Redalyc.Exploratory Data Analysis in the Context of Data Mining And
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
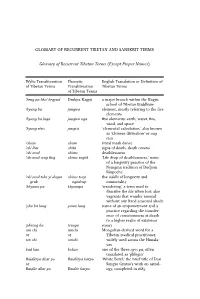
Glossary of Recurrent Tibetan and Sanskrit Terms
GLOSSARY OF RECURRENT TIBETAN AND SANSKRIT TERMS Glossary of Recurrent Tibetan Terms (Except Proper Names) Wylie Transliteration Phonetic English Translation or Defijinition of of Tibetan Terms Transliteration Tibetan Terms of Tibetan Terms ’brug pa bka’ brgyud Drukpa Kagyü a major branch within the Kagyü school of Tibetan Buddhism ’byung ba jungwa element, mostly referring to the fijive elements ’byung ba lnga jungwa nga fijive elements: earth, water, fijire, wind, and space ’byung rtsis jungtsi ‘elemental calculation,’ also known as ‘Chinese divination’ or nag rtsis ’cham cham ritual mask dance ’chi ltas chitä signs of death, death omens ’chi med chime deathlessness ’chi med srog thig chime sogtik ‘Life drop of deathlessness,’ name of a longevity practice of the Nyingma tradition of Dudjom Rinpoche ’chi med tshe yi dngos chime tseyi the siddhi of longevity and grub ngödrup immortality ’khyams pa khyampa ‘wandering,’ a term used to describe the bla when lost; also vagrants that wander around without any fijixed seasonal abode ’pho ba lung powa lung name of an empowerment and a practice regarding the transfer- ence of consciousness at death to a higher realm of existence ’phreng ba trenga rosary am chi amchi Mongolian-derived word for a or or Tibetan medical practitioner, em chi emchi widely used across the Himala- yas bad kan bekan one of the three nyes pa, often translated as ‘phlegm’ Baidūrya dkar po Baidūrya karpo ‘White Beryl,’ the brief title of Desi or Sangye Gyatso’s work on astrol- Baiḍūr dkar po Baidūr karpo ogy, completed in 1685 -

+1. Introduction 2. Cyrillic Letter Rumanian Yn
MAIN.HTM 10/13/2006 06:42 PM +1. INTRODUCTION These are comments to "Additional Cyrillic Characters In Unicode: A Preliminary Proposal". I'm examining each section of that document, as well as adding some extra notes (marked "+" in titles). Below I use standard Russian Cyrillic characters; please be sure that you have appropriate fonts installed. If everything is OK, the following two lines must look similarly (encoding CP-1251): (sample Cyrillic letters) АабВЕеЗКкМНОопРрСсТуХхЧЬ (Latin letters and digits) Aa6BEe3KkMHOonPpCcTyXx4b 2. CYRILLIC LETTER RUMANIAN YN In the late Cyrillic semi-uncial Rumanian/Moldavian editions, the shape of YN was very similar to inverted PSI, see the following sample from the Ноул Тестамент (New Testament) of 1818, Neamt/Нямец, folio 542 v.: file:///Users/everson/Documents/Eudora%20Folder/Attachments%20Folder/Addons/MAIN.HTM Page 1 of 28 MAIN.HTM 10/13/2006 06:42 PM Here you can see YN and PSI in both upper- and lowercase forms. Note that the upper part of YN is not a sharp arrowhead, but something horizontally cut even with kind of serif (in the uppercase form). Thus, the shape of the letter in modern-style fonts (like Times or Arial) may look somewhat similar to Cyrillic "Л"/"л" with the central vertical stem looking like in lowercase "ф" drawn from the middle of upper horizontal line downwards, with regular serif at the bottom (horizontal, not slanted): Compare also with the proposed shape of PSI (Section 36). 3. CYRILLIC LETTER IOTIFIED A file:///Users/everson/Documents/Eudora%20Folder/Attachments%20Folder/Addons/MAIN.HTM Page 2 of 28 MAIN.HTM 10/13/2006 06:42 PM I support the idea that "IA" must be separated from "Я". -

DR. ISAACS ENDS 15 YEARS ·At P9stf: by Irwin Witty Special to the Commentator
' -Good Luck . :. .·:. :. ·-~-- on :. · ~ Finals • .,I. .' ·' •• -- ~ ~ .., ••.,. ~ • Official Undergi:aduate :J~·ewspapef of Yeshiva College •. ,,._/ • : VOLUME XXXYI I NEW YORK CITY, .THURS~AY, JU~E-4, · 1953 . : ,. DR. ISAACS ENDS 15 YEARS ·At P9Stf: By Irwin Witty Special to the Commentator The resignation of Dr. Moses Legis Isaacs, Dean of Y eshitva College, eJ;f ective Sep tember I, 1953, was revealed by Dr. Samuel Belkin, President of:i the-University. Dr. Isaacs' resignation terminates 15 years of teen years. You may i remember that I served as a member of the Executivie Committee of Yeshiva College service as administrator of the College, 11 years I . ., under your chairmanship during the administration of my of which he served in the capacity of dean, and late predecessor, the sainted Dr. Bernard Revel of blessed comes at the end of 25 years of instruction as memory. I say in all sincerity that I never met a man a 01e01her of the college faculty. No im.01ediate more honest, sincere, and self-effacing than you. · successor has been ·named. "I can readily understand, however, thlt a position Dr. Belkin also announced that he expects of a dean-at best-is a very difficult one r;ndeed, it is Dr. Isaacs to remain with the faculty in the ca almo~t ~possible to satisfy a faculty, a student body, and alunµii. • pacity of Professor of Chemistry. "You Will always be remembered in the annals of In his letter to Dr. Is~cs, dated June 1, the Yeshiva College for having been greatly· instrumen~ in president wrote : . -

Speaking Russian
05_149744 ch01.qxp 7/26/07 6:07 PM Page 5 Chapter 1 I Say It How? Speaking Russian In This Chapter ᮣ Understanding the Russian alphabet ᮣ Pronouncing words properly ᮣ Discovering popular expressions elcome to Russian! Whether you want to read Wa Russian menu, enjoy Russian music, or just chat it up with your Russian friends, this is the begin- ning of your journey. In this chapter, you get all the letters of the Russian alphabet, discover the basic rules of Russian pronunciation, and say some popular Russian expressions and idioms. Looking at the Russian Alphabet If you’re like most English speakers, you probably think that the Russian alphabet is the most challenging aspect of picking up the language. But not to worry. The Russian alphabet isn’t as hard as you think. COPYRIGHTED MATERIAL From A to Ya: Making sense of Cyrillic The Russian alphabet is based on the Cyrillic alpha- bet, which was named after the ninth-century Byzantine monk, Cyril. But throughout this book, we convert all the letters into familiar Latin symbols, which are the same symbols we use in the English 05_149744 ch01.qxp 7/26/07 6:07 PM Page 6 6 Russian Phrases For Dummies alphabet. This process of converting from Cyrillic to Latin letters is known as transliteration. We list the Cyrillic alphabet here in case you’re adventurous and brave enough to prefer reading real Russian instead of being fed with the ready-to-digest Latin version of it. And even if you don’t want to read the real Russian, check out Table 1-1 to find out what the whole fuss is about regarding the notorious “Russian alphabet.” Notice that, in most cases, a transliterated letter corresponds to the way it’s actually pronounced. -

3. Summarizing Distributions
3. Summarizing Distributions A. Central Tendency 1. What is Central Tendency 2. Measures of Central Tendency 3. Median and Mean 4. Additional Measures 5. Comparing measures B. Variability 1. Measures of Variability C. Shape 1. Effects of Transformations 2. Variance Sum Law I D. Exercises Descriptive statistics often involves using a few numbers to summarize a distribution. One important aspect of a distribution is where its center is located. Measures of central tendency are discussed first. A second aspect of a distribution is how spread out it is. In other words, how much the numbers in the distribution vary from one another. The second section describes measures of variability. Distributions can differ in shape. Some distributions are symmetric whereas others have long tails in just one direction. The third section describes measures of the shape of distributions. The final two sections concern (1) how transformations affect measures summarizing distributions and (2) the variance sum law, an important relationship involving a measure of variability. 123 What is Central Tendency? by David M. Lane and Heidi Ziemer Prerequisites • Chapter 1: Distributions • Chapter 2: Stem and Leaf Displays Learning Objectives 1. Identify situations in which knowing the center of a distribution would be valuable 2. Give three different ways the center of a distribution can be defined 3. Describe how the balance is different for symmetric distributions than it is for asymmetric distributions. What is “central tendency,” and why do we want to know the central tendency of a group of scores? Let us first try to answer these questions intuitively. Then we will proceed to a more formal discussion. -

Language Specific Peculiarities Document for Halh Mongolian As Spoken in MONGOLIA
Language Specific Peculiarities Document for Halh Mongolian as Spoken in MONGOLIA Halh Mongolian, also known as Khalkha (or Xalxa) Mongolian, is a Mongolic language spoken in Mongolia. It has approximately 3 million speakers. 1. Special handling of dialects There are several Mongolic languages or dialects which are mutually intelligible. These include Chakhar and Ordos Mongol, both spoken in the Inner Mongolia region of China. Their status as separate languages is a matter of dispute (Rybatzki 2003). Halh Mongolian is the only Mongolian dialect spoken by the ethnic Mongolian majority in Mongolia. Mongolian speakers from outside Mongolia were not included in this data collection; only Halh Mongolian was collected. 2. Deviation from native-speaker principle No deviation, only native speakers of Halh Mongolian in Mongolia were collected. 3. Special handling of spelling None. 4. Description of character set used for orthographic transcription Mongolian has historically been written in a large variety of scripts. A Latin alphabet was introduced in 1941, but is no longer current (Grenoble, 2003). Today, the classic Mongolian script is still used in Inner Mongolia, but the official standard spelling of Halh Mongolian uses Mongolian Cyrillic. This is also the script used for all educational purposes in Mongolia, and therefore the script which was used for this project. It consists of the standard Cyrillic range (Ux0410-Ux044F, Ux0401, and Ux0451) plus two extra characters, Ux04E8/Ux04E9 and Ux04AE/Ux04AF (see also the table in Section 5.1). 5. Description of Romanization scheme The table in Section 5.1 shows Appen's Mongolian Romanization scheme, which is fully reversible. -

TLD: Сайт Script Identifier: Cyrillic Script Description: Cyrillic Unicode (Basic, Extended-A and Extended-B) Version: 1.0 Effective Date: 02 April 2012
TLD: сайт Script Identifier: Cyrillic Script Description: Cyrillic Unicode (Basic, Extended-A and Extended-B) Version: 1.0 Effective Date: 02 April 2012 Registry: сайт Registry Contact: Iliya Bazlyankov <[email protected]> Tel: +359 8 9999 1690 Website: http://www.corenic.org This document presents a character table used by сайт Registry for IDN registrations in Cyrillic script. The policy disallows IDN variants, but prevents registration of names with potentially similar characters to avoid any user confusion. U+002D;U+002D # HYPHEN-MINUS -;- U+0030;U+0030 # DIGIT ZERO 0;0 U+0031;U+0031 # DIGIT ONE 1;1 U+0032;U+0032 # DIGIT TWO 2;2 U+0033;U+0033 # DIGIT THREE 3;3 U+0034;U+0034 # DIGIT FOUR 4;4 U+0035;U+0035 # DIGIT FIVE 5;5 U+0036;U+0036 # DIGIT SIX 6;6 U+0037;U+0037 # DIGIT SEVEN 7;7 U+0038;U+0038 # DIGIT EIGHT 8;8 U+0039;U+0039 # DIGIT NINE 9;9 U+0430;U+0430 # CYRILLIC SMALL LETTER A а;а U+0431;U+0431 # CYRILLIC SMALL LETTER BE б;б U+0432;U+0432 # CYRILLIC SMALL LETTER VE в;в U+0433;U+0433 # CYRILLIC SMALL LETTER GHE г;г U+0434;U+0434 # CYRILLIC SMALL LETTER DE д;д U+0435;U+0435 # CYRILLIC SMALL LETTER IE е;е U+0436;U+0436 # CYRILLIC SMALL LETTER ZHE ж;ж U+0437;U+0437 # CYRILLIC SMALL LETTER ZE з;з U+0438;U+0438 # CYRILLIC SMALL LETTER I и;и U+0439;U+0439 # CYRILLIC SMALL LETTER SHORT I й;й U+043A;U+043A # CYRILLIC SMALL LETTER KA к;к U+043B;U+043B # CYRILLIC SMALL LETTER EL л;л U+043C;U+043C # CYRILLIC SMALL LETTER EM м;м U+043D;U+043D # CYRILLIC SMALL LETTER EN н;н U+043E;U+043E # CYRILLIC SMALL LETTER O о;о U+043F;U+043F -

Robust Shewhart-Type Control Charts for Process Location
UvA-DARE (Digital Academic Repository) Robust control charts in statistical process control Nazir, H.Z. Publication date 2014 Link to publication Citation for published version (APA): Nazir, H. Z. (2014). Robust control charts in statistical process control. General rights It is not permitted to download or to forward/distribute the text or part of it without the consent of the author(s) and/or copyright holder(s), other than for strictly personal, individual use, unless the work is under an open content license (like Creative Commons). Disclaimer/Complaints regulations If you believe that digital publication of certain material infringes any of your rights or (privacy) interests, please let the Library know, stating your reasons. In case of a legitimate complaint, the Library will make the material inaccessible and/or remove it from the website. Please Ask the Library: https://uba.uva.nl/en/contact, or a letter to: Library of the University of Amsterdam, Secretariat, Singel 425, 1012 WP Amsterdam, The Netherlands. You will be contacted as soon as possible. UvA-DARE is a service provided by the library of the University of Amsterdam (https://dare.uva.nl) Download date:27 Sep 2021 Chapter 3 Robust Shewhart-type Control Charts for Process Location This chapter studies estimation methods for the location parameter. Estimation method based on a Phase I analysis as well as several robust location estimators are considered. The Phase I method and estimators are evaluated in terms of their mean squared errors and their effect on the control charts used for real-time process monitoring is assessed. It turns out that the Phase I control chart based on the trimmed trimean far outperforms the existing estimation methods. -

A Measure of Relative Efficiency for Location of a Single Sample Shlomo S
Journal of Modern Applied Statistical Methods Volume 1 | Issue 1 Article 8 5-1-2002 A Measure Of Relative Efficiency For Location Of A Single Sample Shlomo S. Sawilowsky Wayne State University, [email protected] Follow this and additional works at: http://digitalcommons.wayne.edu/jmasm Part of the Applied Statistics Commons, Social and Behavioral Sciences Commons, and the Statistical Theory Commons Recommended Citation Sawilowsky, Shlomo S. (2002) "A Measure Of Relative Efficiency For Location Of A Single Sample," Journal of Modern Applied Statistical Methods: Vol. 1 : Iss. 1 , Article 8. DOI: 10.22237/jmasm/1020254940 Available at: http://digitalcommons.wayne.edu/jmasm/vol1/iss1/8 This Regular Article is brought to you for free and open access by the Open Access Journals at DigitalCommons@WayneState. It has been accepted for inclusion in Journal of Modern Applied Statistical Methods by an authorized editor of DigitalCommons@WayneState. Journal O f Modem Applied Statistical Methods Copyright © 2002 JMASM, Inc. Winter 2002, Vol. 1, No. 1,52-60 1538 - 9472/02/$30.00 A Measure Of Relative Efficiency For Location Of A Single Sample Shlomo S. Sawilowsky Evaluation & Research College of Education Wayne State University The question of how much to trim or which weighting constant to use are practical considerations in applying robust methods such as trimmed means (L-estimators) and Huber statistics (M-estimators). An index of location relative effi ciency (LRE), which is a ratio of the narrowness of resulting confidence intervals, was applied to various trimmed means and Huber M-estimators calculated on seven representative data sets from applied education and psychology research. -

Mwite Baba Malumbano Jana Usiku, Na Yu Alikuwa Bado Na Hasi- Kusikia Sauti Yake Juu Ya Mvua Na Radi, Lakini Alijua Ra
Kwa muda mfupi, Yu alikuwa na hisia za ucheshi. alikuwa amechoka sana! Aliangalia mbele. Nyumbani Je, Lin alikuwa sahihi? Huenda anapaswa kumwita bado kulikuwa mbali. Hakupaswa kumpuuza Roho Baba ili amchukue kwenda nyumbani kabla mitaa Mtakatifu kwa sababu ya hoja ya kijinga. haijafurika maji. Lakini yeye na Baba walikuwa na Yu alisimama ili kusema ombi fupi. Hakuweza Mwite Baba malumbano jana usiku, na Yu alikuwa bado na hasi- kusikia sauti yake juu ya mvua na radi, lakini alijua ra. Hakutaka kumwomba Baba msaada. kwamba Baba wa Mbinguni angeweza kumsikia. Kama nitaendesha kwa nguvu, Yu aliifungua baiskeli yake na kusema kwahe- “Baba wa Mbinguni,” Yu aliomba. “Tafadhali nisai- Yu alifikiria, naweza kufika nyu- ri kwa Lin. Kama nitaendesha kwa nguvu, yeye die nifike nyumbani salama.” Alipomaliza, alihisi ngu- mbani kabla ya mitaa kufurika. alifikiria,naweza kufika nyumbani kabla mitaa vu ya kuendelea. haijafurika. Mwishowe, Yu aliweza kuiona nyumba yake kwe- Na Julie Cornelius- Huang Aliendesha kwa bidii, lakini punde mikono yake nye kilima. Akihisi baridi, kuchoka, na kwa namna (Imetokana na hadithi ya kweli) ilikuwa baridi, nguo zake zilikuwa zimelowa, na aliku- fulani akiwa amepoteza kiatu, Yu alijikokota kupanda Mwandishi anaishi katika Utah, Marekani wa amechoka. Kwa mara nyingine, wazo likamjia la kilima. Alimwona Baba akimngojea nje. Baba aliki- “Changamkeni, kwa kuwa nitawaongoza” (Mafundisho kumwita Baba. Je hisia zilikuwa zimetoka kwa Roho mbia kushuka chini ya kilima kukutana naye, akirusha na Maagano 78:18). Mtakatifu? Wamisionari waliokuwa wamembatiza wali- maji wakati akikimbia. u alitoka nje ya shule iliyosongamana kwenda njia sema kwamba Roho Mtakatifu angeweza kuwa mwo- Wakati Baba alipomfikia, aliweka mikono yake Yya watembea kwa miguu. -

Modification of ANOVA with Various Types of Means
Applied Mathematics and Computational Intelligence Volume 8, No.1, Dec 2019 [77-88] Modification of ANOVA with Various Types of Means Nur Farah Najeeha Najdi1* and Nor Aishah Ahad1 1School of Quantitative Sciences, Universiti Utara Malaysia. ABSTRACT In calculating mean equality for two or more groups, Analysis of Variance (ANOVA) is a popular method. Following the normality assumption, ANOVA is a robust test. A modification to ANOVA is proposed to test the equality of population means. The suggested research statistics are straightforward and are compatible with the generic ANOVA statistics whereby the classical mean is supplemented by other robust means such as geometric mean, harmonic mean, trimean and also trimmed mean. The performance of the modified ANOVAs is then compared in terms of the Type I error in the simulation study. The modified ANOVAs are then applied on real data. The performance of the modified ANOVAs is then compared with the classical ANOVA test in terms of Type I error rate. This innovation enhances the ability of modified ANOVAs to provide good control of Type I error rates. In general, the results were in favor of the modified ANOVAs especially ANOVAT and ANOVATM. Keywords: ANOVA, Geometric Mean, Harmonic Mean, Trimean, Trimmed Mean, Type I Error. 1. INTRODUCTION Analysis of variance (ANOVA) is one of the most used model which can be seen in many fields such as medicine, engineering, agriculture, education, psychology, sociology and biology to investigate the source of the variations. One-way ANOVA is based on assumptions that the normality of the observations and the homogeneity of group variances. -

Modern Robust Data Analysis Methods: Measures of Central Tendency
Psychological Methods Copyright 2003 by the American Psychological Association, Inc. 2003, Vol. 8, No. 3, 254–274 1082-989X/03/$12.00 DOI: 10.1037/1082-989X.8.3.254 Modern Robust Data Analysis Methods: Measures of Central Tendency Rand R. Wilcox H. J. Keselman University of Southern California University of Manitoba Various statistical methods, developed after 1970, offer the opportunity to substan- tially improve upon the power and accuracy of the conventional t test and analysis of variance methods for a wide range of commonly occurring situations. The authors briefly review some of the more fundamental problems with conventional methods based on means; provide some indication of why recent advances, based on robust measures of location (or central tendency), have practical value; and describe why modern investigations dealing with nonnormality find practical prob- lems when comparing means, in contrast to earlier studies. Some suggestions are made about how to proceed when using modern methods. The advances and insights achieved during the last more recent publications provide a decidedly different half century in statistics and quantitative psychology picture of the robustness of conventional techniques. provide an opportunity for substantially improving In terms of avoiding actual Type I error probabilities modern ,(05. ס ␣ ,.psychological research. Recently developed methods larger than the nominal level (e.g can provide substantially more power when the stan- methods and conventional techniques produce similar dard assumptions of