Final Notice
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Chronology, 1963–89
Chronology, 1963–89 This chronology covers key political and economic developments in the quarter century that saw the transformation of the Euromarkets into the world’s foremost financial markets. It also identifies milestones in the evolu- tion of Orion; transactions mentioned are those which were the first or the largest of their type or otherwise noteworthy. The tables and graphs present key financial and economic data of the era. Details of Orion’s financial his- tory are to be found in Appendix IV. Abbreviations: Chase (Chase Manhattan Bank), Royal (Royal Bank of Canada), NatPro (National Provincial Bank), Westminster (Westminster Bank), NatWest (National Westminster Bank), WestLB (Westdeutsche Landesbank Girozentrale), Mitsubishi (Mitsubishi Bank) and Orion (for Orion Bank, Orion Termbank, Orion Royal Bank and subsidiaries). Under Orion financings: ‘loans’ are syndicated loans, NIFs, RUFs etc.; ‘bonds’ are public issues, private placements, FRNs, FRCDs and other secu- rities, lead managed, co-managed, managed or advised by Orion. New loan transactions and new bond transactions are intended to show the range of Orion’s client base and refer to clients not previously mentioned. The word ‘subsequently’ in brackets indicates subsequent transactions of the same type and for the same client. Transaction amounts expressed in US dollars some- times include non-dollar transactions, converted at the prevailing rates of exchange. 1963 Global events Feb Canadian Conservative government falls. Apr Lester Pearson Premier. Mar China and Pakistan settle border dispute. May Jomo Kenyatta Premier of Kenya. Organization of African Unity formed, after widespread decolonization. Jun Election of Pope Paul VI. Aug Test Ban Take Your Partners Treaty. -

The Headquarters of National Provincial Bank of England
Symbolism in bank marketing and architecture: the headquarters of National Provincial Bank of England Article Published Version Creative Commons: Attribution 4.0 (CC-BY) Open Access Barnes, V. and Newton, L. (2019) Symbolism in bank marketing and architecture: the headquarters of National Provincial Bank of England. Management and Organizational History, 14 (3). pp. 213-244. ISSN 1744-9359 doi: https://doi.org/10.1080/17449359.2019.1683038 Available at http://centaur.reading.ac.uk/86938/ It is advisable to refer to the publisher’s version if you intend to cite from the work. See Guidance on citing . To link to this article DOI: http://dx.doi.org/10.1080/17449359.2019.1683038 Publisher: Taylor and Francis All outputs in CentAUR are protected by Intellectual Property Rights law, including copyright law. Copyright and IPR is retained by the creators or other copyright holders. Terms and conditions for use of this material are defined in the End User Agreement . www.reading.ac.uk/centaur CentAUR Central Archive at the University of Reading Reading’s research outputs online Management & Organizational History ISSN: 1744-9359 (Print) 1744-9367 (Online) Journal homepage: https://www.tandfonline.com/loi/rmor20 Symbolism in bank marketing and architecture: the headquarters of National Provincial Bank of England Victoria Barnes & Lucy Newton To cite this article: Victoria Barnes & Lucy Newton (2019) Symbolism in bank marketing and architecture: the headquarters of National Provincial Bank of England, Management & Organizational History, 14:3, 213-244, DOI: 10.1080/17449359.2019.1683038 To link to this article: https://doi.org/10.1080/17449359.2019.1683038 © 2019 The Author(s). -

The Employment Tribunals
Case Number: 2203113/2019 A 2204740/2019 A 2205092/2019 A THE EMPLOYMENT TRIBUNALS Claimants Respondents (1) Ms S Feng v (1) National Westminster Bank (2) Ms N Holland PLC (2) Ms M Tang (3) Ms A Hammond Heard at: London Central On: 21 January 2021 Before: Employment Judge Glennie Representation: Claimants: (1) In person (2) Represented by Ms Feng Respondents: Ms T Barsam (Counsel) JUDGMENT ON PRELIMINARY HEARING 1. National Westminster Bank PLC is added as First Respondent to the claims. 2. Coutts & Co and Royal Bank of Scotland Group are discharged as Respondents. 3. The Tribunal does not have jurisdiction to hear the complaints of negligence and/or breach of duty at common law giving rise to personal injury in Schedule 5 of the Claimants’ schedule of claims. These complaints are therefore struck out. REASONS 1. Ms Feng asked for written reasons for my decision to discharge Coutts & Co and Royal Bank of Scotland Group as Respondents, but not in relation to my decision about the negligence / breach of common law duty complaints. These reasons therefore cover the former point only. 1 Case Number: 2203113/2019 A 2204740/2019 A 2205092/2019 A 2. Claim number 2203113/2019 was brought by Ms Feng with “Coutts (Royal Bank of Scotland)” named as First Respondent. The complaints were of race discrimination. The Response identified National Westminster Bank PLC as the correct First Respondent. Claim number 2204740/2019 was brought by Ms Feng and Ms Holland and named the First Respondent as “Coutts (Royal Bank of Scotland Group)”. The complaints were of victimisation, detriments by reason of protected disclosures, indirect race discrimination, harassment and negligence. -

Rbs.Com Annual Review and Summary Financial Statement 2010
Annual Review and Summary Financial Statement 2010 rbs.com What’s inside 01 Essential reading 20 Divisional review 02 Chairman’s statement 22 UK Retail 04 Group Chief Executive’s review 24 UK Corporate 06 Q&As on progress 26 Wealth 07 Our key targets 28 Global Transaction Services 30 Ulster Bank 08 Our business and our strategy 32 US Retail & Commercial 10 Our approach to business 34 Global Banking & Markets 12 Progress on our Strategic Plan 36 RBS Insurance 14 Our Core businesses 38 Business Services and Central Functions 16 The economic environment 40 Non-Core Division 17 Our approach to risk management 41 Asset Protection Scheme (APS) 42 Sustainability 44 Sustainability in practice 45 Our five key themes 45 Our community programmes 47 Highlights of how we focus action across our businesses 48 Directors’ report and summary financial statement 50 Board of directors and secretary 52 Executive Committee 54 Our approach to Governance M Why go online? 56 Letter from the Chair of the Remuneration Committee www.rbs.com/AnnualReport 58 Summary remuneration report If you haven’t already tried it, visit our easy-to-use online Annual Report. Many shareholders are now 62 Financial results benefiting from more accessible information and 69 Shareholder information helping the environment too. Essential reading We have met, and in some cases exceeded, the targets for the second year of our Strategic Plan. 2010 business achievements Our 2013 vision Good progress against Strategic Plan targets Enduring customer franchises Core bank becoming stronger -

Royal Bank of Scotland International Rated 'BBB/A-2'; Outlook Positive
Research Update: Royal Bank of Scotland International Rated 'BBB/A-2'; Outlook Positive Primary Credit Analyst: Sadat Preteni, London (44) 20-7176-7560; [email protected] Secondary Contact: Alexandre Birry, London (44) 20-7176-7108; [email protected] Table Of Contents Overview Rating Action Rationale Outlook Related Criteria Related Research Ratings List WWW.STANDARDANDPOORS.COM/RATINGSDIRECT JANUARY 30, 2018 1 1986956 | 301308293 Research Update: Royal Bank of Scotland International Rated 'BBB/A-2'; Outlook Positive Overview • The Royal Bank of Scotland Group PLC (RBSG) plans to complete a formal separation of its banking operations under the U.K's ring-fencing regime by mid-2018. • Under the upcoming ring-fencing regulations, Jersey-based Royal Bank of Scotland International Ltd. (RBS International) will be one of the non-ring-fenced operating subsidiaries of RBSG. • We are assigning our 'BBB/A-2' ratings to RBS International as we regard this entity as a highly strategic operating subsidiary of RBSG. • The positive outlook reflects our view that we could revise upward RBS' group credit profile over the coming 18-24 months, which would result in an upgrade of RBS International. Rating Action On Jan. 30, 2018, S&P Global Ratings assigned its 'BBB/A-2' long- and short-term issuer credit ratings to RBS International. The outlook is positive. Rationale The U.K. financial regulator's ring-fencing requirements seek to remove the operational and financial dependencies and links between the systemically important activities of major U.K. banks and their less-systemically important, and often risker, activities. Each bank has therefore had to decide how to split those activities between different subsidiaries or whether to cease offering some of them. -

National Westminster Bank Plc Annual Report and Accounts 2019
National Westminster Bank Plc Annual Report and Accounts 2019 natwest.com Strategic report Franchises Page Commercial & Private Banking (CPB), combining the reportable Strategic report segments of Commercial Banking and Private Banking ceased to Presentation of information 1 operate as one business area and the franchise Personal & Ulster, Description of business 1 combining the reportable segments of UK Personal Banking and Ulster Principal activities and operating segments 1 Bank RoI was also disbanded. The reportable operating segments Performance overview 1 remain unchanged and no comparatives have been restated. Stakeholder engagement and s.172(1) statement 3 Principal activities and operating segments Board of directors and secretary 5 NWB Group serves customers across the UK and Ireland with a range Top and emerging risks 6 of retail and commercial banking products and services. A wide range Financial review 7 of personal products are offered including current accounts, credit Capital and risk management 10 cards, personal loans, mortgages and wealth management services. Report of the directors 65 NWB Plc is the main provider of shared service activities for RBS Statement of directors’ responsibilities 69 Group. This includes the provision of Treasury services on behalf of Financial Statements 70 the ring-fenced bank and RBS Group. Risk factors 150 The reportable operating segments are as follows: Forward-looking statements 163 UK Personal Banking serves individuals and mass affluent customers Presentation of information in the UK and includes Ulster Bank customers in Northern Ireland. National Westminster Bank Plc (‘NWB Plc’) is a wholly-owned subsidiary of NatWest Holdings Limited (‘NWH Ltd’ or ‘the intermediate Commercial Banking serves start-up, SME, commercial and corporate holding company’). -

Annual Report and Accounts 2016
Annual Report & Accounts 2016 Report & Accounts Annual Building our brands Direct Line Insurance Group plc Annual Report & Accounts 2016 Contents Strategic report 2 Group highlights 4 Group at a glance 6 Market overview 8 Business model 10 Chairman’s statement 12 Chief Executive Officer’s review 14 Our strategy 24 Our key performance indicators 26 Risk management 30 Corporate social responsibility 34 Operating review 38 Finance review Governance 48 Chairman’s introduction 50 Board of Directors 52 Executive Committee 53 Corporate governance report 64 Committee reports 82 Directors’ remuneration report 110 Directors’ report Financial statements 114 Contents 115 Independent Auditor’s report 122 Consolidated financial statements 127 Notes to the consolidated For all the latest news financial statements and announcements visit www.directlinegroup.com 179 Parent Company financial statements 182 Notes to the Parent Company financial statements Other information 187 Additional information 189 Glossary and appendices 195 Forward-looking statements disclaimer 196 Contact information Building our brands Our mission: To make insurance much easier and better value for our customers Our strategy supports our aspiration to be the leading personal and small business general insurer in the UK. Our customers are at the centre of everything we do, as we remain focused on protecting an ever-changing Britain. Building a culture of great service Find out more on page 18 Building our brands by offering more Find out more on page 22 Building our technology and data capabilities Find out more on page 20 www.directlinegroup.com 1 Group highlights Providing stability for our customers and shareholders Profit before tax1 Return on tangible equity2 Combined operating ratio2 (£m) (%) Ongoing operations2 (%) 9 7. -

Natwest-Markets-Nv-Cash-Ssi.Pdf
NatWest Markets N.V., AMSTERDAM Standard Settlement Instruction (cash) for Foreign Exchange, Money Market, Currency Options, FRAs, Interest Rate & Commodity Swaps, Interest Rate & Commodity Options, Fixed Income, Collateral, Credit Derivatives and Exchange Traded Futures & Options & Equity Derivatives Transactions. All accounts are in the name of NatWest Markets N.V., Amsterdam OMGEO Alert Acronym is RBSFMFX. Model Name is NWMNV. Effective From 15/04/2019 Correspondent Swift Beneficiary ISO CCY Country Correspondent Details Account Number Address Swift Code United Arab 1012003958924016 AED NBADAEAA National Bank of Abu Dhabi RBOSNL2RTCM Emirates IBAN - AE540351012003958924016 AUD Australia NATAAU3303M National Australia Bank Ltd Melbourne 1803114456500 RBOSNL2RTCM BBD BARBADOS BNBABBBB Republic Bank (Barbados) Ltd 028042192003 RBOSNL2RTCM 1030028017 BGN BULGARIA RZBBBGSF Raiffesen Bank AD Sofia RBOSNL2RTCM IBAN - BG55RZBB91551030028017 0099637057 BHD BAHRAIN NBOBBHBM National Bank of Bahrain RBOSNL2RTCM IBAN - BH94NBOB00000099637057 BMD Bermuda BNTBBMHM Bank of NT Butterfield & Son Hamilton 0601664670019 RBOSNL2RTCM CAD CANADA ROYCCAT2 Royal Bank of Canada Toronto 095911005743 RBOSNL2RTCM 02300000061046050000B CHF Switzerland UBSWCHZH80A UBS AG, Zurich RBOSNL2RTCM IBAN - CH140023023006104605B Care should be taken as this relates to CNH/CNY trading and settling offshore in CNY Hong Kong SCBLHKHH 44700867654 RBOSNL2RTCM Hong Kong with Standard Chartered Bank (Hong Kong) Ltd 266310663 CZK CZECH REPUBLIC CEKOCZPP Ceskoslovenska Obchodni Banka -
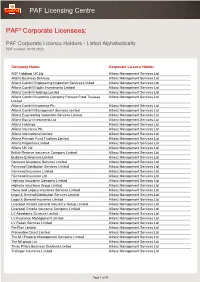
PAF Corporate Licence Holders - Listed Alphabetically PDF Created: 03 09 2020
PAF Licensing Centre PAF ® Corporate Licensees: PAF Corporate Licence Holders - Listed Alphabetically PDF created: 03 09 2020 Company Name. Corporate Licence Holder AGF Holdings UK Ltd Allianz Management Services Ltd Allianz Business Services Allianz Management Services Ltd Allianz Cornhill Engineering Inspection Services Limited Allianz Management Services Ltd Allianz Cornhill Equity Investments Limited Allianz Management Services Ltd Allianz Cornhill Holdings Limited Allianz Management Services Ltd Allianz Cornhill Insurance Company Pension Fund Trustees Allianz Management Services Ltd Limited Allianz Cornhill Insurance Plc Allianz Management Services Ltd Allianz Cornhill Management Services Limited Allianz Management Services Ltd Allianz Engineering Inspection Services Limited Allianz Management Services Ltd Allianz Equity Investments Ltd Allianz Management Services Ltd Allianz Holdings Allianz Management Services Ltd Allianz Insurance Plc Allianz Management Services Ltd Allianz International Limited Allianz Management Services Ltd Allianz Pension Fund Trustees Limited Allianz Management Services Ltd Allianz Properties Limited Allianz Management Services Ltd Allianz UK Ltd Allianz Management Services Ltd British Reserve Insurance Company Limited Allianz Management Services Ltd Buddies Enterprises Limited Allianz Management Services Ltd Domestic Insurance Services Limited Allianz Management Services Ltd Fairmead Distribution Services Limited Allianz Management Services Ltd Fairmead Insurance Limited Allianz Management Services Ltd Fairmead -

RBS Resolution Plan
Logo RBS Public Section RBS Group pic Resolution Plan Pursuant to 12 C.F.R. Parts 217 & 381 and RBS Citizens, N.A. Resolution Plan Pursuant to 12 C.F.R. 360 July 1, 2013 Table of Contents III IntroductionRBS Group pageand RBS 1 Americas page 2 II.CII.BII.A MaterialGlobalPrincipal Operations Supervisory Officers of of RBS AuthoritiesRBS Group Group plcpage page page 4 2 5 IIIII.EII.D RBSCNA SummaryResolution IDI of PlanningPlan Financial and Corporate RBS Information, Citizens Governance, CapitalResolution and Structure PlanMajor page Funding and 10 Processes Sources pagepage 67 III.CIII.BIII.A CoreMaterialSummary Business Entities of Financial Lines page page 11Information, 12 Capital and Major Funding Sources page 13 III.FIII.EIII.D ForeignMembershipDerivative Operations and in HedgingMaterial page Payment,Activities 17 pageClearing 16 and Settlement Systems page 17 III.IIII.HIII.G RBS PrincipalMaterial Citizens' SupervisoryOfficers Resolution page Authorities 17 Planning page Corporate 17 Governance, Structure and III.KIII.JProcesses MaterialHigh-Level page Management Description 18 Information of RBS Citizens' Systems Resolution page 19 Strategy page 20 IV.BIV.AIV Markets CoreMaterial Business & EntitiesInternational Lines page page Banking22 23 Americas page 22 IV.EIV.DIV.C MembershipsDerivativeSummary ofand Financial in Hedging Material Information, Activities Payment, page CapitalClearing 24 and and Major Settlement Funding Systems Sources page page 24 24 IV.HIV.GIV.F ForeignPrincipalMaterial Operations SupervisoryOfficers page page Authorities 25 25 page 25 IV.JIV.I M&IBA'sMaterial ManagementResolution Planning Information Corporate Systems Governance, page 26 Structure and Processes page 25 StrategyIV.K High-Level page 26 Description of Markets & International Banking Americas' Resolution Chapter 1. -

Natwest Markets Plc Cash Ssis
NatWest Markets, London Standard Settlement Instruction (cash) for Foreign Exchange, Money Market, Currency Options, FRAs, Interest Rate & Commodity Swaps, Interest Rate & Commodity Options, Fixed Income, Credit Derivatives and Exchange Traded Futures & Options & Equity Derivatives Transactions. For Equity Derivative business only, settled via DTCC CFM - please note these settlement instructions pertain to DTCC Participant ID 00007701. All accounts are in the name of NatWest Markets Plc Effective from : 22/05/2019 Correspondent Beneficiary Swift ISO CCY Country Swift Correspondent Details Account Number Code Address United Arab AED NBADAEAA First Abu Dhabi Bank AE120354022003002430029 RBOSGB2RTCM Emirates AUD Australia NATAAU3303M National Australia Bank Ltd Melbourne 1803071544500 RBOSGB2RTCM BBD Barbados BNBABBBB Barbados National Bank Bridgetown 028042192002 RBOSGB2RTCM BGN Bulgaria RZBBBGSF Raiffeisenbank AD Sofia BG93RZBB91551030526107 RBOSGB2RTCM BHD Bahrain NBOBBHBM National Bank Of Bahrain Manama BH48 NBOB 0000 0099628864 RBOSGB2RTCM BMD Bermuda BNTBBMHM Bank of NT Butterfield & Son Hamilton 060 1644010020 RBOSGB2RTCM BWP Botswana BARCBWGX Barclays Bank of Botswana, Gaborone 1002227 RBOSGB2RTCM CAD Canada ROYCCAT2 Royal Bank of Canada Toronto 09591 100 314 4 RBOSGB2RTCM For MT103 ONLY use IBAN CH260023023004042505H CHF Switzerland UBSWCHZH80A UBS AG, Zurich RBOSGB2RTCM For MT202 use account number: 02300000040425050000H Care should be taken as this relates to CNH/CNY trading CNY Hong Kong SCBLHKHH and settling offshore in Hong -

National Westminster Bank Plc
National Westminster Bank Plc Primary Credit Analyst: Richard Barnes, London + 44 20 7176 7227; [email protected] Secondary Contact: John Wright, London (44) 20-7176-0520; [email protected] Table Of Contents Major Rating Factors Outlook Rationale Related Criteria Related Research WWW.STANDARDANDPOORS.COM/RATINGSDIRECT NOVEMBER 23, 2020 1 National Westminster Bank Plc Major Rating Factors Global Scale Ratings Issuer Credit Rating A/Negative/A-1 Resolution Counterparty Rating A+/--/A-1 Strengths: Weaknesses • Core subsidiary of NatWest Group plc. • The sharp recession triggered by the COVID-19 pandemic significantly increased credit impairments. • Solid market position across U.K. retail, commercial, and private banking. • Pressure on revenues from the flatter yield curve and reduced customer activity in some product • Supportive capital, funding, and liquidity profiles. segments. • Geographically concentrated in the U.K. WWW.STANDARDANDPOORS.COM/RATINGSDIRECT NOVEMBER 23, 2020 2 National Westminster Bank Plc Outlook S&P Global Ratings' negative outlook on National Westminster Bank Plc (NWB) mirrors that on ultimate parent NatWest Group plc (NWG; previously named The Royal Bank of Scotland Group plc). It reflects downside risks to the group's asset quality and earnings from the economic and market impact of the COVID-19 pandemic. Although we view positively NWG's robust balance sheet profile and the unprecedented fiscal and monetary response, an extended economic downturn could further increase impairment losses and weaken revenues over our two-year outlook horizon. Our ratings on NWB will move in tandem with those on NWG as long as we continue to view NWB as a core subsidiary of the group.