Cutting Edge Microsoft Browser Security – from People Who Owned It
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

How to Change Your Browser Preferences So It Uses Acrobat Or Reader PDF Viewer
How to change your browser preferences so it uses Acrobat or Reader PDF viewer. If you are unable to open the PDF version of the Emergency Action Plan, please use the instructions below to configure your settings for Firefox, Google Chrome, Apple Safari, Internet Explorer, and Microsoft Edge. Firefox on Windows 1. Choose Tools > Add-ons. 2. In the Add-ons Manager window, click the Plugins tab, then select Adobe Acrobat or Adobe Reader. 3. Choose an appropriate option in the drop-down list next to the name of the plug-in. 4. Always Activate sets the plug-in to open PDFs in the browser. 5. Ask to Activate prompts you to turn on the plug-in while opening PDFs in the browser. 6. Never Activate turns off the plug-in so it does not open PDFs in the browser. Select the Acrobat or Reader plugin in the Add-ons Manager. Firefox on Mac OS 1. Select Firefox. 2. Choose Preferences > Applications. 3. Select a relevant content type from the Content Type column. 4. Associate the content type with the application to open the PDF. For example, to use the Acrobat plug-in within the browser, choose Use Adobe Acrobat NPAPI Plug-in. Reviewed 2018 How to change your browser preferences so it uses Acrobat or Reader PDF viewer. Chrome 1. Open Chrome and select the three dots near the address bar 2. Click on Settings 3. Expand the Advanced settings menu at the bottom of the page 4. Under the Privacy and security, click on Content Settings 5. Find PDF documents and click on the arrow to expand the menu 6. -
Quick Guide Page | 1
Quick Guide Page | 1 Contents Welcome to Windows 10 ................................................................................................................................................................................................... 3 Key innovations ...................................................................................................................................................................................................................... 3 Cortana ................................................................................................................................................................................................................................. 3 Microsoft Edge .................................................................................................................................................................................................................. 4 Gaming & Xbox ................................................................................................................................................................................................................ 5 Built-in apps ....................................................................................................................................................................................................................... 7 Enterprise-grade secure and fast ................................................................................................................................................................................... -
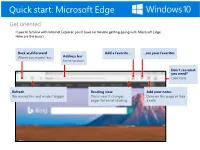
Quick Start: Microsoft Edge
Quick start: Microsoft Edge Get oriented If you’re familiar with Internet Explorer, you’ll have no trouble getting going with Microsoft Edge. Here are the basics. Back and Forward Add a favorite... ...see your favorites Where you expect ‘em. Address bar Same location. Don’t see what you need? Look here. Refresh Reading view Add your notes We moved this and made it bigger. This is new. It changes Draw on this page or take pages for easier reading. a note. Quick start: Microsoft Edge Microsoft Edge makes finding the needles in the internet’s haystack faster and easier. Find answers quickly by typing your question in the address bar. If we’ve got the answer, we’ll show it to you or make a suggestion. 1. Ask your question in the Address bar 2. Find your answer here 3. See other options here Quick start: Microsoft Edge If you’ve got a lot of web reading to do, switch to Reading view and give your eyes a break. Before After Need more contrast or a bigger font? To change settings, select More in the upper-right corner, select Settings, scroll to the Reading section and play with the options. Quick start: Microsoft Edge If you don’t always have internet access, add webpages that you want to read later to your Reading List and you’ll be able to get to them offline, too. 1. Add things to the list 2. Open the list Open a webpage > select the Favorites Hub button > Reading list . button > Reading list > Add. -

Microsoft Patches Were Evaluated up to and Including CVE-2020-1587
Honeywell Commercial Security 2700 Blankenbaker Pkwy, Suite 150 Louisville, KY 40299 Phone: 1-502-297-5700 Phone: 1-800-323-4576 Fax: 1-502-666-7021 https://www.security.honeywell.com The purpose of this document is to identify the patches that have been delivered by Microsoft® which have been tested against Pro-Watch. All the below listed patches have been tested against the current shipping version of Pro-Watch with no adverse effects being observed. Microsoft Patches were evaluated up to and including CVE-2020-1587. Patches not listed below are not applicable to a Pro-Watch system. 2020 – Microsoft® Patches Tested with Pro-Watch CVE-2020-1587 Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability CVE-2020-1584 Windows dnsrslvr.dll Elevation of Privilege Vulnerability CVE-2020-1579 Windows Function Discovery SSDP Provider Elevation of Privilege Vulnerability CVE-2020-1578 Windows Kernel Information Disclosure Vulnerability CVE-2020-1577 DirectWrite Information Disclosure Vulnerability CVE-2020-1570 Scripting Engine Memory Corruption Vulnerability CVE-2020-1569 Microsoft Edge Memory Corruption Vulnerability CVE-2020-1568 Microsoft Edge PDF Remote Code Execution Vulnerability CVE-2020-1567 MSHTML Engine Remote Code Execution Vulnerability CVE-2020-1566 Windows Kernel Elevation of Privilege Vulnerability CVE-2020-1565 Windows Elevation of Privilege Vulnerability CVE-2020-1564 Jet Database Engine Remote Code Execution Vulnerability CVE-2020-1562 Microsoft Graphics Components Remote Code Execution Vulnerability -
Download Edge Browser for Windows 2012 Download Microsoft Edge Offline Installer for Windows 10, 11
download edge browser for windows 2012 Download Microsoft Edge Offline Installer for Windows 10, 11. Download Microsoft Edge's offline installer to install the web browser on multiple computers. Well, if you have been reading tech news for a while, then you might be well aware of the new Edge browser. Microsoft Edge is a new browser released by Microsoft, and it’s based on Chromium Project. The great thing about the new Microsoft Edge browser is that it uses the same Blink engine used by Google Chrome. The Blink engine is also used by some other popular web browsers like Opera, Vivaldi, etc. Microsoft Edge browser comes preinstalled with the latest builds of Windows 10. However, it was missing on the older Windows version such as Windows 7. Windows 8, and Windows 8.1. If you want to use the new Microsoft Edge on an older version of Windows, you need to use the Microsoft Edge installer. Microsoft Edge Installer (Online) Well, Microsoft Edge provides an online installer for downloading Microsoft Edge on the older version of Windows 10. The online installer is small in size, but it requires an active internet connection to download all available files. The good thing about Microsoft Edge online installer is that it downloads the Edge browser’s up-to-date files on your system . So, you don’t need to check for the available updates manually. To download the online installer, check out the download links. Microsoft Edge Offline Installer. If you have multiple computers, then running an online installer would be a waste of time and bandwidth. -

Silk Test 20.5
Silk Test 20.5 Silk4J User Guide Micro Focus The Lawn 22-30 Old Bath Road Newbury, Berkshire RG14 1QN UK http://www.microfocus.com © Copyright 1992-2019 Micro Focus or one of its affiliates. MICRO FOCUS, the Micro Focus logo and Silk Test are trademarks or registered trademarks of Micro Focus or one of its affiliates. All other marks are the property of their respective owners. 2019-10-23 ii Contents Welcome to Silk4J 20.5 ....................................................................................10 Licensing Information ......................................................................................11 Silk4J ................................................................................................................ 12 Do I Need Administrator Privileges to Run Silk4J? ........................................................... 12 Best Practices for Using Silk4J ........................................................................................ 12 Automation Under Special Conditions (Missing Peripherals) ............................................13 Silk Test Product Suite ...................................................................................................... 14 What's New in Silk4J ........................................................................................16 Save Time and Costs with Service Virtualization for Mobile Devices ............................... 16 Enhance Security with Java-based Encryption ................................................................. 16 Usability Enhancements -

Policy Center Requirements Operating Systems: the Following Operating Systems Are Recommended to Access Policy Center
Policy Center Requirements Operating Systems: The following operating systems are recommended to access Policy Center. Operating Systems Supported: Microsoft Windows Vista SP2 Microsoft Windows 7 Microsoft Windows 8 Microsoft Windows 10 * *There are some known issues with these Operating Systems. For more details, see ‘Known Issues’ section below. Internet Browsers: The following browsers are required to access Policy Center. If you currently use an older Microsoft browser than listed, or a non-Microsoft browser, you may receive other errors or experience other unknown issues. Browsers Supported: 32-bit Microsoft Internet Explorer 7+ 32-bit Microsoft Internet Explorer 8+ * 32-bit Microsoft Internet Explorer 9+ * 32-bit Microsoft Internet Explorer 10+ * 32-bit Microsoft Internet Explorer 11+ * *There are some known issues with these browsers. For more details, see ‘Known Issues’ section below. Additional Requirements:** Adobe Reader version 7 or higher (or a similar PDF viewer) Guidewire Document Assistant ActiveX plug-in **Required to view system generated documents. Microsoft Office 2007 or 2010 is suggested to view all other documents. You are responsible for uploading policy documents to Policy Center before and after submission of the application. Upload only what is needed. Most file types are acceptable. All documents will be retained according to TWIA’s document retention policy. Claims Center Requirements Internet Browsers: To provide the best user experience it is recommended to use browsers that support HTML5 & CSS3. Claims Center is a web application accessed through a web browser. There are tiered levels of support for web browsers: Tier 1 includes browsers used in testing environments. Tier 2 includes browsers that can present the core functionality and content, but may not be pixel perfect and may not to perform as well as Tier 1 browsers. -

System Requirements
System Requirements MPulse Means Easy Installation™ Microsoft .NET = World Class Software MPulse Software Tiers and System Requirements MPulse Maintenance Software is a true “n-tier” application, built on Microsoft’s market-leading .NET Framework. As a Microsoft Client Tier Silver ISV Partner, we work closely with Microsoft to bring you Desktop and Laptop Computers Requirements reliable, scalable applications that meet the needs of even the most demanding users. • Current version of Mozilla Firefox, Google Chrome, or Microsoft Edge; Internet Explorer v11 Client Tier Desktop and Laptop Computers Recommendations • Microsoft Windows device running Windows 8 (32 or 64 bit) or higher • Monitor with 1024 x 768 or higher resolution • A minimum of 8 GB of RAM (more recommended) • Internet connection of at least 1 Mbps Mobile Devices • All current Apple devices Hosted or Locally Installed? • All current Android devices Customers who choose MPulse’s Application Hosting Service (AHS) can be sure all their back-end system requirements are met. Business Tier AHS, managed by Rackspace, is free to MPulse Maintenance and The business tier includes the application. It also contains advanced Support Program (MSP) subscribers. For a local install, you’ll need customization and security tools to facilitate communication and to meet the minimum business tier and data tier requirements in data flow through the system. We highly recommend the use of a addition to those for the client tier. dedicated application server for optimal performance. Database Options • Internet connection of at least 1 Mbps MPulse uses Microsoft SQL Server as its underlying database. If you • Microsoft Windows Server 2012 or higher don’t have Microsoft SQL Server licenses, don’t worry. -

X41 D-SEC Gmbh Dennewartstr
Browser Security White PAPER Final PAPER 2017-09-19 Markus VERVIER, Michele Orrù, Berend-Jan WEVER, Eric Sesterhenn X41 D-SEC GmbH Dennewartstr. 25-27 D-52068 Aachen Amtsgericht Aachen: HRB19989 Browser Security White PAPER Revision History Revision Date Change Editor 1 2017-04-18 Initial Document E. Sesterhenn 2 2017-04-28 Phase 1 M. VERVIER, M. Orrù, E. Sesterhenn, B.-J. WEVER 3 2017-05-19 Phase 2 M. VERVIER, M. Orrù, E. Sesterhenn, B.-J. WEVER 4 2017-05-25 Phase 3 M. VERVIER, M. Orrù, E. Sesterhenn, B.-J. WEVER 5 2017-06-05 First DrAFT M. VERVIER, M. Orrù, E. Sesterhenn, B.-J. WEVER 6 2017-06-26 Second DrAFT M. VERVIER, M. Orrù, E. Sesterhenn, B.-J. WEVER 7 2017-07-24 Final DrAFT M. VERVIER, M. Orrù, E. Sesterhenn, B.-J. WEVER 8 2017-08-25 Final PAPER M. VERVIER, M. Orrù, E. Sesterhenn, B.-J. WEVER 9 2017-09-19 Public Release M. VERVIER, M. Orrù, E. Sesterhenn, B.-J. WEVER X41 D-SEC GmbH PAGE 1 OF 196 Contents 1 ExECUTIVE Summary 7 2 Methodology 10 3 Introduction 12 3.1 Google Chrome . 13 3.2 Microsoft Edge . 14 3.3 Microsoft Internet Explorer (IE) . 16 4 Attack Surface 18 4.1 Supported Standards . 18 4.1.1 WEB TECHNOLOGIES . 18 5 Organizational Security Aspects 21 5.1 Bug Bounties . 21 5.1.1 Google Chrome . 21 5.1.2 Microsoft Edge . 22 5.1.3 Internet Explorer . 22 5.2 Exploit Pricing . 22 5.2.1 ZERODIUM . 23 5.2.2 Pwn2Own . -

Microsoft Edge + Internet Explorer Mode Getting Started Guide Table of Contents
Microsoft Edge + Internet Explorer mode Getting Started guide Table of contents Microsoft Edge is replacing Internet Explorer �����������������������3 Transition and timeline ���������������������������������������������������������������4 Plan for deployment �������������������������������������������������������������������5 Internet Explorer mode ��������������������������������������������������������������6 Deploy and update ���������������������������������������������������������������������8 Configure ��������������������������������������������������������������������������������������9 Resources ������������������������������������������������������������������������������������ 10 Appendix Channels overview �������������������������������������������������������������������12 Microsoft Mechanics video series �����������������������������������������13 Microsoft Edge is replacing Internet Explorer Microsoft Edge with Internet Explorer mode offers built-in legacy browser support and is officially replacing the Internet Explorer 11 desktop application, which will be retired and go out of support on June 15, 2022. Moving to Microsoft Edge helps your organization to... Improve compatibility Get the dual engine advantage. The Chromium project provides world-class compatibility for modern websites and Internet Explorer mode provides compatibility for your legacy Internet Explorer-based websites and applications. Streamline productivity Instead of bouncing back and forth between multiple browsers, streamline to a single browser for -

Delphi 2015 SP3-AP4 System Requirements
Delphi 2015 SP3-AP4 System Requirements amadeus-hospitality.com Index Delphi 2015 SP3-AP4 System Requirements ...................................................... 3 Additional Server Requirements ........................................................................ 4 Optional Delphi Components ............................................................................. 5 LAN Workstation Requirements ......................................................................... 5 Remote Workstation Connectivity (Workstations Not on a LAN) ...................... 7 Integration Requirements .................................................................................. 7 Remote Access for Services and Support ........................................................... 7 Additional Information for Customers ............................................................... 8 Amadeus IT Group and its affiliates subsidiaries affiliates and Amadeus GroupIT its and 2017 © Development Last update: 03/09/2017 Page 2 of 8 amadeus-hospitality.com Delphi 2015 SP3-AP4 System Requirements Users Category Minimum Server Hardware Requirement Up to 15 Processor 2.0 GHz Quad Core Memory 4 GB Disk Subsystem 20 GB free space RAID controller (optional) Up to 25 Processor 2.0 GHz Quad Core Memory 4 GB Disk Subsystem Data Drive (RAID 1): 40 GB free space Backup Drive : (RAID 0) (optional)i RAID controller Up to 50 Processor 2.0 GHz Quad Core Memory 8 GB Disk Subsystem Drive(s) for SQL data and log files (RAID 5): 40 GB free space Backup Drive: (RAID 0) (optional)1 -

Concur Travel & Expense Supported Configurations – Client Version
Concur Travel & Expense Supported Configurations Last Revised: September 22, 2021 Contents Supported Configurations.............................................................................................3 Section 1: About Concur Travel & Expense ..................................................................3 Section 2: Technology Requirements and Considerations............................................3 Support for AJAX ........................................................................................................ 3 Proxy Setting ............................................................................................................. 3 DNS Resolution .......................................................................................................... 4 Site Restrictions and Filtering ...................................................................................... 4 Older Browsers and Operating Systems......................................................................... 4 Section 3: Ports ...........................................................................................................4 Section 4: Bandwidth ..................................................................................................5 Section 5: Microsoft JavaScript Engine ........................................................................5 Updating the Jscript.dll File .......................................................................................... 5 Section 6: Certificate Verification ................................................................................5