Worksheet C.1 Introduction to Cryptology: Substitution Ciphers
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Words Should Be Fun: Scrabble As a Tool for Language Preservation in Tuvan and Other Local Languages1
Vol. 4 (2010), pp. 213-230 http://nflrc.hawaii.edu/ldc/ http://hdl.handle.net/10125/4480 Words should be fun: Scrabble as a tool for language preservation in Tuvan and other local languages1 Vitaly Voinov The University of Texas at Arlington One small but practical way of empowering speakers of an endangered language to maintain their language’s vitality amidst a climate of rapid globalization is to introduce a mother-tongue version of the popular word game Scrabble into their society. This paper examines how versions of Scrabble have been developed and used for this purpose in various endangered or non-prestige languages, with a focus on the Tuvan language of south Siberia, for which the author designed a Tuvan version of the game. Playing Scrab- ble in their mother tongue offers several benefits to speakers of an endangered language: it presents a communal approach to group literacy, promotes the use of a standardized orthography, creates new opportunities for intergenerational transmission of the language, expands its domains of usage, and may heighten the language’s external and internal prestige. Besides demonstrating the benefits of Scrabble, the paper also offers practical suggestions concerning both linguistic factors (e.g., choice of letters to be included, cal- culation of letter frequencies, dictionary availability) and non-linguistic factors (board de- sign, manufacturing, legal issues, etc.) relevant to producing Scrabble in other languages for the purpose of revitalization. 1. INTRODUCTION.2 The past several decades have seen globalization penetrating even the most remote corners of the world, bringing with them popular American exports such as Coca-Cola and Hollywood movies. -

Questions These Questions Are in a Specific Order. 1. What Is Scrabble
Questions Re: The Game of Scrabble Radio Interview - 14th March 2019 - 2AIRFM These questions are in a specific order. 1. What is Scrabble? 2:30 sec. 2. Who invented it? 1:40 sec 3. Why is it called Scrabble? 30 sec 4. Why play Scrabble? 1:30 sec 5. Why should I join a Scrabble Club? 2:30 sec 6. What dictionary should I use? 3:00 mins. 7. Why are there weird words in the Scrabble Dictionary? 3:00 mins 8. What should I know? 2:30 sec 9. What is a good score in Scrabble? 1 min 10. How can I improve my Scrabble score? 1 min 11. How did you get interested in Scrabble? 1 min That’s eleven questions the volume has been turned up to 11! These are some suggestions for songs to be played between breaks:- Words of love – the Beatles G.L.O.R.I.A. - Them featuring Van Morrison Words - the Bee Gees V.A.C.A.T.I.O.N. - Connie Francis Words - Neil Young D.I.V.O.R.C.E. - Tammy Wynette https://soundcloud.com/user147680538/community-interview-14th-march-2019 1. What is Scrabble? The game of Scrabble has been around since 1933 in one form or another in Western society, so I’ve always thought that everyone would have least heard of it. It wasn’t until recently that I realised there are people out there who don’t know what it is. Oddly enough, one of my relatives who is a very worldly character having run various clubs in his day, whom you would have thought was very knowledgeable brought this fact home to me, he was unaware of what it is. -

Simple Substitution and Caesar Ciphers
Spring 2015 Chris Christensen MAT/CSC 483 Simple Substitution Ciphers The art of writing secret messages – intelligible to those who are in possession of the key and unintelligible to all others – has been studied for centuries. The usefulness of such messages, especially in time of war, is obvious; on the other hand, their solution may be a matter of great importance to those from whom the key is concealed. But the romance connected with the subject, the not uncommon desire to discover a secret, and the implied challenge to the ingenuity of all from who it is hidden have attracted to the subject the attention of many to whom its utility is a matter of indifference. Abraham Sinkov In Mathematical Recreations & Essays By W.W. Rouse Ball and H.S.M. Coxeter, c. 1938 We begin our study of cryptology from the romantic point of view – the point of view of someone who has the “not uncommon desire to discover a secret” and someone who takes up the “implied challenged to the ingenuity” that is tossed down by secret writing. We begin with one of the most common classical ciphers: simple substitution. A simple substitution cipher is a method of concealment that replaces each letter of a plaintext message with another letter. Here is the key to a simple substitution cipher: Plaintext letters: abcdefghijklmnopqrstuvwxyz Ciphertext letters: EKMFLGDQVZNTOWYHXUSPAIBRCJ The key gives the correspondence between a plaintext letter and its replacement ciphertext letter. (It is traditional to use small letters for plaintext and capital letters, or small capital letters, for ciphertext. We will not use small capital letters for ciphertext so that plaintext and ciphertext letters will line up vertically.) Using this key, every plaintext letter a would be replaced by ciphertext E, every plaintext letter e by L, etc. -

Cryptanalysis of Mono-Alphabetic Substitution Ciphers Using Genetic Algorithms and Simulated Annealing Shalini Jain Marathwada Institute of Technology, Dr
Vol. 08 No. 01 2018 p-ISSN 2202-2821 e-ISSN 1839-6518 (Australian ISSN Agency) 82800801201801 Cryptanalysis of Mono-Alphabetic Substitution Ciphers using Genetic Algorithms and Simulated Annealing Shalini Jain Marathwada Institute of Technology, Dr. Babasaheb Ambedkar Marathwada University, India Nalin Chhibber University of Waterloo, Ontario, Canada Sweta Kandi Marathwada Institute of Technology, Dr. Babasaheb Ambedkar Marathwada University, India ABSTRACT – In this paper, we intend to apply the principles of genetic algorithms along with simulated annealing to cryptanalyze a mono-alphabetic substitution cipher. The type of attack used for cryptanalysis is a ciphertext-only attack in which we don’t know any plaintext. In genetic algorithms and simulated annealing, for ciphertext-only attack, we need to have the solution space or any method to match the decrypted text to the language text. However, the challenge is to implement the project while maintaining computational efficiency and a high degree of security. We carry out three attacks, the first of which uses genetic algorithms alone, the second which uses simulated annealing alone and the third which uses a combination of genetic algorithms and simulated annealing. Key words: Cryptanalysis, mono-alphabetic substitution cipher, genetic algorithms, simulated annealing, fitness I. Introduction II. Mono-alphabetic substitution cipher Cryptanalysis involves the dissection of computer systems by A mono-alphabetic substitution cipher is a class of substitution unauthorized persons in order to gain knowledge about the ciphers in which the same letters of the plaintext are replaced unknown aspects of the system. It can be used to gain control by the same letters of the ciphertext. -
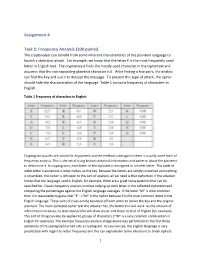
Assignment 4 Task 1: Frequency Analysis (100 Points)
Assignment 4 Task 1: Frequency Analysis (100 points) The cryptanalyst can benefit from some inherent characteristics of the plaintext language to launch a statistical attack. For example, we know that the letter E is the most frequently used letter in English text. The cryptanalyst finds the mostly-used character in the ciphertext and assumes that the corresponding plaintext character is E. After finding a few pairs, the analyst can find the key and use it to decrypt the message. To prevent this type of attack, the cipher should hide the characteristics of the language. Table 1 contains frequency of characters in English. Table 1 Frequency of characters in English Cryptogram puzzles are solved for enjoyment and the method used against them is usually some form of frequency analysis. This is the act of using known statistical information and patterns about the plaintext to determine it. In cryptograms, each letter of the alphabet is encrypted to another letter. This table of letter-letter translations is what makes up the key. Because the letters are simply converted and nothing is scrambled, the cipher is left open to this sort of analysis; all we need is that ciphertext. If the attacker knows that the language used is English, for example, there are a great many patterns that can be searched for. Classic frequency analysis involves tallying up each letter in the collected ciphertext and comparing the percentages against the English language averages. If the letter "M" is most common then it is reasonable to guess that "E"-->"M" in the cipher because E is the most common letter in the English language. -

Consonants, Vowels and Letter Frequency Stephen J
This article was downloaded by:[Canadian Research Knowledge Network] On: 8 January 2008 Access Details: [subscription number 789349985] Publisher: Psychology Press Informa Ltd Registered in England and Wales Registered Number: 1072954 Registered office: Mortimer House, 37-41 Mortimer Street, London W1T 3JH, UK Language and Cognitive Processes Publication details, including instructions for authors and subscription information: http://www.informaworld.com/smpp/title~content=t713683153 Transposed-letter effects: Consonants, vowels and letter frequency Stephen J. Lupker a; Manuel Perea b; Colin J. Davis c a University of Western Ontario, London, ON, Canada b Universitat de València, València, Spain c Royal Holloway University of London, Egham, UK Online Publication Date: 01 January 2008 To cite this Article: Lupker, Stephen J., Perea, Manuel and Davis, Colin J. (2008) 'Transposed-letter effects: Consonants, vowels and letter frequency', Language and Cognitive Processes, 23:1, 93 - 116 To link to this article: DOI: 10.1080/01690960701579714 URL: http://dx.doi.org/10.1080/01690960701579714 PLEASE SCROLL DOWN FOR ARTICLE Full terms and conditions of use: http://www.informaworld.com/terms-and-conditions-of-access.pdf This article maybe used for research, teaching and private study purposes. Any substantial or systematic reproduction, re-distribution, re-selling, loan or sub-licensing, systematic supply or distribution in any form to anyone is expressly forbidden. The publisher does not give any warranty express or implied or make any representation that the contents will be complete or accurate or up to date. The accuracy of any instructions, formulae and drug doses should be independently verified with primary sources. The publisher shall not be liable for any loss, actions, claims, proceedings, demand or costs or damages whatsoever or howsoever caused arising directly or indirectly in connection with or arising out of the use of this material. -

Letter Frequency Analysis of Languages Using Latin Alphabet
International Linguistics Research; Vol. 1, No. 1; 2018 ISSN 2576-2974 E-ISSN 2576-2982 https://doi.org/10.30560/ilr.v1n1p18 Letter Frequency Analysis of Languages Using Latin Alphabet Gintautas Grigas1 & Anita Juškevičienė1 1 Institute of Data Science and Digital Technologies, Vilnius University, Lithuania Correspondence: Anita Juškevičienė, Institute of Data Science and Digital Technologies, Vilnius University, Akademijos str. 4, LT-08663, Vilnius, Lithuania. Tel: 370-5210-9314. E-mail: [email protected], [email protected] Received: February 23, 2018; Accepted: March 8, 2018; Published: March 26, 2018 Abstract The evaluation of the peculiarities of alphabets, particularly the frequency of letters is essential when designing keyboards, analysing texts, designing alphabet-based games, and doing some text mining. Thus, it is important to determine what might be useful for designers of text input tools, and of other technologies related to sets of letters. Knowledge of common features among different languages gives an opportunity to take advantage of the experience of other languages. Nowadays an increasing amount of texts is published on the Internet. In order to adequately compare the frequencies of letters in different languages used in the online space, Wikipedia texts have been selected as a source material for investigation. This paper presents the Method of the Adjacent Letter Frequency Differences in the frequency line, which helps to evaluate frequency breakpoints. This is a uniform evaluation criterion for 25 main languages using Latin script in order to highlight the similarities and differences among them. Research focuses on the letter frequency analysis in the area of rarely used native letters and frequently used foreign letters in a particular language. -

John F. Byrne's Chaocipher Revealed
John F. Byrne’s Chaocipher Revealed John F. Byrne’s Chaocipher Revealed: An Historical and Technical Appraisal MOSHE RUBIN1 Abstract Chaocipher is a method of encryption invented by John F. Byrne in 1918, who tried unsuccessfully to interest the US Signal Corp and Navy in his system. In 1953, Byrne presented Chaocipher-encrypted messages as a challenge in his autobiography Silent Years. Although numerous students of cryptanalysis attempted to solve the challenge messages over the years, none succeeded. For ninety years the Chaocipher algorithm was a closely guarded secret known only to a handful of persons. Following fruitful negotiations with the Byrne family during the period 2009-2010, the Chaocipher papers and materials have been donated to the National Cryptologic Museum in Ft. Meade, MD. This paper presents a comprehensive historical and technical evaluation of John F. Byrne and his Chaocipher system. Keywords ACA, American Cryptogram Association, block cipher encryption modes, Chaocipher, dynamic substitution, Greg Mellen, Herbert O. Yardley, John F. Byrne, National Cryptologic Museum, Parker Hitt, Silent Years, William F. Friedman 1 Introduction John Francis Byrne was born on 11 February 1880 in Dublin, Ireland. He was an intimate friend of James Joyce, the famous Irish writer and poet, studying together in Belvedere College and University College in Dublin. Joyce based the character named Cranly in Joyce’s A Portrait of the Artist as a Young Man on Byrne, used Byrne’s Dublin residence of 7 Eccles Street as the home of Leopold and Molly Bloom, the main characters in Joyce’s Ulysses, and made use of real-life anecdotes of himself and Byrne as the basis of stories in Ulysses. -

Shift Cipher Substitution Cipher Vigenère Cipher Hill Cipher
Lecture 2 Classical Cryptosystems Shift cipher Substitution cipher Vigenère cipher Hill cipher 1 Shift Cipher • A Substitution Cipher • The Key Space: – [0 … 25] • Encryption given a key K: – each letter in the plaintext P is replaced with the K’th letter following the corresponding number ( shift right ) • Decryption given K: – shift left • History: K = 3, Caesar’s cipher 2 Shift Cipher • Formally: • Let P=C= K=Z 26 For 0≤K≤25 ek(x) = x+K mod 26 and dk(y) = y-K mod 26 ʚͬ, ͭ ∈ ͔ͦͪ ʛ 3 Shift Cipher: An Example ABCDEFGHIJKLMNOPQRSTUVWXYZ 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 • P = CRYPTOGRAPHYISFUN Note that punctuation is often • K = 11 eliminated • C = NCJAVZRCLASJTDQFY • C → 2; 2+11 mod 26 = 13 → N • R → 17; 17+11 mod 26 = 2 → C • … • N → 13; 13+11 mod 26 = 24 → Y 4 Shift Cipher: Cryptanalysis • Can an attacker find K? – YES: exhaustive search, key space is small (<= 26 possible keys). – Once K is found, very easy to decrypt Exercise 1: decrypt the following ciphertext hphtwwxppelextoytrse Exercise 2: decrypt the following ciphertext jbcrclqrwcrvnbjenbwrwn VERY useful MATLAB functions can be found here: http://www2.math.umd.edu/~lcw/MatlabCode/ 5 General Mono-alphabetical Substitution Cipher • The key space: all possible permutations of Σ = {A, B, C, …, Z} • Encryption, given a key (permutation) π: – each letter X in the plaintext P is replaced with π(X) • Decryption, given a key π: – each letter Y in the ciphertext C is replaced with π-1(Y) • Example ABCDEFGHIJKLMNOPQRSTUVWXYZ πBADCZHWYGOQXSVTRNMSKJI PEFU • BECAUSE AZDBJSZ 6 Strength of the General Substitution Cipher • Exhaustive search is now infeasible – key space size is 26! ≈ 4*10 26 • Dominates the art of secret writing throughout the first millennium A.D. -

Network Security
Cristina Nita-Rotaru CS6740: Network security Additional material: Cryptography 1: Terminology and classic ciphers Readings for this lecture Required readings: } Cryptography on Wikipedia Interesting reading } The Code Book by Simon Singh 3 Cryptography The science of secrets… } Cryptography: the study of mathematical techniques related to aspects of providing information security services (create) } Cryptanalysis: the study of mathematical techniques for attempting to defeat information security services (break) } Cryptology: the study of cryptography and cryptanalysis (both) 4 Cryptography Basic terminology in cryptography } cryptography } plaintexts } cryptanalysis } ciphertexts } cryptology } keys } encryption } decryption plaintext ciphertext plaintext Encryption Decryption Key_Encryption Key_Decryption 5 Cryptography Cryptographic protocols } Protocols that } Enable parties } Achieve objectives (goals) } Overcome adversaries (attacks) } Need to understand } Who are the parties and the context in which they act } What are the goals of the protocols } What are the capabilities of adversaries 6 Cryptography Cryptographic protocols: Parties } The good guys } The bad guys Alice Carl Bob Eve Introduction of Alice and Bob Check out wikipedia for a longer attributed to the original RSA paper. list of malicious crypto players. 7 Cryptography Cryptographic protocols: Objectives/Goals } Most basic problem: } Ensure security of communication over an insecure medium } Basic security goals: } Confidentiality (secrecy, confidentiality) } Only the -

An Improved Arabic Keyboard Layout
Sci.Int.(Lahore),33(1),5-15,2021 ISSN 1013-5316; CODEN: SINTE 8 5 AN IMPROVED ARABIC KEYBOARD LAYOUT 1Amjad Qtaish, 2Jalawi Alshudukhi, 3Badiea Alshaibani, 4Yosef Saleh, 5Salam Bazrawi College of Computer Science and Engineering, University of Ha'il, Ha'il, Saudi Arabia. [email protected], [email protected], [email protected], [email protected], [email protected] ABSTRACT: One of the most important human–machine interaction (HMI) systems is the computer keyboard. The keyboard layout (KL) dictates how a person interacts with a physical keyboard through the way in which the letters, numbers, punctuation marks, and symbols are mapped and arranged on the keyboard. Mapping letters onto the keys of a keyboard is complex because many issues need to be taken into considerations, such as the nature of the language, finger fatigue, hand balance, typing speed, and distance traveled by fingers during typing and finger movements. There are two main kinds of KL: English and Arabic. Although numerous research studies have proposed different layouts for the English keyboard, there is a lack of research studies that focus on the Arabic KL. To address this lack, this study analyzed and clarified the limitations of the standard legacy Arabic KL. Then an efficient Arabic KL was proposed to overcome the limitations of the current KL. The frequency of Arabic letters and bi-gram probabilities were measured on a large Arabic corpus in order to assess the current KL and to design the improved Arabic KL. The improved Arabic KL was then evaluated and compared against the current KL in terms of letter frequency, finger-travel distance, hand and finger balance, bi-gram frequency, row distribution, and most frequent words. -

Algorithms and Mechanisms Historical Ciphers
Algorithms and Mechanisms Cryptography is nothing more than a mathematical framework for discussing the implications of various paranoid delusions — Don Alvarez Historical Ciphers Non-standard hieroglyphics, 1900BC Atbash cipher (Old Testament, reversed Hebrew alphabet, 600BC) Caesar cipher: letter = letter + 3 ‘fish’ ‘ilvk’ rot13: Add 13/swap alphabet halves •Usenet convention used to hide possibly offensive jokes •Applying it twice restores the original text Substitution Ciphers Simple substitution cipher: a=p,b=m,c=f,... •Break via letter frequency analysis Polyalphabetic substitution cipher 1. a = p, b = m, c = f, ... 2. a = l, b = t, c = a, ... 3. a = f, b = x, c = p, ... •Break by decomposing into individual alphabets, then solve as simple substitution One-time Pad (1917) Message s e c r e t 18 5 3 17 5 19 OTP +15 8 1 12 19 5 7 13 4 3 24 24 g m d c x x OTP is unbreakable provided •Pad is never reused (VENONA) •Unpredictable random numbers are used (physical sources, e.g. radioactive decay) One-time Pad (ctd) Used by •Russian spies •The Washington-Moscow “hot line” •CIA covert operations Many snake oil algorithms claim unbreakability by claiming to be a OTP •Pseudo-OTPs give pseudo-security Cipher machines attempted to create approximations to OTPs, first mechanically, then electronically Cipher Machines (~1920) 1. Basic component = wired rotor •Simple substitution 2. Step the rotor after each letter •Polyalphabetic substitution, period = 26 Cipher Machines (ctd) 3. Chain multiple rotors Each rotor steps the next one when a full