Understanding and Identifying Large-Scale Adaptive Changes from Version Histories
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

KDE 2.0 Development, Which Is Directly Supported
23 8911 CH18 10/16/00 1:44 PM Page 401 The KDevelop IDE: The CHAPTER Integrated Development Environment for KDE by Ralf Nolden 18 IN THIS CHAPTER • General Issues 402 • Creating KDE 2.0 Applications 409 • Getting Started with the KDE 2.0 API 413 • The Classbrowser and Your Project 416 • The File Viewers—The Windows to Your Project Files 419 • The KDevelop Debugger 421 • KDevelop 2.0—A Preview 425 23 8911 CH18 10/16/00 1:44 PM Page 402 Developer Tools and Support 402 PART IV Although developing applications under UNIX systems can be a lot of fun, until now the pro- grammer was lacking a comfortable environment that takes away the usual standard activities that have to be done over and over in the process of programming. The KDevelop IDE closes this gap and makes it a joy to work within a complete, integrated development environment, combining the use of the GNU standard development tools such as the g++ compiler and the gdb debugger with the advantages of a GUI-based environment that automates all standard actions and allows the developer to concentrate on the work of writing software instead of managing command-line tools. It also offers direct and quick access to source files and docu- mentation. KDevelop primarily aims to provide the best means to rapidly set up and write KDE software; it also supports extended features such as GUI designing and translation in con- junction with other tools available especially for KDE development. The KDevelop IDE itself is published under the GNU Public License (GPL), like KDE, and is therefore publicly avail- able at no cost—including its source code—and it may be used both for free and for commer- cial development. -

Historical Dictionary of Sufism
04-655 (1) FM.qxd 4/18/05 12:39 PM Page i HISTORICAL DICTIONARIES OF RELIGIONS, PHILOSOPHIES, AND MOVEMENTS Jon Woronoff, Series Editor 1. Buddhism, by Charles S. Prebish, 1993 2. Mormonism, by Davis Bitton, 1994. Out of print. See No. 32. 3. Ecumenical Christianity, by Ans Joachim van der Bent, 1994 4. Terrorism, by Sean Anderson and Stephen Sloan, 1995. Out of print. See No. 41. 5. Sikhism, by W. H. McLeod, 1995 6. Feminism, by Janet K. Boles and Diane Long Hoeveler, 1995. Out of print. See No. 52. 7. Olympic Movement, by Ian Buchanan and Bill Mallon, 1995. Out of print. See No. 39. 8. Methodism, by Charles Yrigoyen Jr. and Susan E. Warrick, 1996. Out of Print. See No. 57. 9. Orthodox Church, by Michael Prokurat, Alexander Golitzin, and Michael D. Peterson, 1996 10. Organized Labor, by James C. Docherty, 1996. Out of print. See No. 50. 11. Civil Rights Movement, by Ralph E. Luker, 1997 12. Catholicism, by William J. Collinge, 1997 13. Hinduism, by Bruce M. Sullivan, 1997 14. North American Environmentalism, by Edward R. Wells and Alan M. Schwartz, 1997 15. Welfare State, by Bent Greve, 1998 16. Socialism, by James C. Docherty, 1997 17. Bahá’í Faith, by Hugh C. Adamson and Philip Hainsworth, 1998 18. Taoism, by Julian F. Pas in cooperation with Man Kam Leung, 1998 19. Judaism, by Norman Solomon, 1998 20. Green Movement, by Elim Papadakis, 1998 21. Nietzscheanism, by Carol Diethe, 1999 22. Gay Liberation Movement, by Ronald J. Hunt, 1999 23. Islamic Fundamentalist Movements in the Arab World, Iran, and Turkey, by Ahmad S. -

Behavior Based Software Theft Detection, CCS 2009
Behavior Based Software Theft Detection 1Xinran Wang, 1Yoon-Chan Jhi, 1,2Sencun Zhu, and 2Peng Liu 1Department of Computer Science and Engineering 2College of Information Sciences and Technology Pennsylvania State University, University Park, PA 16802 {xinrwang, szhu, jhi}@cse.psu.edu, [email protected] ABSTRACT (e.g., in SourceForge.net there were over 230,000 registered Along with the burst of open source projects, software open source projects as of Feb.2009), software theft has be- theft (or plagiarism) has become a very serious threat to the come a very serious concern to honest software companies healthiness of software industry. Software birthmark, which and open source communities. As one example, in 2005 it represents the unique characteristics of a program, can be was determined in a federal court trial that IBM should pay used for software theft detection. We propose a system call an independent software vendor Compuware $140 million dependence graph based software birthmark called SCDG to license its software and $260 million to purchase its ser- birthmark, and examine how well it reflects unique behav- vices [1] because it was discovered that certain IBM products ioral characteristics of a program. To our knowledge, our contained code from Compuware. detection system based on SCDG birthmark is the first one To protect software from theft, Collberg and Thoborson that is capable of detecting software component theft where [10] proposed software watermark techniques. Software wa- only partial code is stolen. We demonstrate the strength of termark is a unique identifier embedded in the protected our birthmark against various evasion techniques, including software, which is hard to remove but easy to verify. -
![\", 22 \', 22 \(, 31, 32 \), 31, 32 \-, 26 \., 22 \=, 22 \[, 32 \], 32 \ˆ, 21, 22 \`, 22](https://docslib.b-cdn.net/cover/2084/22-22-31-32-31-32-26-22-22-32-32-21-22-22-342084.webp)
\", 22 \', 22 \(, 31, 32 \), 31, 32 \-, 26 \., 22 \=, 22 \[, 32 \], 32 \ˆ, 21, 22 \`, 22
i i i ‘beginlatex’ --- 2018/12/4 --- 23:30 --- page 289 --- #325 i Index Index See Table 2 on page xxx for the meanings of the typographic formatting used here and in the text. \", 22 \ae, 22 \', 22 \affiliation, 42 \(, 31, 32 afm2tfm, 234 \), 31, 32 textbf, 17 \-, 26 Apple Mac \., 22 editor, 189, 194 /p, 236 installation, 189 \=, 22 apt, 190 \@, 162, 164 apt-get, xxvi \[, 32 Aquamacs, 222 \], 32 \arabic, 170 \ˆ, 21, 22 ArcInfo, 96 \`, 22 textbf, 13 \ , 21, 22 array, 85 \arraybackslash, 85 10pt, 37 \arraystretch, 87 11pt, 37 article, 11, 35 12pt, 11, 37 \author, xxx, 42–44, 108, 162 AutoCAD, 95 a4paper, 36, 38 avant, 143 \AA, 22 \aa, 22 b, 100 AbiWord, 175, 177, 178 \b, 22 abstract, 44, 45 babel, 20, 30, 50, 120 \abstractname, 45 textbf, 9 abstracts, 44 textbf, 254 accents, 19 BaKoMa TEX, xxix Acrobat Reader, 185, 194, 222, 258 \baselinestretch, 133 acronym, 126 bbding, 73, 171 \addbibresource, 120 beer, 123 \addcontentsline, 52 lite, 123 \addtocontents, 53 American, 123 \AE, 22 Rogue £ Formatting Information ¢ 289 ¡ i i i i i i i ‘beginlatex’ --- 2018/12/4 --- 23:30 --- page 290 --- #326 i FORMATTING INFORMATION Chocolate Stout, 124 \centering, 29, 85, 87, 148 \begin, 20, 40, 41, 45, 74, 82, cep, 93 163, 180 chancery, 143 \bfseries, 12, 149 textbf, 247 biber, ix, 5, 19, 62, 112–114, 120– \chapter, 47, 48 122, 125 chapter, 170 biber, 247, 249 characters BIBINPUTS, 116 accented, 19 biblatex, 5, 112, 113 ASCII, 267 biblatex, ix, 5, 19, 112–114, 116– math, 31 121 special, 15, 31 biblatex-apa, 114 charmap, 21 biblatex-cheatsheet, 114 charter, -

Family by NEIL SPEARS Requests Contributing Writer Donates VCSD Chancellor Robert C
FEATURES Ughts & Sirens 2 SPORTS Opinion 4 Baseball swi~ away Meet the candidates Features • the competition A.S. presidential profiles 9 Features takes a look at this year's A.S. presidential candidates, Triton baseball went 4-1 over the their slates and independent campaigns - and finds out who Classifieds 12 break, beating CSU Dominguez Hills they are and what they staoo for. page 9 Campus Calendar 11 and Azusa PaCific. P~e 16 UC SAN DIEGO MONDAY, MARCH 11, 2001 VOLU,\IE 109, [ seE I 2003 A.S. ELEOIONS WATCH War advisory group formed Jacobs Appeal Committee to oversee campus climate family By NEIL SPEARS requests Contributing Writer donates VCSD Chancellor Robert C. denied Dynes announced the formation of the pecial Advisory Committee on War Related $110 M Matters on March 19. The goal Committee of me commirree is to advise the chancellor about the impact of Gift part of hears cases of global conflict on the campus community. $1 billion 3 applicants "I want to reassure you that we have developed comprehen By GAELLE FAURE sive plans for enhancing campu fundraising Associate News Editor safety, sustaining campus opera tions, and issuing timely news campalgn Three A.. elections candidates updates," Dynes stated in a who had filed appeals to the elec March 20 campus norice. tions committee Jskll1g to be rein The committee is composed By LISA MAK stated in the race were denied their of a dozen representatives from Staff Writer requests prior to the end of winter different areas of campu opera Irwin Jacobs. former C 'D quarter. -

Rkward: a Comprehensive Graphical User Interface and Integrated Development Environment for Statistical Analysis with R
JSS Journal of Statistical Software June 2012, Volume 49, Issue 9. http://www.jstatsoft.org/ RKWard: A Comprehensive Graphical User Interface and Integrated Development Environment for Statistical Analysis with R Stefan R¨odiger Thomas Friedrichsmeier Charit´e-Universit¨atsmedizin Berlin Ruhr-University Bochum Prasenjit Kapat Meik Michalke The Ohio State University Heinrich Heine University Dusseldorf¨ Abstract R is a free open-source implementation of the S statistical computing language and programming environment. The current status of R is a command line driven interface with no advanced cross-platform graphical user interface (GUI), but it includes tools for building such. Over the past years, proprietary and non-proprietary GUI solutions have emerged, based on internal or external tool kits, with different scopes and technological concepts. For example, Rgui.exe and Rgui.app have become the de facto GUI on the Microsoft Windows and Mac OS X platforms, respectively, for most users. In this paper we discuss RKWard which aims to be both a comprehensive GUI and an integrated devel- opment environment for R. RKWard is based on the KDE software libraries. Statistical procedures and plots are implemented using an extendable plugin architecture based on ECMAScript (JavaScript), R, and XML. RKWard provides an excellent tool to manage different types of data objects; even allowing for seamless editing of certain types. The objective of RKWard is to provide a portable and extensible R interface for both basic and advanced statistical and graphical analysis, while not compromising on flexibility and modularity of the R programming environment itself. Keywords: GUI, integrated development environment, plugin, R. -

Why Be a KDE Project? Martin Klapetek David Edmundson
Why be a KDE Project? Martin Klapetek David Edmundson What is KDE? KDE is not a desktop, it's a community „Community of technologists, designers, writers and advocates who work to ensure freedom for all people through our software“ --The KDE Manifesto What is a KDE Project? Project needs more than just good code What will you get as a KDE Project? Git repository Git repository plus „scratch repos“ (your personal playground) Creating a scratch repo git push –all kde:scratch/username/reponame Git repository plus web interface (using GitPHP) Git repository plus migration from Gitorious.org Bugzilla (the slightly prettier version) Review Board Integration of git with Bugzilla and Review Board Integration of git with Bugzilla and Review Board Using server-side commit hooks ● BUG: 24578 ● CCBUG: 29456 ● REVIEW: 100345 ● CCMAIL: [email protected] Communication tools Mailing lists Wiki pages Forums Single sign-on to all services Official IRC channels #kde-xxxxx (on Freenode) IRC cloak me@kde/developer/mklapetek [email protected] email address Support from sysadmin team Community support Development support Translations (71 translation teams) Testing support (Active Jenkins and EBN servers, plus Quality Team) Project continuation (when you stop developing it) KDE e.V. support Financial and organizational help Trademark security Project's licence defense via FLA Promo support Stories in official KDE News site (Got the Dot?) Your blog aggregated at Planet KDE Promo through social channels Web hosting under kde.org domain Association with one of the best -

KDE Galaxy 4.13
KDE Galaxy 4.13 - Devaja Shah About Me ●3rd Year Alienatic Student at DA- !"# Gandhinagar ●Dot-editor %or KDE &romo "ea' ●Member of KDE e.(. ●&a))ion for Technology# Literature ●+un the Google Developer Group in !olle$e ●-rganizin$ Tea' of KDE Meetup# con%./de.in 14 -/ay, sooooo....... ●Ho1 many of you are %an) of Science Fiction3 ●Astronomy3 ● 0o1 is it Related to KDE3 ●That i) precisely 1hat the talk is about. ●Analogy to $et you to kno1 everythin$ that you should about ● “Galaxy KDE 4.13” 4ait, isn't it 4.14? ●KDE5) late)t ver)ion S! 4.14 6 7ove'ber 8914 ●KDE Soft1are !o',ilation ::.xx ●Significance o% +elea)e) ●- -r$ani.ed# )y)te'atic co',ilation o% %eature) < develo,'ent) ●- 2ive )erie) of relea)e) till date. ●7o Synchronized +elea)e) Any lon$er: ● - KDE 2ra'e1ork) > ?'onthly@ ● - KDE &la)'a > ?3 'onth)@ ● - KDE Ap,lication) ?date ba)ed@ ●Au)t *i/e Ap, (er)ion) But, 1hat am I to do o% the Galaxy 7umber? ●4ork in a "eam ●4ork acros) a Deadline ●-%;ce Space Si'ulation ●Added 'petus %or Deliverin$ your 2eature) ●You 1ork a) a ,art of the C!oreD Developer "ea' ● nstils Discipline ●Better +e),onse# Better 2eedbac/ ●Better Deliverance ●Synchronized 1ork with other C)ea)onedD developer) Enough of the bore....... ●Ho1 do $et started3 ● - Hope you didn't )nooze yesterday ● +!# Subscribe to Mailing Lists ●Mentoring Progra') ●GsoC# Season of KDE, O2W Progra') ●Bootstra,pin$ Training Session) Strap yourself onto the Rocket ●And Blast O%%......... ● ● ● Entered A 4ormhole and Ea,ped into the KDE Galaxy ●No1 what? ●Pick a Planet to nhabit ●But.... -

Manual Do Kexi
Manual do Kexi Esta documentação foi convertida a partir da página Kexi/Handbook da Base de Usuários do KDE em 14/09/2012. Atualizado para o 2.4 pela Equipe de Documentação do KDE Tradução: Marcus Gama Manual do Kexi 2 Conteúdo 1 Introdução 8 2 Fundamentos do Kexi9 2.1 Bancos de dados do Kexi . .9 2.2 Criando um Novo Arquivo de Banco de Dados . 10 2.3 A Janela Principal do Kexi . 12 2.3.1 Elementos principais do aplicativo . 12 2.3.2 Barra de ferramentas em abas . 13 2.3.3 Área do Navegador do Projeto . 13 2.3.4 Área de objetos de bancos de dados aberta / Janelas por abas . 14 2.3.5 Painel do Editor de propriedades . 14 2.4 Abrindo um arquivo de banco de dados do Kexi existente . 15 2.4.1 Abrindo um arquivo de banco de dados na janela Abrir um projeto . 15 2.4.2 Abrindo um arquivo de banco de dados do Kexi existente, clicando no ícone do arquivo .kexi . 16 2.5 Usando a ajuda embutida . 17 3 Criando Bancos de Dados Simples 18 3.1 Introdução . 18 3.2 Desenhar as tabelas do banco de dados . 19 3.2.1 A janela do Desenhador de Tabelas . 19 3.2.1.1 A janela do Desenhador de Tabelas consiste nas seguintes colunas: 19 3.2.1.2 Desenhar a tabela de Pessoas . 19 3.3 Inserir dados nas tabelas . 20 3.3.1 Detalhes Sobre Ações Disponíveis ao Inserir Dados em Tabelas . 21 3.4 Desenhar consultas do banco de dados . -

Authenticity of Aroma Components Enantiomeric Separation and Compound Specific Stable Isotope Analysis
Downloaded from orbit.dtu.dk on: Oct 06, 2021 Authenticity of aroma components Enantiomeric separation and compound specific stable isotope analysis Hansen, Anne-Mette Sølvbjerg Publication date: 2015 Document Version Publisher's PDF, also known as Version of record Link back to DTU Orbit Citation (APA): Hansen, A-M. S. (2015). Authenticity of aroma components Enantiomeric separation and compound specific stable isotope analysis. National Food Institute, Technical University of Denmark. General rights Copyright and moral rights for the publications made accessible in the public portal are retained by the authors and/or other copyright owners and it is a condition of accessing publications that users recognise and abide by the legal requirements associated with these rights. Users may download and print one copy of any publication from the public portal for the purpose of private study or research. You may not further distribute the material or use it for any profit-making activity or commercial gain You may freely distribute the URL identifying the publication in the public portal If you believe that this document breaches copyright please contact us providing details, and we will remove access to the work immediately and investigate your claim. Authenticity of aroma components Enantiomeric separation and compound specific stable isotope analysis Anne-Mette Sølvbjerg Hansen PhD Thesis 2015 Authenticity of aroma components Enantiomeric separation and compound specific stable isotope analysis Anne-Mette Sølvbjerg Hansen August 2015 Authenticity of aroma components Enantiomeric separation and compound specific stable isotope analysis PhD thesis 2015 By Anne-Mette Sølvbjerg Hansen Copyright: National Food Institute, Technical University of Denmark Cover photo: Copyright to the author Published by: Ledelse og Administration, Anker Engelunds Vej 1, Bygning 101 A, 2800 Kgs. -
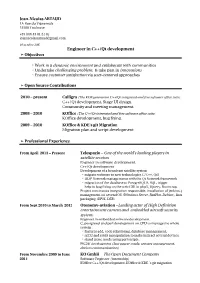
Engineer in C++/Qt Development ➢ Objectives
Jean-Nicolas ARTAUD 1A Rue du Vignemale 31500 Toulouse +33 (0)6.43.01.51.02 [email protected] 10 octobre 1987 Engineer in C++/Qt development ➢ Objectives ◦ Work in a dynamic environment and collaborate with communities ◦ Undertake challenging problems & take part in innovations ◦ Ensure customer satisfaction via user-centered approaches ➢ Open Source Contributions 2010 – present Calligra (The KDE generation C++/Qt integrated and free software office suite) C++/Qt development, Stage UI design. Community and meeting management. 2008 – 2010 KOffice (The C++/Qt integrated and free software office suite) KOffice development, bug fixing. 2009 – 2010 KOffice & KDE's git Migration Migration plan and script development. ➢ Professional Experience From April 2013 – Present Telespazio – One of the world’s leading players in satellite services Engineer in software development. C++/Qt development Development of a broadcast satellite system ◦ migrate software to new technologies C/C++, Qt5 ◦ UDP Network managements with the Qt Network framework ◦ migration of the database to PostgreSQL 9, SQL, trigger ◦ help in bug fixing on the web GUI in php5, JQuery, Bootstrap, Project continuous integration responsible, installation of jenkins, jobs management on several OS (Windows Server, RedHat, Debian), linux project packaging (RPM, DEB) From Sept 2010 to March 2013 Otonomy-aviation –Leading actor of High Definition entertainment camera and embedded aircraft security systems Engineer in embedded software development. C, postgresql and perl development on CPU to manage the whole system : ◦ features add, code refactoring, database management, ◦ rs232 and rs485 manipulation to make interact several devices, ◦ stand alone mode using perl scripts . PIC24f development (low power mode, sensors management, devices communication). -

Proceedings of the 61St International Council for Educational Media And
Proceedings of ICEM&SIIE‘11 Joint Conference EVTux: uma distribuição de Linux para a integração das ferramentas digitais na disciplina de EVT José Alberto Rodrigues Universidade de Aveiro Portugal [email protected] António Moreira Universidade de Aveiro Portugal [email protected] Resumo O EVTux1 é uma distribuição de Linux que tem por base o trabalho de investigação que desenvolvemos sobre a integração de ferramentas digitais na disciplina de Educação Visual e Tecnológica. Após quinze meses de estudo e desenvolvimento do projeto, recensearam- se quase quatrocentas ferramentas digitais passíveis de integração em contexto de Educação Visual e Tecnológica. O EVTux tem pré instaladas todas as aplicações para Linux bem como integradas no browser as ferramentas digitais que não necessitam de instalação e correm diretamente a partir da Web, para além dos mais de trezentos manuais de apoio à utilização dessas ferramentas. O EVTux está disponível em versão live ou dual boot e constitui-se como um poderoso recurso podendo ser uma ferramenta de eleição para os docentes desta disciplina utilizarem em contexto de sala de aula. Palavras-chave: Currículo; Educação; Educação Visual e Tecnológica; EVTdigital; EVTux. 1. Introdução Decorrente da investigação que atualmente desenvolvemos no âmbito do Programa Doutoral em Multimédia em Educação da Universidade de Aveiro intitulado ―Ferramentas Web, Web 2.0 e Software Livre em EVT‖, foram recenseadas e catalogadas cerca de quatrocentas ferramentas digitais passíveis de utilização em contexto de Educação Visual e Tecnológica (EVT), disciplina do 2º Ciclo do Ensino Básico, para abordagem dos diversos conteúdos e áreas de exploração da mesma, integrados em múltiplas Unidades de Trabalho desenvolvidas pelos professores com os seus alunos.