Ramzi Yousef
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Chapter 7 War on Terror
Chapter 7 War on Terror Thou shall not kill – But we will. In July 2005, Ahmed Ressam was sentenced to 22 years of impris- onment after a jury convicted him of an attempt to bomb Los Angeles International Airport on the eve of the millennium. Emphasizing the rule of law in punishing terrorists, US District Judge John C. Coughenour made the following comments during the sentencing hearing: I would like to convey the message that our system works. We did not need to use a secret military tribunal, or detain the defendant indefinitely as an enemy combatant, or deny him the right to coun- sel, or invoke any proceedings beyond those guaranteed by or con- trary to the US Constitution...Despite the fact that Mr. Ressam is not an American citizen and despite the fact that he entered this country intent upon killing American citizens, he received an effec- tive, vigorous defense, and the opportunity to have his guilt or inno- cence determined by a jury of 12 ordinary citizens. Most importantly, all of this occurred in the sunlight of a public trial. There were no secret proceedings, no indefinite detention, no denial of counsel. The tragedy of September 11th shook our sense of security and made us realize that we, too, are vulnerable to acts of terrorism. Unfortunately, some believe that this threat renders our Constitution obsolete. The war on terror is the antithesis of the criminal justice system that Judge Coughenour describes above. The criminal justice sys- tem is the peacetime legal infrastructure to arrest, indict, prose- War on Terror 249 cute, and punish persons accused of committing terrorists acts. -

Highlights of 1997 Accomplishments
Highlights of 1997 Accomplishments Making America Safe • Continued the Department’s firm policy for dealing with terror- ist acts, focusing on deterrence, quick and decisive investiga- tions and prosecutions, and international cooperation to vigor- ously pursue and prosecute terrorists, both domestic and for- eign. • Continued to prosecute the most violent criminal offenders under the Anti-Violent Crime Initiative, forging unprecedented working relationships with members of local communities, State and local prosecutors, and local law enforcement officials. • Focused enforcement operations on the seamless continuum of drug trafficking, using comprehensive investigative techniques to disrupt, dismantle, and destroy trafficking operations ema- nating from Mexico, Colombia, Asia, Africa, and other coun- tries. • Coordinated multijurisdictional and multiagency investigations to immobilize drug trafficking organizations by arresting their members, confiscating their drugs, and seizing their assets. • Continued to eliminate the many criminal enterprises of organized crime families, including the La Cosa Nostra fami- lies and their associates and nontraditional organized crime groups emanating from the former Soviet Bloc and Asia. • Chaired the High-Tech Subgroup of the P8 focusing on interna- tional trap-and-trace procedures and transborder searches, and represented the United States at the Council of Europe’s Com- mittee of Experts on Crime in Cyberspace, which is drafting an international convention on a wide range of high-tech issues. • Promulgated legislation enacted to effect BOP’s takeover of Lorton prison before 2001 and to transfer D.C. parole jurisdic- tion to the U.S. Parole Commission; further consideration and action are expected on a number of crime-related proposals during the second session of Congress. -
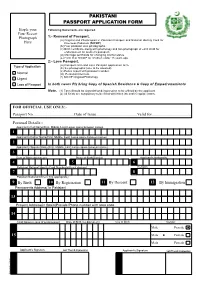
Pakistani Passport Application Form
PAKISTANI PASSPORT APPLICATION FORM Staple your Following Documents are required. Four Recent Photograph 1:- Renewal of Passport. (a) Original and Photocopies of Pakistani Passport and National Identity Card for Here Overseas Pakistani (NICOP) (b( Four passport size photographs. (c) Birth certificate along with photocopy and two photograph of each child for endorsement on mother’s passport. (d) Marriage certificate for changing marital status. (e) Form B or NICOP for children under 18 years age. 2:- Loss Passport. Type of Application (a) Passport form and Loss Passport application form. (b) Six photographs (one to be attested). (c) Police report with passport number. Normal (d) Personal interview. Urgent (f) NICOP Original/Photocopy Loss of Passport In both cases Plz bring Copy of Spanish Residence & Copy of Empadronamiento Note. (1) Form Should be signed/thumb impression to be affixed by the applicant (2) All fields are compulsory to be filled with black ink and in capital letters. FOR OFFICIAL USE ONLY:- Passport No.......................................Date of Issue.......................................Valid for..................................... Personal Details:- Applicant’s Full Name(First, Middle, Last) Leave space between names. 1 Applicant’s Father Name(First, Middle, Last) Leave space between names. 2 Applicant’s Spouse Name(First, Middle, Last) Leave space between names. 3 Date of Birth (dd-mm-yy) Place of Birth(District) Applicant’s Nationality 4 5 6 Pakistani National Identity Card Number(with out dashes) Religion 7 8 -

Psychology of Terrorism
Psychology of Terrorism EDITED BY Bruce Bongar Lisa M. Brown Larry E. Beutler James N. Breckenridge Philip C. Zimbardo OXFORD USIVERSITT PRESS War Versus Justice in Response to Terrorist Attacks Competing Frames and Their Implications Clark McCauley Often lost m d~scussionof the September 11, 2001, terrorism. "On September the 11th. entmies of attacks on the World Trad? Center (WTC) 1s the freedom committed an act of war against our coun- fact that a very nmllar attack, v;lth similar moti- t~.. Our war on terror begns with a1 Qaeda. but vation and related perpetrators. occurred eight it does not end there. It m~llnot end until evey years earlier On February 16. 1993, a truck bomb terrorist group of global reach has been found. in the basement parking garage of the WTC killed stopped and defeated" (Bush, 2001) SLX.injured hundreds, and damaged property to \Vithin the rhetonc of war., however. here has [he extent of half a billion dollars. The bomb was been frequent recourse to the rhetoric of cnminal designed to topple one of the towers into the other justice. "Whether we bring our enemes to lusuce or and to bring both tolvers down. The man behind justice to our enemies, justice will be done. .\Ye thls plan, Ramzi Yousef, noted regretfully that if he wdl come together to gve law enforc?ment the had had a little more funding his design would additional toois it needs to track dorm terror here have succeeded and killed tens of thousands (Krk. at home" (Bush, 2001; White House Press Office. -

Consolidated UN Security Council Sanctions List Last Updated on 14 October 2015
The Consolidated UN Security Council Sanctions List Last updated on 14 October 2015 Consolidated United Nations Security Council Sanctions List Generated on: 14 October 2015 Composition of the List The list consists of the two sections specified below: A. Individuals B. Entities and other groups Information about de-listing may be found on the Committee's website at: http://www.un.org/sc/committees /dfp.shtml and http://www.un.org/sc/committees/1267/delisting.shtml . A. Individuals TAi.155 Name: 1: ABDUL AZIZ 2: ABBASIN 3: na 4: na 56 ا:Name (original script): 123456 879 Title: na Designation: na DOB: 1969 POB: Sheykhan Village, Pirkowti Area, Orgun District, Paktika Arovince, Afghanistan Good quality a.k.a.: Abdul ABiB Mahsud Low quality a.k.a.: na Nationality: na Passport no.: na National identification no.: na Address: na Listed on: 4 Oct. 2011 (amended on 22 Apr. 2013 ) Other information: Fey commander in the Haqqani Net ork (TAe.012) under SiraIuddin Jallaloudine Haqqani (TAi.144). Taliban Shadow Governor for Orgun District, Paktika Province as of early 2010. Operated a training camp for non-Afghan fighters in Paktika Province. Has been involved in the transport of weapons to Afghanistan. QDi.012 Name: 1: NASHWAN 2: A-. AL-RA//AM 3: A-. AL--AMI 4: na TUVاﻥ 56 ا:Rﺯاق 56 ا:Name (original script): NO45 Title: na Designation: na DOB: 1961 POB: Cosul, IraH Good quality a.k.a.: a) Abdal Al-Hadi Al-Iraqi b) Abd Al-Hadi Al-Iraqi Low quality a.k.a.: Abu Abdallah Nationality: Iraqi Passport no.: na National identification no.: na Address: na Listed on: 6 Oct. -

Foreign Terrorist Organizations
Order Code RL32223 CRS Report for Congress Received through the CRS Web Foreign Terrorist Organizations February 6, 2004 Audrey Kurth Cronin Specialist in Terrorism Foreign Affairs, Defense, and Trade Division Huda Aden, Adam Frost, and Benjamin Jones Research Associates Foreign Affairs, Defense, and Trade Division Congressional Research Service ˜ The Library of Congress Foreign Terrorist Organizations Summary This report analyzes the status of many of the major foreign terrorist organizations that are a threat to the United States, placing special emphasis on issues of potential concern to Congress. The terrorist organizations included are those designated and listed by the Secretary of State as “Foreign Terrorist Organizations.” (For analysis of the operation and effectiveness of this list overall, see also The ‘FTO List’ and Congress: Sanctioning Designated Foreign Terrorist Organizations, CRS Report RL32120.) The designated terrorist groups described in this report are: Abu Nidal Organization (ANO) Abu Sayyaf Group (ASG) Al-Aqsa Martyrs Brigade Armed Islamic Group (GIA) ‘Asbat al-Ansar Aum Supreme Truth (Aum) Aum Shinrikyo, Aleph Basque Fatherland and Liberty (ETA) Communist Party of Philippines/New People’s Army (CPP/NPA) Al-Gama’a al-Islamiyya (Islamic Group, IG) HAMAS (Islamic Resistance Movement) Harakat ul-Mujahidin (HUM) Hizballah (Party of God) Islamic Movement of Uzbekistan (IMU) Jaish-e-Mohammed (JEM) Jemaah Islamiya (JI) Al-Jihad (Egyptian Islamic Jihad) Kahane Chai (Kach) Kurdistan Workers’ Party (PKK, KADEK) Lashkar-e-Tayyiba -

Pakistan's Institutions
Pakistan’s Institutions: Pakistan’s Pakistan’s Institutions: We Know They Matter, But How Can They We Know They Matter, But How Can They Work Better? Work They But How Can Matter, They Know We Work Better? Edited by Michael Kugelman and Ishrat Husain Pakistan’s Institutions: We Know They Matter, But How Can They Work Better? Edited by Michael Kugelman Ishrat Husain Pakistan’s Institutions: We Know They Matter, But How Can They Work Better? Essays by Madiha Afzal Ishrat Husain Waris Husain Adnan Q. Khan, Asim I. Khwaja, and Tiffany M. Simon Michael Kugelman Mehmood Mandviwalla Ahmed Bilal Mehboob Umar Saif Edited by Michael Kugelman Ishrat Husain ©2018 The Wilson Center www.wilsoncenter.org This publication marks a collaborative effort between the Woodrow Wilson International Center for Scholars’ Asia Program and the Fellowship Fund for Pakistan. www.wilsoncenter.org/program/asia-program fffp.org.pk Asia Program Woodrow Wilson International Center for Scholars One Woodrow Wilson Plaza 1300 Pennsylvania Avenue NW Washington, DC 20004-3027 Cover: Parliament House Islamic Republic of Pakistan, © danishkhan, iStock THE WILSON CENTER, chartered by Congress as the official memorial to President Woodrow Wilson, is the nation’s key nonpartisan policy forum for tackling global issues through independent research and open dialogue to inform actionable ideas for Congress, the Administration, and the broader policy community. Conclusions or opinions expressed in Center publications and programs are those of the authors and speakers and do not necessarily reflect the views of the Center staff, fellows, trustees, advisory groups, or any individuals or organizations that provide financial support to the Center. -

Surprise, Intelligence Failure, and Mass Casualty Terrorism
SURPRISE, INTELLIGENCE FAILURE, AND MASS CASUALTY TERRORISM by Thomas E. Copeland B.A. Political Science, Geneva College, 1991 M.P.I.A., University of Pittsburgh, 1992 Submitted to the Graduate Faculty of The Graduate School of Public and International Affairs in partial fulfillment of the requirements for the degree of Doctor of Philosophy University of Pittsburgh 2006 UNIVERSITY OF PITTSBURGH FACULTY OF ARTS AND SCIENCES This dissertation was presented by Thomas E. Copeland It was defended on April 12, 2006 and approved by Davis Bobrow, Ph.D. Donald Goldstein, Ph.D. Dennis Gormley Phil Williams, Ph.D. Dissertation Director ii © 2006 Thomas E. Copeland iii SURPRISE, INTELLIGENCE FAILURE, AND MASS CASUALTY TERRORISM Thomas E. Copeland, PhD University of Pittsburgh, 2006 This study aims to evaluate whether surprise and intelligence failure leading to mass casualty terrorism are inevitable. It explores the extent to which four factors – failures of public policy leadership, analytical challenges, organizational obstacles, and the inherent problems of warning information – contribute to intelligence failure. This study applies existing theories of surprise and intelligence failure to case studies of five mass casualty terrorism incidents: World Trade Center 1993; Oklahoma City 1995; Khobar Towers 1996; East African Embassies 1998; and September 11, 2001. A structured, focused comparison of the cases is made using a set of thirteen probing questions based on the factors above. The study concludes that while all four factors were influential, failures of public policy leadership contributed directly to surprise. Psychological bias and poor threat assessments prohibited policy makers from anticipating or preventing attacks. Policy makers mistakenly continued to use a law enforcement approach to handling terrorism, and failed to provide adequate funding, guidance, and oversight of the intelligence community. -

Al-Jedda-Preliminary-Issue-Judgment
Appeal No: SC/66/2008 Hearing Dates: 2nd – 4th and 7th July 2014 Date of Judgment: 18th July 2014 SPECIAL IMMIGRATION APPEALS COMMISSION Before: THE HONOURABLE MR JUSTICE FLAUX UPPER TRIBUNAL JUDGE WARR SIR STEWART ELDON Hilal Abdul Razzaq Ali AL-JEDDA APPELLANT and SECRETARY OF STATE FOR THE HOME DEPARTMENT RESPONDENT For the Appellant: Mr Tom Hickman and Ms Samantha Knights Instructed by: Public Interest Lawyers For the Respondent: Mr Jonathan Swift QC, Ms Karen Steyn QC and Mr Rupert Jones Instructed by: The Treasury Solicitor JUDGMENT Page 1 The Honourable Mr Justice Flaux: Introduction 1. On 1 November 2013, the Respondent (referred to hereafter as “the Secretary of State” made an order in exercise of the power under section 40(2) of the British Nationality Act 1981 as amended (“the 1981 Act”) depriving the appellant (referred to hereafter as “Mr Al-Jedda”) of his British citizenship. Mr Al-Jedda appeals against that order to the Commission pursuant to section 2B of the Special Immigration Appeals Commission Act 1997 (“the 1997 Act”). 2. By Order of Irwin J dated 13 February 2014, the Commission ordered the determination of the following preliminary issues: (1) Did the deprivation order made by the Secretary of State on 1 November 2013 render Mr Al-Jedda stateless contrary to section 40(4) of the 1981 Act (including the sub-issues of issue estoppel and abuse of process which are referred to in the Scott Schedule and the Grounds of Appeal)? (2) Is the Secretary of State required to provide a minimum level of disclosure and information about the case against Mr Al-Jedda pursuant to the requirements of the European Convention on Human Rights and/or European Union law? (3) Was the deprivation of citizenship unfair by failing to provide Mr Al- Jedda with an adequate opportunity to make representations to the Secretary of State before it was made? 3. -

Central Intelligence Agency (CIA) Freedom of Information Act (FOIA) Case Log October 2000 - April 2002
Description of document: Central Intelligence Agency (CIA) Freedom of Information Act (FOIA) Case Log October 2000 - April 2002 Requested date: 2002 Release date: 2003 Posted date: 08-February-2021 Source of document: Information and Privacy Coordinator Central Intelligence Agency Washington, DC 20505 Fax: 703-613-3007 Filing a FOIA Records Request Online The governmentattic.org web site (“the site”) is a First Amendment free speech web site and is noncommercial and free to the public. The site and materials made available on the site, such as this file, are for reference only. The governmentattic.org web site and its principals have made every effort to make this information as complete and as accurate as possible, however, there may be mistakes and omissions, both typographical and in content. The governmentattic.org web site and its principals shall have neither liability nor responsibility to any person or entity with respect to any loss or damage caused, or alleged to have been caused, directly or indirectly, by the information provided on the governmentattic.org web site or in this file. The public records published on the site were obtained from government agencies using proper legal channels. Each document is identified as to the source. Any concerns about the contents of the site should be directed to the agency originating the document in question. GovernmentAttic.org is not responsible for the contents of documents published on the website. 1 O ct 2000_30 April 2002 Creation Date Requester Last Name Case Subject 36802.28679 STRANEY TECHNOLOGICAL GROWTH OF INDIA; HONG KONG; CHINA AND WTO 36802.2992 CRAWFORD EIGHT DIFFERENT REQUESTS FOR REPORTS REGARDING CIA EMPLOYEES OR AGENTS 36802.43927 MONTAN EDWARD GRADY PARTIN 36802.44378 TAVAKOLI-NOURI STEPHEN FLACK GUNTHER 36810.54721 BISHOP SCIENCE OF IDENTITY FOUNDATION 36810.55028 KHEMANEY TI LEAF PRODUCTIONS, LTD. -

Staff Statement No
Outline of the 9/11 Plot Staff Statement No. 16 Members of the Commission, your staff is prepared to report its preliminary findings regarding the conspiracy that produced the September 11 terrorist attacks against the United States. We remain ready to revise our understanding of this subject as our work continues. Dietrich Snell, Rajesh De, Hyon Kim, Michael Jacobson, John Tamm, Marco Cordero, John Roth, Douglas Greenburg, and Serena Wille did most of the investigative work reflected in this statement. We are fortunate to have had access to the fruits of a massive investigative effort by the Federal Bureau of Investigation and other law enforcement agencies, as well intelligence collection and analysis from the Central Intelligence Agency, the National Security Agency, the State Department, and the Department of Defense. Much of the account in this statement reflects assertions reportedly made by various 9/11 conspirators and captured al Qaeda members while under interrogation. We have sought to corroborate this material as much as possible. Some of this material has been inconsistent. We have had to make judgment calls based on the weight and credibility of the evidence. Our information on statements attributed to such individuals comes from written reporting; we have not had direct access to any of them. Plot Overview Origins of the 9/11 Attacks The idea for the September 11 attacks appears to have originated with a veteran jihadist named Khalid Sheikh Mohammed (KSM). A Kuwaiti from the Baluchistan region of Pakistan, KSM grew up in a religious family and claims to have joined the Muslim Brotherhood at the age of 16. -

The Open Door How Militant Islamic Terrorists Entered and Remained in the United States, 1993-2001 by Steven A
Center for Immigration Studies The Open Door How Militant Islamic Terrorists Entered and Remained in the United States, 1993-2001 By Steven A. Camarota Center for Immigration Studies Center for 1 Center Paper 21 Center for Immigration Studies About the Author Steven A. Camarota is Director of Research at the Center for Immigration Studies in Wash- ington, D.C. He holds a master’s degree in political science from the University of Pennsyl- vania and a Ph.D. in public policy analysis from the University of Virginia. Dr. Camarota has testified before Congress and has published widely on the political and economic ef- fects of immigration on the United States. His articles on the impact of immigration have appeared in both academic publications and the popular press including Social Science Quarterly, The Washington Post, The Chicago Tribune, Campaigns and Elections, and National Review. His most recent works published by the Center for Immigration Studies are: The New Ellis Islands: Examining Non-Traditional Areas of Immigrant Settlement in the 1990s, Immigration from Mexico: Assessing the Impact on the United States, The Slowing Progress of Immigrants: An Examination of Income, Home Ownership, and Citizenship, 1970-2000, Without Coverage: Immigration’s Impact on the Size and Growth of the Population Lacking Health Insurance, and Reconsidering Immigrant Entrepreneurship: An Examination of Self- Employment Among Natives and the Foreign-born. About the Center The Center for Immigration Studies, founded in 1985, is a non-profit, non-partisan re- search organization in Washington, D.C., that examines and critiques the impact of immi- gration on the United States.