“Reject the Evidence of Your Eyes and Ears”: Deepfakes and the Law of Virtual Replicants
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Strong Case for a New START a National Security Briefing Memo
A Strong Case for a New START A National Security Briefing Memo Max Bergmann and Samuel Charap April 6, 2010 What is New START and why do we need it? New START, the agreement between the United States and Russia on a successor to the Strategic Arms Reduction Treaty, is a historic achievement that will increase the United States’ safety and security. It will help us move beyond the outdated strategic approaches of the Cold War and reduce the threat of nuclear war, and marks a significant step in advancing President Barack Obama’s vision of a world without nuclear weapons. It also shows that his policy of constructive engagement with Russia is working. New START strengthens and modernizes the original START Treaty that President Ronald Reagan initiated in 1982 and George H.W. Bush signed in 1991. That agreement significantly reduced the number of nuclear weapons and launchers, but it also embodied Reagan’s favorite Russian proverb “trust but verify” by establishing an extensive verifica- tion and monitoring system to ensure compliance. This system helped build trust and mutual confidence that decreased the unimaginable consequences of а conflict between the world’s only nuclear superpowers. Yet President George W. Bush’s reckless policies left this cornerstone of nuclear stability’s fate in doubt. Bush effectively cut off relations between the United States and Russia on nuclear issues by unilaterally pulling out of the Anti-Ballistic Missile Treaty and refusing to engage in negotiations on a successor to START even though it was set to expire less than a year after he left office. -

Images and Dilemmas in International Relations
Introduction Man State System Security Dilemma Conclusion Images and Dilemmas in International Relations Dustin Tingley [email protected] Department of Government, Harvard University Introduction Man State System Security Dilemma Conclusion Introduction Three images of IR I Man I State I System Introduction Man State System Security Dilemma Conclusion Man Man Introduction Man State System Security Dilemma Conclusion Man Man I Motivations, dispositions, pathologies of individuals explains international affairs I \Human nature" matters I Quests for power/status essential because that is what individuals care about Associated with scholars like Hobbes, Morgenthau (at times), Rosen, and Tingley Introduction Man State System Security Dilemma Conclusion Man Man I Motivations, dispositions, pathologies of individuals explains international affairs I \Human nature" matters I Quests for power/status essential because that is what individuals care about Associated with scholars like Hobbes, Morgenthau (at times), Rosen, and Tingley Introduction Man State System Security Dilemma Conclusion Man Man I Motivations, dispositions, pathologies of individuals explains international affairs I \Human nature" matters I Quests for power/status essential because that is what individuals care about Associated with scholars like Hobbes, Morgenthau (at times), Rosen, and Tingley Introduction Man State System Security Dilemma Conclusion Man Man I Motivations, dispositions, pathologies of individuals explains international affairs I \Human nature" matters I Quests -

Joe Rosochacki - Poems
Poetry Series Joe Rosochacki - poems - Publication Date: 2015 Publisher: Poemhunter.com - The World's Poetry Archive Joe Rosochacki(April 8,1954) Although I am a musician, (BM in guitar performance & MA in Music Theory- literature, Eastern Michigan University) guitarist-composer- teacher, I often dabbled with lyrics and continued with my observations that I had written before in the mid-eighties My Observations are mostly prose with poetic lilt. Observations include historical facts, conjecture, objective and subjective views and things that perplex me in life. The Observations that I write are more or less Op. Ed. in format. Although I grew up in Hamtramck, Michigan in the US my current residence is now in Cumby, Texas and I am happily married to my wife, Judy. I invite to listen to my guitar works www.PoemHunter.com - The World's Poetry Archive 1 A Dead Hand You got to know when to hold ‘em, know when to fold ‘em, Know when to walk away and know when to run. You never count your money when you're sittin at the table. There'll be time enough for countin' when the dealins' done. David Reese too young to fold, David Reese a popular jack of all trades when it came to poker, The bluffing, the betting, the skill that he played poker, - was his ace of his sleeve. He played poker without deuces wild, not needing Jokers. To bad his lungs were not flushed out for him to breathe, Was is the casino smoke? Or was it his lifestyle in general? But whatever the circumstance was, he cashed out to soon, he had gone to see his maker, He was relatively young far from being too old. -

Into the Promised Land Daily Discipleship Guide SPRING 2019 | VOL
THE GOSPEL PROJECT Into the Promised Land Daily Discipleship Guide SPRING 2019 | VOL. 3 | ESV Daily DiscipleshipDaily Guide ESV SPRING 2019 © 2019 LifeWay Christian Resources God’s Word to You A Life Worth Dying For In the beginning, God created all things good. With the making of humankind as male and female, He even declared His creation to be very good. Paradise was the location; abundant life was the experience, that is, until the taint of sin covered the world through the rebellion of Adam and Eve against their Creator. As a result, humanity lost its paradise and was separated from the God who created all things good. Death was God’s warning for disobedience, and death became the reality—the death of living apart from God (sin), the death of life (physical death), and the death of eternal separation from God’s goodness (spiritual death). But the God of all good things was not finished. He called a people to Himself to be a light to the world. He gave them His holy expectations that they should follow them. He made provision for sin through sacrifices. And even when His people continued to rebel against Him, He promised life from death. In comes Jesus, the Son of God sent into the world to make all things new. “In him was life, and that life was the light of men” (John 1:4). “Full of grace and truth,” Jesus obeyed all of the Father’s holy expectations (1:14). He is “the Lamb of God, who takes away the sin of the world!” (1:29). -

Hardball Diplomacy and Ping-Pong Politics
University of Massachusetts Amherst ScholarWorks@UMass Amherst Masters Theses 1911 - February 2014 2004 Hardball diplomacy and ping-pong politics: Cuban baseball, Chinese table tennis, and the diplomatic use of sport during the Cold War Matthew .J Noyes University of Massachusetts Amherst Follow this and additional works at: https://scholarworks.umass.edu/theses Noyes, Matthew J., "Hardball diplomacy and ping-pong politics: Cuban baseball, Chinese table tennis, and the diplomatic use of sport during the Cold War" (2004). Masters Theses 1911 - February 2014. 1841. Retrieved from https://scholarworks.umass.edu/theses/1841 This thesis is brought to you for free and open access by ScholarWorks@UMass Amherst. It has been accepted for inclusion in Masters Theses 1911 - February 2014 by an authorized administrator of ScholarWorks@UMass Amherst. For more information, please contact [email protected]. HARDBALL DIPLOMACY AND PING-PONG POLITICS: CUBAN BASEBALL, CHINESE TABLE TENNIS, AND THE DIPLOMATIC USE OF SPORT DURING THE COLD WAR A Thesis Presented by Matthew J. Noyes Submitted to the Graduate School of the University of Massachusetts Amherst in partial fulfillment of the requirements for the degree of Master of Arts May 2004 Department of History © Copyright by Matthew J. Noyes 2004 All Rights Reserved HARDBALL DIPLOMACY AND PING-PONG POLITICS: CUBAN BASEBALL, CHINESE TABLE TENNIS AND THE DIPLOMATIC USE OF SPORT DURING THE COLD WAR A Thesis Presented by Matthew J. Noyes Approved as to style and content by Ronald Story, Chair Jane TVl. Rausch, Member Laura Lovett, Member David Glassberg, Chair Department of History DEDICATION To my parents, never say thank you enough for all you have done for ACKNOWLEDGEMENTS I owe a deep debt of gratitude to a number of people without whom this thesis would never have been completed. -

New Start Joint Statement from December 2009
Joint Statement by the President of the United States of America and the President of the ... Page 1 of 3 Home • Briefing Room • Statements & Releases The White House Office of the Press Secretary For Immediate Release December 04, 2009 Joint Statement by the President of the United States of America and the President of the Russian Federation on the Expiration of the Strategic Arms Reduction Treaty (START) Recognizing our mutual determination to support strategic stability between the United States of America and the Russian Federation, we express our commitment, as a matter of principle, to continue to work together in the spirit of the START Treaty following its expiration, as well as our firm intention to ensure that a new treaty on strategic arms enter into force at the earliest possible date. http://www.whitehouse.gov/the-press-office/joint-statement-president-united-states-americ... 6/14/2010 Joint Statement by the President of the United States of America and the President of the ... Page 2 of 3 Home Briefing Room Issues The Administration A H The White House Your Weekly Address Civil Rights President Barack Obama Blog Speeches & Remarks Defense Vice President Joe Biden H Photos & Videos Press Briefings Disabilities First Lady Michelle Obama P F Photo Galleries Statements & Releases Economy Dr. Jill Biden T Video Presidential Actions Education The Cabinet Featured Legislation Energy & Environment White House Staff T Live Streams R Podcasts Nominations & Ethics Executive Office of the Appointments President E Family O Disclosures Other Advisory Boards Fiscal Responsibility C Foreign Policy A Health Care W Homeland Security W Immigration W Poverty T Rural Seniors & Social Security Service Taxes Technology Urban Policy Veterans Women Additional Issues http://www.whitehouse.gov/the-press-office/joint-statement-president-united-states-americ.. -

President Obama's Foreign Policy Vision: Defining the Obama Doctrine Based On: the Obama Doctrine: Hindering American Foreign
President Obama’s Foreign Policy Vision: Defining the Obama Doctrine Based on: The Obama Doctrine: Hindering American Foreign Policy, The Heritage Foundation’s Lecture Event featuring Dr. Kim Holmes and Dr. Henry Nau, September 30, 2010. Defining the Obama Doctrine, Its Pitfalls, and How to Avoid Them by Kim Holmes, Ph.D., and James Carafano, Ph.D., Published by The Heritage Foundation, September 1, 2010 Obama’s Foreign Policy by Henry Nau, Published by Hoover Institution, Policy Review, Number 160, September 29, 2010 What Are the Key Tenets of the Obama Doctrine? By Kim Holmes, Ph.D. and James Carafano, Ph.D. Published online at The Heritage Foundation (no date provided) Almost two years into his term, President Obama had hoped to improve America’s standing in the world by crafting a foreign policy vastly different from his predecessor’s. His statements and actions demonstrate a doctrine that sees America less as “the exceptional nation” than as an “equal partner,” one nation among many. Characteristics of his policies include a heightened emphasis on multilateralism, an apologetic attitude toward the past, a more restrained role on the global stage, and an atmosphere of mutual respect toward oppressive autocracies. Examining the principles and policies advanced thus far by the Obama Administration, Professor Henry Nau and former Assistant Secretary of State Kim R. Holmes analyzed whether the unfolding Obama Doctrine has in fact improved America’s standing in the world and our national interests According to Dr. Holmes and Dr. Nau, President Obama has “laid out in his public statements, the tenets of a doctrine that, if enacted, would enable his Administration to remake America as one nation among many, with no singular claim either to responsibility or exceptionalism. -

A Supercut of Supercuts: Aesthetics, Histories, Databases
A Supercut of Supercuts: Aesthetics, Histories, Databases PRACTICE RESEARCH MAX TOHLINE ABSTRACT CORRESPONDING AUTHOR: Max Tohline The genealogies of the supercut, which extend well past YouTube compilations, back Independent scholar, US to the 1920s and beyond, reveal it not as an aesthetic that trickled from avant-garde [email protected] experimentation into mass entertainment, but rather the material expression of a newly-ascendant mode of knowledge and power: the database episteme. KEYWORDS: editing; supercut; compilation; montage; archive; database TO CITE THIS ARTICLE: Tohline, M. 2021. A Supercut of Supercuts: Aesthetics, Histories, Databases. Open Screens, 4(1): 8, pp. 1–16. DOI: https://doi.org/10.16995/os.45 Tohline Open Screens DOI: 10.16995/os.45 2 Full Transcript: https://www.academia.edu/45172369/Tohline_A_Supercut_of_Supercuts_full_transcript. Tohline Open Screens DOI: 10.16995/os.45 3 RESEARCH STATEMENT strong patterning in supercuts focuses viewer attention toward that which repeats, stoking uncritical desire for This first inklings of this video essay came in the form that repetition, regardless of the content of the images. of a one-off blog post I wrote seven years ago (Tohline While critical analysis is certainly possible within the 2013) in response to Miklos Kiss’s work on the “narrative” form, the supercut, broadly speaking, naturally gravitates supercut (Kiss 2013). My thoughts then comprised little toward desire instead of analysis. more than a list; an attempt to add a few works to Armed with this conclusion, part two sets out to the prehistory of the supercut that I felt Kiss and other discover the various roots of the supercut with this supercut researchers or popularizers, like Tom McCormack desire-centered-ness, and other pragmatics, as a guide. -
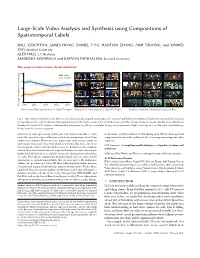
Large-Scale Video Analysis and Synthesis Using Compositions of Spatiotemporal Labels
Large-Scale Video Analysis and Synthesis using Compositions of Spatiotemporal Labels WILL CRICHTON, JAMES HONG, DANIEL Y FU, HAOTIAN ZHANG, ANH TRUONG, and XINWEI YAO, Stanford University ALEX HALL, UC Berkeley MANEESH AGRAWALA and KAYVON FATAHALIAN, Stanford University This paper is under review, do not distribute! 100 Male Female 75 50 25 0 2010 2012 2014 2016 2018 Percent of total host screen time Percent Host Screen Time (by Gender) on Cable TV News Hillary Clinton Interviews on Cable TV News Hermione Positioned Between Harry and Ron Fig. 1. We compose low-level video labels (faces, human poses, aligned transcripts, etc.) to form high-level spatiotemporal labels that are useful for analysis and synthesis tasks. Left: Understanding representation in the media: screen time of female hosts on cable TV news shows increased steadily since 2010before leveling off around 2015. Center: Understanding time given to political candidates during on-air interviews. Right: Curating shots of the stars fromtheHarry Potter series for use in a supercut. Advances in video processing techniques now make it feasible to auto- in the media, and the evolution of film editing style. We also leverage label matically annotate video collections with basic information about their composition for the video synthesis task of curating source clips for video audiovisual contents. However, basic annotations such as faces, poses, or supercuts. time-aligned transcripts, when considered in isolation, offer only a low-level CCS Concepts: · Computing methodologies → Graphics systems and description of a video’s contents. In this paper we demonstrate that composi- interfaces. tions of these basic annotations are a powerful means to create increasingly higher level labels that are useful for a range of video analysis and synthe- Additional Key Words and Phrases: video processing, video data mining sis tasks. -

Brazilian Magazine About the Electroacoustic Culture
Y, 2015 Y, MA V, V, I - BRAZILIAN MAGAZINE ABOUT THE ELECTROACOUSTIC CULTURE iiiiiiiiiiii iiiiiiiiiiii iiiiiiiiiiii iiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiii iiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiii iiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiii iiiiiiiiiiii iiiiiiiiiiii iiiiiiiiiiii iiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiii iiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiii iiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiii iiiiiiiiiiii iiiiiiiiiiii iiiiiiiiiiii iiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiii iiiiiiiiiiiiiiiiiiiiiiii iiiiiiiiiiiiiiiiiiiiiiii iiiiiiiiiiiiiiiiiiiiiiii iiiiiiiiiiiiiiiiiiiiiiii iiiiiiiiiiii iiiiiiiiiiii iiiiiiiiiiii iiiiiiiiiiiiiiiiiiiiiiii This linda-iv we’re presenting now is comprised And if in linda-i we stopped by Sweden in iiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiii iiiiiiiiiiii iiiiiiiiiiii iiiiiiiiiiii iiiiiiiiiiii iiiiiiiiiiii iiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiii iiiiiiiiiiiiiiiiiiiiiiii iiiiiiiiiiiiiiiiiiiiiiii iiiiiiiiiiii iiiiiiiiiiii iiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiii of articles and visual works published in the a conversation with Eva Sidén and Jens iiiiiiiiiiiiiiiiiiiiiiii iiiiiiiiiiii iiiiiiiiiiii FOREWORD iiiiiiiiiiii iiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiiii iiiiiiiiiiiiiiiiiiiiiiii iiiiiiiiiiii iiiiiiiiiiii iiiiiiiiiiii iiiiiiiiiiiiiiiiiiiiiiii Hedman and in linda-ii we got a taste of the iiiiiiiiiiii iiiiiiiiiiii iiiiiiiiiiiiiiiiiiiiiiii iiiiiiiiiiii iiiiiiiiiiii iiiiiiiiiiii experimental music scene in Russia, we close iiiiiiiiiiii -

Russian Strategic Intentions
APPROVED FOR PUBLIC RELEASE Russian Strategic Intentions A Strategic Multilayer Assessment (SMA) White Paper May 2019 Contributing Authors: Dr. John Arquilla (Naval Postgraduate School), Ms. Anna Borshchevskaya (The Washington Institute for Near East Policy), Dr. Belinda Bragg (NSI, Inc.), Mr. Pavel Devyatkin (The Arctic Institute), MAJ Adam Dyet (U.S. Army, J5-Policy USCENTCOM), Dr. R. Evan Ellis (U.S. Army War College Strategic Studies Institute), Mr. Daniel J. Flynn (Office of the Director of National Intelligence (ODNI)), Dr. Daniel Goure (Lexington Institute), Ms. Abigail C. Kamp (National Consortium for the Study of Terrorism and Responses to Terrorism (START)), Dr. Roger Kangas (National Defense University), Dr. Mark N. Katz (George Mason University, Schar School of Policy and Government), Dr. Barnett S. Koven (National Consortium for the Study of Terrorism and Responses to Terrorism (START)), Dr. Jeremy W. Lamoreaux (Brigham Young University- Idaho), Dr. Marlene Laruelle (George Washington University), Dr. Christopher Marsh (Special Operations Research Association), Dr. Robert Person (United States Military Academy, West Point), Mr. Roman “Comrade” Pyatkov (HAF/A3K CHECKMATE), Dr. John Schindler (The Locarno Group), Ms. Malin Severin (UK Ministry of Defence Development, Concepts and Doctrine Centre (DCDC)), Dr. Thomas Sherlock (United States Military Academy, West Point), Dr. Joseph Siegle (Africa Center for Strategic Studies, National Defense University), Dr. Robert Spalding III (U.S. Air Force), Dr. Richard Weitz (Center for Political-Military Analysis at the Hudson Institute), Mr. Jason Werchan (USEUCOM Strategy Division & Russia Strategic Initiative (RSI)) Prefaces Provided By: RDML Jeffrey J. Czerewko (Joint Staff, J39), Mr. Jason Werchan (USEUCOM Strategy Division & Russia Strategic Initiative (RSI)) Editor: Ms. -

The Disinformation Age
Steven Livingston W. LanceW. Bennett EDITED BY EDITED BY Downloaded from terms of use, available at https://www.cambridge.org/core/product/1F4751119C7C4693E514C249E0F0F997THE DISINFORMATION AGE https://www.cambridge.org/core Politics, and Technology, Disruptive Communication in the United States the United in https://www.cambridge.org/core/terms . IP address: 170.106.202.126 . , on 27 Sep 2021 at 12:34:36 , subject to the Cambridge Core Downloaded from https://www.cambridge.org/core. IP address: 170.106.202.126, on 27 Sep 2021 at 12:34:36, subject to the Cambridge Core terms of use, available at https://www.cambridge.org/core/terms. https://www.cambridge.org/core/product/1F4751119C7C4693E514C249E0F0F997 The Disinformation Age The intentional spread of falsehoods – and attendant attacks on minorities, press freedoms, and the rule of law – challenge the basic norms and values upon which institutional legitimacy and political stability depend. How did we get here? The Disinformation Age assembles a remarkable group of historians, political scientists, and communication scholars to examine the historical and political origins of the post-fact information era, focusing on the United States but with lessons for other democracies. Bennett and Livingston frame the book by examining decades-long efforts by political and business interests to undermine authoritative institutions, including parties, elections, public agencies, science, independent journalism, and civil society groups. The other distinguished scholars explore the historical origins and workings of disinformation, along with policy challenges and the role of the legacy press in improving public communication. This title is also available as Open Access on Cambridge Core. W. Lance Bennett is Professor of Political Science and Ruddick C.