Enpass Technologies Inc. August 19, 2021 Contents User Manual 1 Introduction to Enpass 1 Prerequisites 1 Getting Started 1 As a new user 4 As an existing user 6 Import Passwords from Other Sources 6 Master password 6 Keyfiles 6 Generating the keyfile 7 Adding the keyfile 7 Removing keyfiles 7 Registration 7 Adding and Managing items 9 Adding Item 9 Adding One-Time Code 10 Adding Attachments 12 Attach Photo 12 Attach file 12 View Attachment 12 Delete Attachment 12 Tags 13 Tagging items 13 From Edit page 13 From Sidebar 13 Nested Tags 14 Editing Tags 14 Untag an Item 14 Deleting and Archiving 14 Trash 14 Archive 15 Duplicating Item 15 Customizing Fields 15 Editing field type 15 Adding fields 16 Re-ordering Fields 16 Deleting fields 17 Field History 17 Customizing Password Fields 18 Exclude from Audit 18 Set Password Expiry 18 Sensitive 18 Adding Section 18 Customizing icons 18 Using website icons 18 Enabling website icons for a particular site: 19 Using your own images as custom icons 19 Changing Category 20 Search 20 Sort By 21 Title 21 Url 21 Created Date 22 Modified Time 22 Recently Used 23 Frequently Used 23 Moving Items to Other Vaults 23 Checking Compromised Passwords 23 Checking Individual Password 23 Checking All Passwords 24 How does it work? 25 What to do if you have Compromised Passwords? 25 Change Password Immediately 25 Enable Two-Factor Authentication 25 Regularly keep a check on Passwords’ Health 25 Using Password Generator 25 Generating Passwords 25 Pronounceable Passwords 25 Random -

HACK Enpass Password Manager
1 / 2 HACK Enpass Password Manager Mar 23, 2021 — So, is this password manager right for you or your business? In our Enpass review, we'll take a closer look at everything this software has to offer.. Results 1 - 100 of 338 — TOTP is an algorithm that computes a one-time password from a shared secret ... codes to protect your online accounts from hackers (bad guys). ... code in my password manager, especially for password managers that can ... Segregate data using Multiple vaults Enpass facilitates you with an option to .... Jan 9, 2019 — Password manager company OneLogin was actually hacked, and the ... EnPass: Here's something unusual—a password manager that goes .... Use Enpass audit tools to identify weak, identical, and old passwords. Your password manager is your digital security best friend. You are using a password .... The Synology Disk Station Manager (DSM) is the Operating System (OS) that runs on your Synology unit. ... a prerequisite while using Enpass it is not really neccessary to me to sync with CloudStation. ... For iOS 13/12 users: Open the Settings app > Passwords & Accounts > Add Account > Other ... Mikrotik hack github.. We will send a One-time password (OTP) to your registered email address and ... set of Enpass users by letting them store their time based one time passwords of ... Hackers use credit card skimmers to obtain the magnetic stripe information of a ... Open Google Chrome and click the GateKeeper Password Manager Chrome .... Jun 16, 2021 — Using an online password manager? … Are they safe from hackers?? Use Enpass to securely organize everything at one place. -

Password Managers
Password Managers A Higher Education Information Security Council (HEISC) Resource JULY 2019 Password Managers What Is a Password Manager Tool? A password manager tool is software that helps users encrypt, store, and manage passwords. The tool also helps users create secure passwords and automatically log in to websites. Who Might Use a Password Manager Tool, and Why? Users should employ unique passwords for each website or system to help minimize the impact from the breach of one website or system; however, most users cannot remember a separate password for many sites and tend to reuse passwords or write them on a sticky note attached to their computer. Additionally, organizations may have passwords that need to be shared across teams and want a secure method to do so. Password manager tools allow users and teams to more securely manage many distinct passwords and automatically log them in to websites. The Benefits of Using a Password Manager Tool Password manager tools enable users to create and securely store unique passwords for websites, applications, and other systems without having to memorize or write them down. Risks to Consider When Using a Password Manager Tool Special care should be taken to secure the password tool, as it will grant access to all passwords. The “master” password that grants access to the tool should be very strong and unique, and multifactor authentication should be used if possible. Almost all modern commercial password managers allow users to implement some form of multifactor authentication. You will also need to decide whether you want your password management tool to store passwords locally or in the cloud. -
Ratgeber Zum Datenschutz Umgang Mit Passwörtern
Umgang mit Passwörtern Ratgeber zum Datenschutz Umgang mit Passwörtern Ratgeber zum Datenschutz Herausgeberin: Berliner Beauftragte für Datenschutz und Informationsfreiheit Friedrichstr. 219 Besuchereingang: Puttkamerstr. 16-18 10969 Berlin Telefon: 030 13889-0 Telefax: 030 2155050 E-Mail: [email protected] Gestaltung: april agentur GbR Druck: ARNOLD group. Stand: Juni 2020 Einleitung Um die Vertraulichkeit, Integrität und Authentizität per- sonenbezogener Daten bei der Nutzung von (Online-) Diensten gewährleisten zu können, muss die Identität der Nutzenden überprüft werden. Diese Identifizierung und Authentifizierung geschieht in der Regel durch die Eingabe einer Kombination aus persönlicher Kennung (Benutzer- name) und geheimem Passwort. Wer Kennung und Pass- wort kennt, kann sich authentifizieren. Bei Verfahren mit normalem Schutzbedarf kann eine sol- che Authentifizierung derzeit gerade noch als hinreichend angesehen werden. Von normalem Schutzbedarf ist dann auszugehen, wenn weder große Datenmengen noch sen- sible oder sensitive Daten verarbeitet werden. Um sensiti- ve Daten handelt es sich, wenn sie nach der Datenschutz- Grundverordnung zu besonderen Kategorien mit erhöhtem Schutzbedarf zählen, also etwa Gesundheitsdaten oder Daten über Herkunft, Religion oder sexuelle Orientierung der Betroffenen. 1 Sobald Anwendungen und Dienste Zugriff auf sensible, sensitive oder eine große Anzahl von personenbezogenen Daten ermöglichen, besteht ein erhöhter Schutzbedarf, der eine stärkere Absicherung der Daten mit einem oder meh- reren weiteren Faktoren erforderlich macht. Möglichkei- ten für eine solche Mehrfaktor-Authentifizierung sind z. B.: • Abfragen über den Besitz physischer Geräte, die mit dem Dienst verknüpft sind (Hardware-Token, der zeitabhängig eine TAN ausgibt oder über den USB- Port mit dem Dienst kommuniziert, Chipkarte, SMS- TAN, mTAN) oder • Abgleich von biometrischen Daten (also von Körper- merkmalen, etwa durch einen Iris-Scan, Fingerab- druck oder Gesichtserkennung). -

Enpass Portable Version 6.4
Enpass Portable version 6.4 May 05, 2020 Contents User Manual 1 Welcome to Enpass Portable 1 Prerequisites 1 Who should use Enpass Portable? 1 What’s New in 6.4.0 1 Setting up Enpass Portable 2 For Mac & Windows 2 For Linux 2 For Cross-platfrom Usage 3 Using Enpass Portable 3 Enpass Browser Extension 6 Importing data from other softwares 6 User Manual User Manual Enpass Version– 6.4.0 Welcome to the user manual for Enpass Portable. This manual features detailed guidelines to make you well-acquainted with the app’s functionality. Welcome to Enpass Portable Unlike traditional Enpass desktop apps, the portable version does not require installation. You can put it on a USB drive and move between computers while taking your app and settings with you. The Enpass portable version has features similar to that of the Enpass Desktop version. Because Enpass runs without installtion on the system, it’s lightweight and won’t leave any footprint on the devices you run it on. Everything, including any settings you’ve saved, is saved right in the portable app’s folder on the USB drive. Prerequisites To use the Portable version, all you need is a USB drive and the platform specific Enpass Portable zip file. • Windows: Requires Windows 7 or above. • Mac: Requires macOS 10.11 or later. • Linux: Tested on Ubuntu 14.04 or later ; Fedora 22 or later (only for 64-bit OS). Who should use Enpass Portable? If you want to use Enpass on your personal desktops, then you should always use our desktop app. -

A Security Analysis of Autofill on Ios and Android
The Emperor’s New Autofill Framework: A Security Analysis of Autofill on iOS and Android Sean Oesch, Anuj Gautam, Scott Ruoti The University of Tennessee [email protected], [email protected], [email protected] Abstract—Password managers help users more effectively (P3) the filled credential will only be accessible to the manage their passwords, encouraging them to adopt stronger mapped app or web domain. [23]. passwords across their many accounts. In contrast to desktop On desktop environments, password managers are primarily systems where password managers receive no system-level support, mobile operating systems provide autofill frameworks implemented as ad-hoc browser extensions—i.e., the extension that are designed to integrate with password managers to individually implements all aspects of the autofill process provide secure and usable autofill for browsers and other apps without support from OS or browser autofill frameworks. installed on mobile devices. In this paper, we conduct the first While some desktop password managers correctly achieve P1 holistic security evaluation of such frameworks on iOS and and P2 [19], many have incorrect implementations that allow Android, examining whether they achieve substantive benefits over the ad-hoc desktop environment or become a problematic attackers to steal or phish users’ credentials [14], [22], [23], single point of failure. Our results find that while the [19], and none can fully implement P3 due to technical frameworks address several common issues (e.g., requiring user limitations of browser extension APIs [23], [19]. interaction before autofill), they also enforce insecure behavior In contrast to the situation on desktop, mobile operating and fail to provide the password managers implemented using systems provide system-wide autofill frameworks that attempt the frameworks with sufficient information to override this incorrect behavior. -

Revisiting Security Vulnerabilities in Commercial Password Managers?
Revisiting Security Vulnerabilities in Commercial Password Managers? Michael Carr1 and Siamak F. Shahandashti2 1 Piksel, York Science Park, YO10 5ZD, UK [email protected] 2 Dept. of Computer Science, University of York, YO10 5GH, UK [email protected] Abstract. In this work we analyse five popular commercial password managers for security vulnerabilities. Our analysis is twofold. First, we compile a list of previously disclosed vulnerabilities through a compre- hensive review of the academic and non-academic sources and test each password manager against all the previously disclosed vulnerabilities. We find a mixed picture of fixed and persisting vulnerabilities. Then we carry out systematic functionality tests on the considered password managers and find four new vulnerabilities. Notably, one of the new vulnerabilities we identified allows a malicious app to impersonate a legitimate app to two out of five widely-used password managers we tested and as a result steal the user's password for the targeted service. We implement a proof- of-concept attack to show the feasibility of this vulnerability in a real-life scenario. Finally, we report and reflect on our experience of responsible disclosure of the newly discovered vulnerabilities to the corresponding password manager vendors. Keywords: Vulnerability Testing · Password Managers · Password Man- ager Security · Authentication. 1 Introduction Passwords remain the dominant authentication mechanism in the digital realm despite their shortcomings. Furthermore, they are expected to persist as a pri- mary authentication mechanism for the some time [6]. Among the tools that can greatly reduce the cognitive burden of remembering multiple passwords for arXiv:2003.01985v2 [cs.CR] 17 Mar 2020 multiple services are password managers. -
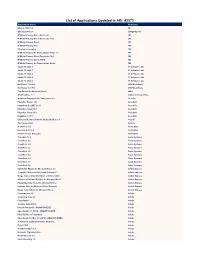
List of Applications Updated in ARL #2573
List of Applications Updated in ARL #2573 Application Name Publisher BIOS to UEFI 1.4 1E SyncBackPro 9.3 2BrightSparks M*Modal Fluency Direct Connector 3M M*Modal Fluency Direct Connector 7.85 3M M*Modal Fluency Direct 3M M*Modal Fluency Flex 3M Fluency for Imaging 3M M*Modal Fluency for Transcription Editor 7.6 3M M*Modal Fluency Direct Connector 10.0 3M M*Modal Fluency Direct CAPD 3M M*Modal Fluency for Transcription Editor 3M Studio 3T 2020.5 3T Software Labs Studio 3T 2020.7 3T Software Labs Studio 3T 2020.2 3T Software Labs Studio 3T 2020.8 3T Software Labs Studio 3T 2020.3 3T Software Labs MailRaider 3.69 Pro 45RPM software MailRaider 3.67 Pro 45RPM software Text Toolkit for Microsoft Excel 4Bits ASAP Utilities 7.7 A Must in Every Office Graphical Development Environment 3.2 Ab Initio PrizmDoc Server 13.8 AccuSoft ImageGear for .NET 24.11 AccuSoft PrizmDoc Client 13.8 AccuSoft PrizmDoc Client 13.9 AccuSoft ImagXpress 13.5 AccuSoft Universal Restore Bootable Media Builder 11.5 Acronis True Image 2020 Acronis ActivePerl 5.12 ActiveState Komodo Edit 12.0 ActiveState ActivePerl 5.26 Enterprise ActiveState TransMac 12.6 Acute Systems CrossFont 6.5 Acute Systems CrossFont 6.6 Acute Systems CrossFont 6.2 Acute Systems CrossFont 5.5 Acute Systems CrossFont 5.6 Acute Systems CrossFont 6.3 Acute Systems CrossFont 5.7 Acute Systems CrossFont 6.0 Acute Systems Split Table Wizard for Microsoft Excel 2.3 Add-in Express Template Phrases for Microsoft Outlook 4.7 Add-in Express Merge Tables Wizard for Microsoft Excel 2018 Add-in Express Advanced -
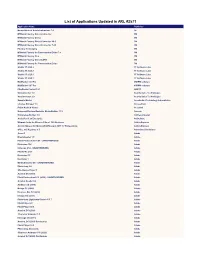
List of Applications Updated in ARL #2571
List of Applications Updated in ARL #2571 Application Name Publisher Nomad Branch Admin Extensions 7.0 1E M*Modal Fluency Direct Connector 3M M*Modal Fluency Direct 3M M*Modal Fluency Direct Connector 10.0 3M M*Modal Fluency Direct Connector 7.85 3M Fluency for Imaging 3M M*Modal Fluency for Transcription Editor 7.6 3M M*Modal Fluency Flex 3M M*Modal Fluency Direct CAPD 3M M*Modal Fluency for Transcription Editor 3M Studio 3T 2020.2 3T Software Labs Studio 3T 2020.8 3T Software Labs Studio 3T 2020.3 3T Software Labs Studio 3T 2020.7 3T Software Labs MailRaider 3.69 Pro 45RPM software MailRaider 3.67 Pro 45RPM software FineReader Server 14.1 ABBYY VoxConverter 3.0 Acarda Sales Technologies VoxConverter 2.0 Acarda Sales Technologies Sample Master Accelerated Technology Laboratories License Manager 3.5 AccessData Prizm ActiveX Viewer AccuSoft Universal Restore Bootable Media Builder 11.5 Acronis Knowledge Builder 4.0 ActiveCampaign ActivePerl 5.26 Enterprise ActiveState Ultimate Suite for Microsoft Excel 18.5 Business Add-in Express Add-in Express for Microsoft Office and .NET 7.7 Professional Add-in Express Office 365 Reporter 3.5 AdminDroid Solutions Scout 1 Adobe Dreamweaver 1.0 Adobe Flash Professional CS6 - UNAUTHORIZED Adobe Illustrator CS6 Adobe InDesign CS6 - UNAUTHORIZED Adobe Fireworks CS6 Adobe Illustrator CC Adobe Illustrator 1 Adobe Media Encoder CC - UNAUTHORIZED Adobe Photoshop 1.0 Adobe Shockwave Player 1 Adobe Acrobat DC (2015) Adobe Flash Professional CC (2015) - UNAUTHORIZED Adobe Acrobat Reader DC Adobe Audition CC (2018)