Cisco Billing and Measurements Server User's Guide, Release 3.30
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Administering Unidata on UNIX Platforms
C:\Program Files\Adobe\FrameMaker8\UniData 7.2\7.2rebranded\ADMINUNIX\ADMINUNIXTITLE.fm March 5, 2010 1:34 pm Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta UniData Administering UniData on UNIX Platforms UDT-720-ADMU-1 C:\Program Files\Adobe\FrameMaker8\UniData 7.2\7.2rebranded\ADMINUNIX\ADMINUNIXTITLE.fm March 5, 2010 1:34 pm Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Notices Edition Publication date: July, 2008 Book number: UDT-720-ADMU-1 Product version: UniData 7.2 Copyright © Rocket Software, Inc. 1988-2010. All Rights Reserved. Trademarks The following trademarks appear in this publication: Trademark Trademark Owner Rocket Software™ Rocket Software, Inc. Dynamic Connect® Rocket Software, Inc. RedBack® Rocket Software, Inc. SystemBuilder™ Rocket Software, Inc. UniData® Rocket Software, Inc. UniVerse™ Rocket Software, Inc. U2™ Rocket Software, Inc. U2.NET™ Rocket Software, Inc. U2 Web Development Environment™ Rocket Software, Inc. wIntegrate® Rocket Software, Inc. Microsoft® .NET Microsoft Corporation Microsoft® Office Excel®, Outlook®, Word Microsoft Corporation Windows® Microsoft Corporation Windows® 7 Microsoft Corporation Windows Vista® Microsoft Corporation Java™ and all Java-based trademarks and logos Sun Microsystems, Inc. UNIX® X/Open Company Limited ii SB/XA Getting Started The above trademarks are property of the specified companies in the United States, other countries, or both. All other products or services mentioned in this document may be covered by the trademarks, service marks, or product names as designated by the companies who own or market them. License agreement This software and the associated documentation are proprietary and confidential to Rocket Software, Inc., are furnished under license, and may be used and copied only in accordance with the terms of such license and with the inclusion of the copyright notice. -

LATEX for Beginners
LATEX for Beginners Workbook Edition 5, March 2014 Document Reference: 3722-2014 Preface This is an absolute beginners guide to writing documents in LATEX using TeXworks. It assumes no prior knowledge of LATEX, or any other computing language. This workbook is designed to be used at the `LATEX for Beginners' student iSkills seminar, and also for self-paced study. Its aim is to introduce an absolute beginner to LATEX and teach the basic commands, so that they can create a simple document and find out whether LATEX will be useful to them. If you require this document in an alternative format, such as large print, please email [email protected]. Copyright c IS 2014 Permission is granted to any individual or institution to use, copy or redis- tribute this document whole or in part, so long as it is not sold for profit and provided that the above copyright notice and this permission notice appear in all copies. Where any part of this document is included in another document, due ac- knowledgement is required. i ii Contents 1 Introduction 1 1.1 What is LATEX?..........................1 1.2 Before You Start . .2 2 Document Structure 3 2.1 Essentials . .3 2.2 Troubleshooting . .5 2.3 Creating a Title . .5 2.4 Sections . .6 2.5 Labelling . .7 2.6 Table of Contents . .8 3 Typesetting Text 11 3.1 Font Effects . 11 3.2 Coloured Text . 11 3.3 Font Sizes . 12 3.4 Lists . 13 3.5 Comments & Spacing . 14 3.6 Special Characters . 15 4 Tables 17 4.1 Practical . -

Factor — Factor Analysis
Title stata.com factor — Factor analysis Description Quick start Menu Syntax Options for factor and factormat Options unique to factormat Remarks and examples Stored results Methods and formulas References Also see Description factor and factormat perform a factor analysis of a correlation matrix. The commands produce principal factor, iterated principal factor, principal-component factor, and maximum-likelihood factor analyses. factor and factormat display the eigenvalues of the correlation matrix, the factor loadings, and the uniqueness of the variables. factor expects data in the form of variables, allows weights, and can be run for subgroups. factormat is for use with a correlation or covariance matrix. Quick start Principal-factor analysis using variables v1 to v5 factor v1 v2 v3 v4 v5 As above, but retain at most 3 factors factor v1-v5, factors(3) Principal-component factor analysis using variables v1 to v5 factor v1-v5, pcf Maximum-likelihood factor analysis factor v1-v5, ml As above, but perform 50 maximizations with different starting values factor v1-v5, ml protect(50) As above, but set the seed for reproducibility factor v1-v5, ml protect(50) seed(349285) Principal-factor analysis based on a correlation matrix cmat with a sample size of 800 factormat cmat, n(800) As above, retain only factors with eigenvalues greater than or equal to 1 factormat cmat, n(800) mineigen(1) Menu factor Statistics > Multivariate analysis > Factor and principal component analysis > Factor analysis factormat Statistics > Multivariate analysis > Factor and principal component analysis > Factor analysis of a correlation matrix 1 2 factor — Factor analysis Syntax Factor analysis of data factor varlist if in weight , method options Factor analysis of a correlation matrix factormat matname, n(#) method options factormat options matname is a square Stata matrix or a vector containing the rowwise upper or lower triangle of the correlation or covariance matrix. -

Text Processing Tools
Tools for processing text David Morgan Tools of interest here sort paste uniq join xxd comm tr fmt sed fold head file tail dd cut strings 1 sort sorts lines by default can delimit fields in lines ( -t ) can sort by field(s) as key(s) (-k ) can sort fields of numerals numerically ( -n ) Sort by fields as keys default sort sort on shell (7 th :-delimited) field UID as secondary (tie-breaker) field 2 Do it numerically versus How sort defines text ’s “fields ” by default ( a space character, ascii 32h = ٠ ) ٠bar an 8-character string ٠foo “By default, fields are separated by the empty string between a non-blank character and a blank character.” ٠bar separator is the empty string between non-blank “o” and the space ٠foo 1 2 ٠bar and the string has these 2 fields, by default ٠foo 3 How sort defines text ’s “fields ” by –t specification (not default) ( a space character, ascii 32h = ٠ ) ٠bar an 8-character string ٠foo “ `-t SEPARATOR' Use character SEPARATOR as the field separator... The field separator is not considered to be part of either the field preceding or the field following ” separators are the blanks themselves, and fields are ' "٠ " ٠bar with `sort -t ٠foo whatever they separate 12 3 ٠bar and the string has these 3 fields ٠foo data sort fields delimited by vertical bars field versus sort field ("1941:japan") ("1941") 4 sort efficiency bubble sort of n items, processing grows as n 2 shell sort as n 3/2 heapsort/mergesort/quicksort as n log n technique matters sort command highly evolved and optimized – better than you could do it yourself Big -O: " bogdown propensity" how much growth requires how much time 5 sort stability stable if input order of key-equal records preserved in output unstable if not sort is not stable GNU sort has –stable option sort stability 2 outputs, from same input (all keys identical) not stable stable 6 uniq operates on sorted input omits repeated lines counts them uniq 7 xxd make hexdump of file or input your friend testing intermediate pipeline data cf. -

QLOAD Queue Load / Unload Utility for IBM MQ
Queue Load / Unload Utility for IBM MQ User Guide Version 9.1.1 27th August 2020 Paul Clarke MQGem Software Limited [email protected] Queue Load / Unload Utility for IBM MQ Take Note! Before using this User's Guide and the product it supports, be sure to read the general information under "Notices” Twenty-fourth Edition, August 2020 This edition applies to Version 9.1.1 of Queue Load / Unload Utility for IBM MQ and to all subsequent releases and modifications until otherwise indicated in new editions. (c) Copyright MQGem Software Limited 2015, 2020. All rights reserved. ii Queue Load / Unload Utility for IBM MQ Notices The following paragraph does not apply in any country where such provisions are inconsistent with local law. MQGEM SOFTWARE LIMITED PROVIDES THIS PUBLICATION "AS IS" WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESS OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. Some states do not allow disclaimer of express or implied warranties in certain transactions, therefore this statement may not apply to you. The information contained in this document has not be submitted to any formal test and is distributed AS IS. The use of the information or the implementation of any of these techniques is a customer responsibility and depends on the customer's ability to evaluate and integrate them into the customer's operational environment. While each item has been reviewed by MQGem Software for accuracy in a specific situation, there is no guarantee that the same or similar results will be obtained elsewhere. -

(LS-Factor) for Modeling Soil Erosion by Water
Geosciences 2015, 5, 117-126; doi:10.3390/geosciences5020117 OPEN ACCESS geosciences ISSN 2076-3263 www.mdpi.com/journal/geosciences Short Communication A New European Slope Length and Steepness Factor (LS-Factor) for Modeling Soil Erosion by Water Panos Panagos 1,*, Pasquale Borrelli 1,† and Katrin Meusburger 2,† 1 European Commission, Joint Research Centre, Institute for Environment and Sustainability, Via Enrico Fermi 2749, I-21027 Ispra (VA), Italy; E-Mail: [email protected] 2 Environmental Geosciences, University of Basel, Bernoullistrasse 30, 4056 Basel, Switzerland; E-Mail: [email protected] † These authors contributed equally to this work. * Author to whom correspondence should be addressed; E-Mail: [email protected]; Tel.: +39-0332-785574; Fax: +39-0332-786394. Academic Editor: Jesus Martinez-Frias Received: 24 December 2014 / Accepted: 23 March 2015 / Published: 3 April 2015 Abstract: The Universal Soil Loss Equation (USLE) model is the most frequently used model for soil erosion risk estimation. Among the six input layers, the combined slope length and slope angle (LS-factor) has the greatest influence on soil loss at the European scale. The S-factor measures the effect of slope steepness, and the L-factor defines the impact of slope length. The combined LS-factor describes the effect of topography on soil erosion. The European Soil Data Centre (ESDAC) developed a new pan-European high-resolution soil erosion assessment to achieve a better understanding of the spatial and temporal patterns of soil erosion in Europe. The LS-calculation was performed using the original equation proposed by Desmet and Govers (1996) and implemented using the System for Automated Geoscientific Analyses (SAGA), which incorporates a multiple flow algorithm and contributes to a precise estimation of flow accumulation. -

5 Command Line Functions by Barbara C
ADAPS: Chapter 5. Command Line Functions 5 Command Line Functions by Barbara C. Hoopes and James F. Cornwall This chapter describes ADAPS command line functions. These are functions that are executed from the UNIX command line instead of from ADAPS menus, and that may be run manually or by automated means such as “cron” jobs. Most of these functions are NOT accessible from the ADAPS menus. These command line functions are described in detail below. 5.1 Hydra Although Hydra is available from ADAPS at the PR sub-menu, Edit Time Series Data using Hydra (TS_EDIT), it can also be started from the command line. However, to start Hydra outside of ADAPS, a DV or UV RDB file needs to be available to edit. The command is “hydra rdb_file_name.” For a complete description of using Hydra, refer to Section 4.5.2 Edit Time-Series Data using Hydra (TS_EDIT). 5.2 nwrt2rdb This command is used to output rating information in RDB format. It writes RDB files with a table containing the rating equation parameters or the rating point pairs, with all other information contained in the RDB comments. The following arguments can be used with this command: nwrt2rdb -ooutfile -zdbnum -aagency -nstation -dddid -trating_type -irating_id -e (indicates to output ratings in expanded form; it is ignored for equation ratings.) -l loctzcd (time zone code or local time code "LOC") -m (indicates multiple output files.) -r (rounding suppression) Rules • If -o is omitted, nwrt2rdb writes to stdout; AND arguments -n, -d, -t, and -i must be present. • If -o is present, no other arguments are required, and the program will use ADAPS routines to prompt for them. -

Computing in the ACI Cluster
Computing in the ACI Cluster Ben Seiyon Lee Pennsylvania State University Department of Statistics October 5, 2017 Graduate Workshop 10/5/2017 1 Outline 1 High Performance Computing 2 Accessing ACI 3 Basic Unix Commands 4 Navigation and File Creation 5 SCP clients 6 PBS scripts 7 Running PBS scripts 8 Parallelization 9 Best Practices Graduate Workshop 10/5/2017 2 High Performance Computing High Performance Computing Large number of processors Large memory requirements Large storage requirements Long runtimes ACI-B: Batch Log in to a head node and submit jobs to compute nodes Groups can purchase allocations or use open queue Intel Xeon E5-2680 v2 2.8 GHz, 256 Gb RAM, 20 cores per node Statistics Department has 5 nodes (20 processors per node) Graduate Workshop 10/5/2017 3 Accessing ACI Sign up for an account: ICS-ACI Account Sign-up 2-Factor Authentication Mac Open Terminal ssh into ACI: ssh <username>@aci-b.aci.ics.psu.edu Complete 2 Factor Authentication Windows Open Putty Enter aci-b.aci.ics.psu.edu in the Host Name field Select SSH then X11 and Enable X11 forwarding Select Connection then Data and enter your username in the Auto-login username field Graduate Workshop 10/5/2017 4 Unix Commands Change directories: cd Home Directory: cd Here: cd . Up one directory: cd .. All files in the directory: ls * Wildcards: Test* . *.png Send output to another command: | Write command output to a file: ls > log.txt Create Directory: mkdir cd ~/ work mkdir Workshop mkdir WorkshopB l s Remove Directory: rmdir rmdir WorkshopB l s mkdir WorkshopB Graduate Workshop 10/5/2017 5 Unix Commands Move Files: mv mv file1 .txt ./WorkshopB/ mv ../WorkshopB/file1 .txt ./WorkshopB/file2 .txt Copy Files: cp cp ../WorkshopB/file1 .txt ../WorkshopB/file2 .txt Remove Files: rm rm file1.txt rm −r WorkshopB Access Manual for commands: man man rm q List files: ls l s ls ~/work/Workshop Graduate Workshop 10/5/2017 6 Unix Commands Print the current directoy: pwd pwd Past commands: history h i s t o r y Manage permissions for a file: chmod chmod u=rwx,g=rwx,o=rwx file1 . -

From Donor to Patient: Collection, Preparation and Cryopreservation of Fecal Samples for Fecal Microbiota Transplantation
diseases Review From Donor to Patient: Collection, Preparation and Cryopreservation of Fecal Samples for Fecal Microbiota Transplantation Carole Nicco 1 , Armelle Paule 2, Peter Konturek 3 and Marvin Edeas 1,* 1 Cochin Institute, INSERM U1016, University Paris Descartes, Development, Reproduction and Cancer, Cochin Hospital, 75014 Paris, France; [email protected] 2 International Society of Microbiota, 75002 Paris, France; [email protected] 3 Teaching Hospital of the University of Jena, Thuringia-Clinic Saalfeld, 07318 Saalfeld, Germany; [email protected] * Correspondence: [email protected] Received: 6 March 2020; Accepted: 10 April 2020; Published: 15 April 2020 Abstract: Fecal Microbiota Transplantation (FMT) is suggested as an efficacious therapeutic strategy for restoring intestinal microbial balance, and thus for treating disease associated with alteration of gut microbiota. FMT consists of the administration of fresh or frozen fecal microorganisms from a healthy donor into the intestinal tract of diseased patients. At this time, in according to healthcare authorities, FMT is mainly used to treat recurrent Clostridium difficile. Despite the existence of a few existing stool banks worldwide and many studies of the FMT, there is no standard method for producing material for FMT, and there are a multitude of factors that can vary between the institutions. The main constraints for the therapeutic uses of FMT are safety concerns and acceptability. Technical and logistical issues arise when establishing such a non-standardized treatment into clinical practice with safety and proper governance. In this context, our manuscript describes a process of donor safety screening for FMT compiling clinical and biological examinations, questionnaires and interviews of donors. -

A Type System for Format Strings E
ifact t * r * Comple t te A A n * te W E is s * e C n l l o D C A o * * c T u e m S s E u e S e n I R t v A Type System for Format Strings e o d t y * s E a * a l d u e a t Konstantin Weitz Gene Kim Siwakorn Srisakaokul Michael D. Ernst University of Washington, USA {weitzkon,genelkim,ping128,mernst}@cs.uw.edu ABSTRACT // Untested code (Hadoop) Most programming languages support format strings, but their use Resource r = ... format("Insufficient memory %d", r); is error-prone. Using the wrong format string syntax, or passing the wrong number or type of arguments, leads to unintelligible text // Unchecked input (FindBugs) output, program crashes, or security vulnerabilities. String urlRewriteFormat = read(); This paper presents a type system that guarantees that calls to format(urlRewriteFormat, url); format string APIs will never fail. In Java, this means that the API will not throw exceptions. In C, this means that the API will not // User unaware log is a format routine (Daikon) log("Exception " + e); return negative values, corrupt memory, etc. We instantiated this type system for Java’s Formatter API, and // Invalid syntax for Formatter API (ping-gcal) evaluated it on 6 large and well-maintained open-source projects. format("Unable to reach {0}", server); Format string bugs are common in practice (our type system found Listing 1: Real-world code examples of common programmer 104 bugs), and the annotation burden on the user of our type system mistakes that lead to format routine call failures. -

Advanced Topics in Sorting
Advanced Topics in Sorting complexity system sorts duplicate keys comparators 1 complexity system sorts duplicate keys comparators 2 Complexity of sorting Computational complexity. Framework to study efficiency of algorithms for solving a particular problem X. Machine model. Focus on fundamental operations. Upper bound. Cost guarantee provided by some algorithm for X. Lower bound. Proven limit on cost guarantee of any algorithm for X. Optimal algorithm. Algorithm with best cost guarantee for X. lower bound ~ upper bound Example: sorting. • Machine model = # comparisons access information only through compares • Upper bound = N lg N from mergesort. • Lower bound ? 3 Decision Tree a < b yes no code between comparisons (e.g., sequence of exchanges) b < c a < c yes no yes no a b c b a c a < c b < c yes no yes no a c b c a b b c a c b a 4 Comparison-based lower bound for sorting Theorem. Any comparison based sorting algorithm must use more than N lg N - 1.44 N comparisons in the worst-case. Pf. Assume input consists of N distinct values a through a . • 1 N • Worst case dictated by tree height h. N ! different orderings. • • (At least) one leaf corresponds to each ordering. Binary tree with N ! leaves cannot have height less than lg (N!) • h lg N! lg (N / e) N Stirling's formula = N lg N - N lg e N lg N - 1.44 N 5 Complexity of sorting Upper bound. Cost guarantee provided by some algorithm for X. Lower bound. Proven limit on cost guarantee of any algorithm for X. -
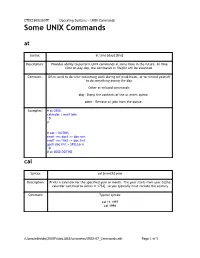
Some UNIX Commands At
CTEC1863/2007F Operating Systems – UNIX Commands Some UNIX Commands at Syntax: at time [day] [file] Description: Provides ability to perform UNIX commands at some time in the future. At time time on day day, the commands in filefile will be executed. Comment: Often used to do time-consuming work during off-peak hours, or to remind yourself to do something during the day. Other at-related commands: atq - Dump the contents of the at event queue. atrm - Remove at jobs from the queue. Examples: # at 0300 calendar | mail john ^D # # cat > DOTHIS nroff -ms doc1 >> doc.fmt nroff -ms file2 >> doc.fmt spell doc.fmt > SPELLerrs ^D # at 0000 DOTHIS cal Syntax: cal [month] year Description: Prints a calendar for the specified year or month. The year starts from year 0 [the calendar switched to Julian in 1752], so you typically must include the century Comment: Typical syntax: cal 11 1997 cal 1998 /Users/mboldin/2007F/ctec1863/unixnotes/UNIX-07_Commands.odt Page 1 of 5 CTEC1863/2007F Operating Systems – UNIX Commands calendar Syntax: calendar [-] Description: You must set-up a file, typically in your home directory, called calendar. This is a database of events. Comment: Each event must have a date mentioned in it: Sept 10, 12/5, Aug 21 1998, ... Each event scheduled for the day or the next day will be listed on the screen. lpr Syntax: lpr [OPTIONS] [FILE] [FILE] ... Description: The files are queued to be output to the printer. Comment: On some UNIX systems, this command is called lp, with slightly different options. Both lpr and lp first make a copy of the file(s) to be printed in the spool directory.